当前位置:网站首页>Review and arrangement of HCIA
Review and arrangement of HCIA
2022-07-07 11:57:00 【qq_ fifty-two million one hundred and seventy-eight thousand fi】
Abstract language ( written words , video , Pictures, etc ) --- Electrical signals ( Languages that computers can recognize )
Abstract language --- code application layer
code --- Binary system The presentation layer
Binary system --- Electrical signals medium ( Hardware ) Access control layer
Process electrical signals The physical layer
OSI/RM -- Open system interconnection reference model
ISO --- International Organization for Standardization (1979 year ) //IBM First to launch SNA Reference model
The core idea --- layered
--- Different functions belonging to the same layer have the same or similar purposes and functions ; Each layer provides higher-level services on the basis of the services provided by the next layer , The top layer provides human-computer interaction application services
Open system interconnection reference model
application layer — Provide various application services , Convert abstract language into code , Provide interactive instructions for others
The presentation layer — Convert the encoding to binary
The session layer — Maintain session links between web applications and web servers
Transport layer — Realize end-to-end communication — Port number —0—6535 — among 0 Not as a port of the transport layer
No. use , therefore , The real value range of the port number is 1—65535—— among 1—1023 It's called a well-known port
Number — SPORT, DPORT
The network layer — Use IP Address realizes logical addressing between hosts —— SIP, DIP
obtain DIP Address method :
1, Know the server directly P Address
2, Access the server through the domain name
3, Access the server through the application
4, radio broadcast
Data link layer — Control physical hardware , Convert binary to electrical signal . In Ethernet , The data link layer needs to pass MAC Address in Row physical addressing -48 Bit binary structure
1, The only global ;2, use the same pattern
obtain DMAC Methods — ARP agreement —-— Address resolution protocol
positive ARP — adopt IP The address for MAC Address
