当前位置:网站首页>The most complete security certification of mongodb in history
The most complete security certification of mongodb in history
2022-07-07 04:04:00 【janyxe】
MongoDB List of articles
- In the history of the most complete MongoDB First knowledge of
- In the history of the most complete MongoDB Deployment of
- In the history of the most complete MongoDB And Mongo Shell Use
- In the history of the most complete MongoDB Safety certification
If this article is helpful to your development path , Please give me a compliment , Your support is my motivation to stick to blogging
Scan the QR code at the bottom of the article to get the e-book and the latest interview materials
Preface
This series of courses will take you in the form of face-to-face test questions Go deep into distributed topics MongoDB. This article takes you in depth MongoDB Safety certification
MongoDB Introduction to user permissions of
- MongoDB 2.4 Support RABC Model , Using role-based access control (Role-Based Access Control,RBAC) To manage user access to instances
RBAC( Role-based access control ): English name Role-Based Access Control
MongoDB role
| role | Permission to name |
|---|---|
| Database user role | read、readWrite |
| Database management role | dbAdmin、dbOwner、userAdmin |
| The role of cluster management | clusterAdmin、clusterManager、clusterMonitor、hostManager |
| Backup recovery role | backup、restore |
| All database roles | readAnyDatabase、readWriteAnyDatabase、userAdminAnyDatabase、dbAdminAnyDatabase |
| Super user role | root |
| Internal roles | __system |
MongoDB jurisdiction
| Authority Name | describe |
|---|---|
| read | Allows the user to read the specified database |
| readWrite | Allows users to read and write to a specified database |
| dbAdmin | Allows the user to execute administrative functions in the specified database , Like index creation 、 Delete , View statistics or access system.profile |
| dbOwner | Allows users to perform arbitrary operations in the specified database , increase 、 Delete 、 Change 、 Check etc |
| userAdmin | Allow the user to system.users A collection of written , Can be created in the specified database 、 Delete Divide and manage users |
