当前位置:网站首页>Xin'an Second Edition: Chapter 23 cloud computing security requirements analysis and security protection engineering learning notes
Xin'an Second Edition: Chapter 23 cloud computing security requirements analysis and security protection engineering learning notes
2022-07-06 17:34:00 【Moon Dream Studio】
One 、 The outline of this chapter requires
6. Cloud computing security requirements analysis and security protection engineering
6.1 Cloud computing security threats and needs analysis
6.1.1 Cloud computing security threats
◆ Cloud computing user security threats
◆ Cloud computing platform security threats
◆ Virtual machine security threats
◆ Cloud platform operation and maintenance security threats
6.1.2 Cloud computing security requirements
◆ Cloud operating system security
◆ Cloud service security compliance
◆ Multi tenant security isolation
◆ Data hosting
◆ Privacy protection
6.2 Cloud computing security protection mechanism and technical scheme
6.2.1 Cloud computing security level protection framework
◆ Security classification of cloud computing protection objects
◆ Cloud computing protection object security protection methods
◆ Cloud computing security level protection design framework
6.2.2 Cloud computing security protection
◆ Physical and environmental security ( Traditional physical environment security 、 Cloud computing platform physical location selection )
◆ Network and communication security 【 Network communication security 、 Network boundary security, etc , It involves infrastructure as a service (laaS) Security 】
◆ Device and computing security 【 Resource control 、 Image and snapshot protection , Involving platform as a service (PaaS) Security 】
◆ Application and data security 【 Software fault tolerance 、 Resource control 、 Interface security 、 Data integrity 、 Data confidentiality 、 Data backup recovery 、 Residual information protection 、 Personal information protection, etc , Involving software as a service (SaaS) Security 】
◆ Cloud user security ( Identity identification and authentication of cloud users 、 Cloud user access control )
6.2.3 Cloud computing security management
◆ Security policy and management system
◆ Safety management organization and personnel
◆ Safety management object
6.2.4 Cloud computing security operation and maintenance
◆ Cloud computing environment and asset operation and maintenance management
◆ Security vulnerability inspection and risk analysis of cloud computing system
◆ Cloud computing system security equipment and policy maintenance
◆ Cloud computing system security supervision
◆ Security monitoring and emergency response of cloud computing system
边栏推荐
- Start job: operation returned an invalid status code 'badrequst' or 'forbidden‘
- Akamai talking about risk control principles and Solutions
- Flink parsing (IV): recovery mechanism
- yarn : 无法加载文件 D:\ProgramFiles\nodejs\yarn.ps1,因为在此系统上禁止运行脚本
- 06 products and promotion developed by individuals - code statistical tools
- Flink analysis (I): basic concept analysis
- Connect to LAN MySQL
- Flink 解析(一):基础概念解析
- Re signal writeup
- List set data removal (list.sublist.clear)
猜你喜欢

全网最全tcpdump和Wireshark抓包实践
Take you hand-in-hand to do intensive learning experiments -- knock the level in detail
CTF逆向入门题——掷骰子

关于Selenium启动Chrome浏览器闪退问题
Akamai talking about risk control principles and Solutions
How does wechat prevent withdrawal come true?
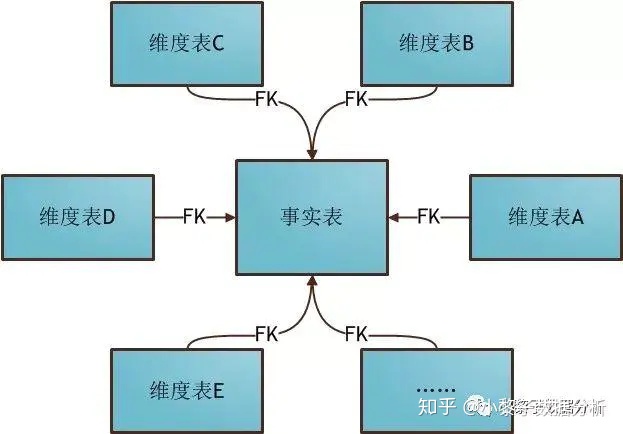
Models used in data warehouse modeling and layered introduction
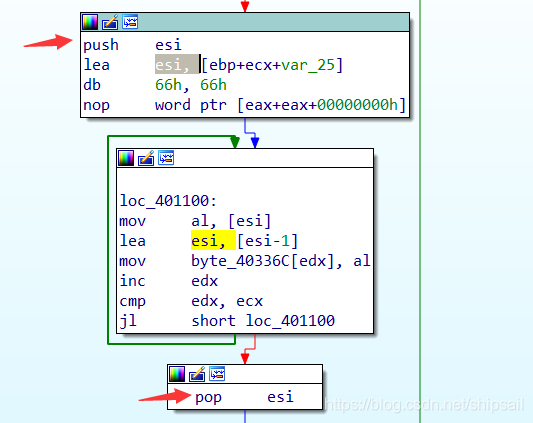
EasyRE WriteUp

