当前位置:网站首页>Sqlmap tutorial (1)
Sqlmap tutorial (1)
2022-07-05 06:06:00 【A τθ】
One 、 Introduce
Official website https://sqlmap.org/
sqlmap Is an open source penetration testing tool , It can automatically detect and utilize SQL Inject vulnerabilities and take over the database server . It has a powerful detection engine ,
Many good features and numerous operational options for ultimate penetration testing , Fingerprint from database 、 Data access to the underlying file system 、 Execute operating system commands .
Two 、 characteristic
Full support MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite,
Firebird, Sybase and SAP MaxDB Database management system .
Support six SQL Injection technology :boolean-based Blind note 、time-based Blind note 、error-based、UNION Inquire about 、 Stack query and out of band query .
By providing DBMS voucher 、IP Address 、 Port and database name , Support failed SQL Injected direct connection database .
Support enumerating users 、 Password hash 、 Privilege 、 role 、 database 、 Tables and columns .
Automatically identify password hash format , Support dictionary based attack cracking .
Support full dump of database tables , Dump entries or specific columns in a certain range according to the user's choice . The user can also choose to dump only the specified characters from each column .
Support searching specific database names 、 Table name , Or search for specific column names across tables . This is very useful , for example , Identify the tables that contain custom application credentials , It's related
The column name may contain name、pass Etc .
Support downloading and uploading any file through the file system where the database server is located , When the database software is MySQL, PostgreSQL or Microsoft SQL
server when .
It supports executing arbitrary commands and obtaining output through the operating system where the database server is located , When the database software is MySQL、PostgreSQL or Microsoft SQL
server when .
Support the establishment of out of band stateful between the attacker machine and the operating system of the database server TCP Connect , This channel can be interactive according to the user's choice
Order line 、Meterpreter Session or graphical user interface (VNC).
Supported by Metasploit Of getsystem Command to upgrade the user rights of the database process .
SQLMAP Six different injection methods supported :
B:Boolean-basedblindSQLinjection( Boolean Injection )
E:Error-basedSQLinjection( Error reporting injection )
U:UNIONquerySQLinjection( Query injection can be combined )
S:StackedqueriesSQLinjection( Multi statement query injection )
T:Time-basedblindSQLinjection( Injection based on time delay )
Q:InlineSQLInjection( Inline Injection )
3、 ... and 、 download
kali Bring their own sqlmap
git clone --depth 1 https://github.com/sqlmapproject/sqlmap.git sqlmap
to update sqlmap:
python sqlmap.py --update
Four 、 Help document
1、 Display terminal help documents
sqlmap -h
2、 Show sqlmap Detailed help documentation
sqlmap -hh
3、 Chinese help document
usage :python sqlmap.py [ Options ]
Options :
-h, --help Display basic help information and exit
-hh Display advanced help and exit
--version Display the program version information and exit
-v VERBOSE Output information detail level :0-6( The default is 1)
The goal is :
Provide at least one of the following options to specify the target
-d DIRECT Connect directly to the database
-u URL, --url=URL The goal is URL( for example :"http://www.site.com/vuln.php?id=1")
-l LOGFILE from Burp or WebScarab Resolve the target address in the agent's log file
-x SITEMAPURL From a remote site map (.xml) Parse target in file
-m BULKFILE Get batch target from text file
-r REQUESTFILE Read from file HTTP request
-g GOOGLEDORK Use Google dork Results as a goal
-c CONFIGFILE from INI Load options in configuration file
request :
The following options can specify how to connect to the destination address
--method=METHOD Force the use of the provided HTTP Method ( for example :PUT)
--data=DATA Use POST Send data string
--param-del=PARA.. Set the parameter value separator
--cookie=COOKIE Appoint HTTP Cookie
--cookie-del=COO.. Set up cookie Separator
--load-cookies=L.. Specified in Netscape/wget Format storage cookies The file of
