当前位置:网站首页>[reverse intermediate] eager to try
[reverse intermediate] eager to try
2022-07-06 17:23:00 【TiggerRun】
Eager to
stem
After downloading , Title said to find Serial
Let me use it first. PEiD Check the shell , See if it's an executable , It is found that it is an executable file with a shell .
Then I changed the suffix to exe, Find that you can open .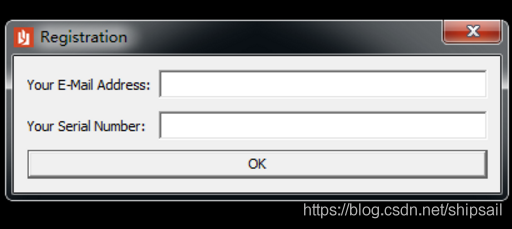
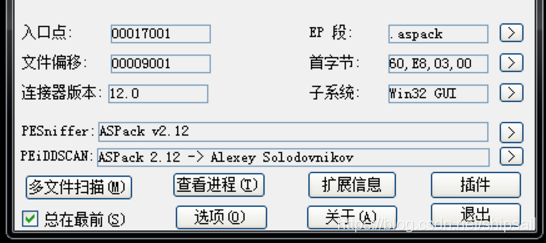
0x1 Shelling
This question is classified in intermediate , Because at the beginning, I did a program to analyze the registration code by debugging the encryption algorithm , I think this problem is to get rid of the shell first .
OD Pause after loading pushad, Save register state 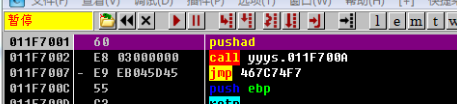
I use esp Law + HR The breakpoint , To trace popad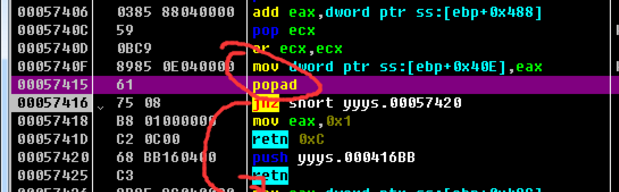
But it's strange , This shell retn To a CALL, And then go into this CALL After that is push ebp Wait for the operation , I guess CALL What's inside is OEP, The use of plug-in Dump After the program runs, an error is reported , Checked the information and said it was repaired IAT, I downloaded it again importREC, Finally, I know by querying the information win7 Not suitable for shelling , Need to install XP virtual machine , I didn't continue shelling .
This process will occur after the subsequent shelling is successful , This shell should have other protective treatments .
0x2 OD debugging
I just type in an email , Casually enter the following SerialNumber, Then click OK
Through the last registration machine learning , I used API The breakpoint , Because at last, a message box appears , I ctrl + G Came to MessageBoxA The function header of , Put a common breakpoint on its function header .
