当前位置:网站首页>409. Longest palindrome
409. Longest palindrome
2022-07-06 16:08:00 【mrbone9】
Address :
Power button  https://leetcode-cn.com/problems/longest-palindrome/
https://leetcode-cn.com/problems/longest-palindrome/
subject :
Given a string of uppercase and lowercase letters s , return Constructed from these letters The longest palindrome string .
In the process of construction , Please note that Case sensitive . such as "Aa" Can't be treated as a palindrome string .
Example 1:
| Input :s = "abccccdd" Output :7 explain : The longest palindrome string we can construct is "dccaccd", Its length is 7. |
Example 2:
| Input :s = "a" Input :1 |
Example 3:
| Input :s = "bb" Input : 2 |
Tips :
| 1 <= s.length <= 2000 s Only lowercase and / Or capital letters |
source : Power button (LeetCode)
link :https://leetcode-cn.com/problems/longest-palindrome
Copyright belongs to the network . For commercial reprint, please contact the official authority , Non-commercial reprint please indicate the source .
Ideas :
Palindromes mean pairs , Even number , As for whether there is an odd number in the middle , All palindromes
So we use the idea of counting arrays to complete
Count array can refer to :
Counting sorting of sorting algorithm
Method 1 、 Count array
int longestPalindrome(char * s){
int count[58]={0};
