当前位置:网站首页>Deadlock conditions and preventive treatment [easy to understand]
Deadlock conditions and preventive treatment [easy to understand]
2022-07-07 21:04:00 【Full stack programmer webmaster】
Hello everyone , I meet you again , I'm the king of the whole stack .
The so-called deadlock : Two or more processes in the process of execution , A phenomenon of waiting for each other caused by competing for resources . If there is no external force , They will not be able to move forward . At this point, the system is said to be in a deadlock state or the system has produced a deadlock , These processes that are always waiting for each other are called deadlock processes . Because resource occupation is mutually exclusive , When a process requests resources , Make the relevant process without external assistance , You can never allocate the necessary resources to continue execution . This creates a special phenomenon deadlock .
Although the process is in the process of execution , Deadlock could happen , But the occurrence of deadlock must also have certain conditions , The occurrence of deadlock must meet the following four necessary conditions .
1) Mutually exclusive condition :
Refers to the exclusive use of resources allocated by the process , That is, a resource is occupied by only one process for a period of time . Suppose there are other processes requesting resources at this time , Then the requester can only wait , Until the process of taking possession of resources is completed and released .
2) Request and hold conditions :
Means that the process has kept at least one resource . But new resource requests were made , The resource is already occupied by other processes , At this time, the request process is blocked , However, they are not willing to let go of other resources they have obtained .
3) Conditions of non deprivation :
Refers to the resources obtained by the process , Before use , Can't be deprived of , It can only be released by itself when it is used up .
4) Loop waiting condition :
When a life and death lock is issued , There must be a process —— Circular chain of resources . That is, process set {P0,P1,P2,···,Pn} Medium P0 Waiting for one P1 Occupied resources .P1 Is waiting for P2 Occupied resources .…….Pn Waiting for has been P0 Occupied resources .
After a deadlock has occurred in the system , Deadlock should be detected in time , And take appropriate measures to release the deadlock . At present, there are four ways to deal with deadlocks :
1) Deadlock prevention .
This is a simple and intuitive method of prevention in advance .
By setting some restrictions . To destroy one or more of the four necessary conditions for deadlock , To prevent deadlock . Deadlock prevention is an easy method , Has been widely used . However, the restrictions imposed are often too strict , It may lead to the reduction of system resource utilization and system throughput .
2) Avoid deadlock .
This method belongs to the strategy of prevention in advance . However, it does not need to take various restrictive measures in advance to destroy the four necessary conditions for deadlock , But in the process of dynamic allocation of resources , Some way to prevent the system from entering unsafe state , So as to avoid deadlock .
3) Detect deadlock .
Such an approach does not require any restrictive measures in advance . It is not necessary to check whether the system has entered the unsafe area , This method allows the system to deadlock during execution .
But it can be detected by the detection mechanism set by the system , Timely detect the occurrence of deadlock , And accurately determine the processes and resources related to deadlock . Then take appropriate measures , Removed from the deadlocks that have occurred in the system .
4) Deadlock Relieving .
This is a measure matched with deadlock detection . When a deadlock is detected in the system . Process must be freed from deadlock .
The commonly used implementation method is to undo or suspend some processes , In order to recycle some resources , Then allocate these resources to the blocked process . Make it ready , To carry on .
Deadlock detection and removal measures , It is possible for the system to achieve better resource utilization and throughput , But it is also the most difficult to achieve .
Publisher : Full stack programmer stack length , Reprint please indicate the source :https://javaforall.cn/116453.html Link to the original text :https://javaforall.cn
边栏推荐
- 恶魔奶爸 指南帖——简易版
- [UVALive 6663 Count the Regions] (dfs + 离散化)[通俗易懂]
- 想杀死某个端口进程,但在服务列表中却找不到,可以之间通过命令行找到这个进程并杀死该进程,减少重启电脑和找到问题根源。
- 阿里云有奖体验:如何通过ECS挂载NAS文件系统
- Codeforces Round #296 (Div. 2) A. Playing with Paper[通俗易懂]
- How to choose fund products? What fund is suitable to buy in July 2022?
- Tensorflow2. How to run under x 1 Code of X
- Nebula importer data import practice
- 部署、收回和删除解决方式—-STSADM和PowerShell「建议收藏」
- OneSpin | 解决IC设计中的硬件木马和安全信任问题
猜你喜欢
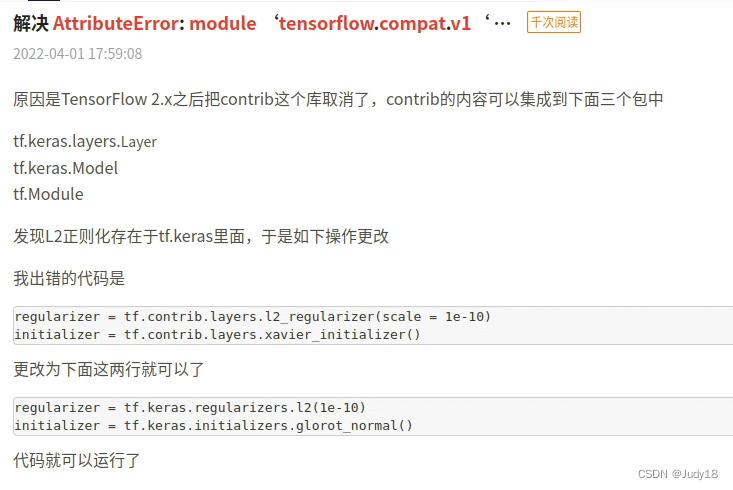
Tensorflow2. How to run under x 1 Code of X
使用高斯Redis实现二级索引
![Is embedded system really safe? [how does onespin comprehensively solve the IC integrity problem for the development team]](/img/af/61b384b1b6ba46aa1a6011f8a30085.png)
Is embedded system really safe? [how does onespin comprehensively solve the IC integrity problem for the development team]
恶魔奶爸 B3 少量泛读,完成两万词汇量+

Measure the height of the building

神兵利器——敏感文件发现工具
解决使用uni-app MediaError MediaError ErrorCode -5
Apifox interface integrated management new artifact
智能软件分析平台Embold
Nebula importer data import practice
随机推荐
Solve the problem that the executable file of /bin/sh container is not found
国家正规的股票交易app有哪些?使用安不安全
特征生成
部署、收回和删除解决方式—-STSADM和PowerShell「建议收藏」
嵌入式系统真正安全了吗?[ OneSpin如何为开发团队全面解决IC完整性问题 ]
awk处理JSON处理
FTP steps for downloading files from Huawei CE switches
Lingyun going to sea | saihe & Huawei cloud: jointly help the sustainable development of cross-border e-commerce industry
如何挑选基金产品?2022年7月份适合买什么基金?
Helix QAC 2020.2 new static test tool maximizes the coverage of standard compliance
H3C s7000/s7500e/10500 series post stack BFD detection configuration method
openGl超级宝典学习笔记 (1)第一个三角形「建议收藏」
阿洛的烦恼
I have to use my ID card to open an account. Is the bank card safe? I don't understand it
Phoenix JDBC
Écrivez une liste de sauts
UVA 11080 – Place the Guards(二分图判定)
华泰证券可以做到万一佣金吗,万一开户安全嘛
Jetty:配置连接器[通俗易懂]
You want to kill a port process, but you can't find it in the service list. You can find this process and kill it through the command line to reduce restarting the computer and find the root cause of