Then click OK again , Through the stack, you can return to the call MessageBoxA Code snippet of function
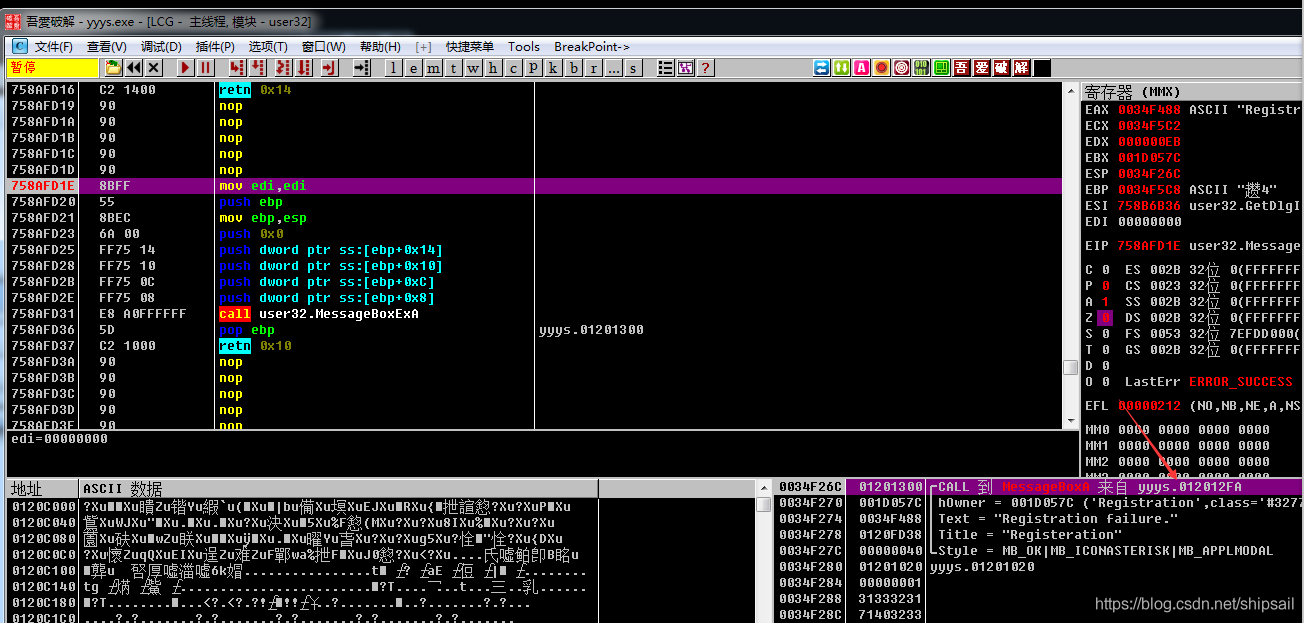
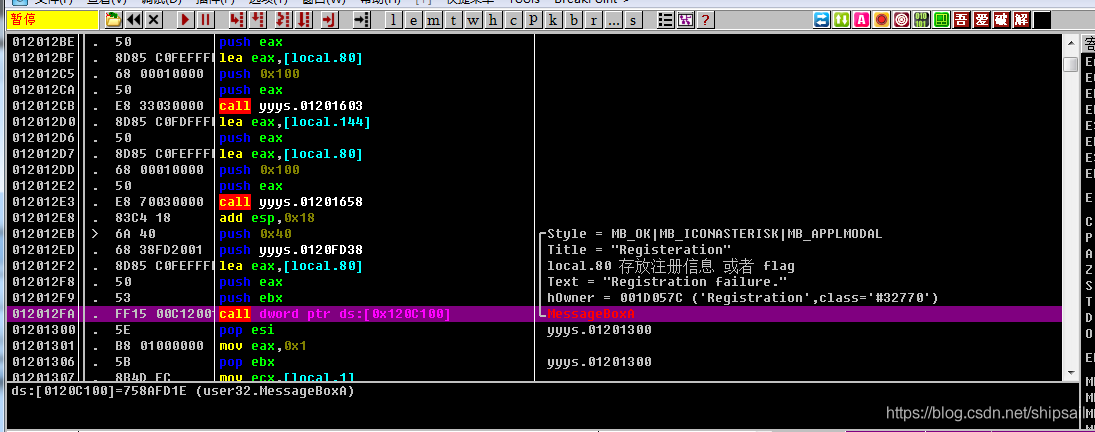
So follow up yyyx Module
Then we analyze where these parameters come from 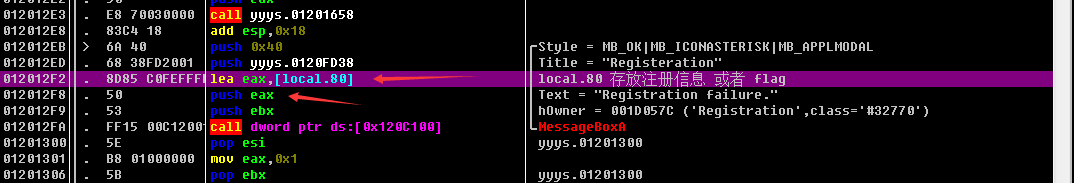
Among them, the 4 Parameters , Among them eax It's the information box text Content , come from lecal.80
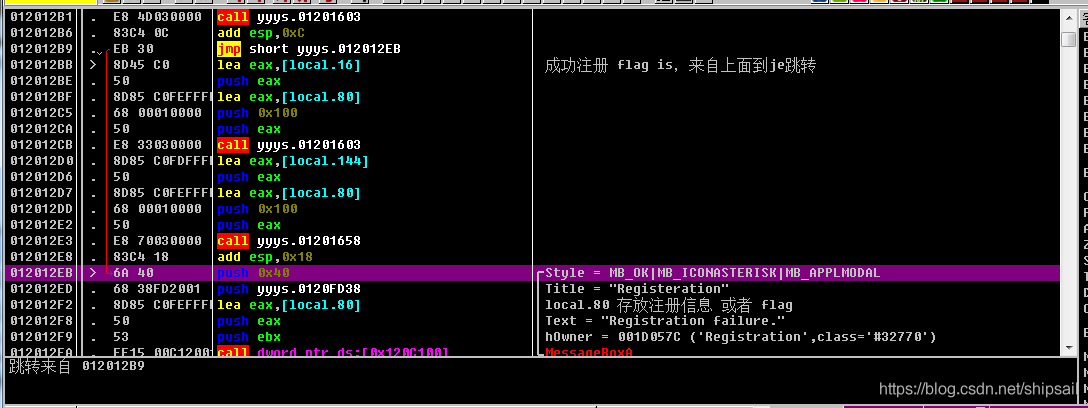
Then analyze it upwards , Where did you jump from
There is a jmp Go directly to this message box to prompt , Skipped the middle piece of code , Then I went to check what was skipped in the middle of the code
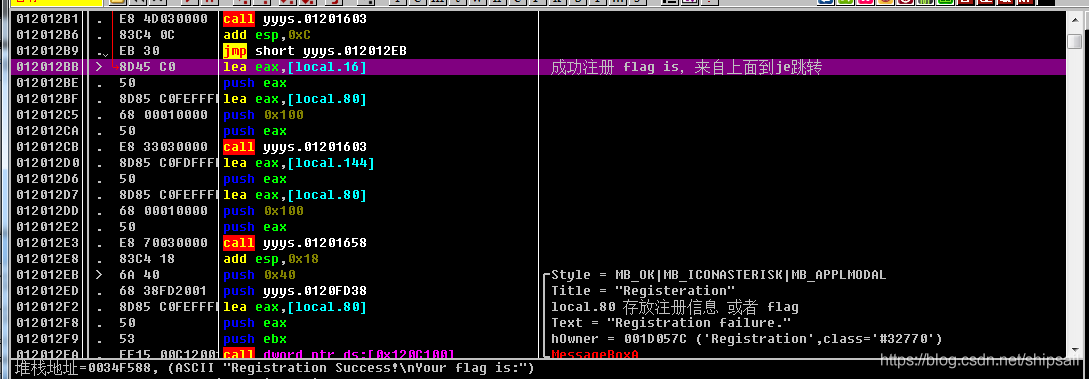
