当前位置:网站首页>[principles and technologies of network attack and Defense] Chapter 3: network reconnaissance technology
[principles and technologies of network attack and Defense] Chapter 3: network reconnaissance technology
2022-07-07 18:01:00 【Godams】
3.1 summary
⽹ Network reconnaissance needs reconnaissance ⽬ Basic information of the subject
- Static information
All kinds of contact information , Including name, 、 mailbox 、 Phone number, etc
DNS、Web The server
Where the host is located ⽹ Collaterals ,IP Address
⽹ Network topology - Dynamic information
⽬ Mark whether the host is powered on
⽬ Check whether the host has installed the software you are interested in
⽬ Mark the type of operating system installed on the host
⽬ Mark whether there is a security vulnerability on the host ⽤ To attack - other ⼀ Be sure to ⽹ Collateral attack produces ⽣ do ⽤ Information about .
⽹ Network information collection ⽅ Law
- ⽹ Luo stampede : The attacker's response to ⽬ Mark in ⾏ information gathering , understand ⽬ The underlying ⽹ Network environment and information security . Prepare for attack . Specific contents ⻅ ⽹ Network detection often ⽤ Of ⼿ Paragraph and ⽅ Law .
- ⽹ Network scanning : Race seconds ⽬ mark ⽹ Collateral , Find as many connections as possible ⽬ mark . Before going into ⼀ Step probe to get the type 、 Existing security weaknesses and other information .
- ⽹ Check : For known weaknesses , For the identified services ⾏ More targeted exploration , Find what can really be attacked ⼊⼝, And the key data that may be needed during the attack . be relative to ⽹ Network scanning , More detailed , The scope is more ⼩.
3.2 Network reconnaissance methods
- Search engine information collection
- Whois Inquire about
- DNS Information Service
- ⽹ Network topology discovery
- benefit ⽤ social contact ⽹ Get information online
- other ⽅ Law
- social ⼯ Cheng Xue
- garbage
- Look up web Site
3.2.1 Search engine information collection
Baidu often uses advanced grammar
- site:[ Domain ] – site:zhihu.com
Returns search results related to a specific domain . - link:[Web⻚⾯] – link:www.csdn.net
Give and specify web⻚⾯ Linked sites . May leak ⽬ Business relationship of target site - Intitle:[ Conditions ]
⽤ The search title contains a specific search ⽂ Ben's ⻚⾯ - intext:[ Conditions ]
⽤ In search of ⽂ Contains specific searches ⽂ Ben's ⻚⾯ - related:[ Site ]
Display with specific retrieval ⻚⾯ Related ( similar ) Of web⻚⾯ - filetype:[ suffix ]
⽤ For finding specific types of ⽂ Pieces of - cache:[⻚⾯] – cache:www.csdn.net lookup csdn.net Was recently Baidu bot grabbing ⻚⾯ Show me ⾃ On Baidu Snapshot ⻚⾯ Content . For finding recently removed or currently unavailable ⽤ Of ⻚⾯ when ⾮ There is often ⽤.
- Not
Filter Web⻚⾯ Specific conditions contained in - Plus
tell Baidu This keyword should not be filtered out
Shodan and ZoomEye The basic characteristics of
Be able to connect ⽹ Search the host 、 The server 、 camera 、 Devices like printers and routers
Search for :⽹ Network devices 、⽹ Contact services 、⽹ Collateral system 、banner Information
Search format :A B C fiter:value filter:value filter:value
Zoomeye And Shodan The difference between :
Shodan Mainly for device fingerprints , That is, for some specific ends ⼝ Returned after communication banner Information into ⾏ Collection and indexing
Zoomeye In addition to detecting device fingerprints , Detection is also enhanced for some services .⽐ Such as Web Detailed analysis of services .
ping、nslookup、tracert(tracerout)
Traceroute :⽹ Network fault diagnosis and acquisition ⽹ Network topology ⼯ have .
nslookup: Inquire about DNS The record of , Check whether domain name resolution is normal , stay ⽹ When the network fails ⽤ To diagnose ⽹ The problem of network . Query the domain name IP Address
ping: testing ⽹ Network connectivity .
