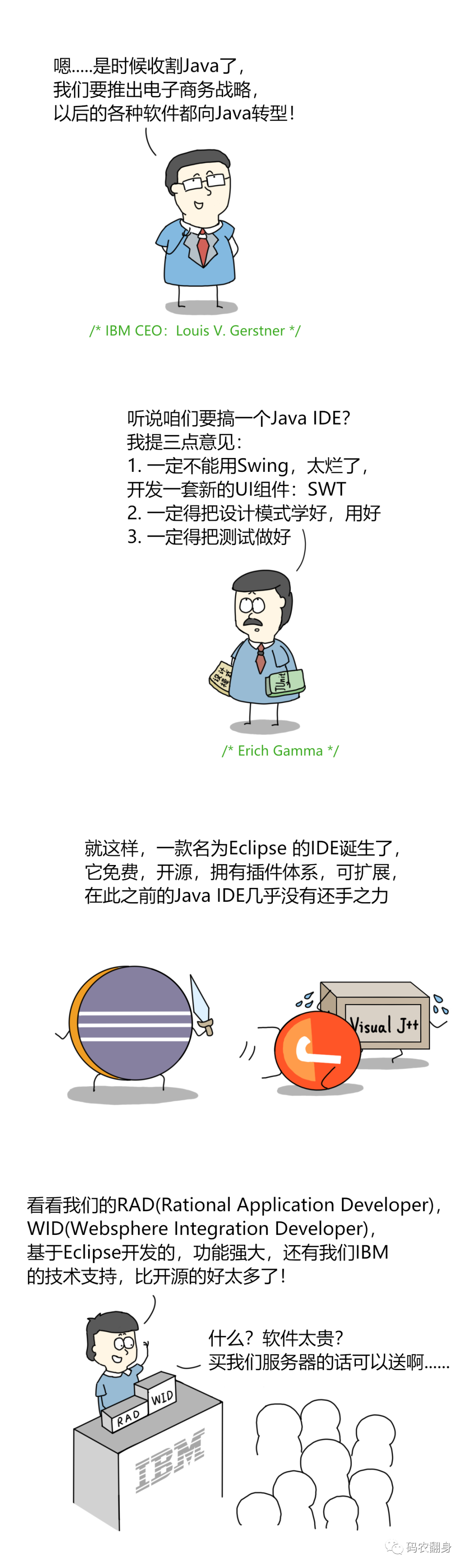
当前位置:网站首页>[trusted computing] Lesson 12: TPM authorization and conversation
[trusted computing] Lesson 12: TPM authorization and conversation
2022-07-07 18:00:00 【Godams】
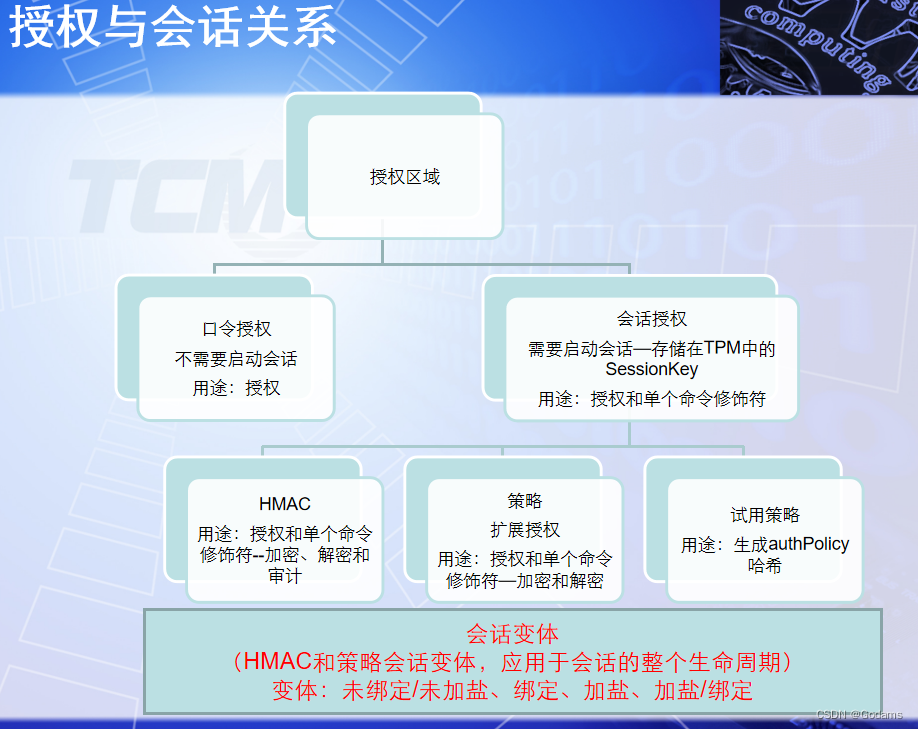
One 、 Authorization and conversation
What is Authorization ?