int cnt = 0;
int odd = 0;
int i = 0;
while(s[i])
{
int idx = s[i] - 'A';
//printf("s[%d]=%d, idx=%d\n", i, s[i], idx);
count[idx]++;
i++;
}
for(i=0; i<58; i++)
{
if(count[i] != 0)
{
if(count[i] & 1)
odd = 1;
cnt += count[i] / 2;
}
}
cnt *= 2;
if(odd == 1)
cnt++;
return cnt;
}边栏推荐
- 【高老师软件需求分析】20级云班课习题答案合集
- STM32 how to use stlink download program: light LED running light (Library version)
- 【练习-10】 Unread Messages(未读消息)
- HDU-6025-Coprime Sequence(女生赛)
- Alice and Bob (2021 Niuke summer multi school training camp 1)
- D - function (HDU - 6546) girls' competition
- MySQL grants the user the operation permission of the specified content
- Find 3-friendly Integers
- Opencv learning log 27 -- chip positioning
- Alice and Bob (2021牛客暑期多校训练营1)
猜你喜欢
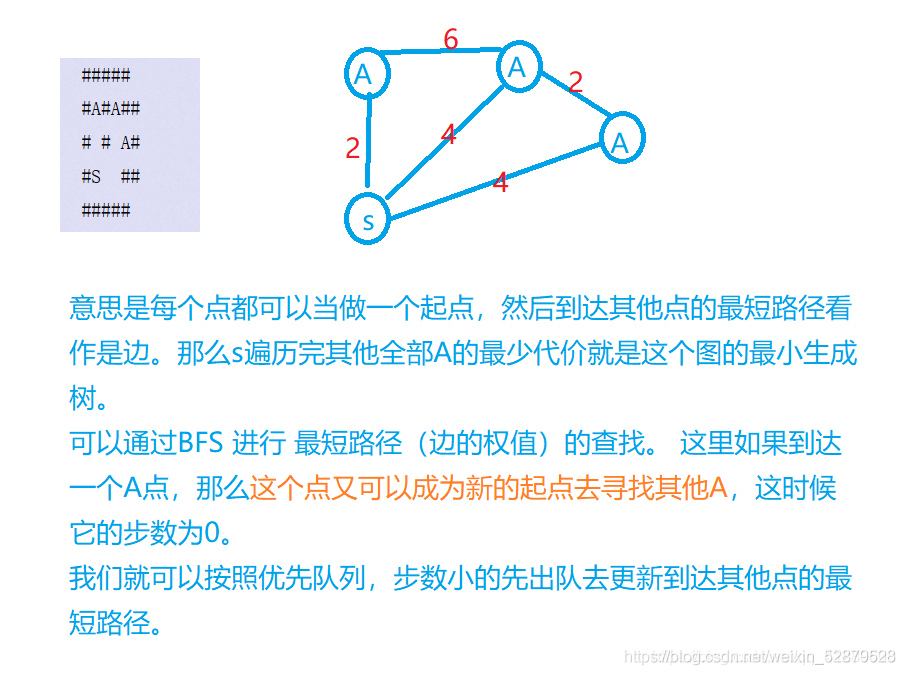
Borg maze (bfs+ minimum spanning tree) (problem solving report)
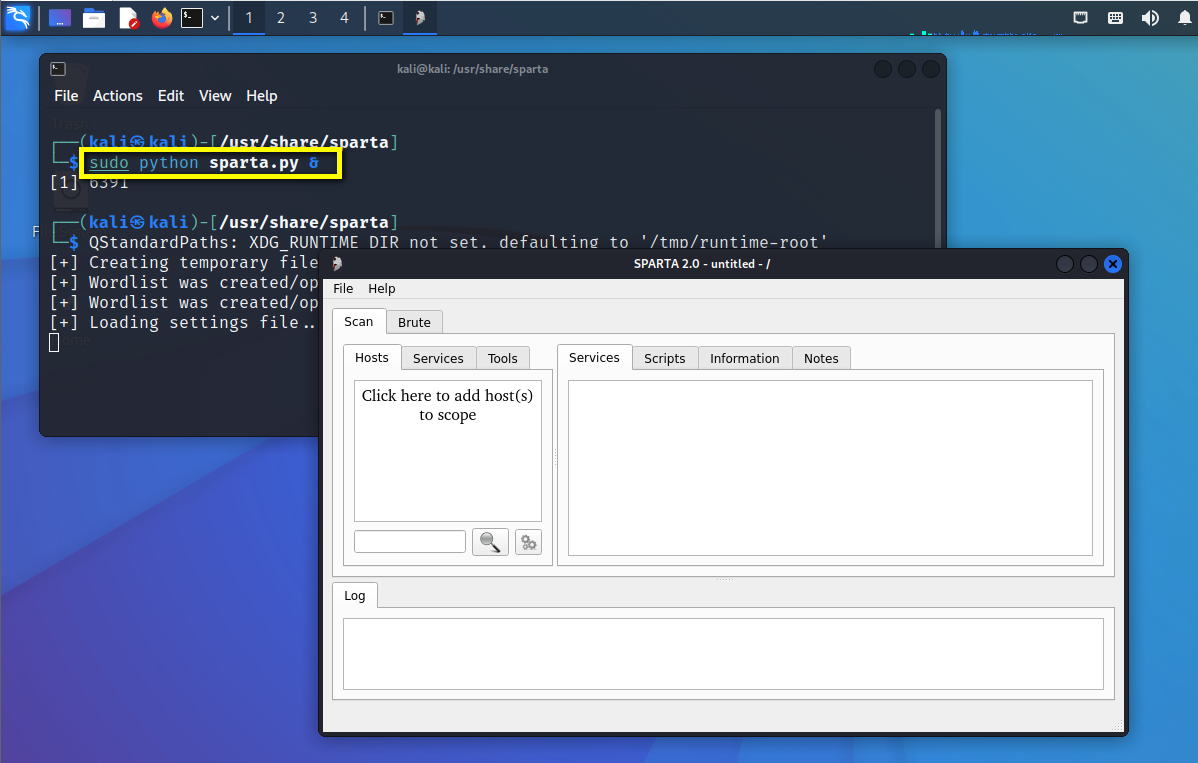
Essai de pénétration (1) - - outils nécessaires, navigation
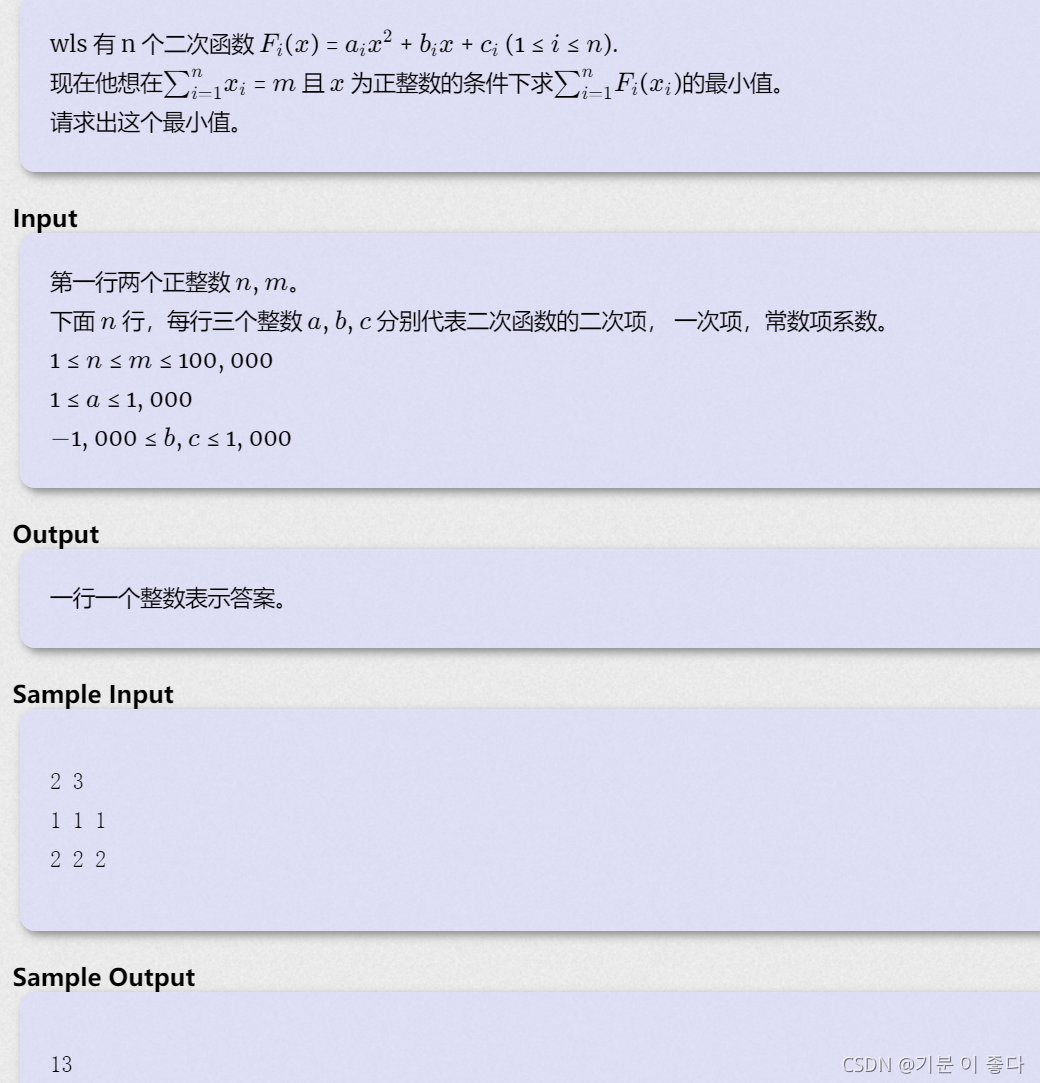
D - Function(HDU - 6546)女生赛

The concept of C language array

STM32 how to use stlink download program: light LED running light (Library version)
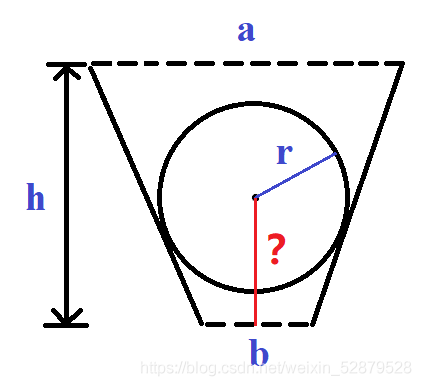
Ball Dropping
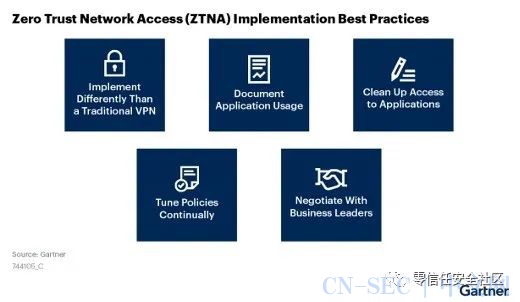
Gartner:关于零信任网络访问最佳实践的五个建议