--drop-set-cookie Ignore HTTP In response Set-Cookie Parameters
--user-agent=AGENT Appoint HTTP User-Agent
--random-agent Use random HTTP User-Agent
--host=HOST Appoint HTTP Host
--referer=REFERER Appoint HTTP Referer
-H HEADER, --hea.. Set up extra HTTP Header parameters ( for example :"X-Forwarded-For: 127.0.0.1")
--headers=HEADERS Set up extra HTTP Header parameters ( for example :"Accept-Language: fr\nETag: 123")
--auth-type=AUTH.. HTTP authentication (Basic,Digest,NTLM or PKI)
--auth-cred=AUTH.. HTTP Authentication credentials (username:password)
--auth-file=AUTH.. HTTP authentication PEM certificate / Private key file
--ignore-code=IG.. Ignore HTTP Error code ( for example :401)
--ignore-proxy Ignore the system default proxy settings
--ignore-redirects Ignore redirection attempts
--ignore-timeouts Ignore connection timeout
--proxy=PROXY Use a proxy to connect to the target URL
--proxy-cred=PRO.. Use an agent for authentication (username:password)
--proxy-file=PRO.. Load the agent list from the file
--tor Use Tor Anonymous networks
--tor-port=TORPORT Set up Tor The proxy port replaces the default port
--tor-type=TORTYPE Set up Tor Agency mode (HTTP,SOCKS4 or SOCKS5( Default ))
--check-tor Check whether the is used correctly Tor
--delay=DELAY Set each HTTP Requested delay seconds
--timeout=TIMEOUT Set the number of valid seconds for the connection response ( The default is 30)
--retries=RETRIES Number of retries when the connection timed out ( The default is 3)
--randomize=RPARAM Randomly change the given parameter value
--safe-url=SAFEURL It can be accessed frequently and legally during the test URL Address ( translator's note :
Some websites will close the session connection when you visit the wrong address several times in a row ,
hinder “ request ” The section has a detailed description )
--safe-post=SAFE.. Use POST Method to send legal data
--safe-req=SAFER.. Load legal... From file HTTP request
--safe-freq=SAFE.. Every two visits to a given legal URL Just send a test request
--skip-urlencode incorrect payload Data processing URL code
--csrf-token=CSR.. Set up a website to counter CSRF The attack token
--csrf-url=CSRFURL Specifies the extractable inverse CSRF attack token Of URL
--force-ssl Compulsory use SSL/HTTPS
--hpp Use HTTP Parameter pollution attack
--eval=EVALCODE Execute the given... Before initiating the request Python Code ( for example :
"import hashlib;id2=hashlib.md5(id).hexdigest()")
Optimize :
The following options are used to optimize sqlmap performance
-o Turn on all optimization switches
--predict-output Predict the output of common requests
--keep-alive Use persistent HTTP(S) Connect
--null-connection Only get the page size, not the actual HTTP Respond to
--threads=THREADS Set up HTTP(S) Maximum number of concurrent requests ( The default is 1)
Inject :
The following options are used to specify the parameters to be tested ,
Provide custom injection payloads And scripts that tamper with parameters
-p TESTPARAMETER Specify the parameters to be tested
--skip=SKIP Specify the parameters to skip
--skip-static Specifies to skip non dynamic parameters
--param-exclude=.. Exclude parameters with regular expressions ( for example :"ses")
--dbms=DBMS Appoint DBMS type ( for example :MySQL)
--dbms-cred=DBMS.. DBMS Authentication credentials (username:password)
--os=OS Appoint DBMS The operating system type of the server
--invalid-bignum Set invalid value to a large number
--invalid-logical Use logical operations on invalid values
--invalid-string Use a random string for invalid values
--no-cast close payload Structural mechanism
--no-escape Turn off the string escape mechanism
--prefix=PREFIX Inject payload Prefix string
--suffix=SUFFIX Inject payload Suffix string
--tamper=TAMPER Modify the injected data with the given script
testing :
The following options are used to customize the detection method
--level=LEVEL Set the test level (1-5, The default is 1)
--risk=RISK Set the test risk level (1-3, The default is 1)
--string=STRING String used to determine when the query result is true
--not-string=NOT.. Used to determine the string when the query result is false
--regexp=REGEXP Regular expression used to determine when the query result is true
--code=CODE Used to determine when the query result is true HTTP Status code
