当前位置:网站首页>Web security - payload
Web security - payload
2022-07-06 20:14:00 【the zl】
Payload —Payload
summary : stay Web Safe learning process , It's usually mentioned that Payload The word , But what does this mean in security .
brief introduction :
Payload It can be directly translated into " Payload ", Its meaning can be understood as " Valid data ".
Payload Understand and summarize :
Analysis from the perspective of agreement : A complete data transmission process usually consists of three parts , Data headers + Raw data ( Data frame or packet + Check tail ), The data header and check tail are for the accurate transmission of original data , Then the original data is what we usually say Payload.
IPV4 Example of protocol packet structure :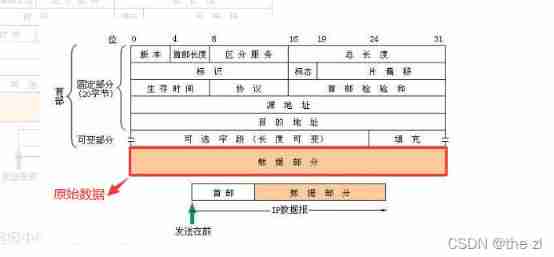
BurpSuite in Payload give an example :
DVWA In the shooting range Brute Force modular , stay BurpSuite Pick up the agent , Send to the attack module 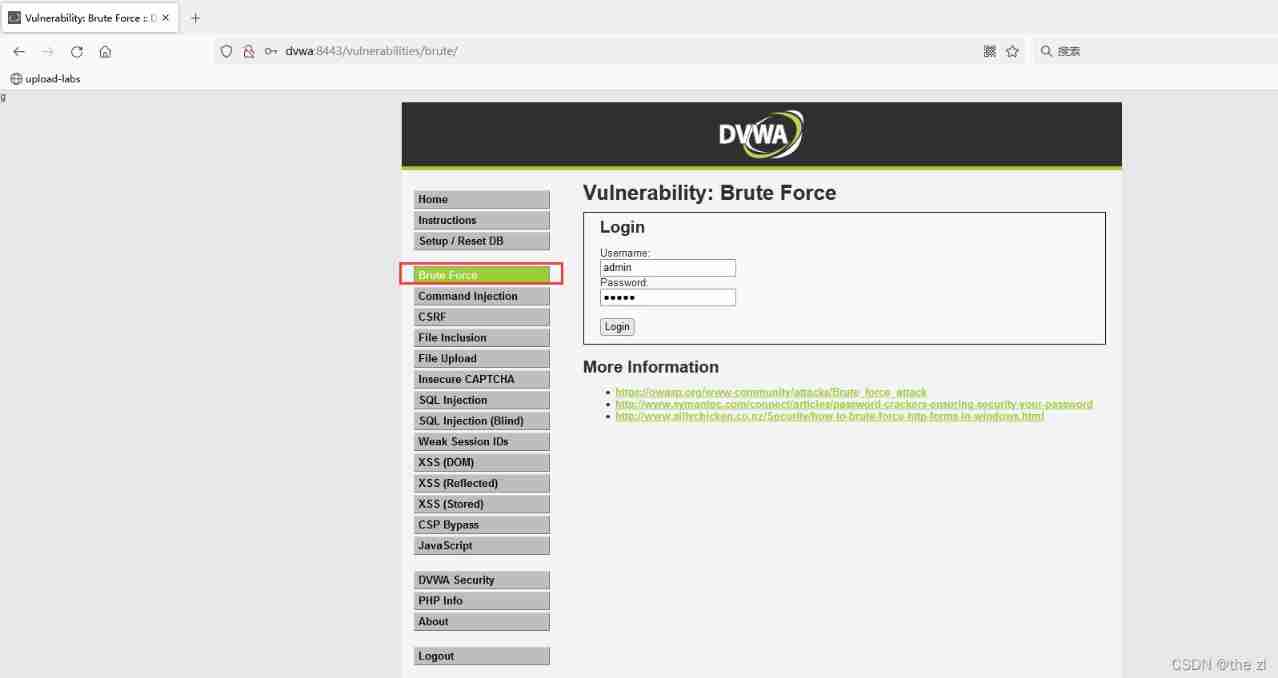
BurpSuite Marked in is HTTP The original data transmitted by the Protocol , That's what they say Payload, We can use dictionaries to construct Payload Data to achieve violent cracking attacks 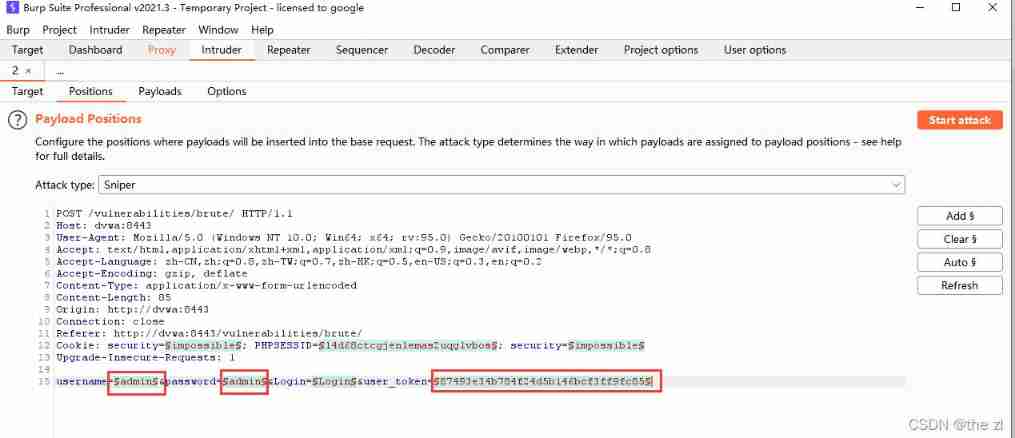
summary :
1,Payload Is the valid data in the transmission packet
2,Payload Usually modifiable , It can be used for vulnerability exploitation and detection
边栏推荐
- Logstash expressway entrance
- 腾讯T3手把手教你,真的太香了
- A5000 vGPU显示模式切换
- beegfs高可用模式探讨