![[teacher Gao UML software modeling foundation] collection of exercises and answers for level 20 cloud class](/img/57/bc6eda91f7263acda38b9ee8732318.png)
[teacher Gao UML software modeling foundation] collection of exercises and answers for level 20 cloud class

1903. Maximum odd number in string
Analysis of protobuf format of real-time barrage and historical barrage at station B
随机推荐
[exercise -11] 4 values why sum is 0 (and 4 values of 0)
Information security - Analysis of security orchestration automation and response (soar) technology
渗透测试 ( 1 ) --- 必备 工具、导航
Shell Scripting
Opencv learning log 29 -- gamma correction
【练习-6】(PTA)分而治之
Penetration test (7) -- vulnerability scanning tool Nessus
What is the difficulty of programming?
[exercise -10] unread messages
【练习4-1】Cake Distribution(分配蛋糕)
F - birthday cake (Shandong race)
PySide6 信号、槽
Penetration test (8) -- official document of burp Suite Pro
STM32 how to use stlink download program: light LED running light (Library version)
渗透测试 ( 7 ) --- 漏洞扫描工具 Nessus
Penetration test (3) -- Metasploit framework (MSF)
[analysis of teacher Gao's software needs] collection of exercises and answers for level 20 cloud class
[teacher Gao UML software modeling foundation] collection of exercises and answers for level 20 cloud class
Gartner:关于零信任网络访问最佳实践的五个建议
Opencv learning log 12 binarization of Otsu method