当前位置:网站首页>Japanese government and enterprise employees got drunk and lost 460000 information USB flash drives. They publicly apologized and disclosed password rules
Japanese government and enterprise employees got drunk and lost 460000 information USB flash drives. They publicly apologized and disclosed password rules
2022-07-07 13:09:00 【Internet Security Research Institute】
In recent days, , Staff in nizaki, Japan lost their belongings due to drunkenness 46 Name of 10000 Japanese citizens 、 address 、 Tax payment amount and other sensitive personal information U The matter of the plate attracted attention . City officials held a press conference to publicly apologize , But inadvertently revealed U Disk password digits and composition rules .
According to the Japanese media , Equipped with nizaki City, Hyogo Prefecture, Japan 46 ten thousand 517 Personal information of citizens U Pan Yu 21 Lost by accident , It contains the names of all citizens 、 address 、 Date of birth and amount of tax paid .
6 month 23 Japan , The city government officials held a press conference , Just U Apologize for the accidental loss of the disk . At the meeting , Site officials said , Nizaki municipal government outsourced the business of granting subsidies to the third-party enterprises , The staff of the enterprise have no permission , Copy citizen information into U disc , On 21 Daily carry U I went to Kaida City, Osaka Prefecture to deal with business . The employee did not delete the data after processing , evening 7 Take it at halfpastten U Pan and his colleagues went to a restaurant to have a drink about 3 Hours , evening 10 I got drunk and fell asleep on the road on my way home at halfpastten .22 Early morning 3 Wake up , It was found that U The briefcase on disk is missing , Immediately call the police and report to nizaki city .
At the press conference, relevant officials said ,U The disk password is hard to crack , Call the password a total of 13 digit , It consists of English letters and numbers .
This answer was ridiculed by netizens , This is it. “ The ultimate negative teaching material ”. On the Internet , Many netizens have given 13 Bit password guessing , The loudest voice is “Amagasaki2022”—— The English words of nizaki plus the year 2022. Whether the password is true as guessed by netizens 、 Before finding the briefcase U Whether the disk password has been cracked , The results of the investigation by the nizaki police are yet to be seen .
Based on the above events , Should we also “ Look in the mirror ”, Whether our government and enterprises are U Disk usage 、 The data transfer 、 Data usage 、 There are similar security risks in data management ?
Enterprises usually have complete, detailed and strict rules and regulations , But there are still various loopholes , In addition, the network environment is complex , There are many uncertain factors , Timely detection and prevention of data leakage has become a key problem that every enterprise must face .
Enterprises in network security 、 Data security protection will go through two stages
The first stage , Enterprises mainly adopt passive defense methods . These companies put all their energy and investment into building a strong external defense , But today these may no longer work .
Second stage , Establish a proactive security strategy . today , Everyone in the industry has realized , Network security vulnerabilities can exist in the company's network for a long time , It's hard to detect , And will continue to appear . The vulnerability that initially led to the disclosure of enterprise data may be unknown , They may exist until they are discovered . therefore , Enterprises have gradually changed from passive to active .
The transformation trend has taken shape . Enterprises begin to realize that safety protective measures should be , External defensive measures and internal defensive measures , Both are necessary . We have fully recognized the need to establish a modern security posture through targeted strategies and new investments .
The best way to protect sensitive data , That is, take the initiative to do a good job in prevention and control before the incident . Don't wait for security problems to make amends and apologies .
that , What protective measures should government and enterprise institutions take ?
1. Data encryption
Data encryption is more reliable than simple password protection . At present, data encryption is still the most reliable way for computer systems to protect information . Use password technology to encrypt information , Achieve information concealment , So as to protect the security of information . Even if the password is cracked , Irrelevant people can't get the real content , And it is impossible to copy data .
2. The Internet transmits data safely
Data encrypted transmission , Third parties cannot steal through technology and other tools 、 Tamper with protected information data , Ensure data security and integrity , Avoid data leaks 、 The occurrence of fishing and other events .
3. Internal data control
Internal leakage is one of the root causes of enterprise data leakage , Possible intentional or unintentional misconduct by internal employees , Is the key cause of data leakage .

边栏推荐
猜你喜欢
Ogre入门尝鲜
- Oui. Migration entièrement automatisée de la Sous - base de données des tableaux d'effets sous net
Smart cloud health listed: with a market value of HK $15billion, SIG Jingwei and Jingxin fund are shareholders

Lingyunguang of Dachen and Xiaomi investment is listed: the market value is 15.3 billion, and the machine is implanted into the eyes and brain

PACP学习笔记一:使用 PCAP 编程

【无标题】
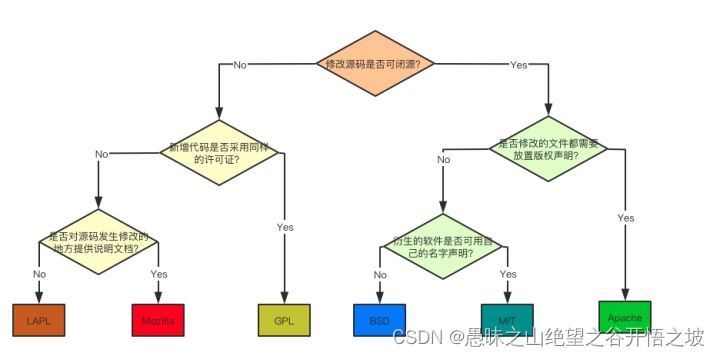
详细介绍六种开源协议(程序员须知)
Analysis of DHCP dynamic host setting protocol

Leetcode skimming: binary tree 27 (delete nodes in the binary search tree)

关于 appium 启动 app 后闪退的问题 - (已解决)
随机推荐
Go语言学习笔记-结构体(Struct)
非分区表转换成分区表以及注意事项
服务器到服务器 (S2S) 事件 (Adjust)
Aosikang biological sprint scientific innovation board of Hillhouse Investment: annual revenue of 450million yuan, lost cooperation with kangxinuo
Leetcode skimming: binary tree 20 (search in binary search tree)
Coscon'22 community convening order is coming! Open the world, invite all communities to embrace open source and open a new world~
Lingyunguang of Dachen and Xiaomi investment is listed: the market value is 15.3 billion, and the machine is implanted into the eyes and brain
谷歌浏览器如何重置?谷歌浏览器恢复默认设置?
Common text processing tools
Enterprise custom form engine solution (XII) -- experience code directory structure
解决缓存击穿问题
Sed of three swordsmen in text processing
10 张图打开 CPU 缓存一致性的大门
Awk of three swordsmen in text processing
Isprs2021/ remote sensing image cloud detection: a geographic information driven method and a new large-scale remote sensing cloud / snow detection data set
About how appium closes apps (resolved)
Leetcode brush questions: binary tree 19 (merge binary tree)
Ip2long and long2ip analysis
博文推荐|Apache Pulsar 跨地域复制方案选型实践
Smart cloud health listed: with a market value of HK $15billion, SIG Jingwei and Jingxin fund are shareholders