当前位置:网站首页>Xiaoman network model & http1-http2 & browser cache
Xiaoman network model & http1-http2 & browser cache
2022-07-06 21:59:00 【Xiaoman ZS】
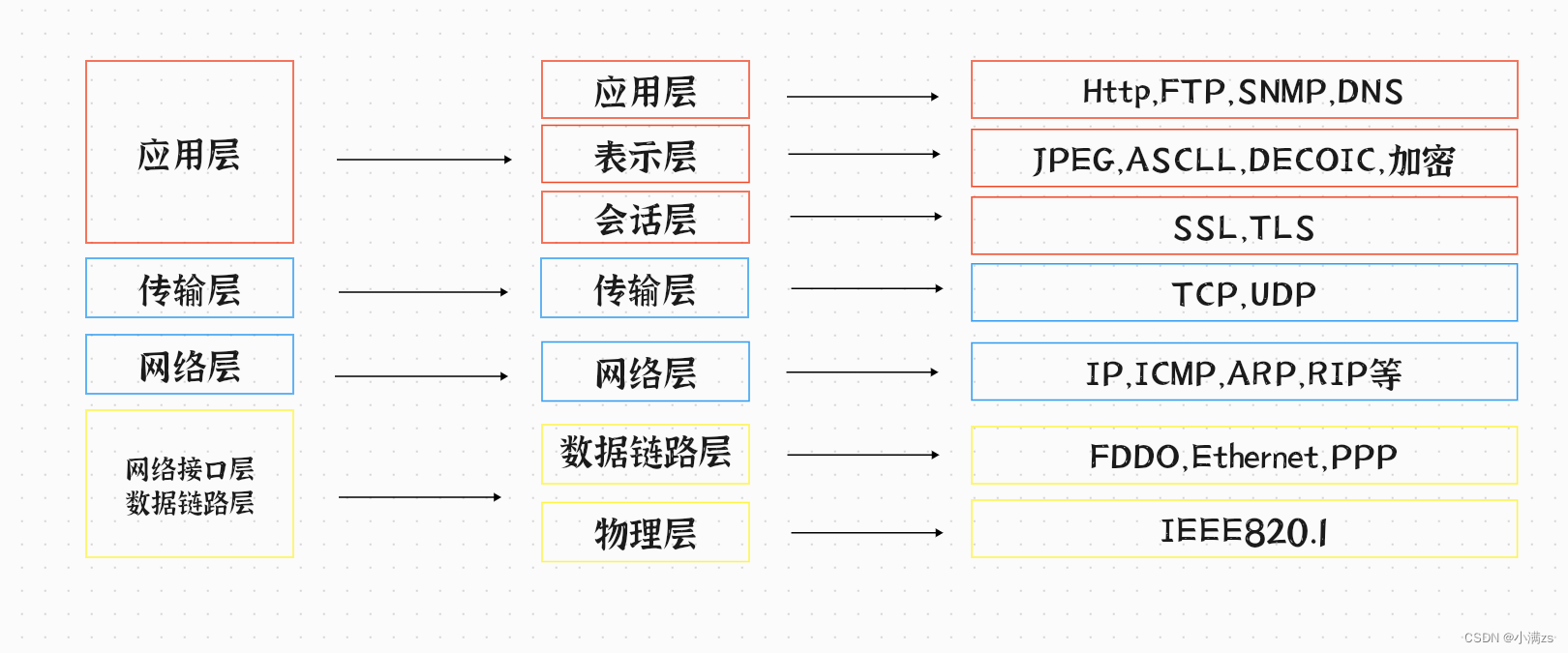
application layer
Is closest to the application OSI layer . Users use corresponding interfaces to implement their own services .
The agreement has :HTTP FTP SMTP etc.
The presentation layer
Presentation of data 、 Security 、 Compress . It can ensure that the information sent by the application layer of one system is read by the application layer of another system . The format is : JPEG、ASCII、 Encryption format, etc .
In the presentation layer , The data is formatted according to a scheme that the network can understand . Manage data encryption and decryption .
The session layer
establish 、 management 、 Terminate the conversation , Corresponding host process , Refers to the ongoing session between the local host and the remote host . Be responsible for establishing between the two nodes of the network 、 Maintain and terminate Communications .
The functions of the conversation layer include : Establish communication links , Keep the communication connection smooth during the conversation , Synchronize the conversation between two nodes , Decide whether the communication is sent by the terminal and where to resend when the communication is interrupted .