--text-only Compare pages only according to the text content of the page
--titles Compare pages only according to the page title
technology :
The following options are used to adjust specific parameters SQL Test method of injection technology
--technique=TECH The use of SQL Injection technology ( The default is “BEUSTQ”, translator's note :
B: Boolean-based blind SQL injection( Boolean blind note )
E: Error-based SQL injection( Error reporting injection )
U: UNION query SQL injection( Joint query injection )
S: Stacked queries SQL injection( Heap query injection )
T: Time-based blind SQL injection( Time blind injection )
Q: inline Query injection( Inline query injection )
--time-sec=TIMESEC Delay DBMS Number of seconds of response ( The default is 5)
--union-cols=UCOLS Set the range of columns for the joint query injection test
--union-char=UCHAR Characters used to guess the number of splits
--union-from=UFROM Set joint query injection FROM Table used at
--dns-domain=DNS.. Setting is used for DNS The domain name of the exudation attack ( translator's note :
Recommended reading 《 stay SQL Use in injection DNS get data 》
http://cb.drops.wiki/drops/tips-5283.html,
In the rear “ technology ” There are corresponding explanations in the section )
--second-order=S.. Set the result display page of the second-order response URL( translator's note :
This option is used for second order SQL Inject )
fingerprint identification :
-f, --fingerprint Carry out extensive DBMS Version fingerprint identification
enumeration :
The following options are used to obtain the information of the back-end database management system , Structure and data in the data table .
Besides , You can also run the SQL sentence
-a, --all Get all the information 、 data
-b, --banner obtain DBMS banner
--current-user obtain DBMS The current user
--current-db obtain DBMS Current database
--hostname obtain DBMS The hostname of the server
--is-dba Probe DBMS Whether the current user is DBA( Database administrator )
--users List DBMS All users
--passwords List DBMS Password hashes for all users
--privileges List DBMS All user privilege levels
--roles List DBMS All user roles
--dbs List DBMS All databases
--tables List DBMS All the tables in the database
--columns List DBMS All the columns in the table
--schema List DBMS All modes
--count Get the number of data tables
--dump export DBMS Database table entries
--dump-all Export all DBMS Database table entries
--search Search column , Table and / Or database name
--comments obtain DBMS notes
-D DB Specify the to enumerate DBMS database
-T TBL Specify the to enumerate DBMS Data sheet
-C COL Specify the to enumerate DBMS Data columns
-X EXCLUDECOL Specify the to exclude DBMS Data columns
-U USER Specifies the of the enumeration DBMS user
--exclude-sysdbs When enumerating all data tables , Specifies to exclude specific system databases
--pivot-column=P.. Specify the primary column
--where=DUMPWHERE Use... When dumping tables WHERE Conditional statements
--start=LIMITSTART Specify the number of starting rows of data table entries to export
--stop=LIMITSTOP Specify the number of end rows of data table entries to export
--first=FIRSTCHAR Specifies the starting character bit of the returned query result
--last=LASTCHAR Specifies the end character bit of the returned query result
--sql-query=QUERY Specifies which to execute SQL sentence
--sql-shell Call up interactive SQL shell
--sql-file=SQLFILE Execute the SQL sentence
Brute force :
The following options are used for brute force testing
--common-tables Check whether common table names exist
--common-columns Check whether the commonly used column names exist
User defined function Injection :
The following options are used to create user-defined functions
--udf-inject Injection of user-defined functions
--shared-lib=SHLIB The local path to the shared library
Accessing the file system :
The following options are used to access the underlying file system of the back-end database management system
--file-read=RFILE Read the backend DBMS Files in the file system
--file-write=WFILE Write back end DBMS Files in the file system
--file-dest=DFILE Use the absolute path of the file to write to the back end DBMS
Access the operating system :
