当前位置:网站首页>Computer graduation design PHP enterprise staff training management system
Computer graduation design PHP enterprise staff training management system
2022-07-06 01:44:00 【q_ one billion thirty-nine million six hundred and ninety-two t】
Project introduction
The enterprise staff training management system adopts php and mysql Database development , It is an important part of enterprise human resource development and management , Employee training system can more effectively mine training projects 、 Make better use of limited resources for training : Give full play to the enterprise 、 management layer 、 The positive role of training management , Organize employees to train and learn more effectively . In this process, the circulation of information is increased 、 Open training and strengthen the supervision of training projects , Make training really become employees' own training , This will also enhance the enthusiasm of employees to learn and make them devote themselves to their future work with greater enthusiasm .
1. System login : System login is the intersection for users to access the system , The system login interface is designed , Include user name 、 Password and verification code , Then judge the identity information of the logged in user , Determine whether it is an administrator user or an ordinary user .
2. System user management : Both super administrators and ordinary administrators need to manage system users , Including the addition of ordinary administrators 、 Delete 、 modify 、 Inquire about , Change the login password of the Administrator , The newly added administrator user can log in to the system .
3. General user management : The administrator can manage the accounts of other ordinary users of the system , Including entering new users , Delete existing ordinary users , Modify the information of existing ordinary users , And you can search ordinary users through keywords such as user name and name , Print the user list page , Export user list to excel in .
4. Change Password : All users of the system ( Administrators and ordinary users ) You should be able to change your login password , After modification, you need to log in again .
5. Personal data management : Used by ordinary users , After ordinary users log in to the system , You can modify your original personal information , Such as changing the telephone number 、 Mailbox, etc , The user name cannot be modified .
6. Teacher information management : After the administrator releases the teacher information , Ordinary users can query the teacher information , The user selects a teacher information , Query teacher information , Administrator audit add , Or delete the teacher information .
7. Employee information management : After the administrator publishes the employee information , Ordinary users can query the employee information , The user selects an employee information , Query employee information , Administrator audit add , Or delete employee information .
8. Organization information management : After the administrator releases the organization information , Ordinary users can query the information of the organization , The user selects an organization information , Query organization information , Administrator audit add , Or delete organization information .
design sketch
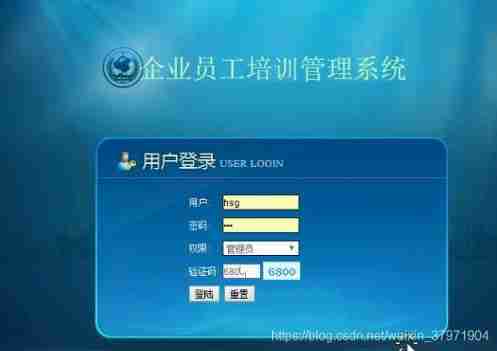
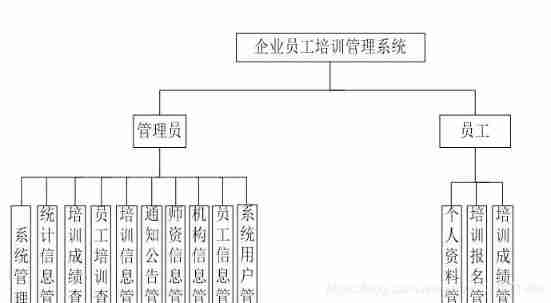
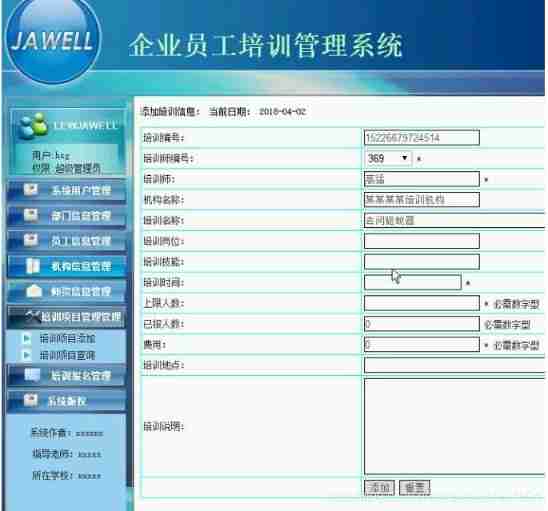
Objective record
The first 1 Chapter The introduction 1
1.1 Development background 1
1.2 Development significance 1
1.3 research contents 1
1.4 The structure of the paper 2
1.5 Summary of this chapter 2
The first 2 Chapter Introduction of system development technology 3
2.1WampServer And Apache brief introduction 3
2.2HTML/CSS brief introduction 3
2.3PHP brief introduction 3
2.4MYSQL Database concepts and features 4
2.5 Summary of this chapter 4
The first 3 Chapter Systems analysis 5
3.1 Functional requirements analysis 5
3.2 Business process analysis 7
3.3 Data flow analysis 7
3.4 Summary of this chapter 9
The first 4 Chapter The system design 10
4.1 System design idea 10
4.2 Overall design of the system 10
4.3 System function module design 11
4.4 Database design 12
4.4.1 Conceptual model design 12
4.4.2 Database table design 13
4.4.3 Database connection count 16
4.5 Summary of this chapter 16
The first 5 Chapter The realization of the system 17
5.1 Implementation environment description 17
5.2 The realization of the front page 17
5.3 The implementation of login module 18
5.4 The realization of organization information management module 20
5.5 The realization of teacher information management module 22
5.6 Implementation of employee information management module 24
5.7 Implementation of training information management module 26
5.9 Implementation of paging algorithm 28
5.10 Summary of this chapter 30
The first 6 Chapter The system test 31
6.1 Test purpose 31
6.2 Interface tests 31
6.3 A functional test 31
6.4 test result 34
6.5 Summary of this chapter 34
The first 7 Chapter summary 35
Cause thank 36
reference 37
边栏推荐
- [detailed] several ways to quickly realize object mapping
- [flask] official tutorial -part2: Blueprint - view, template, static file
- Selenium waiting mode
- Basic process and testing idea of interface automation
- Kubernetes stateless application expansion and contraction capacity
- Paddle框架:PaddleNLP概述【飞桨自然语言处理开发库】
- leetcode刷题_平方数之和
- MySQL learning notes 2
- 【SSRF-01】服务器端请求伪造漏洞原理及利用实例
- Thinking about the best practice of dynamics 365 development collaboration
猜你喜欢
Alibaba-Canal使用详解(排坑版)_MySQL与ES数据同步

