边栏推荐
- Configuration du cadre flask loguru log Library
- Some problems encountered in installing pytorch in windows11 CONDA
- Gartner:关于零信任网络访问最佳实践的五个建议
- 渗透测试 ( 5 ) --- 扫描之王 nmap、渗透测试工具实战技巧合集
- Sword finger offer II 019 Delete at most one character to get a palindrome
- Penetration test (7) -- vulnerability scanning tool Nessus
- QT模拟鼠标事件,实现点击双击移动拖拽等
- Luogu P1102 A-B number pair (dichotomy, map, double pointer)
- CEP used by Flink
- Suffix expression (greed + thinking)
猜你喜欢

1529. Minimum number of suffix flips

2027. Minimum number of operations to convert strings
Flask框架配置loguru日志庫
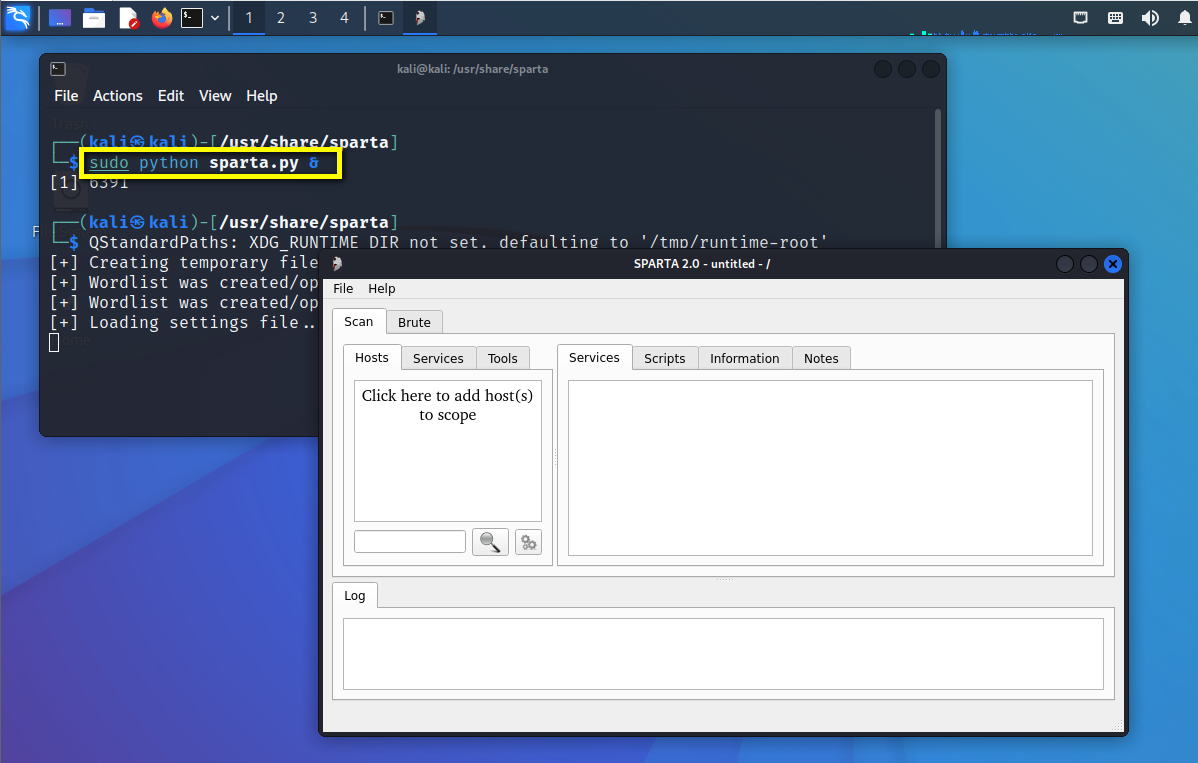
Penetration test (1) -- necessary tools, navigation
渗透测试 ( 3 ) --- Metasploit Framework ( MSF )

Openwrt source code generation image

C language must memorize code Encyclopedia
C language is the watershed between low-level and high-level

1689. Ten - the minimum number of binary numbers
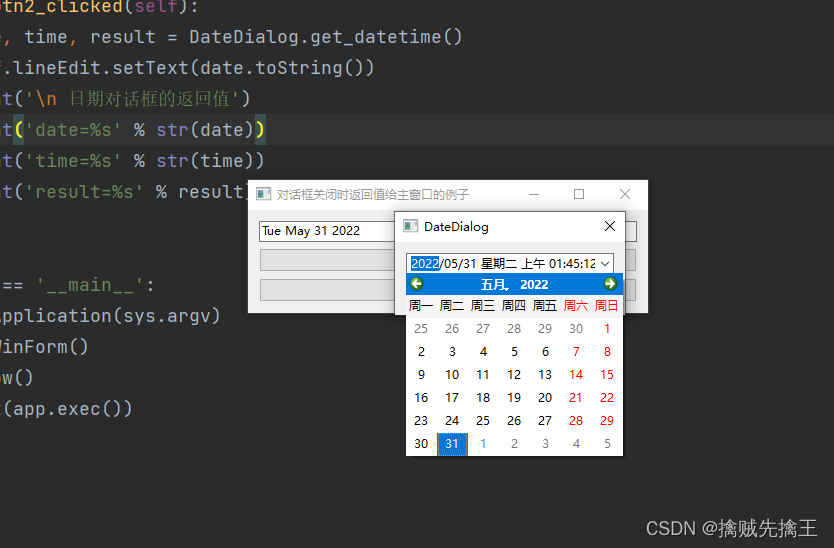
Pyside6 signal, slot
随机推荐
605. Planting flowers
MySQL import database error [err] 1273 - unknown collation: 'utf8mb4_ 0900_ ai_ ci’
双向链表—全部操作
HDU - 6024 building shops (girls' competition)
[analysis of teacher Gao's software needs] collection of exercises and answers for level 20 cloud class
Opencv learning log 28 -- detect the red cup cover
渗透测试 ( 8 ) --- Burp Suite Pro 官方文档
If you want to apply for a programmer, your resume should be written like this [essence summary]
【练习-7】(Uva 10976)Fractions Again?!(分数拆分)
Socket communication
C language learning notes
【练习-10】 Unread Messages(未读消息)
(POJ - 3258) River hopper (two points)
1323. Maximum number of 6 and 9
Write web games in C language
Pyside6 signal, slot
读取和保存zarr文件
Penetration test (8) -- official document of burp Suite Pro
Information security - threat detection - detailed design of NAT log access threat detection platform
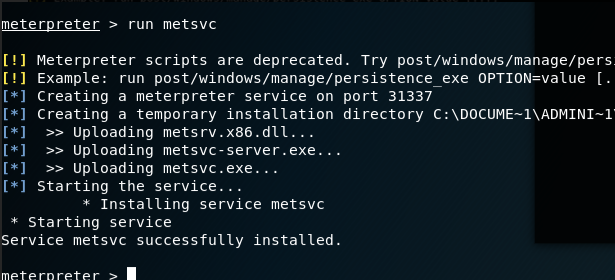
Penetration test (4) -- detailed explanation of meterpreter command