The following options are used to access the underlying operating system of the back-end database management system
--os-cmd=OSCMD Execute operating system commands
--os-shell Call up the interactive operating system shell
--os-pwn Call out OOB shell,Meterpreter or VNC
--os-smbrelay One key call up OOB shell,Meterpreter or VNC
--os-bof Using the buffer overflow of stored procedure
--priv-esc Database process user authorization
--msf-path=MSFPATH Metasploit The local installation path of the framework
--tmp-path=TMPPATH The absolute path to the remote temporary file directory
visit Windows The registry :
The following options are used to access the back-end database management system Windows The registry
--reg-read Read a Windows Registry key
--reg-add Write a Windows Registry key data
--reg-del Delete one Windows Registry key
--reg-key=REGKEY Appoint Windows Registry key
--reg-value=REGVAL Appoint Windows Registry key
--reg-data=REGDATA Appoint Windows Registry key data
--reg-type=REGTYPE Appoint Windows Registry key type
General options :
The following options are used to set general parameters
-s SESSIONFILE From file (.sqlite) Read session information in
-t TRAFFICFILE Save all HTTP Record the traffic to the specified text file
--batch Never ask for user input , Use default configuration
--binary-fields=.. Result field with binary value ( for example :"digest")
--check-internet Check whether you are connected to the Internet properly before accessing the target
--crawl=CRAWLDEPTH From the target URL Start crawling the website
--crawl-exclude=.. Filter crawled pages with regular expressions ( for example :"logout")
--csv-del=CSVDEL Specify output to CVS The separator used in the file ( The default is “,”)
--charset=CHARSET Appoint SQL Blind annotation character set ( for example :"0123456789abcdef")
--dump-format=DU.. Format of exported data (CSV( Default ),HTML or SQLITE)
--encoding=ENCOD.. Specifies the character encoding to use when getting data ( for example :GBK)
--eta Displays the estimated arrival time of each result output
--flush-session Clear the session file of the current target
--forms Parse and test the target URL Form for
--fresh-queries Ignore the query results stored in the session file
--har=HARFILE Will all HTTP The flow is recorded to a HAR In file
--hex Call... When getting data DBMS Of hex function
--output-dir=OUT.. Custom output directory path
--parse-errors Parse and display from response DBMS error message
--save=SAVECONFIG Save the option settings to a INI The configuration file
--scope=SCOPE Filter targets from the provided agent logs with regular expressions
--test-filter=TE.. according to payloads and / Or title ( for example :ROW) Choose a test
--test-skip=TEST.. according to payloads and / Or title ( for example :BENCHMARK) Skip some tests
--update to update sqlmap
The other options :
-z MNEMONICS Use short mnemonics ( for example :“flu,bat,ban,tec=EU”)
--alert=ALERT Find SQL Run during injection OS command
--answers=ANSWERS Set the answer to the question ( for example :“quit=N,follow=N”)
--beep Remind of problems or find SQL A prompt tone is given during injection
--cleanup Specify removal DBMS Specific in UDF Or data tables
--dependencies Check sqlmap What's missing ( Non core ) rely on
--disable-coloring Turn off the color console output
--gpage=GOOGLEPAGE Specify the page number to use Google dork result
--identify-waf in the light of WAF/IPS/IDS Protection is thoroughly tested
--mobile Use HTTP User-Agent Imitate smart phones
--offline Working in offline mode ( Use session data only )
--purge-output Safely delete all contents of the output directory
--skip-waf Skip heuristic detection WAF/IPS/IDS Protect
--smart Only when heuristic detection is used, do thorough testing
--sqlmap-shell Call up interactive sqlmap shell
--tmp-dir=TMPDIR Specify the local directory where temporary files are stored
--web-root=WEBROOT Appoint Web Server root ( for example :"/var/www")
--wizard Wizard interface suitable for junior users
5、 ... and 、 Common command
1、-u、-v Parameters
sqlmap -u "http://192.168.1.50/06/vul/sqli/sqli_str.php?name=1&submit=1" -v 1
-u and --url Same parameter , They are all representatives who fill in the test url Connect , If there is & Symbol , Need to add url Put it in double quotation marks .