3.4 Network reconnaissance and defense
- Defense search engine reconnaissance
- Yes ⼰⽅ Of web Site content construction ⽴ Strict information disclosure strategy . Determine which sensitive data and information should not be in Web Appear on the site . But also for the staff ⼯ Into the ⾏ train , Ask them not to be on newsgroups or BBS Publish sensitive information on .
- Ask search engines to remove what they do not expect to be made public web⻚⾯ Indexes ,
- defense Whois Inquire about
- Guarantee Whois There is no record in that can be used by an attacker additionally ⽤ Information about . Such as the administrator's account name .
- But also for the staff ⼯ Into the ⾏ train , prevent ⽌ They fall into society ⼯ The trap of Engineering .
- defense DNS scout
- Concept supplement : Zone transfer :DNS The server replicates the database ⽂ Piece in ⾏ Sync . For those with this function DNS The server , Attackers can use this DNS Server as a springboard , obtain ⽬ Target host information .
- Avoid passage DNS Divulge additional information . for example : The domain name should not disclose the operating system of the computer ,⽤ Transit information .
- send ⽤DNS Separation technology , stay ⼏ platform DNS Distributed storage on the server DNS Information , Make internal and external ⽤ Household emissary ⽤ Different DNS service .
- Limit DNS Zone transfer . send ⽤ prevent ⽕ Wall configuration filter rules , So that only a few known AIDS are allowed DNS The server enters ⾏ Zone transfer .
- Defense society ⼯ Engineering attacks and garbage retrieval
- Trainer ⼯ Safety awareness . For computer configuration 、⼝ Make phone inquiries of sensitive information such as , Without confirming his identity , Do not disclose the relevant information technology department ⻔ Encountered modification permission 、 Reset password and other requests , Need to be right ⻬ Into the ⾏⼆ Secondary identity authentication . Special emphasis on caller ID technology , You can't just rely on caller ID to confirm ⽅ identity .
