当前位置:网站首页>PostgreSQL 修改数据库用户的密码
PostgreSQL 修改数据库用户的密码
2022-07-06 13:27:00 【ac.char】
pg_hba.conf,认证设置成md5认证连接出现:
postgresql FATAL: password authentication failed for user "postgres"
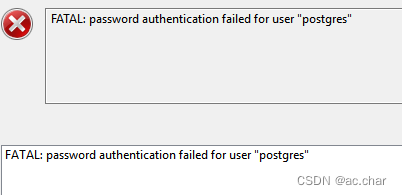
编辑pg_hba.conf,将md5认证修改成trust认证,编辑后退出保存
执行pg_ctl reload加载生效
psql连接,用alter role修改密码
执行以下命令
alter role postgres with password '新密码';
查看当前postgresql 有多少用户,及对应的密码
select rolname,rolpassword from pg_authid;
退出psql
编辑pg_hba.conf,将turst认证修改成md5认证,编辑后退出保存
执行pg_ctl reload加载生效
边栏推荐
- document. Usage of write () - write text - modify style and position control
- 3D face reconstruction: from basic knowledge to recognition / reconstruction methods!
- Common English vocabulary that every programmer must master (recommended Collection)
- Redistemplate common collection instructions opsforlist (III)
- 字符串的使用方法之startwith()-以XX开头、endsWith()-以XX结尾、trim()-删除两端空格
- [redis design and implementation] part I: summary of redis data structure and objects
- 首批入选!腾讯安全天御风控获信通院业务安全能力认证
- How to implement common frameworks
- b站视频链接快速获取
- In JS, string and array are converted to each other (II) -- the method of converting array into string
猜你喜欢

Michael smashed the minority milk sign
![[MySQL] basic use of cursor](/img/cc/39b1e17b48d0de641d3cbffbf2335a.png)
[MySQL] basic use of cursor
2017 8th Blue Bridge Cup group a provincial tournament

Five wars of Chinese Baijiu
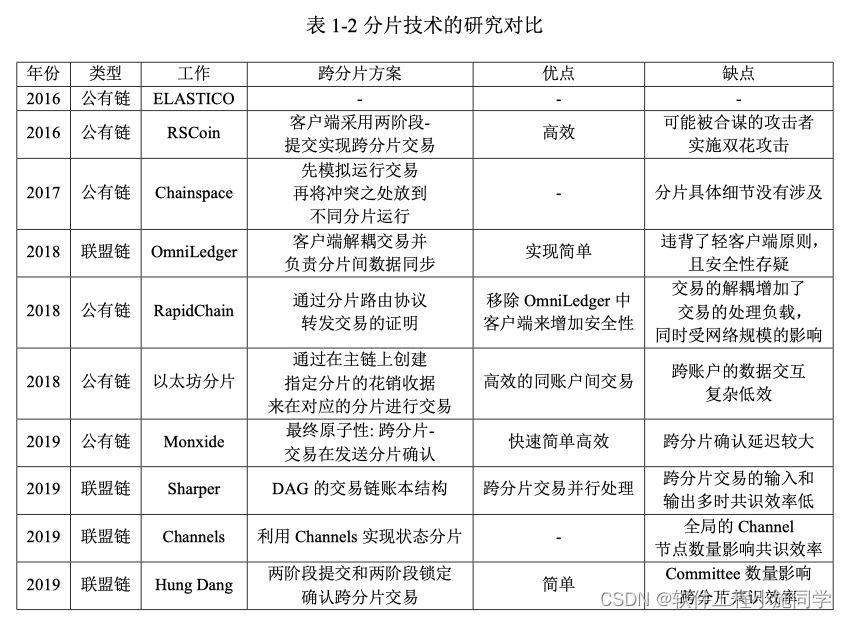
跨分片方案 总结
愛可可AI前沿推介(7.6)