| clusterAdmin | Only in admin Available in the database , Gives the user administrative rights to all sharding and copy-set related functions |
| readAnyDatabase | Only in admin Available in the database , Give the user read rights to all databases |
| readWriteAnyDatabase | Only in admin Available in the database , Gives the user read and write access to all databases |
| userAdminAnyDatabase | Only in admin Available in the database , That gives the user all the databases userAdmin jurisdiction |
| dbAdminAnyDatabase | Only in admin Available in the database , That gives the user all the databases dbAdmin jurisdiction |
| root | Only in admin Available in the database . Super account , Super authority |
MongoDB Suggestions for user permissions
- By default ,MongoDB The server does not start the user
Access right, Client connection MongoDB The server does not need security authentication , It can be operated at will, which has great risks - Production environment Turn on Safety Certification , Start from the command line and add
--auth, Or profile (mongod.conf) addauth=true - It is recommended to modify the default port in the production environment (27017)
- MongoDB It should be deployed in the Intranet environment ,bind_ip Parameters ( The default is localhost), According to client ip modify , Format :
bind_ip=1.1.1.1,2.2.2.2, prohibitbind_ipUse0.0.0.0orbind_ip_allSet totrue - The client operates the database , Should use the dbOwner( Database management role ) Account operation of , The administrator role is prohibited (/ Account with high permission ) Operating the database
Operate user role commands
show roles View the role list command
Concept
View role list
Command application
> show roles
{
"role" : "dbAdmin",
"db" : "test",
"isBuiltin" : true,
"roles" : [ ],
"inheritedRoles" : [ ]
}
{
"role" : "dbOwner",
"db" : "test",
"isBuiltin" : true,
"roles" : [ ],
"inheritedRoles" : [ ]
}
{
"role" : "enableSharding",
"db" : "test",
"isBuiltin" : true,
"roles" : [ ],
"inheritedRoles" : [ ]
}
{
"role" : "read",
"db" : "test",
"isBuiltin" : true,
"roles" : [ ],
"inheritedRoles" : [ ]
}
{