- The authorization is TPM2.0 Core concepts in the specification ,TPM All specifications ensure that access to various resources must be authorized . Authorization is used to control access to TPM Access to entities , Similar to the access control mechanism in the operating system , by TPM Provides security .
What is conversation ?
- stay TPM in , Conversation is closely related to authorization , Sometimes there is some conceptual overlap . The conversation is TPM The carrier and tool to complete authorization . Complete various authorizations by setting various properties and states of the session . Of course , The conversation can also complete its own tasks , Not for authorization .
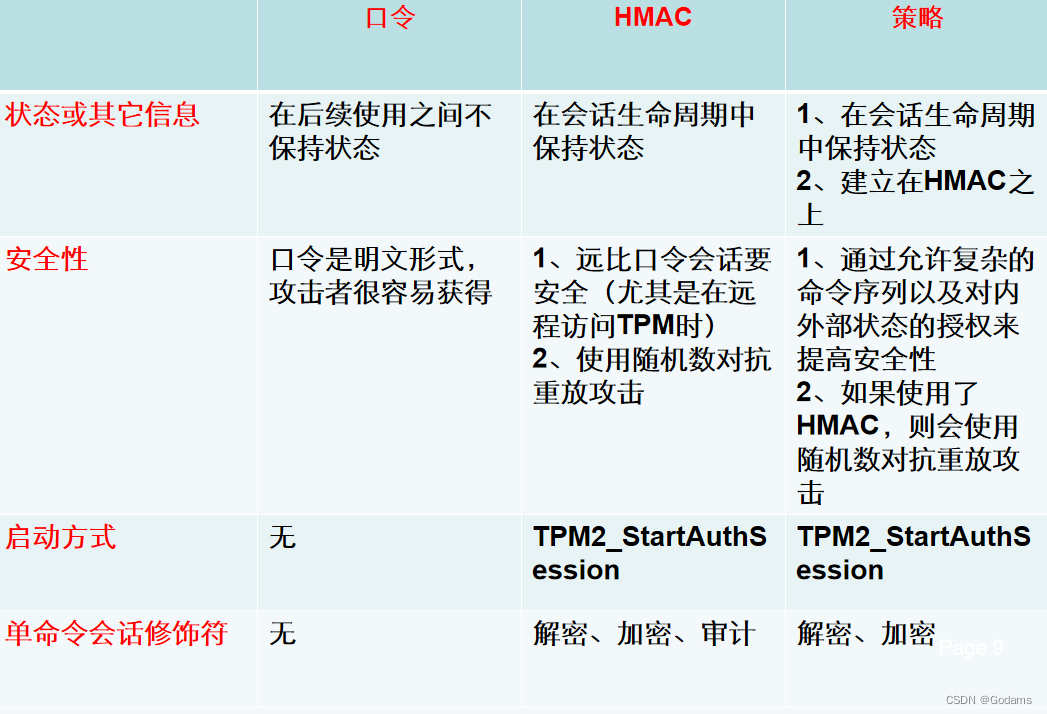
1.1 Password session
This is one of the three basic forms of conversation .TPM When authorizing access , According to the need of security , Choose different forms of sessions to complete authorization .
Password session is the simplest type of authorization :TPM When authorizing , You can pass the plaintext password to TPM Complete the task in the device . Password sessions can only be used locally TPM Entity access authorization , For remote authorization, there will be security problems , Because the password is clear , Unable to make remote transfer .
1.2 HMAC conversation
Once the application and TPM The device agrees on the password ( This is a consensus formed when an entity is created or its authorization value is modified ) after , You no longer need to transmit passwords . The one-time password transmission when creating entities or modifying entity authorization information can also be completed in a secure way : That is, passwords can be transmitted in encrypted form .
One HMAC The session can put the password ( This password is TPM2.0 In the specification, it is called authValue) Calculate as command and response HMAC An input parameter of , So that authorization can reach a high level of security .
When executing a command , The application that invokes the command calculates HMAC Value and insert this value into the command byte stream . When TPM After receiving this command byte stream , If TPM determine HMAC Calculated correctly , Then the corresponding action is authorized . In response to a command ,TPM Accounting response data HMAC Value and then insert this value into the response byte stream . After receiving the command response data flow, the application calling the command will calculate it separately HMAC, Then with the response byte stream TPM The results of the calculation are compared . If these two values match , Then the response data is credible . All these processes are built on the application and TPM All know and reach a consensus authValue Above .
HMAC The conversation will use two random numbers , It's also called nonce, One comes from the caller (nonceCaller), The other one comes from TPM(nonceTPM), These two random numbers can be used to prevent replay attacks . Random numbers will be used for HMAC In the calculation of . because nonceTPM It changes every time you execute a command , The application that invokes the command can also be modified each time the command is executed if desired nonceCaller, Therefore, the attacker cannot reuse the command data stream . The reused command byte stream is used for HMAC The calculation is bound to fail , This is because random numbers ( Exactly nonceTPM) It will change when reused .