Basic operations of databases and tables ----- default constraints
leetcode刷题_反转字符串中的元音字母

1. Introduction to basic functions of power query

NumPy 数组索引 切片

XSS learning XSS lab problem solution
You are using pip version 21.1.1; however, version 22.0.3 is available. You should consider upgradin
c#网页打开winform exe

A picture to understand! Why did the school teach you coding but still not
leetcode3、實現 strStr()
随机推荐
c#网页打开winform exe
ClickOnce 不支持请求执行级别“requireAdministrator”
Sword finger offer 38 Arrangement of strings
Basic operations of databases and tables ----- default constraints
Initialize MySQL database when docker container starts
[flask] obtain request information, redirect and error handling
[solved] how to generate a beautiful static document description page
ctf. Show PHP feature (89~110)
2022年广西自治区中职组“网络空间安全”赛题及赛题解析(超详细)
1. Introduction to basic functions of power query
Flowable source code comments (36) process instance migration status job processor, BPMN history cleanup job processor, external worker task completion job processor
剑指 Offer 38. 字符串的排列
【Flask】官方教程(Tutorial)-part2:蓝图-视图、模板、静态文件
Comments on flowable source code (XXXV) timer activation process definition processor, process instance migration job processor
Alibaba canal usage details (pit draining version)_ MySQL and ES data synchronization
NiO related knowledge (II)
Code review concerns
Reasonable and sensible
2 power view
leetcode-2.回文判断