First , The host sends... In the form of broadcast ARP request , Based on the known P Address , Call for MAC Address . All devices in the broadcast domain can receive request packets , All devices that receive packets will record the source in the packet P Address and source MAc The correspondence of the address is related to the local ARP The cache table . after , Look at the request p Address , If it's local P Address , Will be performed ARP The reply , Local MAc Address inform . If it's not local P Address , The packet will be discarded directly . And , When sending data again , Give priority to local ARP Cache table , If there are records in the table , Then the information will be sent directly according to the record , If there is no record , Then send ARP Request package acquisition MAC Address .
reverse ARP … adopt MAC The address for P Address
free ARP ——1, Self introduction. ;2, Detect address conflicts .
The physical layer —— Handle the transmission of electrical signals
TCP/IP Model
TCP/IP Protocol cluster
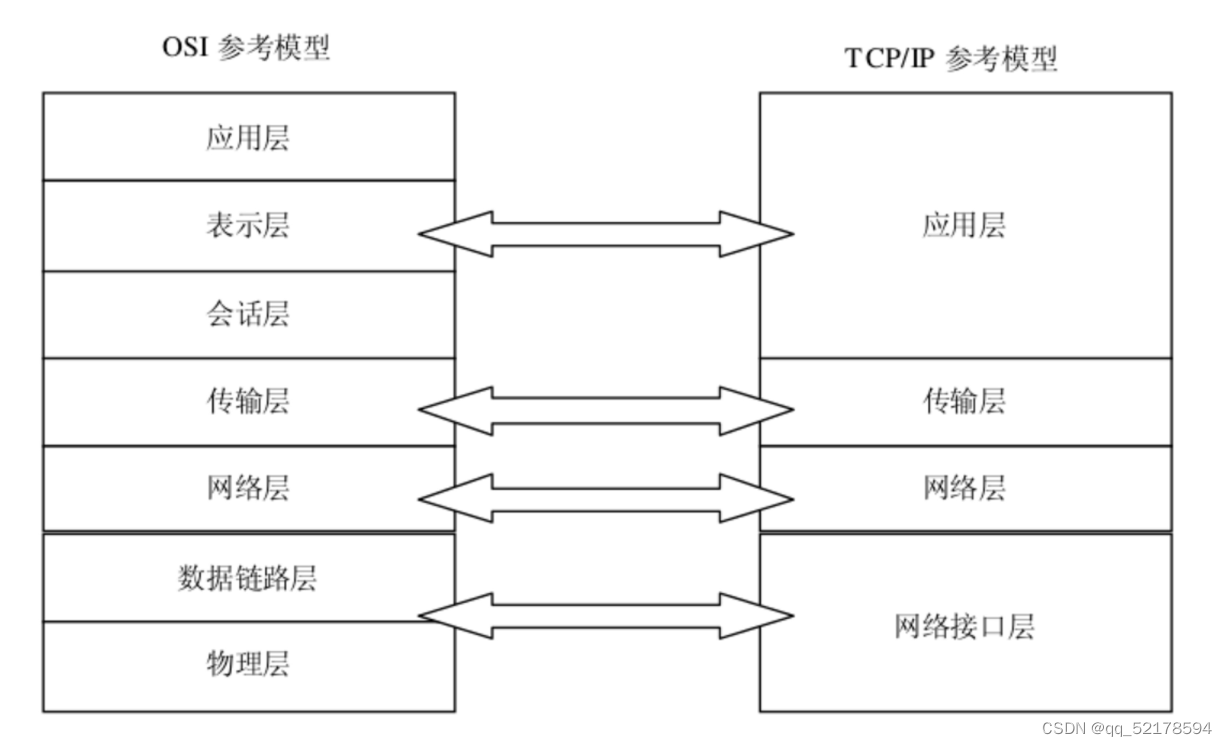
Four layer model ---- TCP/IP The standard model
Five layer model ----TCP/IP peer model
PDU Protocol data unit //TCP Protocol cluster
L1PDU
L2PDU
… L7PDU
application layer --- message
Transport layer --- paragraph
The network layer --- package
Data link layer --- frame
The physical layer --- Bit stream
Encapsulation and de encapsulation
application layer ---- According to the application requirements
Transport layer --- Port number -- TCP/UDP
The network layer --- IP Address --- IP
Data link layer --- MAC Address --- Ethernet protocol Ethernet : Early LAN
Solutions for , Now it is also used in Wan . Is to rely on MAC Address addressable Layer-1 and layer-2 networks .
The physical layer --- No encapsulation required , Binary conversion to electrical signal
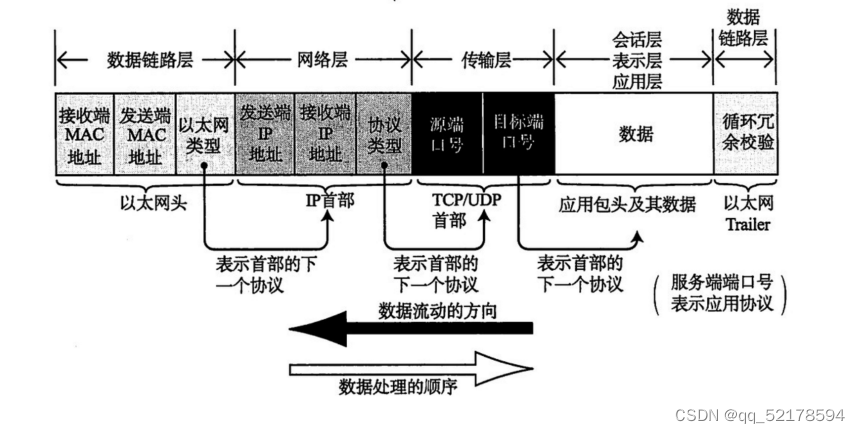
TCP/P The model supports layer collapse encapsulation , And in the OSI Not in the middle ,… Cross layer packaging is generally used in close proximity direct connection devices
Send messages between devices , It can improve the forwarding efficiency .