HMAC The session will maintain the state during the session life cycle , Therefore, the session can be used for TPM Multiple actions of entities . Start a HMAC Conversation use TPM2_StartAuthSession command . When starting a session , It can be configured to bound vs. unbound as well as salted vs. unsalted conversation . The combination of these two options constitutes four HMAC Session variables ; These four variables determine the session key and HMAC How to be created .
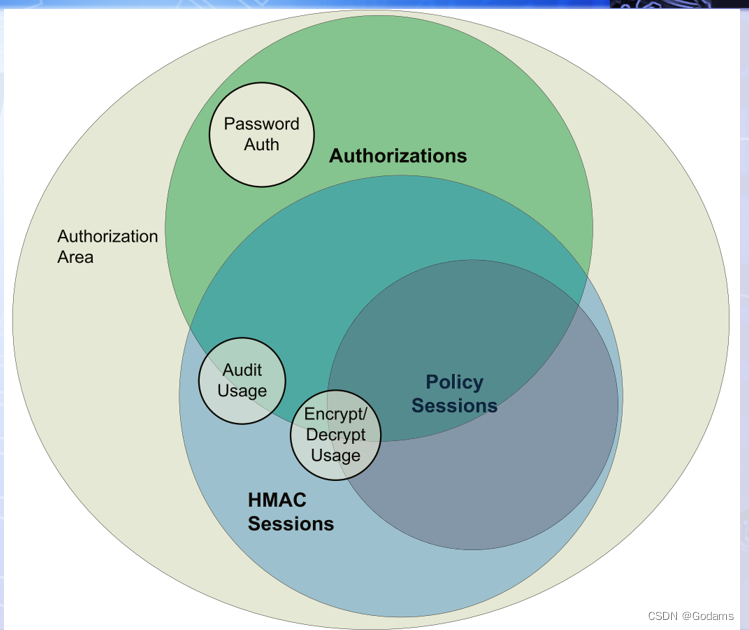
1.3 Policy session
Policy session , Also known as enhanced authorization (Enhanced Authorizaiton), It's based on HMAC Based on conversation , And added additional authorization levels .HMAC Authorization only uses authorization value or password ,Policy Authorization is enhanced on this basis , It can be based on TPM Order of commands ,TPM state , And external devices such as fingerprint card readers , Retinal scanner , And smart card to authorize . Several general authorization conditions can be passed AND and OR Operations are combined into a complex authorization tree , So as to provide unlimited authorization possibilities .
1.4 Comparison of three strategies
1.5 Authorization role
TPM2.0 The number of norms 3 Section specifies authorization roles for each command . The rules of authorization roles are the same as those in the computer operating system ACLs(Access Control Lists) It works in a similar way . Authorization roles control the type of authorization related to command execution , In fact, it controls who can execute what commands under what circumstances .
There are three possible authorization roles :USER,ADMIN, and DUP.USER be used for TPM Normal use of entities .ADMIN Used for system management related tasks .DUP, An unusual role , Mainly used in TPM2_Duplicate In command .
Determine the authorization method of the entity :
decision TPM The two attributes of an entity authorization method are userWithAuth and userWithPolicy. These attributes can be specified explicitly when creating objects , It can also be through specific permanence handle and NV Index to determine :
- userWithAuth:
Set as 1 Express USER The authorization of the role can be through password ,HMAC, perhaps Policy The session provides .
Set as 0 Express USER The authorization of the role must pass Policy The session provides . - adminWithPolicy:
Set as 1 Express ADMIN The authorization of the role must pass Policy The session provides .
Set as 0 Express ADMIN The authorization of the role can be through password ,HAMC, perhaps Policy The session provides .
If the authorization role of a command is ADMIN:
about TPM Object's handle Come on , The authorization required by this object adminWithPolicy Attribute decision , This property is set when the object is created .
about TPM_RH_OWNER,TPM_RH_ENDORSEMENT, as well as TPM_RH_PLATFORM these handle Come on , Their authorization is equivalent to adminWithPolicy Set as 1. That is to say, it must pass Policy Session provides authorization .
about NV The index says , Their authorization is equivalent to creating NV When indexing, the adminWithPolicy This attribute is set to 1.