- send ⽤ Paper shredder, CD shredder and other equipment . For waste equipment and paper with sensitive information , All need to be crushed or incinerated .
边栏推荐
- 机器人工程终身学习和工作计划-2022-
- 基于RGB图像阈值分割并利用滑动调节阈值
- 使用popupwindow創建对话框风格的窗口
- viewflipper的功能和用法
- 使用OneDNS完美解决办公网络优化问题
- Tips for this week 140: constants: safety idioms
- Ansible learning summary (9) -- ansible loop, condition judgment, trigger, processing failure and other task control use summary
- 在窗口上面显示进度条
- SD_DATA_SEND_SHIFT_REGISTER
- Test for 3 months, successful entry "byte", my interview experience summary
猜你喜欢
Run Yolo v5-5.0 and report an error. If the sppf error cannot be found, solve it
企业经营12法的领悟

Chapter 3 business function development (user access project)
serachview的功能和用法

运行yolo v5-5.0版本报错找不到SPPF错误,进行解决
In depth understanding of USB communication protocol
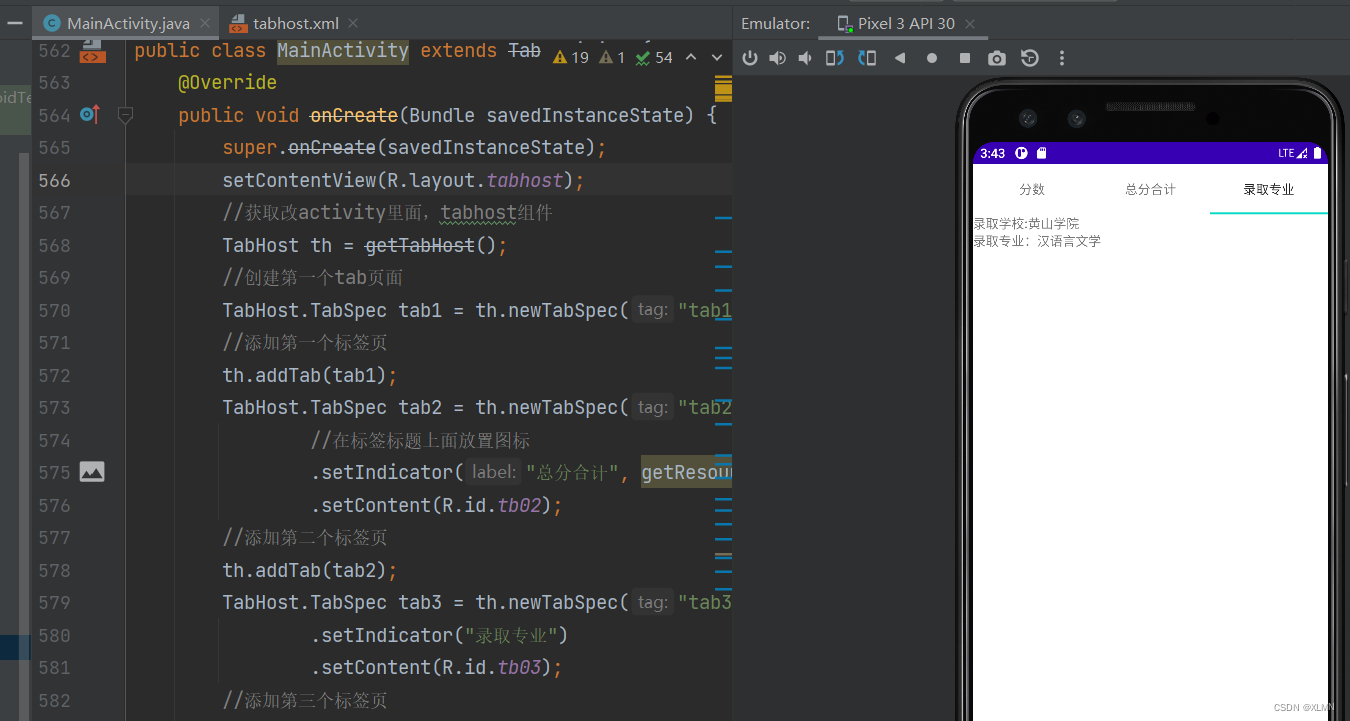
TabHOST 选项卡的功能和用法

Deep learning - make your own dataset
做软件测试 掌握哪些技术才能算作 “ 测试高手 ”?
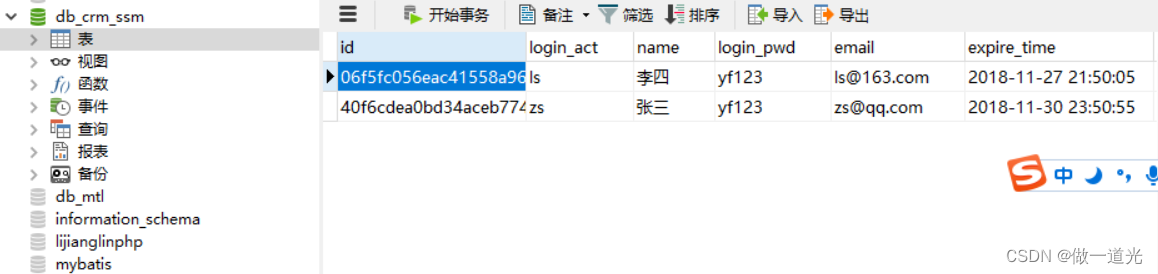
Chapter 2 build CRM project development environment (database design)
随机推荐
Audio Device Strategy 音频设备输出、输入 选择 基于7.0 代码
面试官:页面很卡的原因分析及解决方案?【测试面试题分享】
3分钟学会制作动态折线图!
Understanding of 12 methods of enterprise management
回归测试的分类
手机app外卖订餐个人中心页面
Mui side navigation anchor positioning JS special effect
深入浅出【机器学习之线性回归】
使用 xml资源文件定义菜单
Simple loading animation
Taffydb open source JS database
swiper左右切换滑块插件
mui侧边导航锚点定位js特效
Dateticket and timeticket, functions and usage of date and time selectors
What skills can you master to be a "master tester" when doing software testing?
Chapter 3 business function development (user access project)
机器视觉(1)——概述
MRS离线数据分析:通过Flink作业处理OBS数据
Show progress bar above window
How to implement safety practice in software development stage