1, Cross four layer packaging - OSPF -— 89
2, Span three , Four layer package —— STP
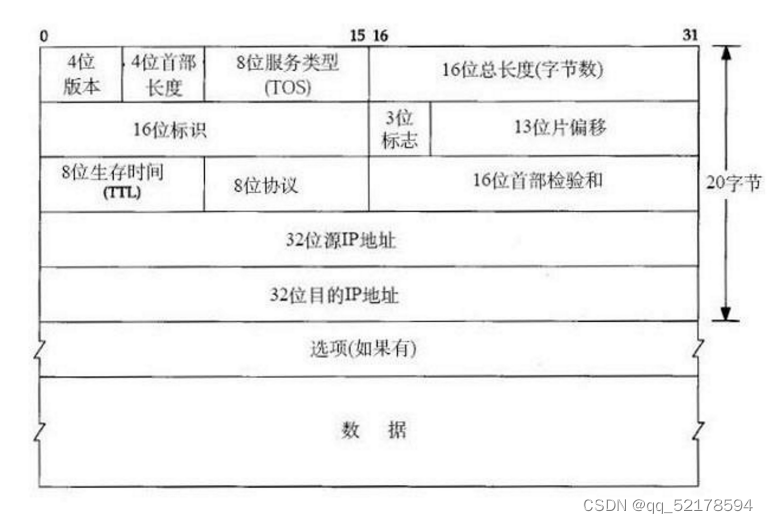
Ethernet Ⅱ Type frame ( Data link layer )
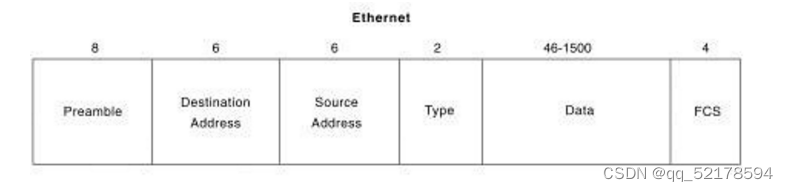
IEEE:
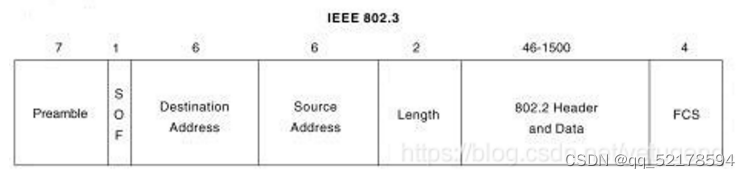
SOF -— Frame header delimiter
DSAP -… Indicate what protocol the upper layer of the device receiving the data frame uses to process the data
SAP —… Indicates the protocol generated by the upper layer of the device that sends the data frame
Control - 1, Connectionless mode ; 2, Connection oriented pattern —— It can realize the fragment reorganization of data packets
Type --- The protocol type used by the upper layer
Preamble --- Forerunner
IP Address
IPV4 -—32 Bit binary structure —- dotted decimal
IPV6 - 128 Bit binary structure —- It's hexadecimal
Network bit —-- The network bits are the same , It means in the same broadcast domain
Host bit —-- In the same broadcast domain , Use the host bit to distinguish different hosts
Subnet mask —-— Continuous 1 And continuous 0 form ,1 On behalf of network bit ,0 Represents the host bit
IP Classification of addresses --------A,B,C,D,E
A,B,C --- Unicast address --- It can be used as a source IP Can also be a goal IP( No category IP)
D --- Multicast address --- Only as a goal IP Use , Cannot be used as a source IP Use
E --- Reserved address
unicast --- one-on-one
Multicast -- One to many ( The same multicast group )
radio broadcast -- A pair of all ( All in the broadcast domain )
A:0XXX XXXX (0 - 127 ) 1 - 126
B:10XX XXXX 128 - 191
C:110X xxxx 192 - 223
D:1110 XXXX 224 - 239
E:1111 XXXX 240 - 255
A:255.0.0.0
B:255.255.0.0
C:255.255.255.0
stay IP In the address space , Part of it IP The address is called private IP Address ( The private network IP Address ), The rest are called
public IP Address ( Public network IP Address )-— We habitually use private networks P The network built by address is called private
network , Use the public network IP The network built by address is called public network .-— Private address can be reused , But in
The uniqueness of the private network must be guaranteed .