Some people will call the session layer network communication “ Traffic police ". When dialing to your ISP( Internet service providers ) When you request to connect to the Internet ,ISP The session layer on the server communicates to you and your PC The session layer on the client negotiates the connection . If your telephone line falls off accidentally , The session layer will detect the connection interruption and restart the connection . The session layer sets the communication period by determining the priority of node communication and the length of communication time .
Transport layer
Define the protocol port number of data transmission , And flow control and error checking .
The agreement has :TCP UDP etc. , Once the packet leaves the network card, it will enter the network transmission layer . Some protocols and port numbers for data transmission are defined , Such as :TCP( Transmission control protocol , Low transmission efficiency , High reliability , High requirements for transmission reliability , A large amount of data ),UDP( User datagram protocol , The requirements for transmission reliability are not high , A small amount of data ). It mainly refers to the segmentation and transmission of data received from the lower layer , Regroup after arriving at the destination . This layer of data is often called segment .
OSI The final layer in the model . The transmission protocol performs browsing control at the same time or specifies an appropriate transmission rate based on the speed of the data that can be received by the receiver . besides , The transport layer compulsorily splits long packets according to the maximum size that the network can handle . for example , Ethernet cannot receive more than 1500 Byte packets . The transmission layer of the sender node divides the data into smaller pieces of data , At the same time, a serial number is arranged for each data slice , So that when the data reaches the transmission layer of the receiver node , Be able to regroup in the right order . This process is called sorting .
The network layer
Logical address addressing , Realize the path selection between different networks . The agreement has :ICMP IGMP IP ARP RARP etc. .
Provides connectivity and path selection between two host systems in a network in different geographic locations .Internet The development of has greatly increased the number of users accessing information from sites around the world , The network layer formally manages the layer of this connection .
OSI The third layer of the model , Its main function is to translate the network address into the corresponding physical address , And decide how to route data from the sender to the receiver .
The network layer considers the priority of transmission through comprehensive consideration 、 The degree of network congestion 、 The quality of service and the cost of optional routing are determined from the nodes in a network A To another network node B The best way . Due to network layer processing , And intelligently guide data transmission , Routers connect all segments of the network , So routers belong to the network layer . In the network ,” route “ It's based on the addressing scheme 、 Use mode and accessibility to guide the sending of data .
The network layer is used locally LAN The computer system above the network segment establishes communication , The reason it can do this , Because it has its own routing address structure , This structure is separate from the second layer machine address 、 independent . This kind of protocol is called routing or routable protocol . Routing protocols include IP、Novell The company's IPX as well as AppleTalk agreement .
Data link layer
Establish logical connections 、 Address the hardware 、 Error checking and other functions . Combining bits into bytes and then into frames , use MAC Address access media , To discover but not correct .
The main function is how to reliably transmit data on unreliable physical lines . To ensure transmission , The data received from the network layer is divided into specific frames that can be transmitted by the physical layer . Frames are structural packets used to move data , It's not just raw data , It also includes physical addresses of sender and receiver as well as error detection and control information . The address determines where the frame will be sent , And the error correction and control information ensure that the frame is error free . If you're transmitting data , The receiver has detected an error in the transmitted data , We need to inform the sender to resend this frame .
The data link layer provides bit stream services on the basis of the physical layer , Establish data links between adjacent nodes , Error free transmission of data frames on the channel is provided through error control , And carry out the action series on each circuit . The main function is physical address addressing 、 Data framing 、 flow control 、 Error detection of data 、 Resend, etc .
The physical layer
establish 、 maintain 、 Disconnect the physical connection .
The main definition of physical equipment standards , Such as the interface type of network cable , Interface type of optical fiber , Transmission rate of various transmission media, etc . The main function is to transmit bit stream ( There is 1、0 It is transformed into power strength for transmission , After arriving at the destination, it is transformed into 1、0).
The second section http1.1 http2
- HTTP/2 Use binary format instead of text format
- HTTP/2 It's fully multiplexed , Not ordered and blocked —— Only one connection is needed to achieve parallelism
- Using header compression ,HTTP/2 Lower the cost
- HTTP/2 Let the server take the initiative to respond “ push ” Into the client cache
1. Binary framing layer
On the binary framing layer ,HTTP 2.0 All transmitted information will be divided into smaller messages and frames , And they are encoded in binary format , among HTTP1.x The first message of will be encapsulated in Headers frame , And ours request body Then package it to Data Inside the frame .