local.16 Deposited Success The prompt text of , It shows that this code is likely to be the code successfully executed by registration , Then execute the above line from top to bottom jmp, This jmp Directly jump to the pop-up message box , It shows that this code is not executed in sequence , It's a jump from an address , adopt OD Find this jump on the Internet .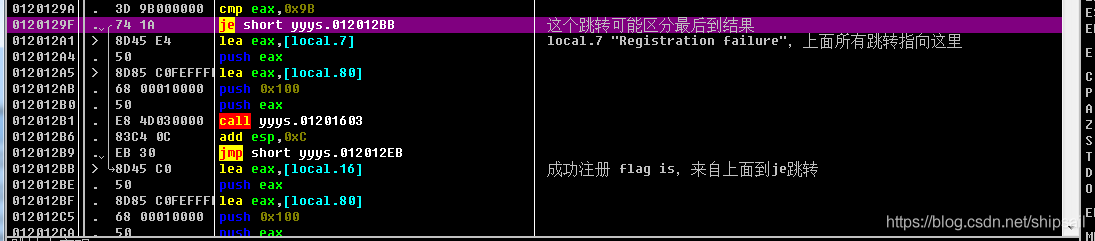
Find this jump je, If jump is not realized ,lea eax,[local.7],local.7 Stored in Registration Failure, Then proceed push Pressing the stack calls the following one CALL, Then jump directly to the pop-up message box , This code is used to handle registration failure .