A: 10.0.0.0—10.25.255.255 amount to 1 individual A Class segment
B: 172.16.0.0—172.31.25.255 amount to 16 individual B Class segment
C: 192.168.0.0—192.168.255.255 amount to 256 individual C Class segment
special IP Address
1,127.0.0.0 - 127.255.255.255 --- Loopback address ---- It is mainly used to detect , test
2,255.255.255.255 --- Restricted broadcast address --- Limited by routers --- Only as a target IP Use
3, All the hosts 1 --- 192.168.1.255 --- Direct address ( Cross routing )--- Only for the purpose mark IP Use ( In principle, it will forward , For security reasons, it will not forward )
4, All the hosts 0 --- 192.168.1.0 --- Network segment --- network number
5,0.0.0.0 ---- 1, It means there is no IP(DHCP You can use );2, Can represent all IP
6,169.254.0.0/16 --- Automatic private address / Local link address ( Communication depends on the surrounding network environment )
ARP The classification of
positive ARP: adopt IP The address for MAC Address
reverse ARP: adopt MAC The address for IP Address RARP
free ARP: Use positive ARP working principle 1, Self introduction. ;2, Detect address conflicts
VLSM --- Variable length subnet mask ( Subnet partition )
CIDR --- No inter domain routing ( Summary )
Take the same , Go different
Static routing : Routing entries manually configured by the network administrator
Dynamic routing : All routers run the same routing protocol , Then communicate through routers , Finally, the routing entry is calculated .
Advantages of static routing :1, No additional resources are required
2, Static routing is more secure
3, The routing administrator selects , Relatively better control
shortcoming :1, In a complex network environment , Large amount of configuration
2, Static routing cannot automatically converge based on the change of network topology
Advantages of dynamic routing :1, Dynamic routing can automatically converge based on the change of topology
2, Simple configuration
shortcoming :1, Need additional resources
2, Dynamic routing needs information transmission , So it's easier to use , Cause safety problems
3, The routing of dynamic routing is calculated by algorithm , Not necessarily the best path , There may even be a loop .
Basic configuration of static routing :
Method 1 :[rlip route—static 192.168.3.0 24 192.168.2.2 —- You need to recursively find the interface
Method 2 : [1lip route—static 192.168.3.02 4 GigabitEthernet 0/0/1- The agent needs to be activated ARP
[r2—GigabitEtherneto/O/0larp—proxy enable — The activation agent ARP —-— ARP A kind of , After activation , The router will check the received ARP Request package , be based on ARP Requested P Address view local routing table , If the local route Can be up to , Will pretend to be the other party's P Address reply ARP The reply . To his own MAC Address reply , after , The data is sent to the route On the device , The router forwards .
Method 3 :[r1]ip route—static 192.168.3.0 24 GigabitEthernet 0/0/1 192.168.2.2— Recursive search is not required look for
Method four : [rl]ip route—static 192.168.4.0 24 192.168.3.2—-— Write down two jumps , You need to look up recursively
Extended configuration of static routing :
1, Load balancing —— When a router accesses the same target with multiple paths with similar overhead , You can make the flow
After splitting the quantity, go from multiple paths at the same time , Play the effect of superimposing bandwidth .
2, Manual summary —— When a router can access multiple consecutive subnets , If they all pass the same next jump , be
These network segments can be summarized and calculated , Directly write a static route to the summary network segment . You can reduce
Reduce the number of routing table entries , Improve forwarding efficiency .
3, The route is black - In the river , The knowledge fruit contains the same segment that does not exist in the middle process of the same name , It may cause traffic
Go without return , Waste link resources .
Reasonable division and aggregation can reduce the generation of routing black holes
4, Default route —— A route that does not limit the destination . When looking up the table , If all routes do not match , Will
Match default route .