"role" : "readWrite",
"db" : "test",
"isBuiltin" : true,
"roles" : [ ],
"inheritedRoles" : [ ]
}
{
"role" : "userAdmin",
"db" : "test",
"isBuiltin" : true,
"roles" : [ ],
"inheritedRoles" : [ ]
}
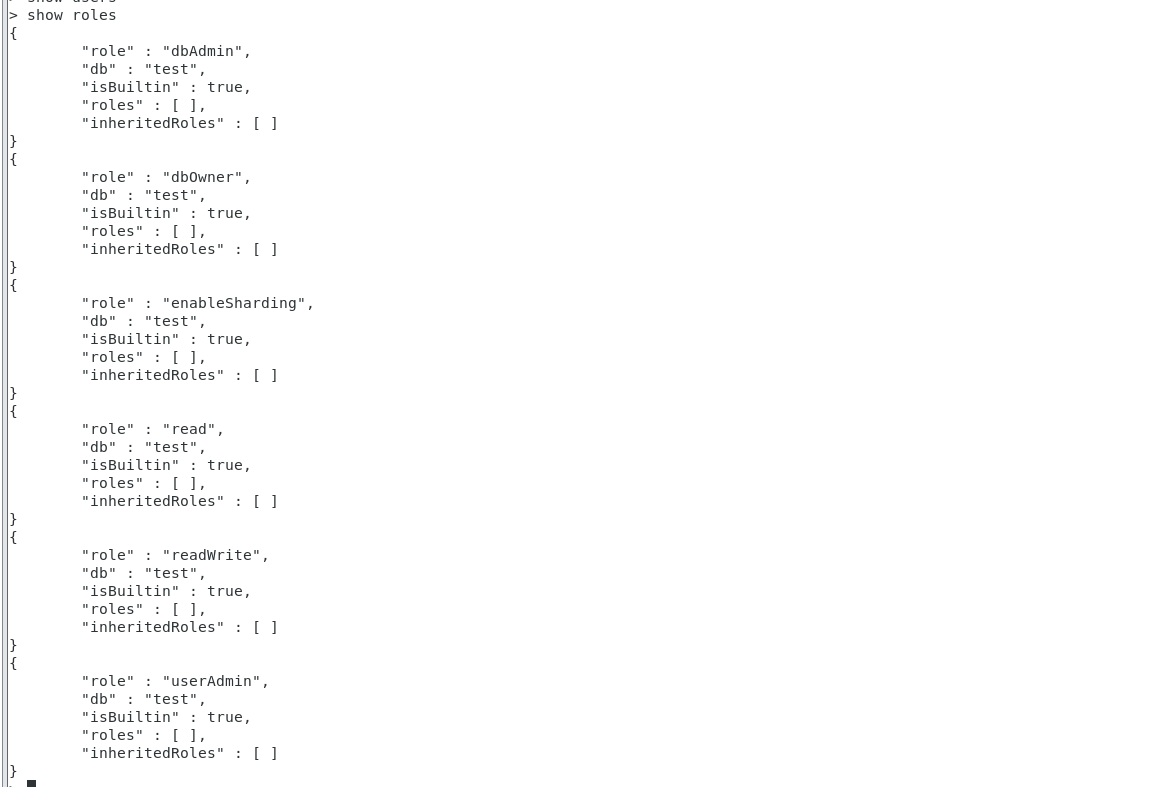
db.createUser( User information ) Create user command
Concept
Create user
Command format
db.createUser({user:“ user name ”,pwd:“ name ”,roles:[“ role ”]})
| Command parameter | meaning |
|---|---|
| user | User name |
| pwd | password |
| roles | Character list |
Command application
establish test library , And designate test The administrator of the library
> use test
switched to db test
> db.createUser({
user:"test",pwd:"test",roles:['dbOwner']})
uncaught exception: ReferenceError: dn is not defined :
@(shell):1:1
> use test
switched to db test
> db.createUser({
user:"test",pwd:"test",roles:['dbOwner']})
Successfully added user: {
"user" : "test", "roles" : [ "dbOwner" ] }
> show users
{
"_id" : "test.test",
"userId" : UUID("d9be5de9-8c28-4b2b-8d88-530be7846b14"),
"user" : "test",
"db" : "test",
"roles" : [
{
"role" : "dbOwner",
"db" : "test"
}
],
"mechanisms" : [
"SCRAM-SHA-1",
"SCRAM-SHA-256"
]
}
>
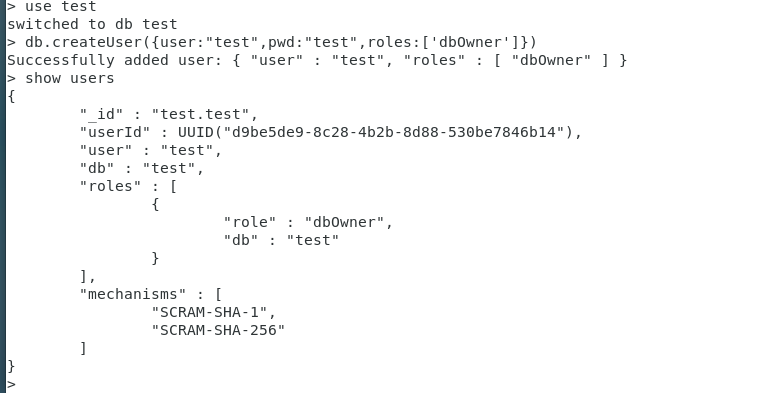
db.dropUser( User name ) Delete user command
Concept
Create user
Command format
db.dropUser(“ user name ”)
Command application
db.dropUser(“test”)
> use test
switched to db test
> dn.createUser({
user:"test",pwd:"test",roles:['dbOwner']})
uncaught exception: ReferenceError: dn is not defined :
@(shell):1:1
> use test
switched to db test
> db.createUser({
user:"test",pwd:"test",roles:['dbOwner']})
Successfully added user: {
"user" : "test", "roles" : [ "dbOwner" ] }
> show users
{
"_id" : "test.test",
"userId" : UUID("d9be5de9-8c28-4b2b-8d88-530be7846b14"),
"user" : "test",
"db" : "test",
"roles" : [
{
"role" : "dbOwner",
"db" : "test"
}
],
"mechanisms" : [
"SCRAM-SHA-1",
"SCRAM-SHA-256"
]
}
>
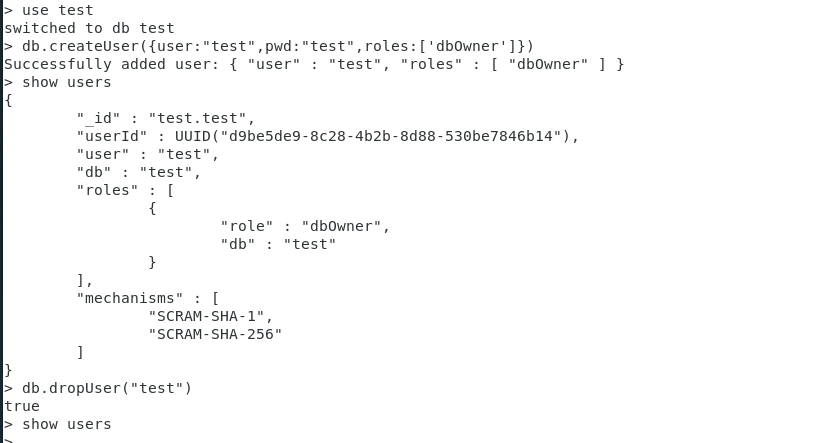
db.grantRolesToUser( User name ,[]) Authorize user rights command
Concept
Authorize user rights
Command format
db.grantRolesToUser(“ user name ”, [{
role: “ role code”,
db: “ Database name ”
},…
])
Command application