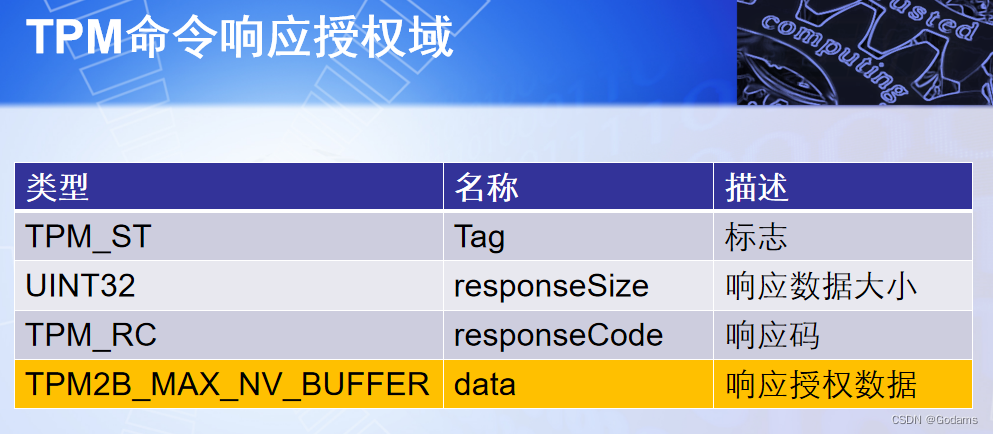
1.6 TPM Authorization domain in command
stay TPM In the command and response specification , Contains an important field — Authorization domain , This field specifies the location and type of session and authorization . For all commands that require authorization , The authorization area will be placed after the handle area and before the parameter area . The authorization area of the command response is placed at the end of the response , Immediately after the response parameters .
For any command that can use authorization , The authorization area can have at most three authorization structures . For a successfully executed TPM2.0 Command, , The number of authorization structures in the command response is always the same as the number of authorization structures in the command . For a failed execution TPM2.0 Command, , The number of authorized data structures for command responses is always 0.
If a command is authHandle Front use @ Symbolic modification : That means authHandle The authorization data of the corresponding entity needs to be added to the authorization area of this command . and “Auth role:USER” Indicates that this command requires authorization of roles .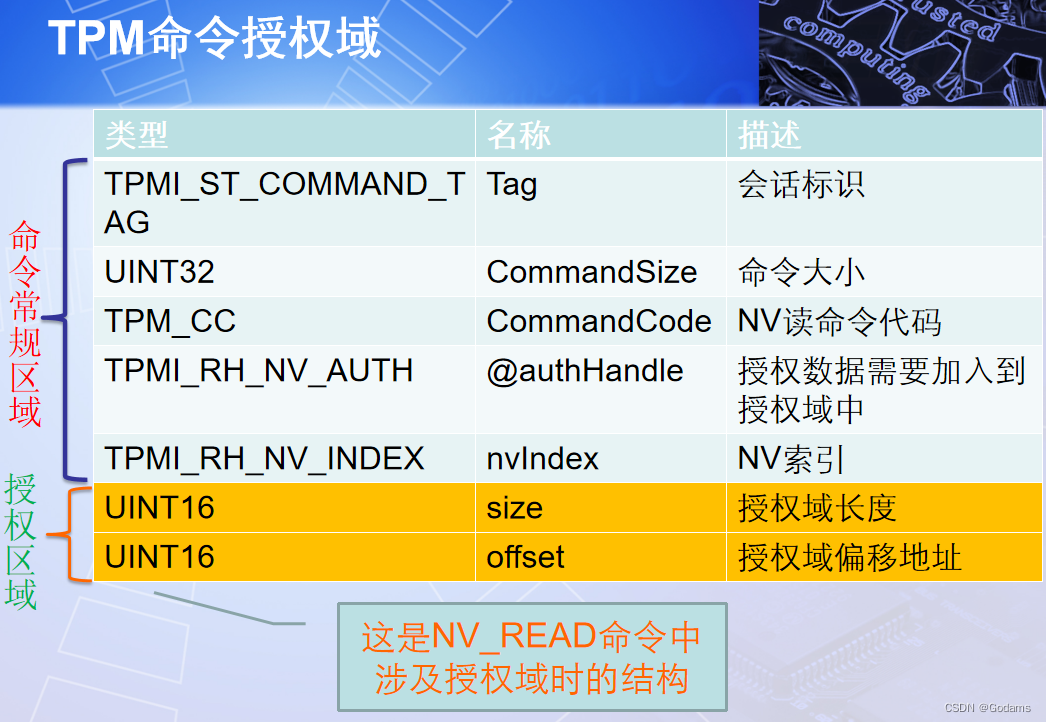


1.7 Password authorization
Password authorization lifecycle : Create an entity that uses a password as authorization , Then use the password to authorize the actions related to the entity . say concretely , The general steps required to create and use password authorization are as follows :
- Create an entity authorized with a password , Or modify the password value of the existing entity . This step is only done once for each entity .
- Use the password to authorize the actions related to the entity . This step can be performed many times , And once the authorization password is set for the entity, it may happen at any time .
1.7.1 Create a password authorization entity
To create an entity , You need to use the following command :TPM2_CreatePrimary,TPM2_Create, as well as TPM2_NV_DefineSpace.
These commands are passed by a user authValue Parameters of , This authValue Is the password used for authorization .authValue It can be a plaintext password , It can also be HMAC Input in authorization .
