当前位置:网站首页>Nat address translation
Nat address translation
2022-07-07 18:38:00 【Chen chacha__】
Technical background
- legal IP Address resources are increasingly scarce
- Effectively hide internal hosts IP, It has a certain role in network security protection
NAT principle : change IP baotou 、 Make destination address 、 The source address or two addresses are replaced by different addresses in the header
NAT classification :
static state NAT: One to one address mapping
dynamic NAT: Pick from the address pool
NAT overload (PAT): Allow internal address mapping to an external address
static state NAT

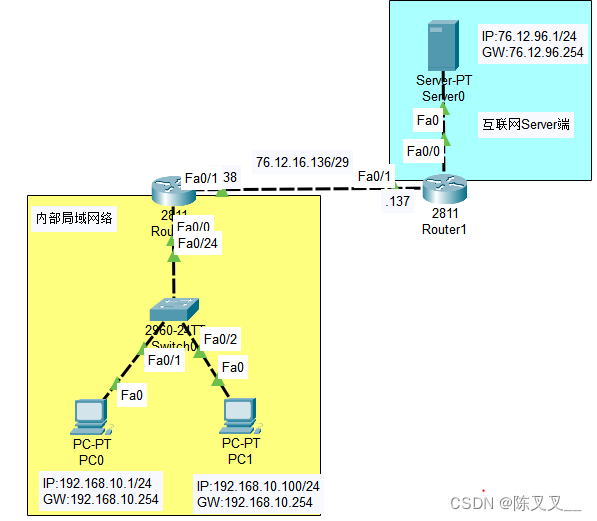
Two routers are respectively configured with default routes , The whole network is connected
1.PC0 Use the public address to access the Internet server , stay R0 The upper configuration enables static address translation between internal local and external legal addresses
ip nat inside soure static 192.168.10.1 76.12.16.139 # The former is the internal address , Followed by the external address to be mapped
Enable on internal and external ports NAT
int e0/0/0
ip nat inside
int f0/1
ip nat outside
show ip nat translations
2. Will be inside server HTTP Services are mapped to the public network IP PC Through the public network IP Internal access server
ip nat inside source static tcp 192.168.20.1 80 76.12.16.140 80
int f0/0
ip nat in
show ip nat translations
dynamic NAT

dynamic NAT Configuration steps
1. To configure ACL, Intranet range for address translation
access-list 1 permit 192.168.10.0 0.0.0.255
int f0/0
ip access-group in
2. Configure the translated address pool
ip nat pool pool-1 76.12.16.139 76.12.16.141 netmask 255.255.255.248
3. Set up ACL Mapping relationship with address pool
ip nat inside source list 1 pool pool-1
4. Enable on internal and external ports NAT
int f0/0
ip nat inside
int f0/1
ip nat outside
show ip nat translation # Check out the NAT Address translation address

边栏推荐
- 直播软件搭建,canvas文字加粗
- Usage of PHP interview questions foreach ($arr as $value) and foreach ($arr as $value)
- Chapter 3 business function development (to remember account and password)
- Tips for this week 134: make_ Unique and private constructors
- C语言中匿名的最高境界
- 高考填志愿规则
- Wireshark分析抓包数据*.cap
- Backup Alibaba cloud instance OSS browser
- 备份阿里云实例-oss-browser
- Tips of this week 141: pay attention to implicit conversion to bool
猜你喜欢

AI 击败了人类,设计了更好的经济机制
Chapter 2 build CRM project development environment (database design)
NAT地址转换
Automated testing: a practical skill that everyone wants to know about robot framework
将模型的记忆保存下来!Meta&UC Berkeley提出MeMViT,建模时间支持比现有模型长30倍,计算量仅增加4.5%...

The report of the state of world food security and nutrition was released: the number of hungry people in the world increased to 828million in 2021

AntiSamy:防 XSS 攻击的一种解决方案使用教程
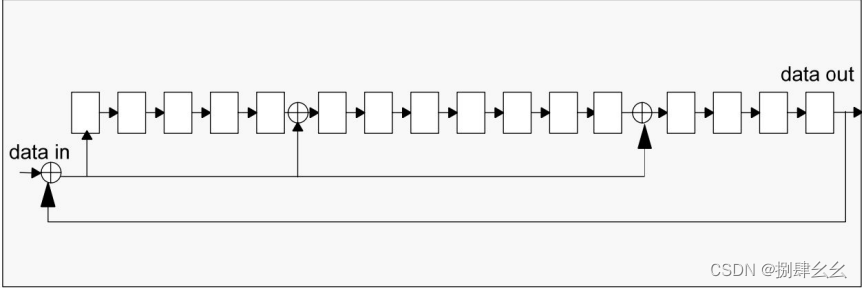
SD_DATA_RECEIVE_SHIFT_REGISTER
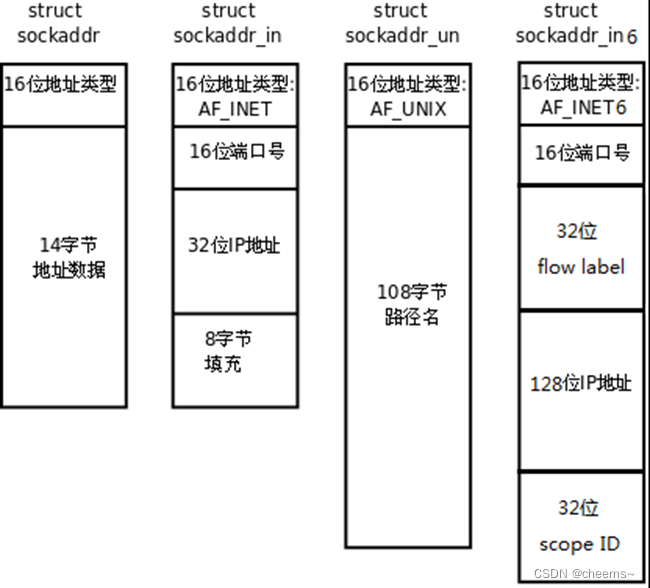
socket編程之常用api介紹與socket、select、poll、epoll高並發服務器模型代碼實現
Yearning-SQL审核平台
随机推荐
Do you really understand sticky bag and half bag? 3 minutes to understand it
元宇宙带来的创意性改变
Industry case | digital operation base helps the transformation of life insurance industry
海量数据去重的hash,bitmap与布隆过滤器Bloom Filter
Save the memory of the model! Meta & UC Berkeley proposed memvit. The modeling time support is 30 times longer than the existing model, and the calculation amount is only increased by 4.5%
socket编程之常用api介绍与socket、select、poll、epoll高并发服务器模型代码实现
Idea completely uninstalls installation and configuration notes
How to clean when win11 C disk is full? Win11 method of cleaning C disk
小程序中实现付款功能
How to open an account for wealth securities? Is it safe to open a stock account through the link
Ten thousand words nanny level long article -- offline installation guide for datahub of LinkedIn metadata management platform
【demo】循环队列及条件锁实现goroutine间的通信
More than 10000 units were offline within ten days of listing, and the strength of Auchan Z6 products was highly praised
Chapter 3 business function development (to remember account and password)
debian10编译安装mysql
直播软件搭建,canvas文字加粗
[trusted computing] Lesson 11: TPM password resource management (III) NV index and PCR
[principles and technologies of network attack and Defense] Chapter 5: denial of service attack
线程池的拒绝策略
静态路由配置