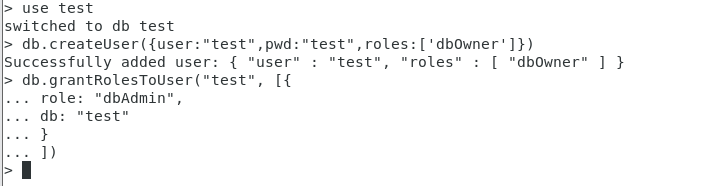
db.grantRolesToUser(“test”, [{
role: “dbAdmin”,
db: “test”
}
])
> use test
switched to db test
> db.createUser({
user:"test",pwd:"test",roles:['dbOwner']})
Successfully added user: {
"user" : "test", "roles" : [ "dbOwner" ] }
> db.grantRolesToUser("test", [{
... role: "dbAdmin",
... db: "test"
... }
... ])
>
Authorized account login command
Concept
Authorized account login
Command format
mongo MONGO_HOST:PORT -u USER -p PWD --authenticationDatabase=DB
| Command parameter | meaning |
|---|---|
| MONGO_HOST | Mongo Server side ip |
| PORT | Mongo Server side port |
| -u | user name |
| -p | password |
| –authenticationDatabase | Authorization database |
Command application
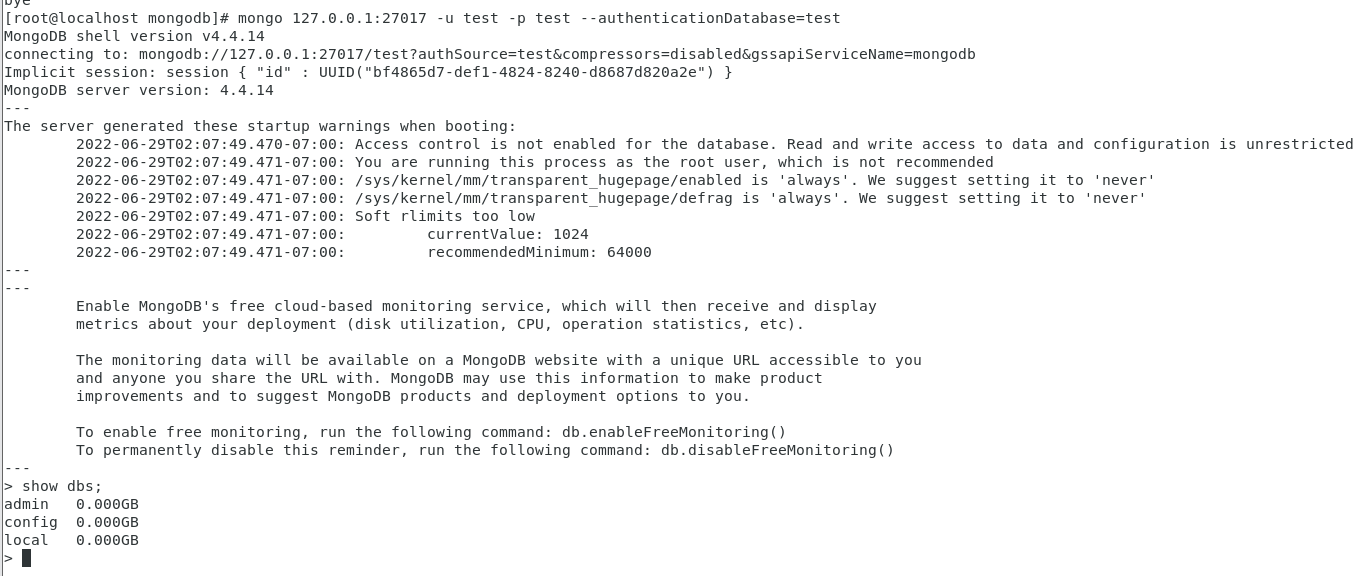
mongo 127.0.0.1:27017 -u test -p test --authenticationDatabase=test
[[email protected] mongodb]# mongo 127.0.0.1:27017 -u test -p test --authenticationDatabase=test
MongoDB shell version v4.4.14
connecting to: mongodb://127.0.0.1:27017/test?authSource=test&compressors=disabled&gssapiServiceName=mongodb
Implicit session: session {
"id" : UUID("bf4865d7-def1-4824-8240-d8687d820a2e") }
MongoDB server version: 4.4.14
---
The server generated these startup warnings when booting:
2022-06-29T02:07:49.470-07:00: Access control is not enabled for the database. Read and write access to data and configuration is unrestricted
2022-06-29T02:07:49.471-07:00: You are running this process as the root user, which is not recommended
2022-06-29T02:07:49.471-07:00: /sys/kernel/mm/transparent_hugepage/enabled is 'always'. We suggest setting it to 'never'
2022-06-29T02:07:49.471-07:00: /sys/kernel/mm/transparent_hugepage/defrag is 'always'. We suggest setting it to 'never'
2022-06-29T02:07:49.471-07:00: Soft rlimits too low
2022-06-29T02:07:49.471-07:00: currentValue: 1024
2022-06-29T02:07:49.471-07:00: recommendedMinimum: 64000
---
---
Enable MongoDB's free cloud-based monitoring service, which will then receive and display
metrics about your deployment (disk utilization, CPU, operation statistics, etc).
The monitoring data will be available on a MongoDB website with a unique URL accessible to you