Create different types of password authorization entities
- TPM2_CreatePrimary It is used to create a main object in the organizational structure . If parameters inPublic Of userWithAuth The attribute is 1,USER Authorization can be a password authorization ; Use USER The authorization action of a role can be a password or HMAC.authValue The value of is through the parameter inSensitive Medium userAuth Delivered , Now? authValue It refers to the password value .
- TPM2_Create Used to create that can be loaded into TPM Objects in the . The authorization type of this command userWithAuth, as well as authValue The configuration mode of is similar to TPM2_CreatPrimary identical .
- TPM2_NV_DefineSpace Used to define a NV Indexes . If the property TPMA_NV_AUTHREAD perhaps TPMA_NV_AUTHWRITE Set up , You can use password authorization . Input parameters authValue It's through TPM2_NV_DefineSpace Of auth Parameters .
1.7.2 Change the password authorization of the created entity
If you need to change the authorization password of an entity , The following order may be required :
- TPM2_ObjectChangeAuth: It can be used to modify “ Not ” Authorization value of the main object .
- TPM2_HierarchyChangeAuth: It is used to modify the authorization value of an organizational structure ( platform , Storage , Or endorsement ), Or the authorized value of the locking mechanism .
- TPM2_NV_ChangeAuth: Used to modify a NV Authorization value of the index .
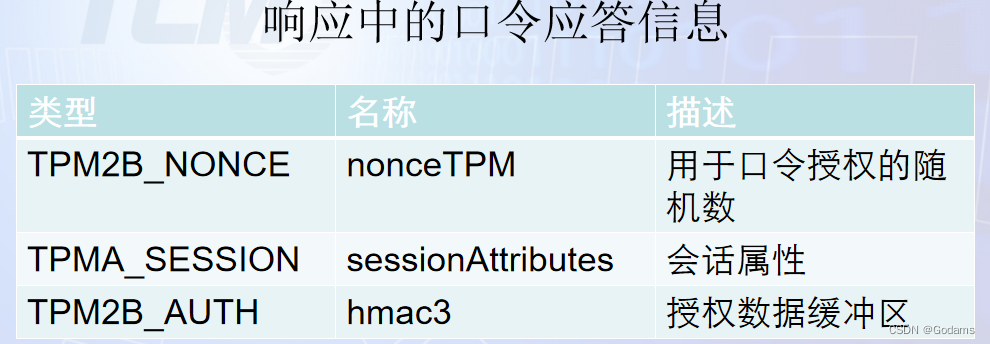
1.7.3 Authorize with password
To use password authorization , There is no need to start a session , The caller only needs to fill in the information in the command and response .
1.7.4 Turn on HMAC And policy sessions
HMAC and Policy Conversations are made by TPM2_StartAuthSession Order to start . When the session is started , It must be one of the following session types :HMAC,Policy, Or is it Trial Policy.Trial Policy Conversation is a dysfunctional Policy conversation : They cannot be used to authorize any action , But it can be used to generate Policy Abstract .
When a session starts , The basic characteristics of conversation have been determined . say concretely , Whether the session is bound 、 With or without salt 、 The strength of the session key , The strength of preventing replay attacks , Strength of parameter encryption and decryption , And conversational HMAC The strength passes TPM2_StartAuthSession Parameters to determine .
1.7.5 TPM2_StartAuthSession Command features
Two handle:
- If tpmKey yes TPM_RH_NULL, So this conversation is a conversation without salt ; otherwise , It's a conversation with salt , also encryptedSalt Parameters will be TPM Decrypt and get salt Value to increase entropy .TPM Use tpmKey This handle Point to the loaded key to decrypt encryptSalt.
- If bind yes TPM_RH_NULL, Then this conversation is unbound conversation . otherwise , It's just one. bound conversation , also bind Of the entity pointed to authValue Will and K Of salt Value connection ,K Is used to calculate sessionKey Of HMAC secret key .
Five parameters :
- nonceCaller Is the first random number , It is set by the caller . This random number also determines the following by TPM The size of the returned random number .
- encryptedSalt Only when the conversation is salted It will only be used when it is used , If the conversation is unsalted, This parameter must be empty .
- sessionType Determines the type of conversation :HMAC,policy, perhaps trial policy.
- symmetric, When the session is set to encrypt perhaps decrypt when , It is used to specify the type of parameter encryption .
- authHash It's an algorithm ID, This ID Specifies the HMAC Hash algorithm required for operation .
TPM2_StartAuthSession The command runs
1、 When a session is started ,TPM Will process commands and then create a session handle, And then calculate nonceTPM, And a session key . This session key will be used to generate HMAC value , Encrypt command parameters , And decryption command response parameters .
2、 When the session is created , The session key remains unchanged until the end of the session . The session handle and nonceTPM Will return with a command response .
