当前位置:网站首页>Software designer: 03 database system
Software designer: 03 database system
2022-07-05 07:45:00 【Laptoy】
List of articles
- One 、 Three level mode - Two level mapping
- Two 、 Database design process
- 3、 ... and 、ER Model
- Four 、 Relational algebra
- 5、 ... and 、 Normalization theory
- 6、 ... and 、 concurrency control
- 7、 ... and 、 Integrity constraints
- 8、 ... and 、 database security
- Nine 、 Database backup
- Nine 、 Data warehouse and data mining
- Ten 、 Anti normalization
- 11、 ... and 、 Basic concept of big data
One 、 Three level mode - Two level mapping
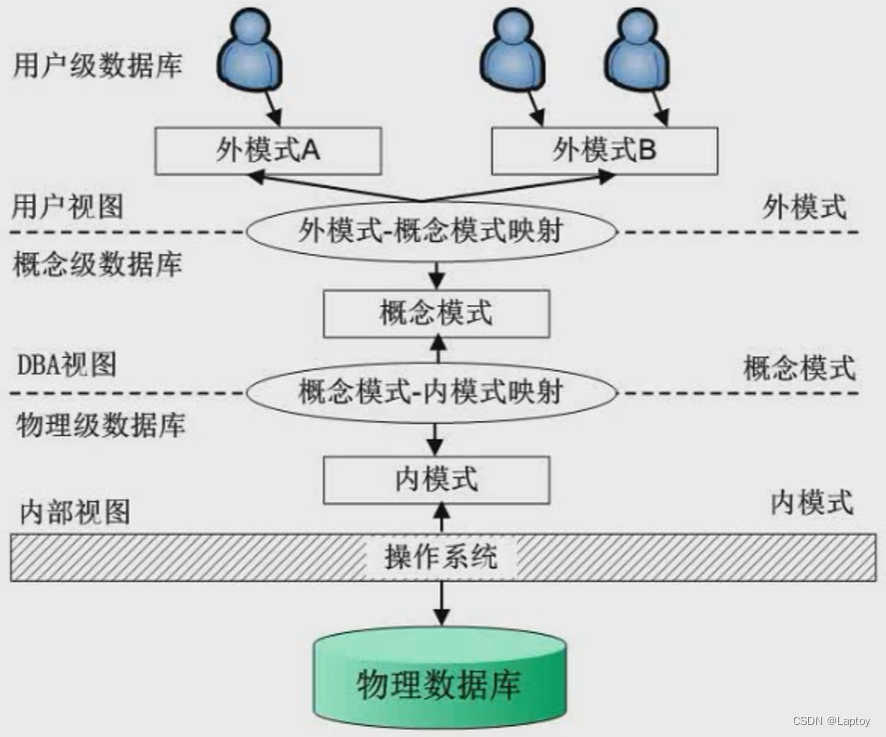
1.1、 Three level mode
Pattern : Also known as conceptual patterns , It is a description of the logical structure and characteristics of all data in the database . Only the description of type is involved , No specific values are involved . A specific value of a conceptual pattern is called an instance of the pattern , There can be many instances of the same pattern . The data definition language for describing the schema is : Pattern DDL.