- 方法关键字Deprecated,ExternalProcName,Final,ForceGenerate
- JS implementation force deduction 71 question simplified path
- Digital triangle model acwing 1018 Minimum toll
- 腾讯T4架构师,android面试基础
- 微信小程序常用集合
- Tencent byte Alibaba Xiaomi jd.com offer got a soft hand, and the teacher said it was great
猜你喜欢
B-杰哥的树(状压树形dp)
22-07-05 upload of qiniu cloud storage pictures and user avatars
02 基础入门-数据包拓展
爬虫(14) - Scrapy-Redis分布式爬虫(1) | 详解

【GET-4】
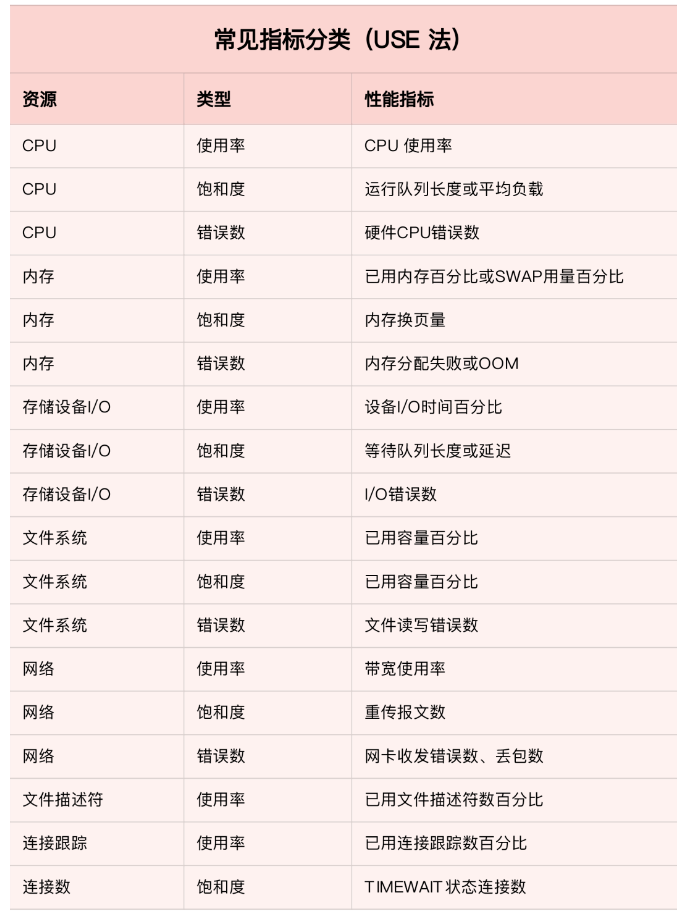
系统与应用监控的思路和方法
Continuous test (CT) practical experience sharing
Redisson bug analysis
Microservice architecture debate between radical technologists vs Project conservatives
Anaconda安裝後Jupyter launch 沒反應&網頁打開運行沒執行
随机推荐
某东短信登录复活 安装部署教程
[network planning] Chapter 3 data link layer (3) channel division medium access control
Social recruitment interview experience, 2022 latest Android high-frequency selected interview questions sharing
Learn to punch in Web
golang的超时处理使用技巧
rt-thread i2c 使用教程
报错分析~csdn反弹shell报错
HDU 1026 Ignatius and the Princess I 迷宫范围内的搜索剪枝问题
Poj3617 best cow line
腾讯架构师首发,2022Android面试笔试总结
How to handle the timeout of golang
OceanBase社区版之OBD方式部署方式单机安装
Recyclerview not call any Adapter method :onCreateViewHolder,onBindViewHolder,
JS get browser system language
腾讯字节阿里小米京东大厂Offer拿到手软,老师讲的真棒
A5000 vgpu display mode switching
系统与应用监控的思路和方法
Tencent T2 Daniel explained in person and doubled his job hopping salary
Tencent T3 teaches you hand in hand. It's really delicious
腾讯T4架构师,android面试基础