3、 The session key will be passed from to the command TPM2_StartAuthSession Parameter determination of , These parameters include :tpmKey,bind,encryptedSalt,nonceCaller, as well as authHash. Parameters of command response ,nonceTPM, Also included in the session key . Use nonceTPM To create a session key, you can guarantee to use the same authValue,salt, as well as nonceCaller Different session keys will be generated .
4、 Because the application that invokes the command also needs the session key , So the application will use nonceTPM And other input parameters TPM Calculation process . Up to now , The session has been started , And the caller and TPM Everyone knows the session key .
TPM2_StartAuthSession Conversation intensity
- The strength of the session key is determined by bind,tpmKey,encryptedSalt,nonceCaller, And the hash algorithm used for the session .
- The session key with the highest strength is obtained through the following configuration : Use bind Point to one TPM Entity ( It means this is a bound conversation ),tpmKey Point to a that has been loaded into TPM The key of ( It means that this is a salted conversation ),nonceCaller The size of is set to the size of the hash algorithm output .
- If bind and tpmKey Are set to TPM_RH_NULL, The result is a length of 0 Session key —— Very weak session key . however , As long as the entity itself authValue The strength is high enough , that HMAC secret key ( It's actually authValue In itself ) Is also strong enough .
- Parameters in the session nonceCaller It's the length that determines nonceTPM The length of . The larger the random number , The better the session prevents replay attacks .
- The session key and the authorization value of the entity will eventually be used to generate the session HMAC. So again , A high-strength session key and authorization value will bring better security .
- call TPM2_StartAuthSession When choosing command parameters, programmers need to carefully consider what kind of security attributes they need .
1.8 Session variants
Add salt vs. No salt
HMAC and Policy Conversation can be with or without salt . A salted session will add more entropy to the creation process of the session key . Whether a conversation is salted depends on TPM2_StartAuthSession Of tpmKey Parameters . Use tpmKey The decrypted salt value will be added to the creation process of the session key . If authValue The intensity of is very weak , Adding salt to a session helps prevent offline brute force cracking . Offline brute force cracking refers to multiple attempts authValue To see if it can generate the correct HMAC value . If the crack succeeds ,authValue It's exposed . Adding salt to the conversation will raise the threshold of this type of attack .
Bound and unbound
HMAC and Policy Sessions can be bound or unbound . A binding session means that the session is “ binding ” To a specific TPM Physical , That's what I mentioned earlier “bind” Entity ; A binding session is usually used for “bind” The entity authorizes multiple actions . The authorization value of the binding entity is used to calculate the session key , But then it's no longer needed . In terms of security , Using authorization values only once is an advantage , Because the calling program does not always prompt the user to enter the authorization value ( password ) Or store the authorization value in memory .
Binding sessions can also be used for other entities ( Not “bind” Entity ) Authorization of , From this point of view ,“bind” The entity's authValue Add entropy to the session key , Thus, stronger command and command response parameter encryption and decryption .bind The authorization value of the entity and the entity to be authorized will be added to HMAC In the calculation of .
An unbound session can be used to authorize actions against many different entities . One Policy The session is usually configured as an unbound session . be relative to Policy For the security provided by the session ,HMAC Value is not so important , And use Policy There is no need to calculate and insert HMAC Value will make authorization much easier .
No salt conversation : When bind The entity's authValue The value is really strong enough to generate strong session keys and add / remove secret keys . If the system administrator can forcibly control the strength of the password , Use one unsalted A conversation without salt should be enough .
Salt conversation : When authValue When it is considered that the strength is insufficient to generate a secure session key and add / remove secret key . A website may ask users for two different passwords : One is used for encryption key use authorization , The other one is used for adding salt . As long as the salt value is strong enough in cryptography , The combination of these two passwords is much stronger than using one of them .
1.9 HMAC And policy conversation
HMAC and Policy The main difference of conversation is reflected in the way of action authorization . For the use of HMAC The command sent by the session , Only when it is sent to TPM Of HMAC The command will succeed only when the value is correct . In order to generate a correct HMAC value , Command callers and TPM We need to share a secret information (authValue). let me put it another way , The calculation is correct HMAC The value needs to know the session key and entity authValue, In this way, the entity can be effectively authorized to perform actions . If you don't know the session key or entity authValue, Can't calculate correctly HMAC value , This leads to command failure .
Policy The authorization of the session is based on a correct policy Command sequence , In many cases, there are also conditions required for the successful execution of these commands . This is just a simple description of this rich and complex authorization method .
There needs to be a before the command to be authorized is executed Policy Command execution sequence .TPM clear through policyDigest Value to confirm the command execution sequence . every last Policy Orders will Policy The hash of the relevant data is extended to the session policyDigest in . The simplest case is , Set the current session's policyDigest With authorized entities policyDigest Compare , The result of the comparison is used to decide whether to authorize the corresponding command .