Position the cursor on this line of code , Found from many addresses 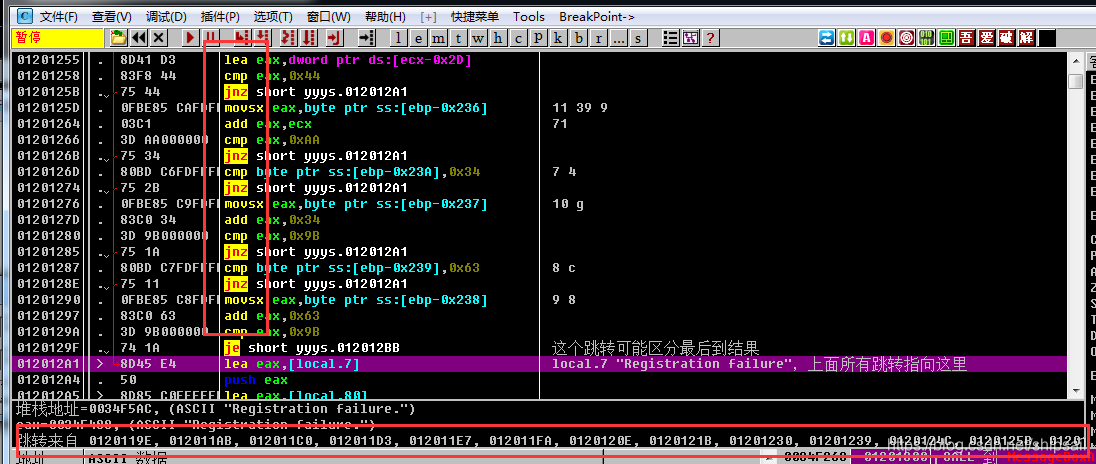
This shows that , The above is the verified Algorithm , There is a large jnz
JNZ : jump if not zero If the result is not zero, then transfer
Then I pull up , See two GetDialogText function 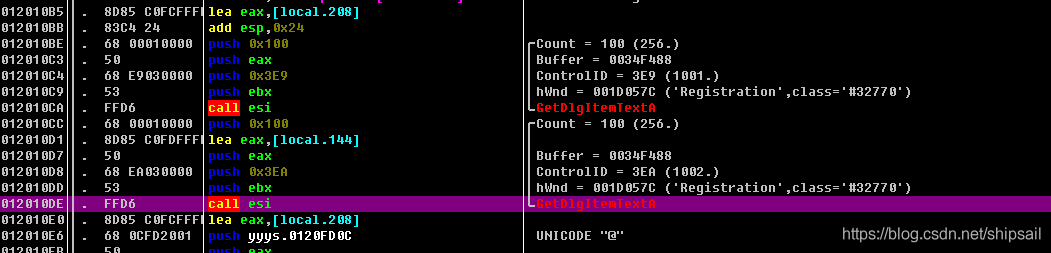
Verify that the content in the edit box is taken out through the breakpoint
We found the beginning of the program processing events , Then we can make a positive analysis 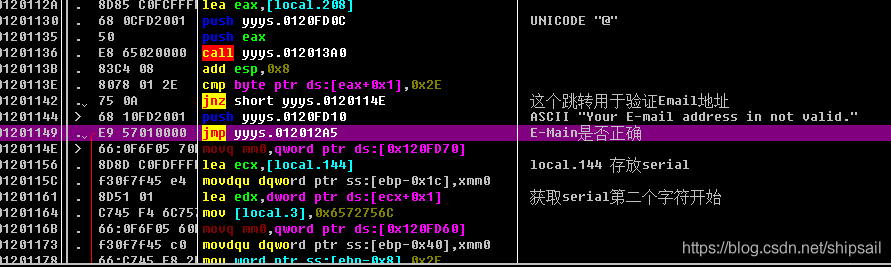
I found this jmp The span is very large , Directly jump to the previous analysis 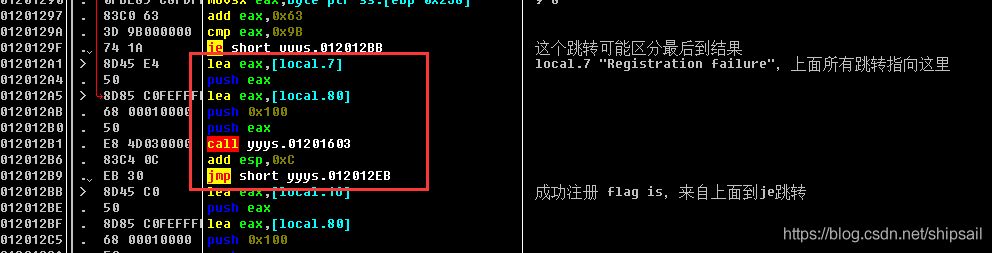
Where error events are handled .
And the one above ASCII Written in the string “E-mail address is not valid” The email address cannot be verified , Explain the previous several CALL Is doing the correct judgment of the format of the email address .
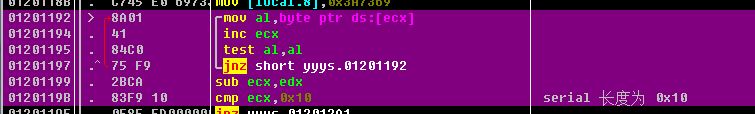
This piece of code needs to be pondered , This function is to take the length of the string , The method is different from that of the last topic , The last topic passed scas Traversal string , Then the register decrements and reverses + 1