and anyone you share the URL with. MongoDB may use this information to make product
improvements and to suggest MongoDB products and deployment options to you.
To enable free monitoring, run the following command: db.enableFreeMonitoring()
To permanently disable this reminder, run the following command: db.disableFreeMonitoring()
---
> show dbs;
admin 0.000GB
config 0.000GB
local 0.000GB
>
to see somebody for the first time , I don't know what to give you . Simply send hundreds of e-books and the latest interview materials , I wish you a better job , Scan the QR code below to get
边栏推荐
- 史上最全MongoDB之部署篇
- vim —- 自己主动的按钮indent该命令「建议收藏」
- 2022年电工杯B 题 5G 网络环境下应急物资配送问题思路分析
- Construction of Hisilicon universal platform: color space conversion YUV2RGB
- idea gradle lombok 报错集锦
- Redis source code learning (31), dictionary learning, dict.c (1)
- Class constant pool and runtime constant pool
- ABAP 动态内表分组循环
- tflite模型转换和量化
- PHP 实现根据概率抽奖
猜你喜欢
Web service performance monitoring scheme
Some thoughts on cross end development of kbone and applet
SQL injection -day15
Redis configuration and optimization of NoSQL
QT opens a file and uses QFileDialog to obtain the file name, content, etc
Construction of Hisilicon universal platform: color space conversion YUV2RGB
tflite模型转换和量化
再AD 的 界面顶部(菜单栏)创建常用的快捷图标
ggplot 分面的细节调整汇总
接口数据安全保证的10种方式
随机推荐
Implementation steps of docker deploying mysql8
使用切面实现记录操作日志
Learn how to use js to merge two objects into one object assign()
Class constant pool and runtime constant pool
史上最全MongoDB之安全认证
链表面试常见题
Free PHP online decryption tool source code v1.2
[dpdk] dpdk sample source code analysis III: dpdk-l3fwd_ 001
使用Thread类和Runnable接口实现多线程的区别
Using thread class and runnable interface to realize the difference between multithreading
Collection of idea gradle Lombok errors
First understand the principle of network
Some common software related
ABAP 动态内表分组循环
How to manage the expiration of enterprise distribution certificates- How to manage Enterprise Distribution certificate expiration?
如何编写一个程序猿另一个面试官眼前一亮的简历[通俗易懂]
termux设置电脑连接手机。(敲打命令贼快),手机termux端口8022
ggplot 分面的细节调整汇总
未来发展路线确认!数字经济、数字化转型、数据...这次会议很重要
Restore backup data on GCS with br