2. Multiplexing
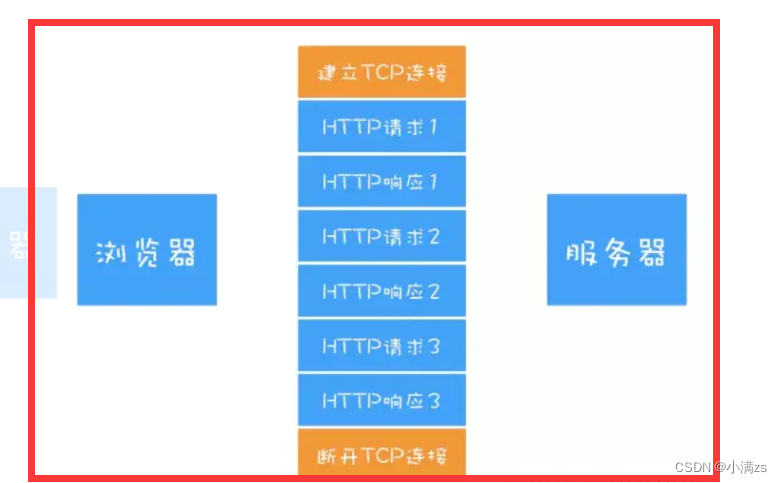
As can be seen from the above figure ,HTTP The number of persistent connections can be reduced effectively TCP Number of connections established and disconnected , The advantage is that it reduces the extra burden on the server , And improve the whole HTTP Request time for
3. The head of compression
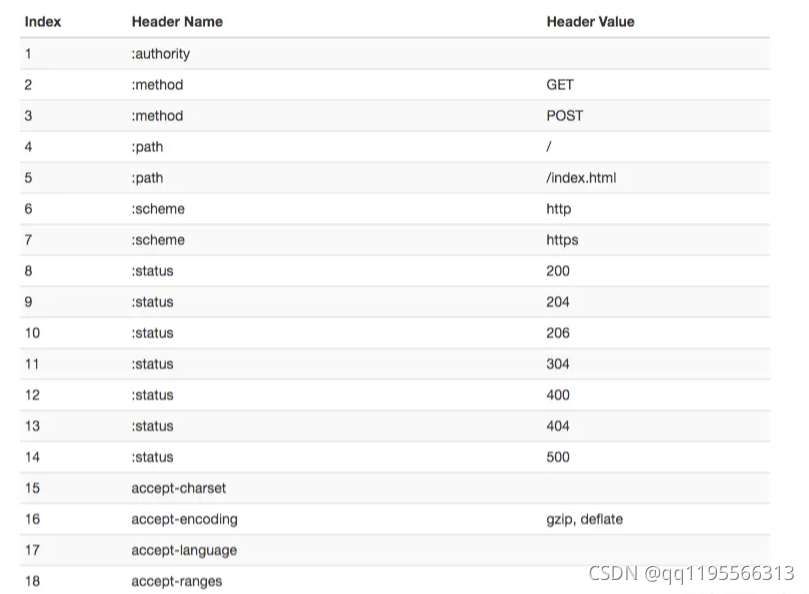
- Maintain the same static dictionary , Contains common header names , And common combinations of header names and values
- Maintain the same dynamic dictionary , You can add content dynamically
- By static Huffman Encoding encodes the header field of the transmission
demonstration demoHTTP/2: the Future of the Internet | Akamai
4. Client cache
Negotiate the cache
Negotiating cache is to judge whether the cache is available through the server
Last-Modify collocation If-Modify-Since: The first time a browser requests a resource , Server returned header I will add Last-Modify,Last-modify Is the last modification time of this resource ; When the browser requests the resource again ,request The request header of will contain If-Modify-Since, The value of the server header In return Last-Modify. Server received If-Modify-Since after , Determine whether to hit the cache according to the last modification time of the resource
Etag collocation If-None-Match:web When the server responds to a request , Will be in header To add a Etag It is used to tell the browser the unique identification of the current resource on the server ( The generation rules are determined by the server ). Again to web Server request with header If-None-Match (Etag Value ).web The server will If-None-Match And Etag compare , Decide whether to hit the negotiation cache ;
ETag and Last-Modified Function and usage of , Their differences :
1.Etag Is better than Last-Modified.Last-Modified In seconds , If a file is in 1 I changed it many times in a second , So their Last-Modified It doesn't actually reflect the modification , however Etag It changes every time to ensure accuracy ;
2. In performance ,Etag To be worse than Last-Modified, After all Last-Modified Just record the time , and Etag You need the server to calculate one using an algorithm hash value ;
3. In priority , Server validation is preferred Etag.
If the request received by the server does not Etag value , Will If-Modified-Since Compare with the last modification time of the requested file , Consensus hits the negotiation cache , return 304; If not, a new last-modified And file and return 200
Strong cache
Expires: The value is absolute time , however Expires yes HTTP 1.0 Things that are , Now the default browser is used by default HTTP 1.1
Cache-Control: The value is relative time , If the Expires If it is set at the same time , Its priority is higher than Expires.