-v Indicates the level of detail of the output information :0-6( The default is 1)
0: Display only Python Back to the source (tracebacks), error (error) And key (criticle) Information .
1: Display information at the same time (info) And warning messages (warning)( The default is 1)
2: Debugging information is displayed at the same time (debug)
3: At the same time, the injected payload (payloads)
4: Show at the same time http request
5: Show at the same time http Response head
6: Show at the same time http Response content
The higher the level , The more detailed the information is , Choose the appropriate output information according to your needs .
2、 Designated target
1、 Designate a url To test :
sqlmap -u http://sqlmap.com/index.php?id=1 -v 1
2、 Load from file http Request test :
sqlmap -r url.txt
3、 Get multiple target scans from text :
sqlmap -m url.txt
url.txt:
http://www.moonsec.com/index.php?id=1
http://www.moonsec.com/new.php?id=1
http://www.moonsec.com/awd.php?id=1
3、 request
http data
1、 Parameters --data
This parameter sets the data as post Mode submission ,sqlmap It will automatically detect post Parameters .
sqlmap -u "http://192.168.0.103/06/vul/sqli/sqli_id.php" --data="id=1&submit=1"

Parameters :--param-del
When GET or POST When the data needs to be segmented with other characters to test parameters , This parameter is required .
sqlmap -u "http://www.target.com/vuln.php" --data="query=foobar;id=1" --param-del=";" --dbs --users
边栏推荐
- leetcode-6108:解密消息
- Codeforces Round #716 (Div. 2) D. Cut and Stick
- 【云原生】微服务之Feign自定义配置的记录
- js快速将json数据转换为url参数
- Overview of variable resistors - structure, operation and different applications
- Dynamic planning solution ideas and summary (30000 words)
- [practical skills] technical management of managers with non-technical background