![[redis design and implementation] part I: summary of redis data structure and objects](/img/2e/b147aa1e23757519a5d049c88113fe.png)
[redis design and implementation] part I: summary of redis data structure and objects
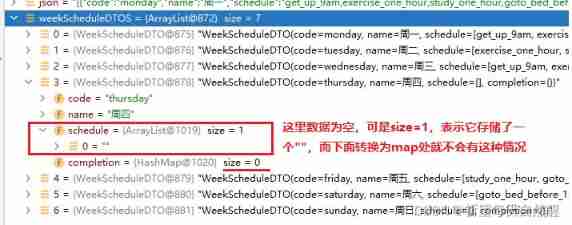
Fastjson parses JSON strings (deserialized to list, map)
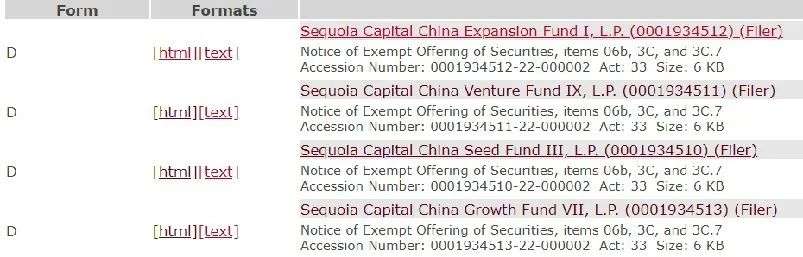
红杉中国,刚刚募资90亿美元
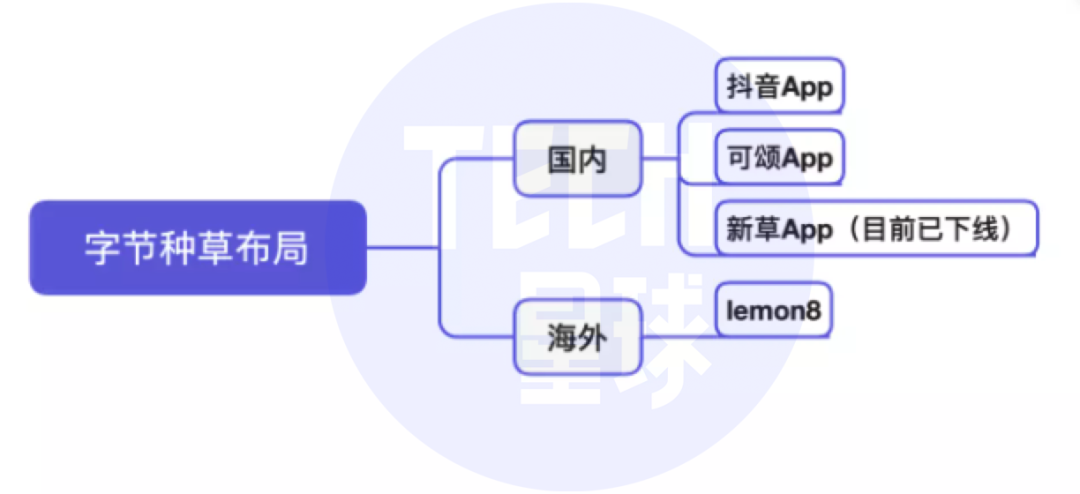
抖音将推独立种草App“可颂”,字节忘不掉小红书?
随机推荐
The difference between break and continue in the for loop -- break completely end the loop & continue terminate this loop
FZU 1686 龙之谜 重复覆盖
968 edit distance
语谱图怎么看
Yyds dry inventory run kubeedge official example_ Counter demo counter
Vim 基本配置和经常使用的命令
【力扣刷题】一维动态规划记录(53零钱兑换、300最长递增子序列、53最大子数组和)
Quick news: the flybook players' conference is held online; Wechat payment launched "education and training service toolbox"
@GetMapping、@PostMapping 和 @RequestMapping详细区别附实战代码(全)
967- letter combination of telephone number
Tiktok will push the independent grass planting app "praiseworthy". Can't bytes forget the little red book?
Nodejs教程之让我们用 typescript 创建你的第一个 expressjs 应用程序
爬虫实战(五):爬豆瓣top250
Fastjson parses JSON strings (deserialized to list, map)
Torch Cookbook
互联网快讯:吉利正式收购魅族;胰岛素集采在31省全面落地
JS traversal array and string
Yuan Xiaolin: safety is not only a standard, but also Volvo's unchanging belief and pursuit
ICML 2022 | Flowformer: 任务通用的线性复杂度Transformer
JPEG2000-Matlab源码实现