External mode : Also known as user mode or sub mode , It is the interface between user and database system , It is the description of the part of data seen by the user . The data definition language for describing the external schema is : External mode DDL.
Internal mode : Also known as storage mode , Is a description of the physical structure and storage of data , Is the representation of data in the database , Define all internal record types 、 Index and document organization , And the details of data control . The data definition language that describes the inner schema is : Internal mode DDL.
In a database system , The external mode can have multiple , There is only one mode and internal mode !!!
External mode —— Pattern —— Internal mode They correspond to each other : View —— Basic table —— file
1.2、 Two level image
First , The independence of data is determined by DBMS The two-level image function of .
Pattern / Internal mode image : Between the conceptual level and the internal level , Realize the mutual transformation between mode and internal mode . Ensure the accuracy of data Physical independence .
Pattern / External mode image : It exists between the external level and the concept level , It realizes the mutual transformation between external modes and modes . Ensure the accuracy of data Logical independence .( For example, creating a view does not change the original situation of the data table )
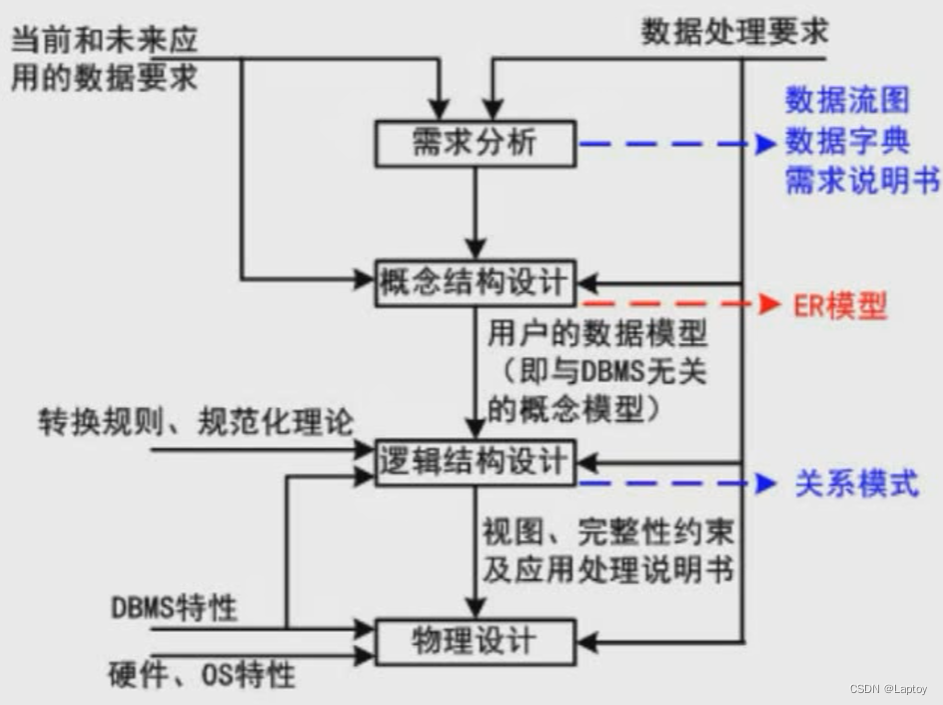
Two 、 Database design process
3、 ... and 、ER Model
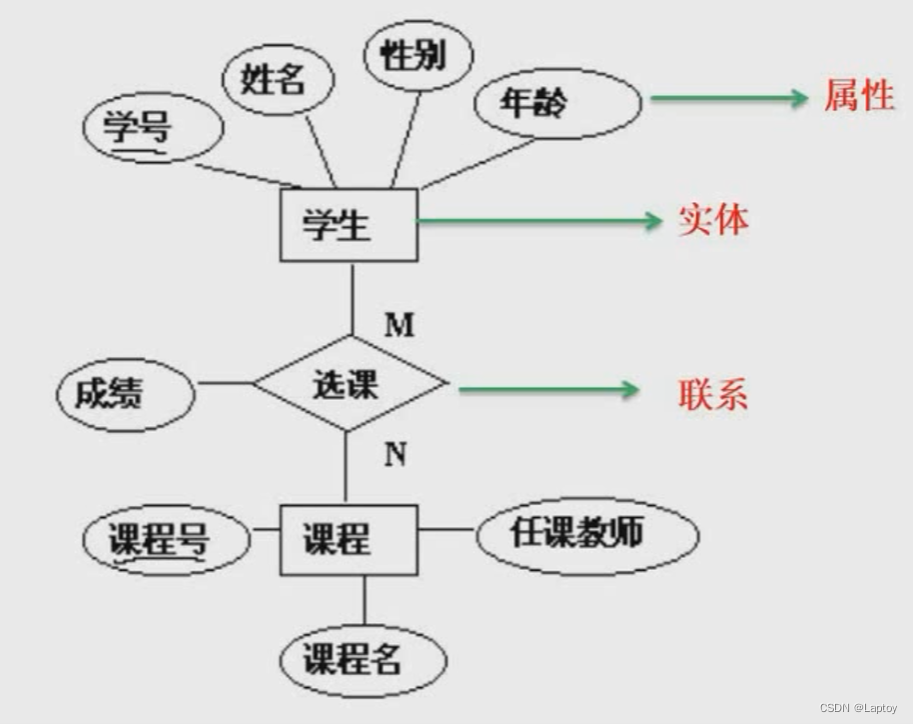
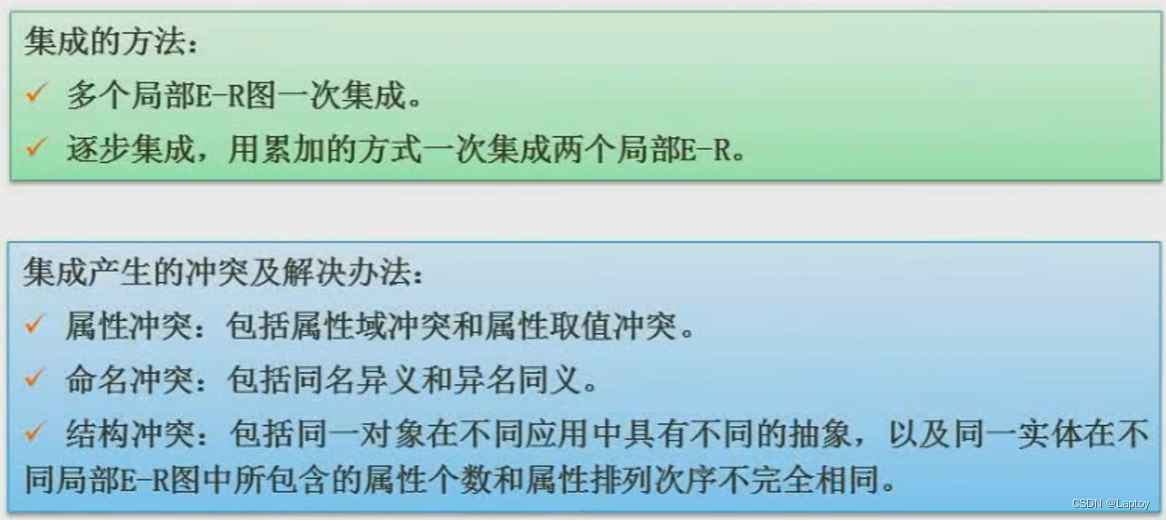
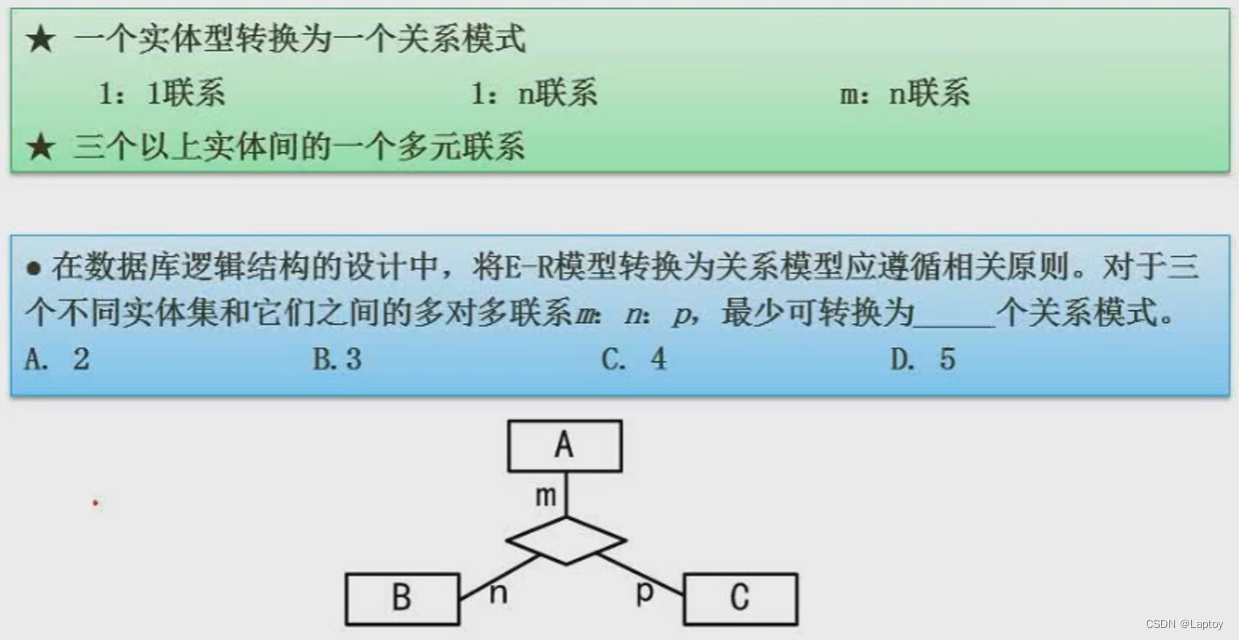
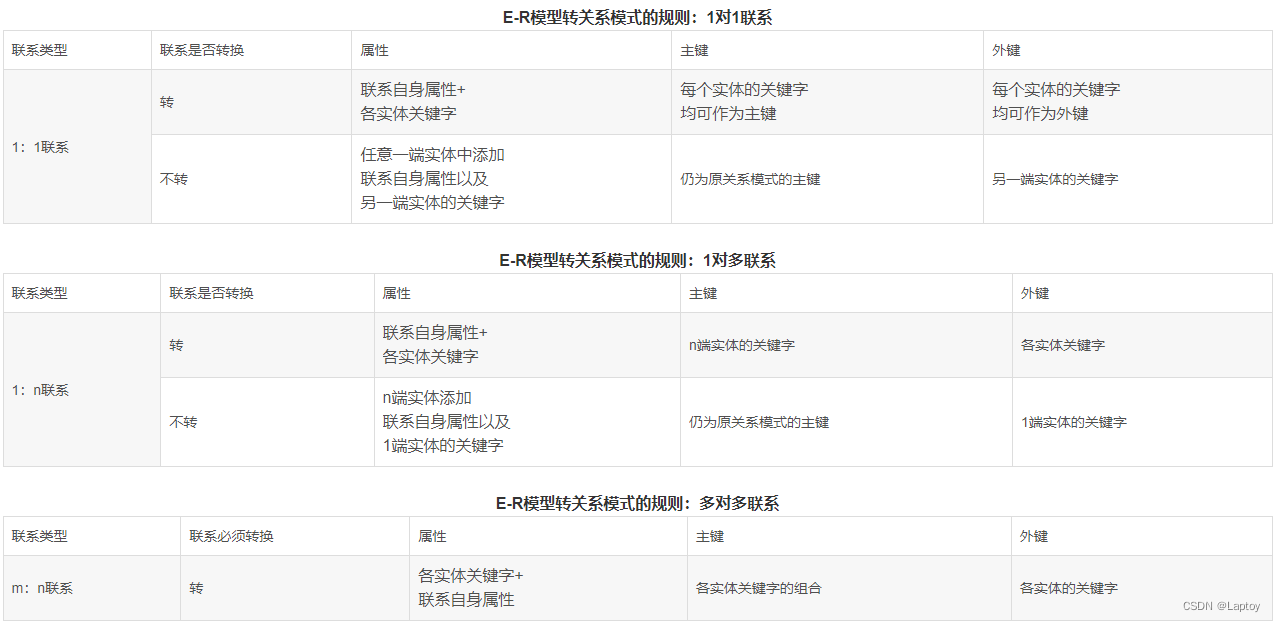
stay E-R In the model , Each entity must be transformed into a relational schema , And the connection is divided into (1:1,1:n,m:n) Three , The first two can be turned or not , The third is that we must turn . So the above example ,A、B、C The three entities are many to many to many connections , So you have to switch , That is, it can be converted into 4 A relationship model . The specific conversion rules are shown in the following three tables :