In summary, it is ,HAMC Authorization is more secure than password authorization ,Policy Authorization is the most abundant and complex authorization .HMAC Authorization to use fully calculated in advance HMAC Value as a way to prove that the caller knows the authorized secret information .Policy Authorization requires a set of Policy Command and a specific set of conditions it requires to authorize an action . about HMAC and Policy For authorization ,HMAC Value can be used to guarantee Integrity of commands and command responses .
1.10 HMAC to grant authorization
Create based on HMAC Authorized entities include the following steps :
- Create an entity that uses authorization values , Or modify the authorization value of the existing entity . For every entity , This step is usually performed only once .
- Create a HMAC conversation .
- Use HMAC The session performs operations based on this entity . This operation can be done in step 1 and 2 Execute at any time after completion , And can be executed many times . One HMAC Sessions can be used to authorize multiple actions .
1.10.1 Modify or create a use HMAC Authorized entity
To create an entity , choice authValue The method of is the same as the password authorization method described above . The same is true for modifying the authorization value of an existing entity . In these two operations ,authValue Are treated equally .
1.10.2 Create a HMAC conversation
One HMAC The conversation is through TPM2_StartAuthSession Ordered sessionType Parameter set to TPM_SE_HAMC To create . When HMAC After the session starts ,TPM A session key will be created according to our previous description . The session key is in TPM Internally created .TPM2_StartAuthSession After the command returns , The caller will recreate the session key , Creating this key will use bind The entity's authValue,salt( Salt value ), And by TPM2_StartAuthSession Send to TPM Parameters of nonceCaller, also TPM Back to nonceTPM.
1.10.3 Use HMAC Session to single command authorization
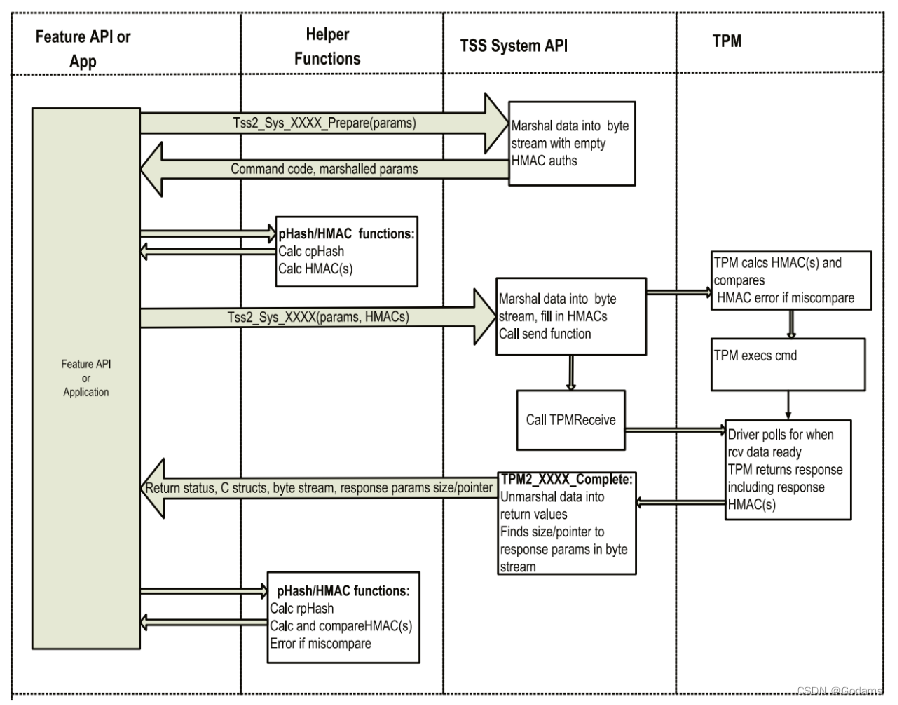
HMAC Session single command authorization process
- Input parameters are standardized , Connect and organize into a buffer , be called cpParams. Of the sample code 183-185 Yes Tss2_Sys_NV_Write_Prepare The command will do this and will cpParams The buffer is placed in sysContext In structure .
- Caller calculation cpHash value , This value is obtained by pairing cpParams The standardized command parameters in the buffer are hashed . The second part of the sample code 202-205 Yes ComputeCommandHamcs Function will perform such operations .
- The caller calculates the HMAC value .cpHash Is one of the input parameters of this calculation . This operation is also the first 202-205 Yes ComputeCommandHamcs Function .
- Calculated HMAC Value will also be ComputeCommandHamcs Automatically copy to HAMC The session HMAC In the region – Notice the pointer type parameters of this function nvCmdAuths.
- The complete command data must be standardized and organized into a byte stream sent to TPM equipment . These data include command headers , conversation , And command parameters . Refer to the 211-214 That's ok .
- from TPM Read command response information in . This is also in the first 211-214 Executed in a function called by line .