Learn the wisdom of investment Masters
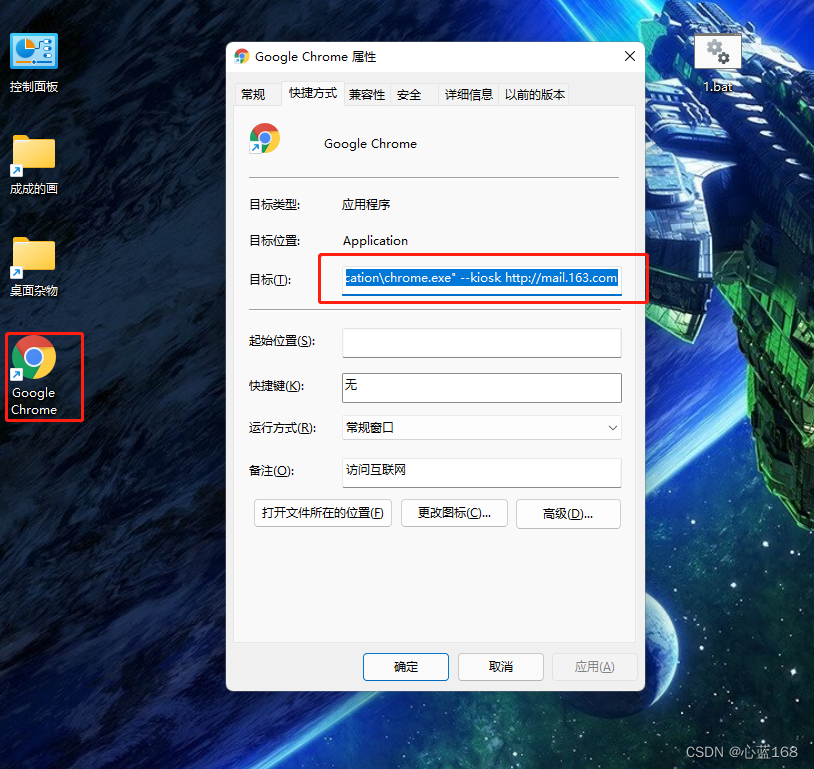
C version selenium operation chrome full screen mode display (F11)
随机推荐
Start job: operation returned an invalid status code 'badrequst' or 'forbidden‘
Flink 解析(五):State与State Backend
暑假刷题嗷嗷嗷嗷
connection reset by peer
Wu Jun's trilogy experience (VII) the essence of Commerce
[VNCTF 2022]ezmath wp
Programmer orientation problem solving methodology
【逆向初级】独树一帜
JVM 垃圾回收器之Serial SerialOld ParNew
C# WinForm系列-Button简单使用
Flink parsing (IV): recovery mechanism
Redis installation on centos7
About selenium starting Chrome browser flash back
Models used in data warehouse modeling and layered introduction
Redis快速入门
Program counter of JVM runtime data area
MySQL报错解决
Flink 解析(三):内存管理
07 personal R & D products and promotion - human resources information management system
Automatic operation and maintenance sharp weapon ansible Foundation