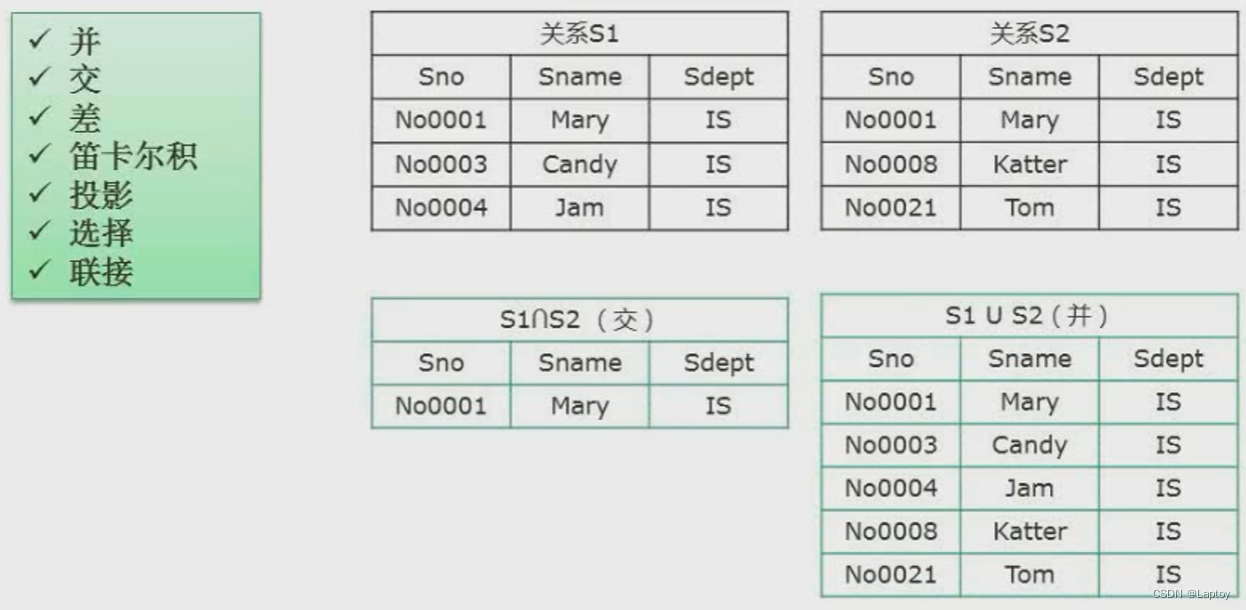
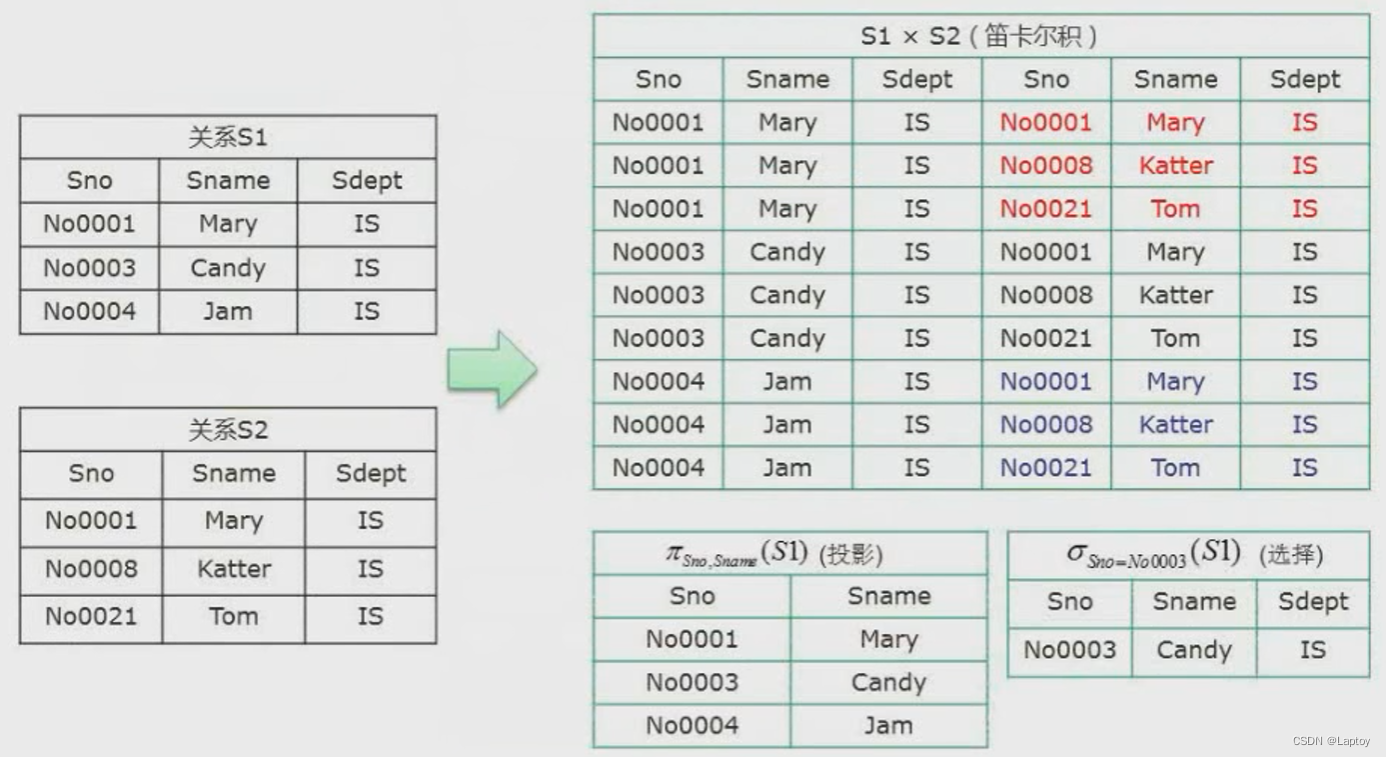
Four 、 Relational algebra
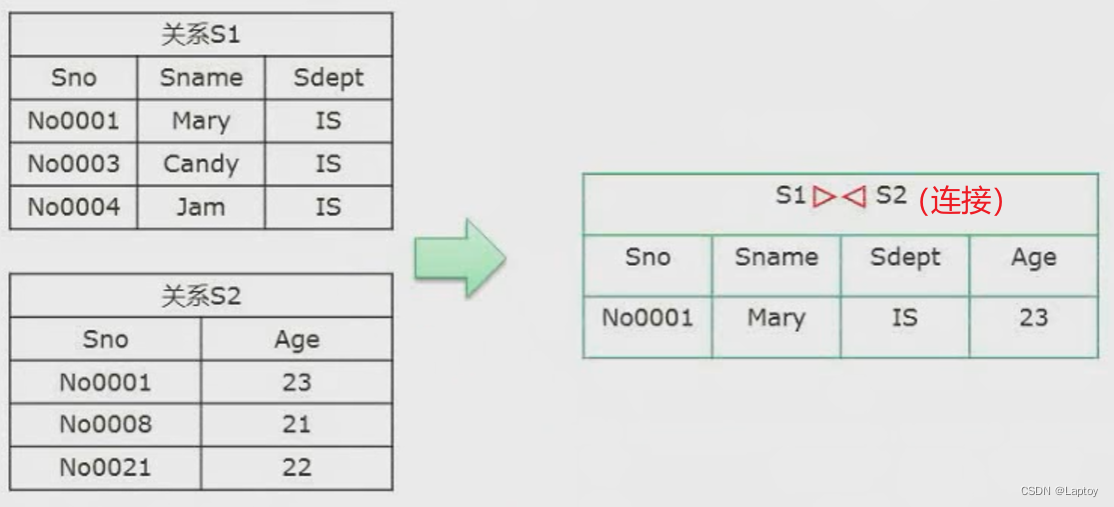
5、 ... and 、 Normalization theory
5.1、 Function dependency
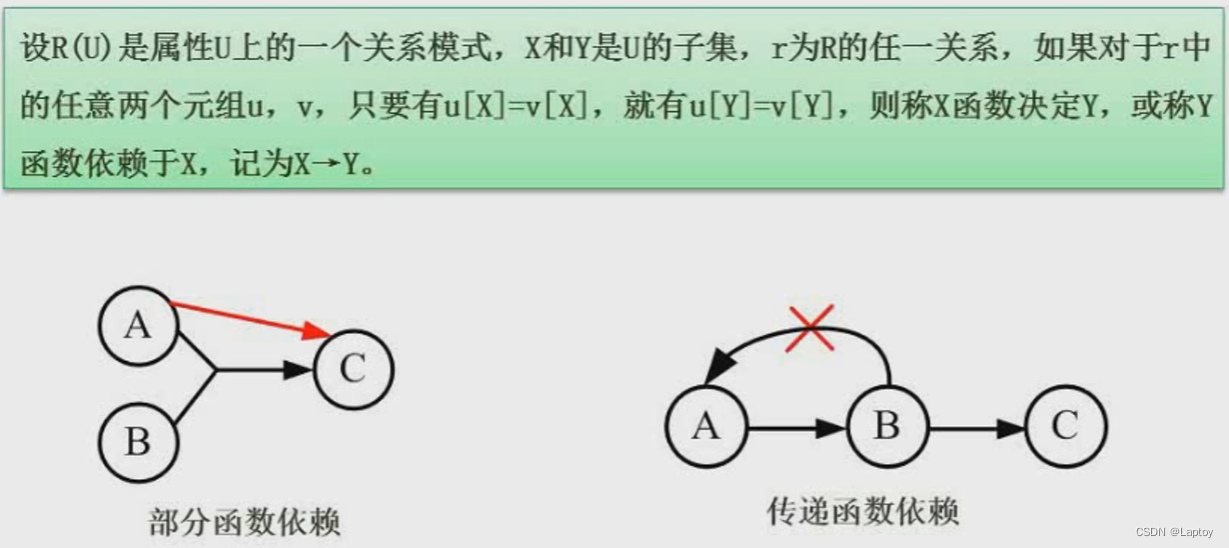
hypothesis : Student number → full name , Indicates that the student ID uniquely identifies the name of a student , In other words, the name is completely dependent on the student number .
hypothesis ( Student number , Course no. )→ Department name , And according to common sense , Obviously, according to a student's student number , You can already confirm the student's Department , There is no need for the attribute of course number , So this is a partial functional dependency .
hypothesis : Student number → Department name , Department name → The name of the dean , Here we can directly draw : Student number → The name of the dean , So this is a transfer function dependency .