- After receiving the command response , Caller calculation rpHash, That is, the hash value of the formatted command response parameter . The first 224-226 Yes CheckResponseHmacs Function will perform this operation .
- The caller calculates the response of the command HMAC value ,rpHash Is one of the inputs to this calculation . This is also the first 224-226 Yes CheckResponseHmacs Function .
- The caller compares the just calculated HMAC And command response session HMAC Regional HMAC value . If they are different , Then it is considered that the command response parameters have been destroyed , Therefore, these parameter data are not credible . If they are the same , That means the command parameters are correctly received . This process is made up of CheckResponseHmacs Function . It will calculate the command response HMAC value , Then and through nvRspAuths Back to HMAC Value comparison .
- If the command responds HMAC Correct , The parameters of the command response can be de sequenced into C The structure of a language for use by the caller ; This process is also by 211-214 One call function of line to execute . For this one-time function , It should be noted that , It assumes HMAC The value is correct , And directly deserialize the parameters . after , If the command responds HMAC If the value is proved to be wrong , Then you can ignore the command response parameters that have been deserialized .
1.10.4 HMAC Session security
In essence ,TPM Use HMAC Three aspects of the session to ensure the security of the command :
session key : Bound to the session key authValue and salt There should be only callers and TPM Secret information known by the device . These two values are used to calculate the session key . An attacker who does not know these values cannot calculate the session key . Because the session key is used to create HMAC secret key , This feature prevents man in the middle attacks .
HMAC: Session key and entity authValue Used to generate HMAC secret key . Of the entity to be authorized authValue It should only be used by the caller and TPM know . therefore , This also means that attackers cannot perform man in the middle attacks .
Nonces:nonces Used to prevent replay attacks .HMAC The calculation will include nonce value , If nonce If the value is incorrect, there is no way to calculate the correct HMAC value . Again because nonce The values are always changing , Therefore, the byte stream of a command cannot be executed repeatedly .
As long as the binding entity is reasonably maintained authValue,salt, And authorized entities authValue, The attacker cannot authorize this entity . Then scroll all the time nonce Value can prevent replay attacks .
1.10.5 HMAC Session command authorization domain
Session handle:4 byte , Represents the session index value related to this authorization content .
Size field:2 byte , Used to indicate Nonce The length of .
Nonce( The caller provides ): If there is , It is a value set by the caller .
Session attributes: A byte , The bit field indicates the purpose of the session .
size of HMAC:2 byte , instructions authorization The size of the area .
Authorizaiton=HMAC If it exists , It is just a containing HMAC Worth array . This HMAC The value is generated by the code that invokes the command .HMAC It is calculated from the parameters of the command .TPM Will calculate independently HMAC Value then and this HMAC Value comparison , Then determine TPM The command information received has not been destroyed .
Size field:2 byte , Used to indicate Nonce The length of .
Nonce(from TPM): If there is , Namely TPM Set a value .
Session attributes: A byte , The bit field indicates the purpose of the session .
size field = sizeof HMAC:2 byte , Used to indicate acknowledgment The size of the area .
Acknowledgment=HMAC If it exists , It is just a containing HMAC Worth array . This HMAC Values are determined by TPM produce .HMAC It is calculated from the parameters of the command response . After receiving the response data, the command caller will calculate HMAC Value then and this HMAC Value comparison , Then determine from TPM The received command response information is not corrupted .
边栏推荐
- Chapter 3 business function development (safe exit)
- Interviewer: why is the page too laggy and how to solve it? [test interview question sharing]
- [deep learning] 3 minutes introduction
- Audio Device Strategy 音频设备输出、输入 选择 基于7.0 代码
- Mobile pixel bird game JS play code
- 保证接口数据安全的10种方案
- Use onedns to perfectly solve the optimization problem of office network
- [OKR target management] case analysis
- Import requirements in batches during Yolo training Txt
- 深入浅出【机器学习之线性回归】
猜你喜欢
随机推荐
Native JS verification code
Import requirements in batches during Yolo training Txt
目标检测1——YOLO数据标注以及xml转为txt文件脚本实战
Management by objectives [14 of management]
在窗口上面显示进度条
Face recognition attendance system based on Baidu flying plasma platform (easydl)
Ansible learning summary (9) -- ansible loop, condition judgment, trigger, processing failure and other task control use summary
什么是敏捷测试
机器视觉(1)——概述
Youth experience and career development
讨论| 坦白局,工业 AR 应用为什么难落地?
Ratingbar的功能和用法
Explain it in simple terms. CNN convolutional neural network
Taffydb open source JS database
【解惑】App处于前台,Activity就不会被回收了?
2021-06-28
ViewSwitcher的功能和用法
Function and usage of numberpick
保证接口数据安全的10种方案
仿今日头条APP顶部点击可居中导航
![[answer] if the app is in the foreground, the activity will not be recycled?](/img/b7/a749d7220c22f92080b71fd3859b8d.png)