- Cluster script of data warehouse project
- Convolution neural network -- convolution layer
- [jailhouse article] performance measurements for hypervisors on embedded ARM processors
猜你喜欢

SQLMAP使用教程(一)
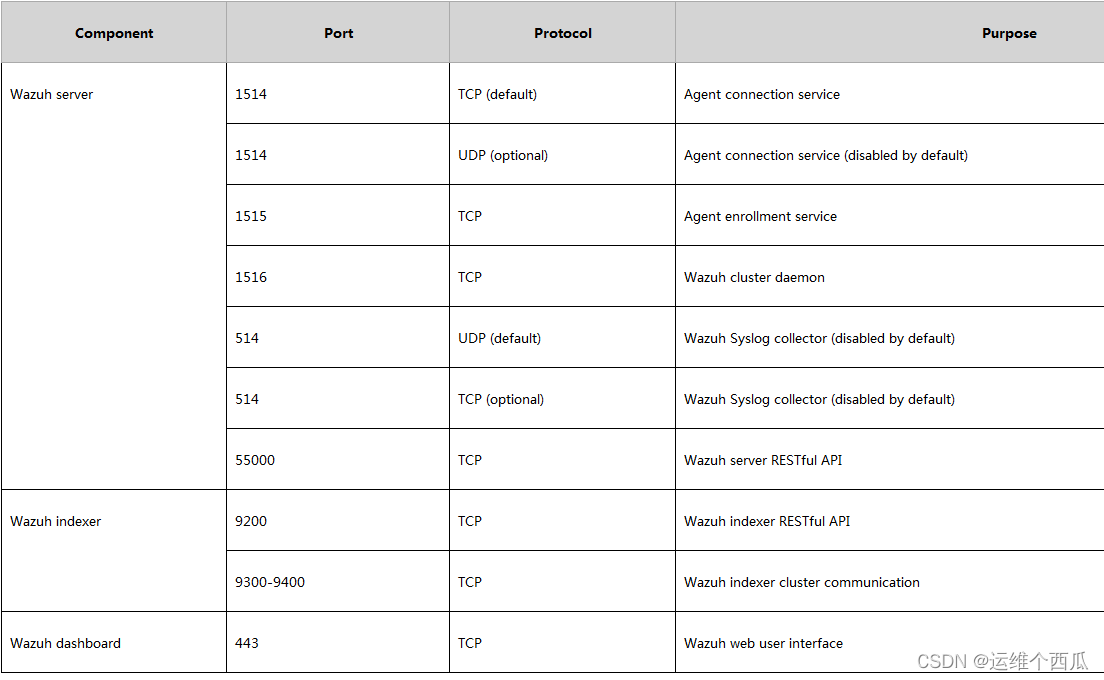
Introduction and experience of wazuh open source host security solution
Implement a fixed capacity stack

个人开发的渗透测试工具Satania v1.2更新
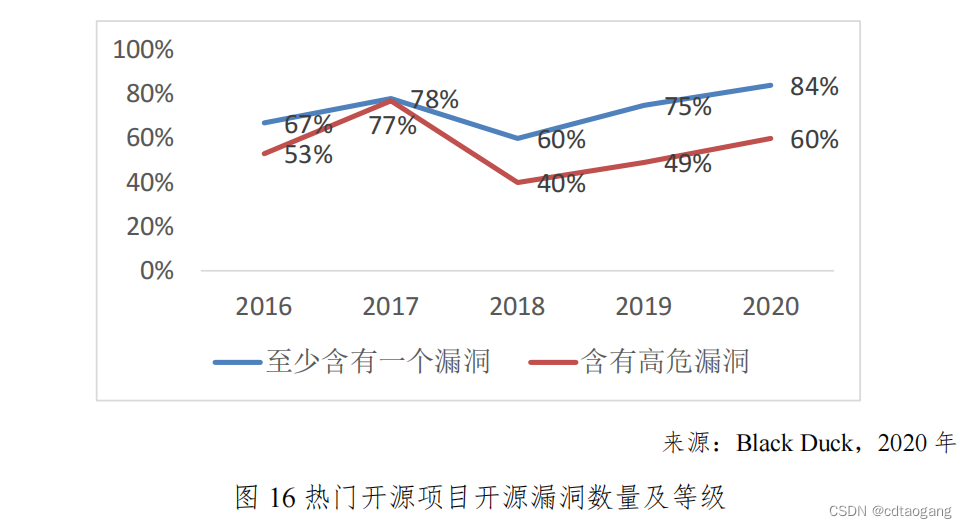
开源存储这么香,为何我们还要坚持自研?
Analysis of backdoor vulnerability in remote code execution penetration test / / phpstudy of national game title of national secondary vocational network security B module
On the characteristics of technology entrepreneurs from Dijkstra's Turing Award speech

Educational Codeforces Round 116 (Rated for Div. 2) E. Arena
![[jailhouse article] performance measurements for hypervisors on embedded ARM processors](/img/c0/4843f887f77b80e3b2329e12d28987.png)
[jailhouse article] performance measurements for hypervisors on embedded ARM processors
RGB LED infinite mirror controlled by Arduino
随机推荐
The connection and solution between the shortest Hamilton path and the traveling salesman problem
AtCoder Grand Contest 013 E - Placing Squares
One question per day 1765 The highest point in the map
Implement an iterative stack
【Rust 笔记】16-输入与输出(上)
【Jailhouse 文章】Jailhouse Hypervisor
剑指 Offer II 058:日程表
LaMDA 不可能觉醒吗?
Daily question 1342 Number of operations to change the number to 0
A reason that is easy to be ignored when the printer is offline
【Rust 笔记】14-集合(下)
Light a light with stm32
F - Two Exam(AtCoder Beginner Contest 238)
SQLMAP使用教程(一)
[jailhouse article] look mum, no VM exits
PC register
MatrixDB v4.5.0 重磅发布,全新推出 MARS2 存储引擎!
SPI 详解
Sword finger offer 05 Replace spaces
Some common problems in the assessment of network engineers: WLAN, BGP, switch