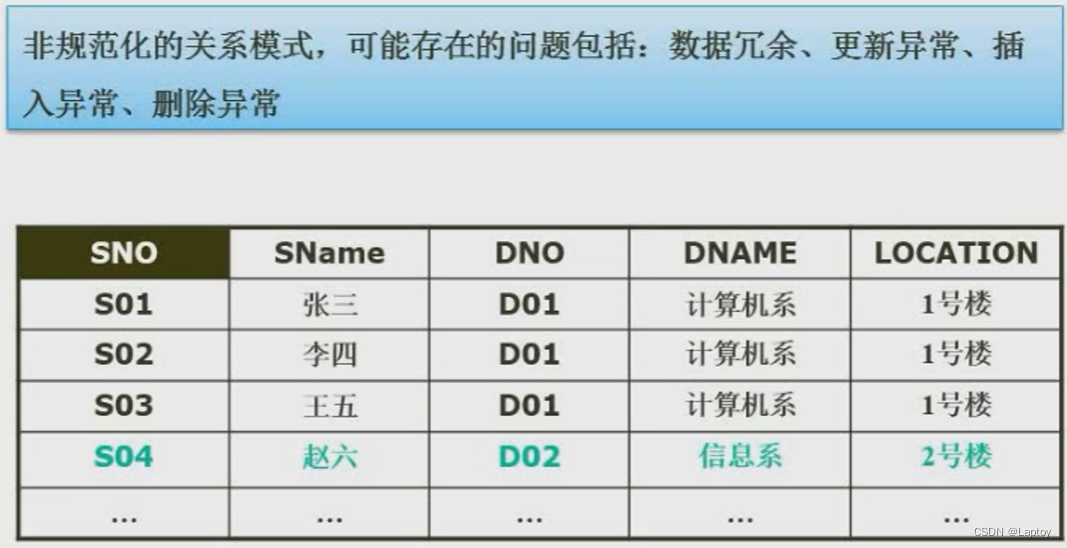
5.2、 Value and purpose
5.3、 key
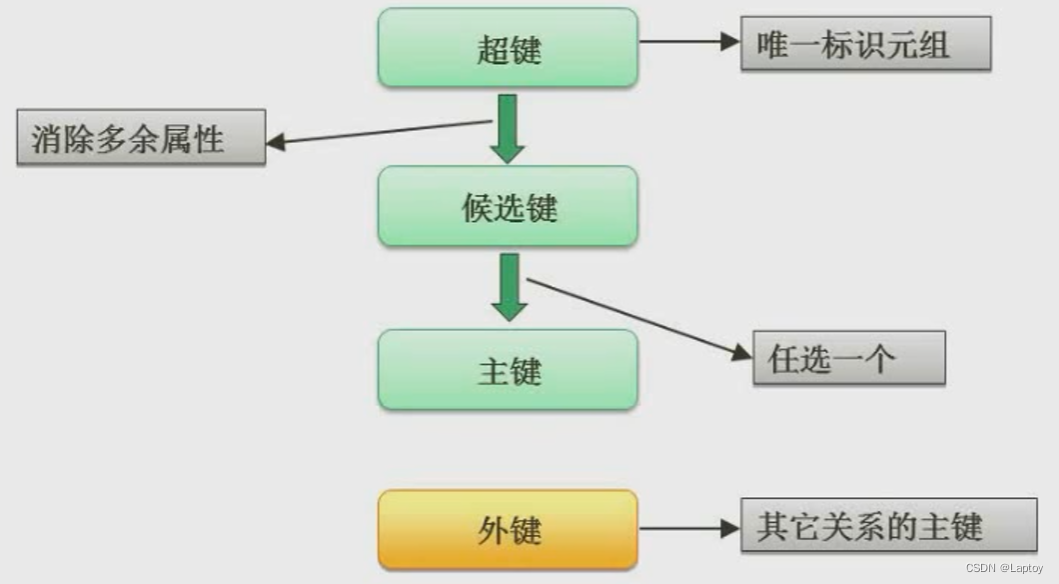
Super key : Student ID or ID number can locate students , that ( Student number + ID number + Class number ) You can also locate students , These three together are called hyperbonds
Candidate key : Remove redundant attributes from hyperkeys , Such as class number , The rest of the student ID and ID number can locate students separately , The set of these two is called candidate key
Primary key : Choose any one of the candidate keys as the primary key
Foreign keys : If the relationship pattern R The attribute or attribute group in is not the code of the relationship , But it is the code of other relationship patterns , Then the attribute or attribute group pair relationship pattern R It's outer code .
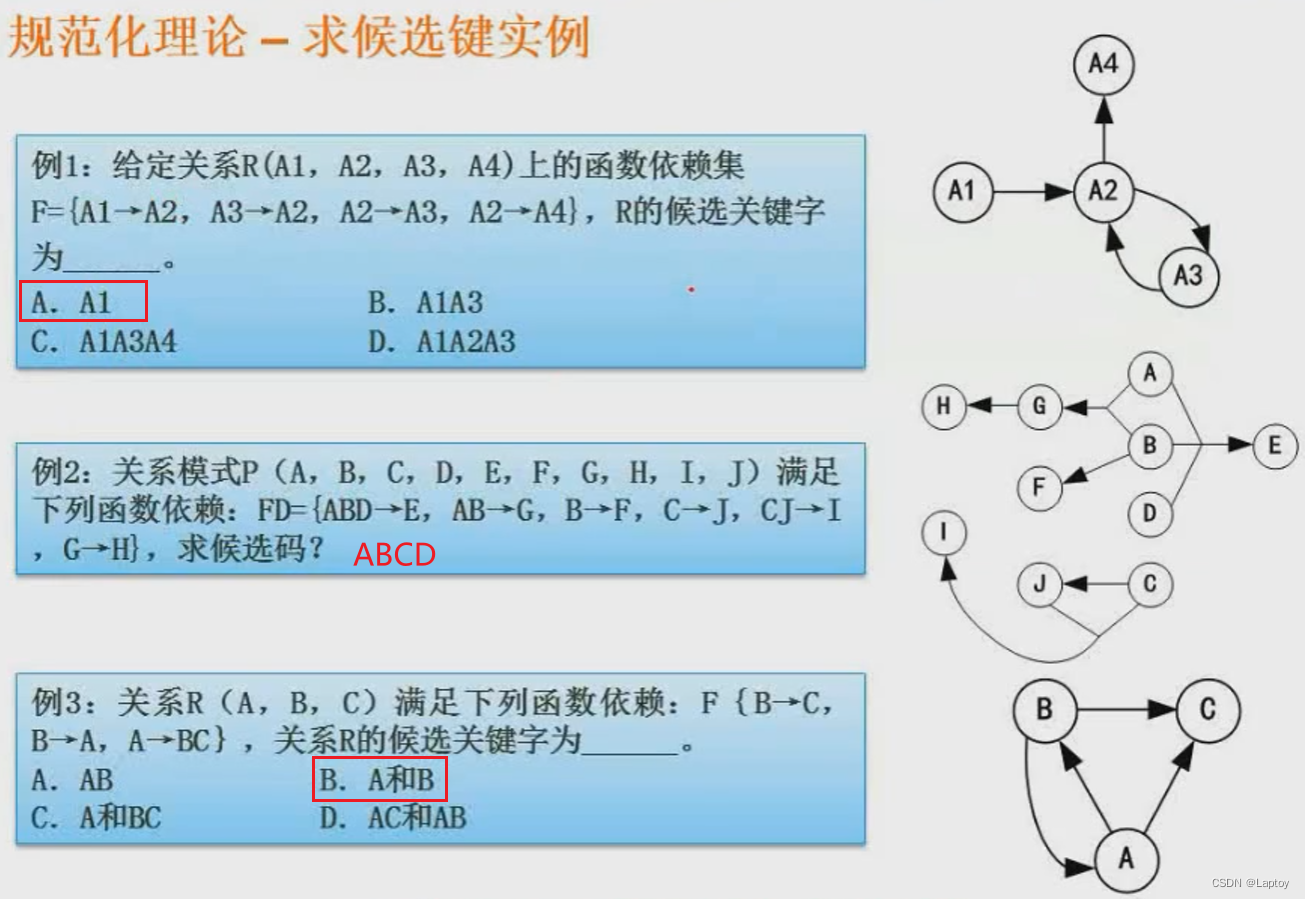
5.4、 Find candidate key

Find out the candidate keywords according to the above method
5.5、 normal form
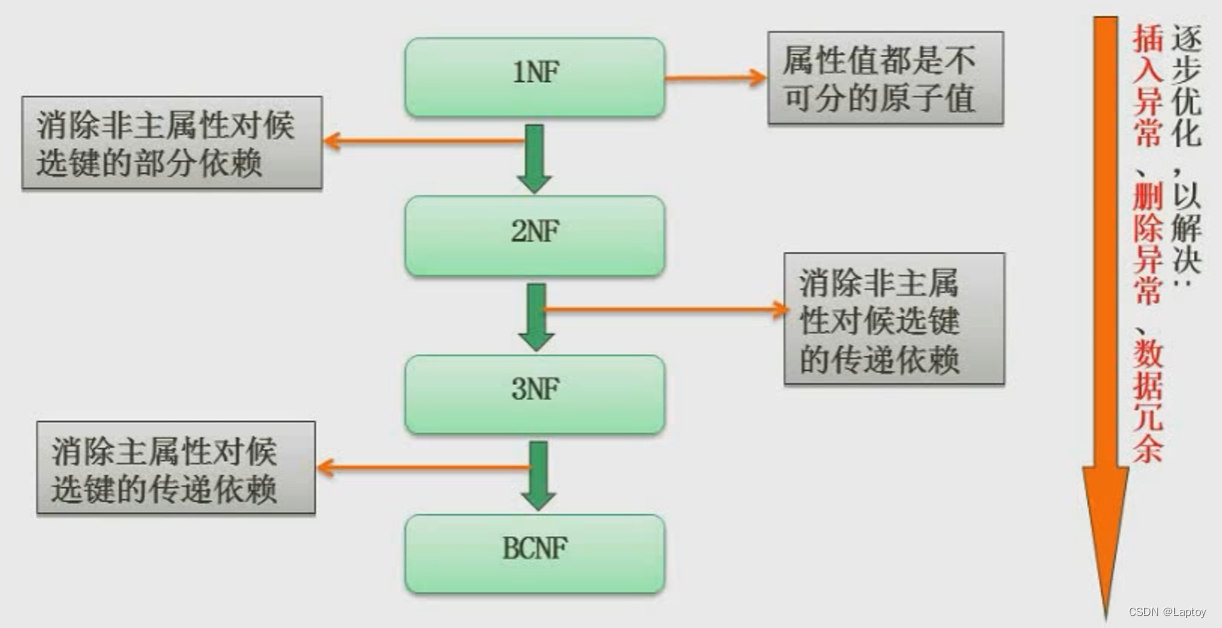
5.5.1、 First normal form