[r1]ip route-static 0.0.0.0 0 12.0.0.2
5, Empty interface routing —— Prevent routing black holes and default routes from meeting and leaving the ring . Configure a black hole router
The route that reaches the summary network segment and points to the empty interface .
1, NUL0 If the outgoing interface of a route entry points to an empty interface , Then match to this route information
Datagrams will be discarded
2, Matching principle of routing table —— The longest match principle ( The principle of exact match )
[r1]ip route-static 192.168.0.0 2 NULL 0
6, Floating static routing —— By modifying the default priority of static routing , Achieve the effect of backup
[r2]ip route-static 192.168.0.0 22 21.0.0.1 preference 61
边栏推荐
- Superscalar processor design yaoyongbin Chapter 9 instruction execution excerpt
- Detailed explanation of debezium architecture of debezium synchronization
- In depth learning autumn recruitment interview questions collection (1)
- 相机标定(1): 单目相机标定及张正友标定基本原理
- 请查收.NET MAUI 的最新学习资源
- STM32F1与STM32CubeIDE编程实例-315M超再生无线遥控模块驱动
- [Yugong series] go teaching course 005 variables in July 2022
- Rationaldmis2022 advanced programming macro program
- In my limited software testing experience, a full-time summary of automation testing experience
- Reasons for the failure of web side automation test
猜你喜欢
![108.网络安全渗透测试—[权限提升篇6]—[Windows内核溢出提权]](/img/c0/8a7b52c46eadd27cf4784ab2f32002.png)
108.网络安全渗透测试—[权限提升篇6]—[Windows内核溢出提权]
MySQL安装常见报错处理大全
5V串口接3.3V单片机串口怎么搞?
![112. Network security penetration test - [privilege promotion article 10] - [Windows 2003 lpk.ddl hijacking rights lifting & MSF local rights lifting]](/img/b6/6dfe9be842204567096d1f4292e8e7.png)
112. Network security penetration test - [privilege promotion article 10] - [Windows 2003 lpk.ddl hijacking rights lifting & MSF local rights lifting]
![[shortest circuit] acwing1128 Messenger: Floyd shortest circuit](/img/a4/783bdcc2b97938efc77b7da6442866.png)
[shortest circuit] acwing1128 Messenger: Floyd shortest circuit
powershell cs-UTF-16LE编码上线
. Net Maui performance improvement
Some opinions and code implementation of Siou loss: more powerful learning for bounding box regression zhora gevorgyan
About how to install mysql8.0 on the cloud server (Tencent cloud here) and enable local remote connection

请查收.NET MAUI 的最新学习资源
随机推荐
Flet tutorial 17 basic introduction to card components (tutorial includes source code)
[question] Compilation Principle
Poor math students who once dropped out of school won the fields award this year
R语言使用quantile函数计算评分值的分位数(20%、40%、60%、80%)、使用逻辑操作符将对应的分位区间(quantile)编码为分类值生成新的字段、strsplit函数将学生的名和姓拆分
Talk about SOC startup (x) kernel startup pilot knowledge
Explore cloud database of cloud services together
Steps of redis installation and self startup configuration under CentOS system
如何理解服装产业链及供应链
Programming examples of stm32f1 and stm32subeide -315m super regenerative wireless remote control module drive
What is high cohesion and low coupling?
When sink is consumed in mysql, the self incrementing primary key has been set in the database table. How to operate in Flink?
What development models did you know during the interview? Just read this one
《通信软件开发与应用》课程结业报告
110.网络安全渗透测试—[权限提升篇8]—[Windows SqlServer xp_cmdshell存储过程提权]
Rationaldmis2022 array workpiece measurement
Ask about the version of flinkcdc2.2.0, which supports concurrency. Does this concurrency mean Multiple Parallelism? Now I find that mysqlcdc is full
Various uses of vim are very practical. I learned and summarized them in my work
【最短路】ACwing 1127. 香甜的黄油(堆优化的dijsktra或spfa)
Easyui学习整理笔记
Blog moved to Zhihu