cache-control There are several commonly used settings :
-max-age: Set the expiration time , The client is within this validity period , If the resource is requested again , Just read the cache directly
-no-cache: Do not use local cache . Cache negotiation required , First confirm with the server whether the returned response has been changed , If a previous response exists ETag, Then the request will be verified with the server , If the resource has not been changed , Then fetch data from the cache
-no-store: Directly prohibit the browser from caching data , Every time a user requests the resource , Will send a request to the server .
-public: Can be cached by all users , Including end users and CDN Wait for intermediate proxy server .
-private: Can only be cached by the end user's browser , Don't allow CDN Wait for the relay cache server to cache it .
The server is set by http in hdader Of Expires and cache-control Field tells the browser the validity of the swap . This method will have a fixed time , The problem is that if the server data is updated , But the expiration time of strong cache is not yet , The data cannot be updated
边栏推荐
猜你喜欢
![[asp.net core] set the format of Web API response data -- formatfilter feature](/img/95/b7e7b5e9e9ac1d9295c17640beccb3.jpg)
[asp.net core] set the format of Web API response data -- formatfilter feature
PostgreSQL modifies the password of the database user
Shell product written examination related

Microsoft technology empowerment position - February course Preview
ViT论文详解
Enhance network security of kubernetes with cilium
【MySQL】Online DDL详解
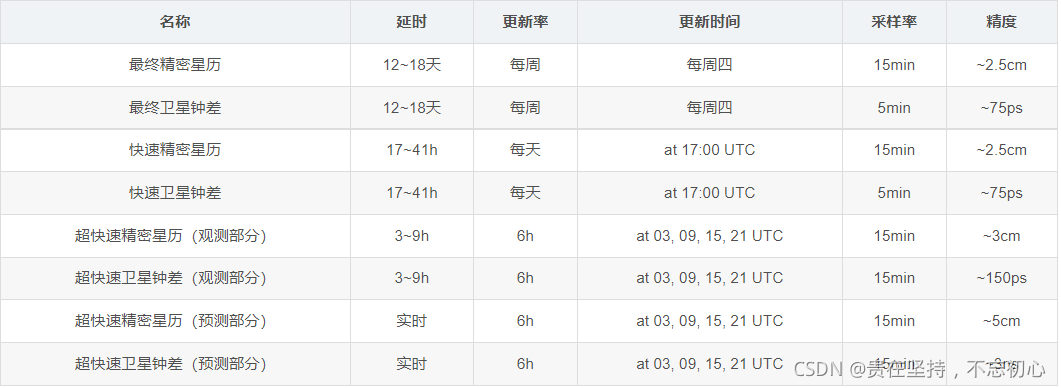
GPS from getting started to giving up (19), precise ephemeris (SP3 format)
jvm:大对象在老年代的分配
![[Chongqing Guangdong education] Information Literacy of Sichuan Normal University: a new engine for efficiency improvement and lifelong learning reference materials](/img/a5/94bdea3a871db5305ef54e3b304beb.jpg)
[Chongqing Guangdong education] Information Literacy of Sichuan Normal University: a new engine for efficiency improvement and lifelong learning reference materials
随机推荐
HDU 2008 数字统计
50个常用的Numpy函数解释,参数和使用示例
C# 如何在dataGridView里设置两个列comboboxcolumn绑定级联事件的一个二级联动效果
抖音将推独立种草App“可颂”,字节忘不掉小红书?
[go][reprint]vscode run a HelloWorld example after configuring go
搜素专题(DFS )
十一、服务介绍及端口
Happy sound 2[sing.2]
红杉中国,刚刚募资90亿美元
GPS从入门到放弃(十二)、 多普勒定速
numpy 下载安装
Digital transformation takes the lead to resume production and work, and online and offline full integration rebuilds business logic
中国白酒的5场大战
功能强大的国产Api管理工具
【sciter Bug篇】多行隐藏
Efficiency tool +wps check box shows the solution to the sun problem
Guava: use of multiset
14 years Bachelor degree, transferred to software testing, salary 13.5k
Leveldb source code analysis series - main process
Intelligent online customer service system source code Gofly development log - 2 Develop command line applications