Remove non atomic values : Number of senior professional titles 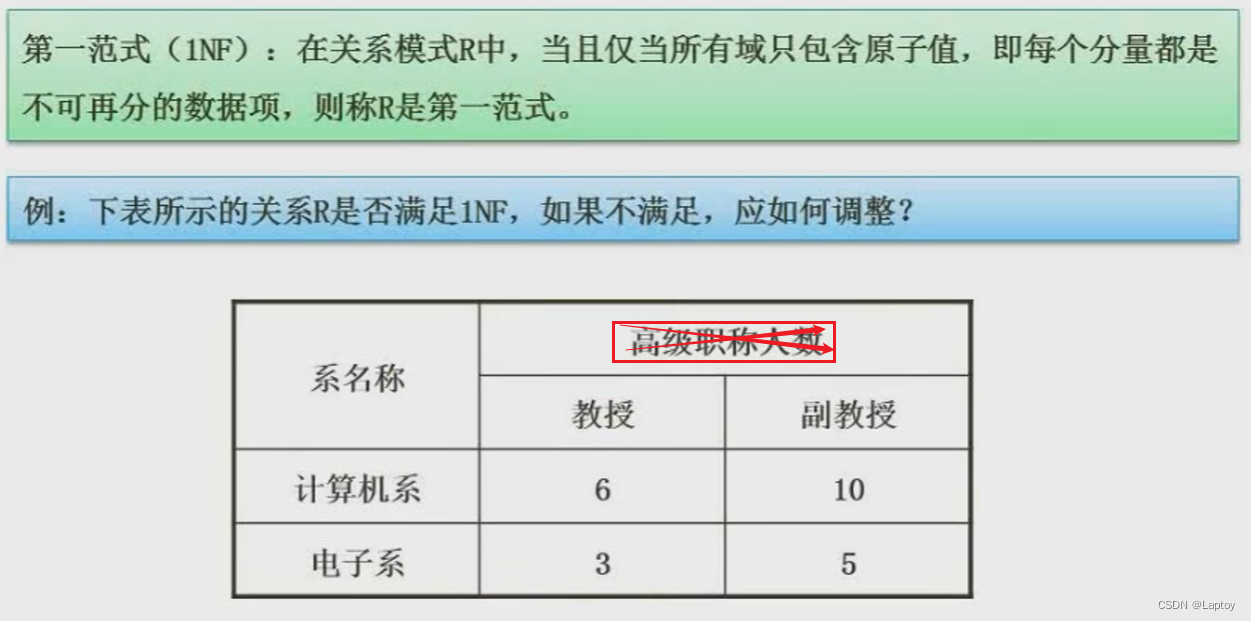
5.5.2、 Second normal form
The non primary attribute must be completely dependent on the primary attribute ( It mainly occurs in the case of joint primary keys , A non primary key column cannot depend on only a part of the primary key , The best is a single primary key )
GRADE Depend on SNO and CNO, accord with
CREDIT Only depends on CNO, Not in line with the second paradigm
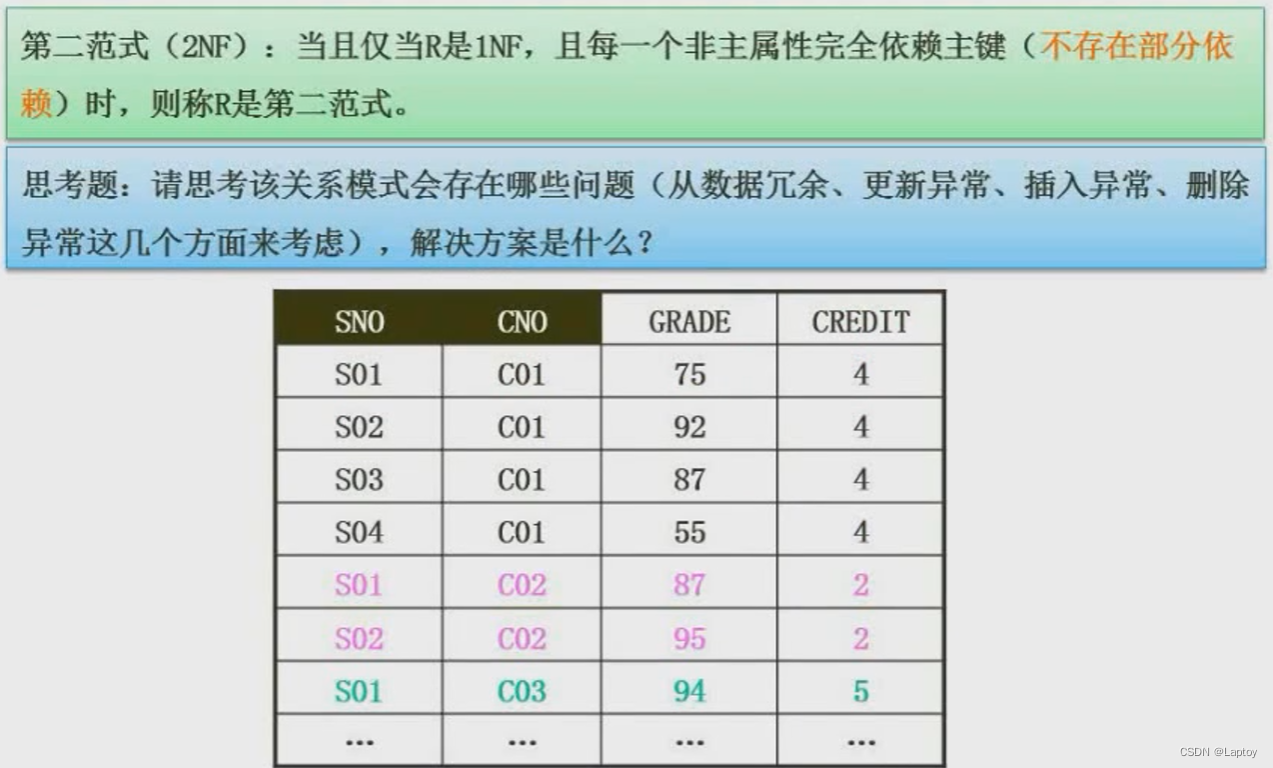
It is amended as follows
| SNO | CNO | GRADE |
|---|---|---|
| SO1 | CO1 | 75 |
| CNO | CREDEIT |
|---|---|
| CO1 | 4 |
5.5.3、 Third normal form
Non primary attributes cannot have dependencies with non primary attributes , Non primary attributes must be directly dependent on primary attributes , You can't depend on the primary property indirectly
DNAME、LOCATION Depend on DNO,DNO Depend on SNO, Transitive dependency , It doesn't conform to the third paradigm 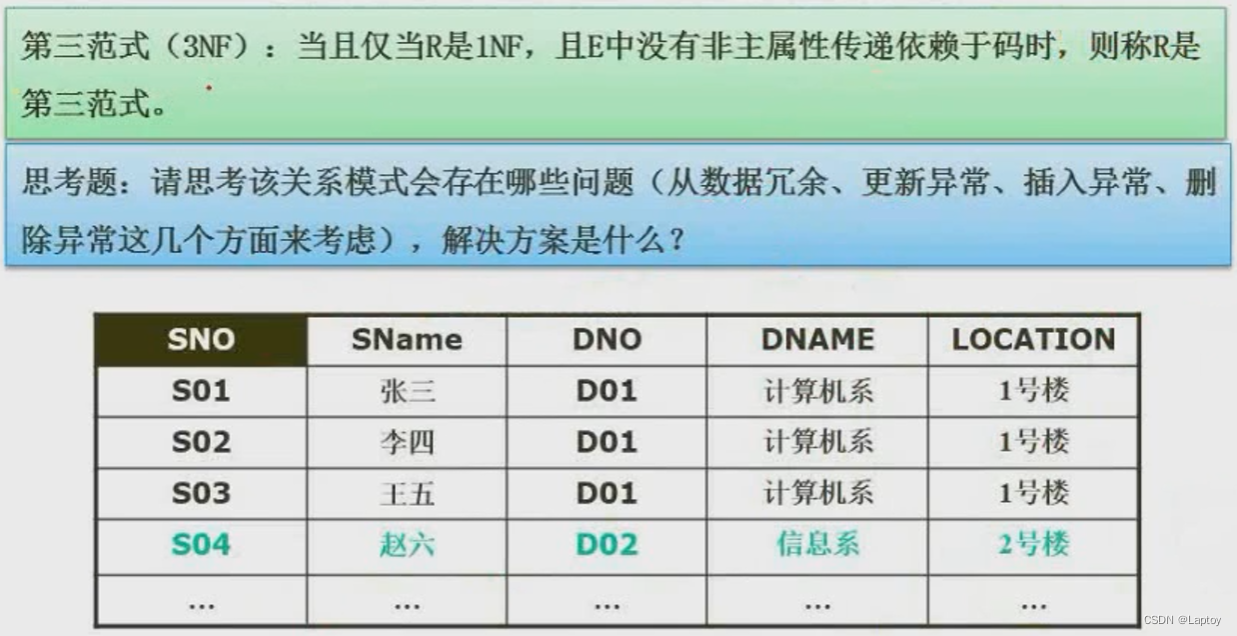