Here is the incremental address , Get the address of the terminator and subtract the first address to calculate the length
Through this cmp and jnz You can know ,serial The length of is 0x10 namely 16 position
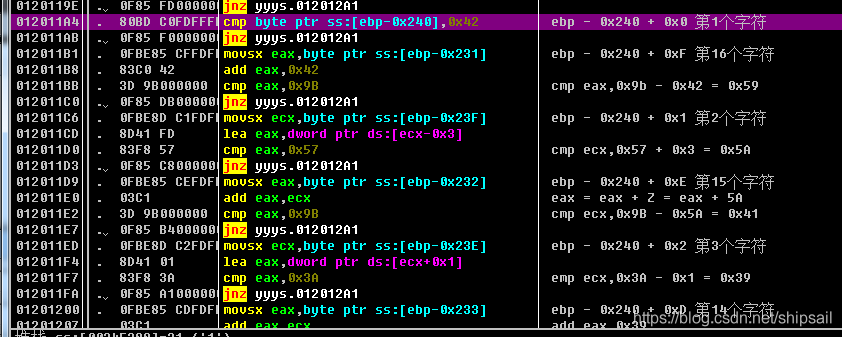
And then some in the back jnz I think it's quite stupid , It should be put in the elementary question …
Last serial Is a static value 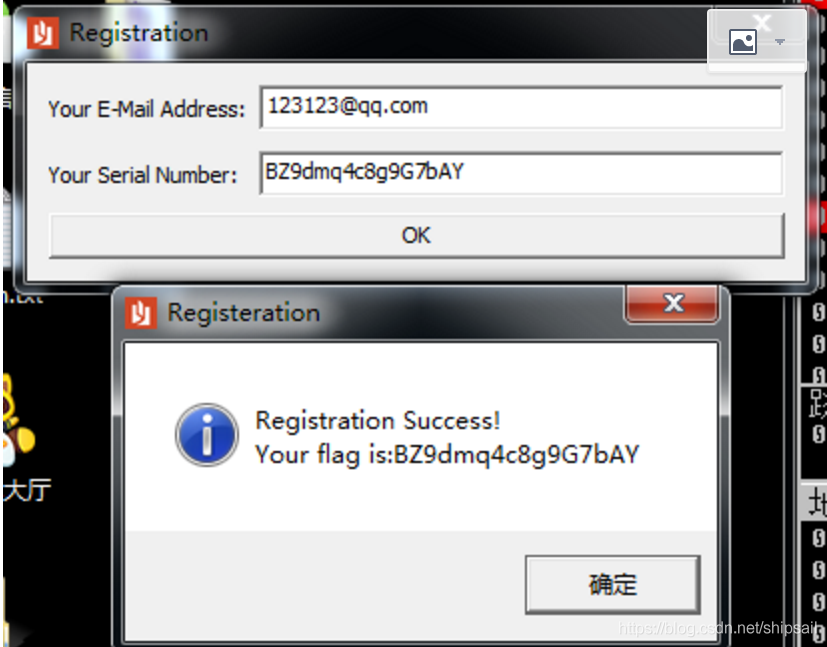
0x3 New knowledge
- Calculate the string length by increasing the address
- ASPack Stack method Shelling
- importREC IAT Repair tools
- LordPE Dump Tools
- Files without suffix can pass PEiD Check the following EP
边栏推荐
- C#版Selenium操作Chrome全屏模式显示(F11)
- mysql 基本增删改查SQL语句
- GCC error: terminate called after throwing an instance of 'std:: regex_ error‘ what(): regex
- arithmetic operation
- Set up the flutter environment pit collection
- CTF逆向入门题——掷骰子
- ByteDance overseas technical team won the championship again: HD video coding has won the first place in 17 items
- Programmer orientation problem solving methodology
- Shawshank's sense of redemption
- Wu Jun trilogy insight (IV) everyone's wisdom
猜你喜欢
Flink源码解读(二):JobGraph源码解读

Wu Jun's trilogy insight (V) refusing fake workers
MySQL optimization notes
Akamai浅谈风控原理与解决方案
TCP's three handshakes and four waves
The daemon thread starts redis and modifies the configuration file
汇编课后作业
Install docker under windows10 (through Oracle VM VirtualBox)
Resume of a microservice architecture teacher with 10 years of work experience
February database ranking: how long can Oracle remain the first?
随机推荐
Assembly language segment definition
Instructions for Redux
控制转移指令
Jetpack compose 1.1 release, based on kotlin's Android UI Toolkit
吴军三部曲见识(四) 大家智慧
信息与网络安全期末复习(完整版)
In the command mode in the VI editor, delete the character usage at the current cursor__ Command.
C# WinForm中DataGridView单元格显示图片
吴军三部曲见识(七) 商业的本质
ByteDance overseas technical team won the championship again: HD video coding has won the first place in 17 items
Akamai 反混淆篇
Set up the flutter environment pit collection
Serial serialold parnew of JVM garbage collector
Only learning C can live up to expectations Top1 environment configuration
服务器端渲染(SSR)和客户端渲染(CSR)的区别
Notes on how the network is connected
Akamai浅谈风控原理与解决方案
Activiti directory (V) reject, restart and cancel process
肖申克的救赎有感
JS garbage collection mechanism and memory leakage