当前位置:网站首页>Restore backup data on GCS with tidb lightning
Restore backup data on GCS with tidb lightning
2022-07-07 04:02:00 【Tianxiang shop】
This document describes how to put Kubernetes through TiDB Operator The backup data is restored to TiDB colony .
The recovery method used in this article is based on TiDB Operator v1.1 And above CustomResourceDefinition (CRD) Realization , The bottom layer uses TiDB Lightning TiDB-backend To recover data .
TiDB Lightning It is a high-speed import of full data to TiDB Clustering tools , Available from local disk 、Google Cloud Storage (GCS) or Amazon S3 Cloud disk reads data . at present ,TiDB Lightning Support three kinds of backend :Importer-backend、Local-backend、TiDB-backend. The method introduced in this article uses TiDB-backend. About the differences and choices of these three backend , see also TiDB Lightning file . If you want to use Importer-backend perhaps Local-backend Import data , see also Use TiDB Lightning Import cluster data .
The following examples will be stored in GCS The cluster backup data on the specified path on is restored to TiDB colony .
Use scenarios
If you need from GCS Export backup data to TiDB colony , And have the following requirements for data recovery , You can use the recovery scheme introduced in this article :
- We hope to recover with low resource utilization and low network bandwidth utilization , And it's acceptable 50 GB/ Hours of recovery
- It is required to meet ACID
- During backup TiDB The cluster can still provide services
Preparation before recovery
Before data recovery , You need to prepare to restore the environment , And have the relevant permissions of the database .
Environmental preparation
Download the file backup-rbac.yaml, And execute the following command in
test2This namespace Create the required for recovery RBAC Related resources :kubectl apply -f backup-rbac.yaml -n test2Remote storage access authorization .
Reference resources GCS Account Authorization Authorized access GCS Remote storage .
establish
restore-demo2-tidb-secretsecret, The secret Store to access TiDB Clustered root Account and key :kubectl create secret generic restore-demo2-tidb-secret --from-literal=user=root --from-literal=password=${password} --namespace=test2
Required database permissions
Use TiDB Lightning take GCS Restore the backup data on to TiDB Before cluster , Make sure you have the following permissions to back up the database :
| jurisdiction | Scope |
|---|---|
| SELECT | Tables |
| INSERT | Tables |
| UPDATE | Tables |
| DELETE | Tables |
| CREATE | Databases, tables |
| DROP | Databases, tables |
| ALTER | Tables |
Restore the specified backup data to TiDB colony
establish restore custom resource (CR), Restore the specified backup data to TiDB colony :
kubectl apply -f restore.yamlrestore.yamlThe contents of the document are as follows :--- apiVersion: pingcap.com/v1alpha1 kind: Restore metadata: name: demo2-restore namespace: test2 spec: to: host: ${tidb_host} port: ${tidb_port} user: ${tidb_user} secretName: restore-demo2-tidb-secret gcs: projectId: ${project_id} secretName: gcs-secret path: gcs://${backup_path} # storageClassName: local-storage storageSize: 1GiThe above examples will be stored in GCS Specify the path on
spec.gcs.pathBackup data to TiDB colonyspec.to.host. About GCS You can refer to GCS Field is introduced .more
RestoreCR For detailed explanation of fields, please refer to Restore CR Field is introduced .Create good
RestoreCR After that, you can view the status of recovery through the following command :kubectl get rt -n test2 -owide
Be careful
TiDB Operator Will create a PVC, For data recovery , The backup data will be downloaded from the remote storage to PV, And then recover . If you want to delete this after the recovery PVC, You can refer to Delete resources First restore Pod Delete , Then take it. PVC Delete .
边栏推荐
- Food Chem|深度学习根据成分声明准确预测食品类别和营养成分
- termux设置电脑连接手机。(敲打命令贼快),手机termux端口8022
- ERROR: Could not build wheels for pycocotools which use PEP 517 and cannot be installed directly
- 2022中青杯数学建模B题开放三孩背景下的生育政策研究思路
- Tflite model transformation and quantification
- Preprocessing - interpolation
- Confirm the future development route! Digital economy, digital transformation, data This meeting is very important
- HW notes (II)
- 【knife-4j 快速搭建swagger】
- On file uploading of network security
猜你喜欢
未来发展路线确认!数字经济、数字化转型、数据...这次会议很重要
史上最全MongoDB之Mongo Shell使用
Machine learning notes - bird species classification using machine learning
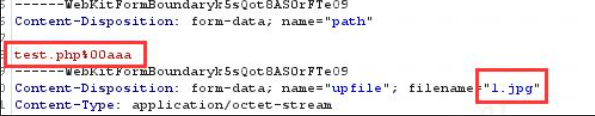
浅谈网络安全之文件上传

Tencent cloud native database tdsql-c was selected into the cloud native product catalog of the Academy of communications and communications
ggplot 分面的细节调整汇总
Que savez - vous de la sérialisation et de l'anti - séquence?
Mobile measurement and depth link platform - Branch
Clock in during winter vacation

2022夏每日一题(一)
随机推荐
再AD 的 界面顶部(菜单栏)创建常用的快捷图标
使用 BR 备份 TiDB 集群到 GCS
ABAP Dynamic Inner table Group cycle
未来发展路线确认!数字经济、数字化转型、数据...这次会议很重要
GPT-3当一作自己研究自己,已投稿,在线蹲一个同行评议
NoSQL之Redis配置与优化
C task expansion method
2022年上半年HIT行业TOP50
1.19.11.SQL客户端、启动SQL客户端、执行SQL查询、环境配置文件、重启策略、自定义函数(User-defined Functions)、构造函数参数
Create commonly used shortcut icons at the top of the ad interface (menu bar)
POJ培训计划2253_Frogger(最短/floyd)
[leetcode]Spiral Matrix II
web服务性能监控方案
PHP implements lottery according to probability
Mobile measurement and depth link platform - Branch
HW notes (II)
Summer 2022 daily question 1 (1)
How to manage the expiration of enterprise distribution certificates- How to manage Enterprise Distribution certificate expiration?
PHP lightweight Movie Video Search Player source code
easyui出口excel无法下载框弹出的办法来解决