| SNO | SNAME | DNO |
|---|---|---|
| S01 | Zhang San | D01 |
| DNO | DNAME | LOCATION |
|---|---|---|
| D01 | Department of Computer Science | 1 building |
5.5.4、BC normal form
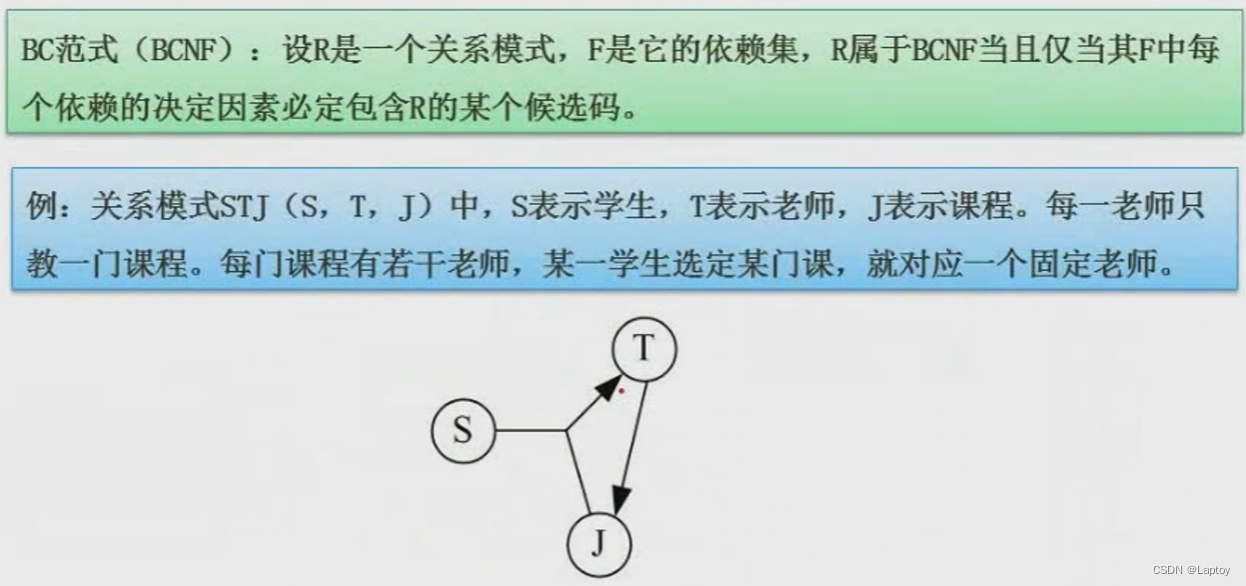
5.6、 Example
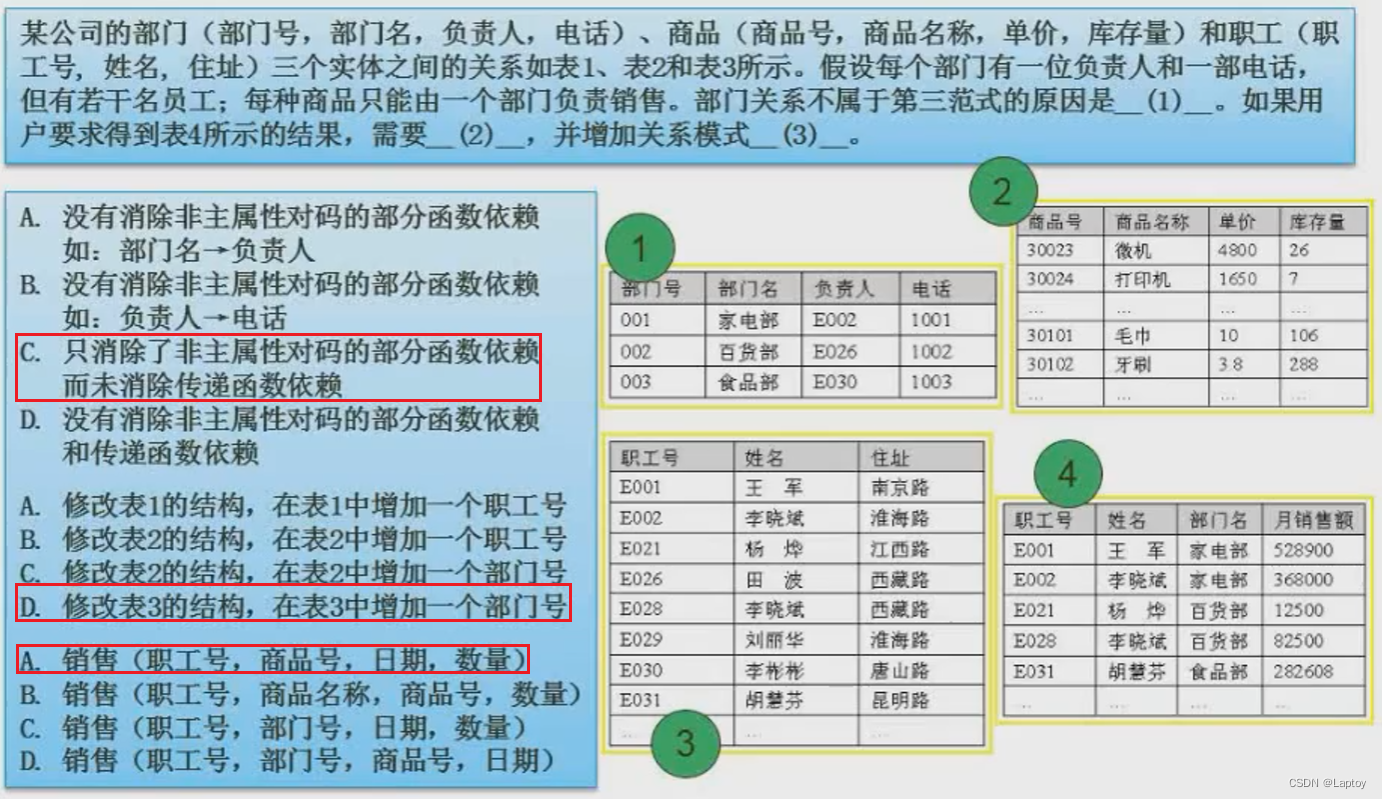
The first time : The Department table has only one primary key and does not generate partial dependencies , But the telephone transmission depends on the person in charge , Therefore, the delivery dependency is not eliminated , choose C
Second empty : Multiple employees correspond to one department , You can only add Department attributes in multiple tables , choose D
The third space : Sales relationship does not need department number and employee number together , Because in 2 Options have been established , The product name can be queried through the product number , So choose A
5.7、 Pattern decomposition
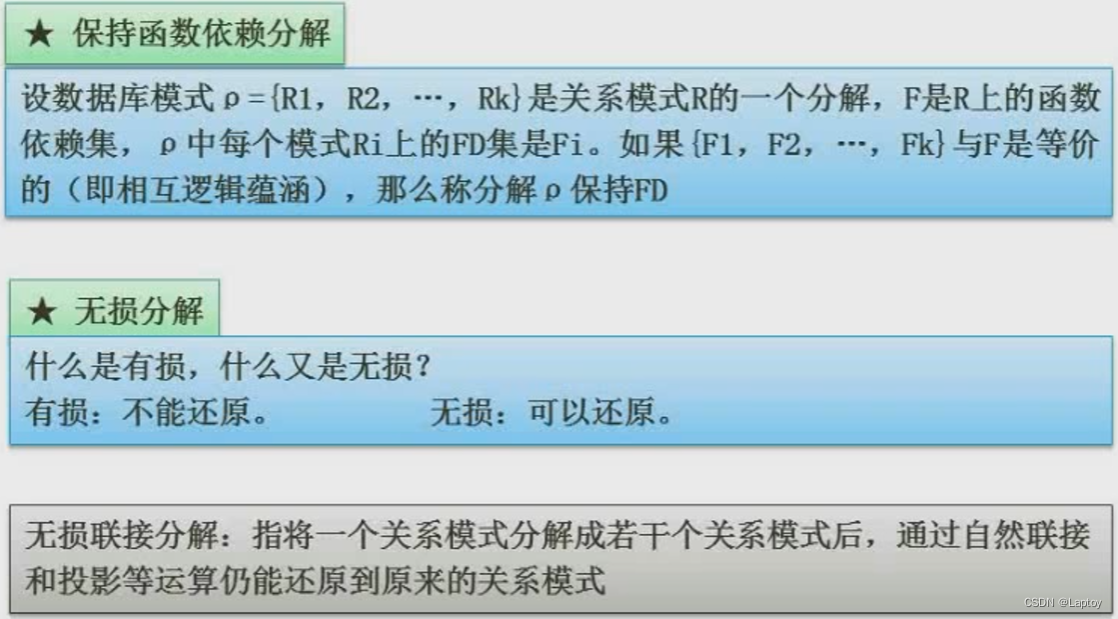
Suppose a relational model R(A,B,C), Functional dependency set F={A→B,B→C}, We will use the relationship model R Decompose into R1(A,B),R2(B,C). So in R1 in , We can find A→B; stay R2 in , We can find B→C, This corresponds exactly to the original functional dependency set , So we call this schema decomposition preserving functional dependency .( let me put it another way , For a general relational schema, it is decomposed into several sub relational schemas , If we can deduce the same content as the original functional dependency set according to the attributes in these sub relationship patterns , Maintain functional dependency )
For schema decomposition , If the number of decomposed sub relationship patterns is greater than 2, You need to use the table method to restore ( The tabular method will not be explained in detail here ); If there are only two decomposed sub relationship patterns :R1 and R2, Then just ask R1∩R2( intersection )、R1-R2( Difference operation )、R2-R1( Difference operation ), If at this time R1∩R2 Be able to launch R1-R2 or R2-R1 One of them , It is said that schema decomposition is lossless .
Example 1
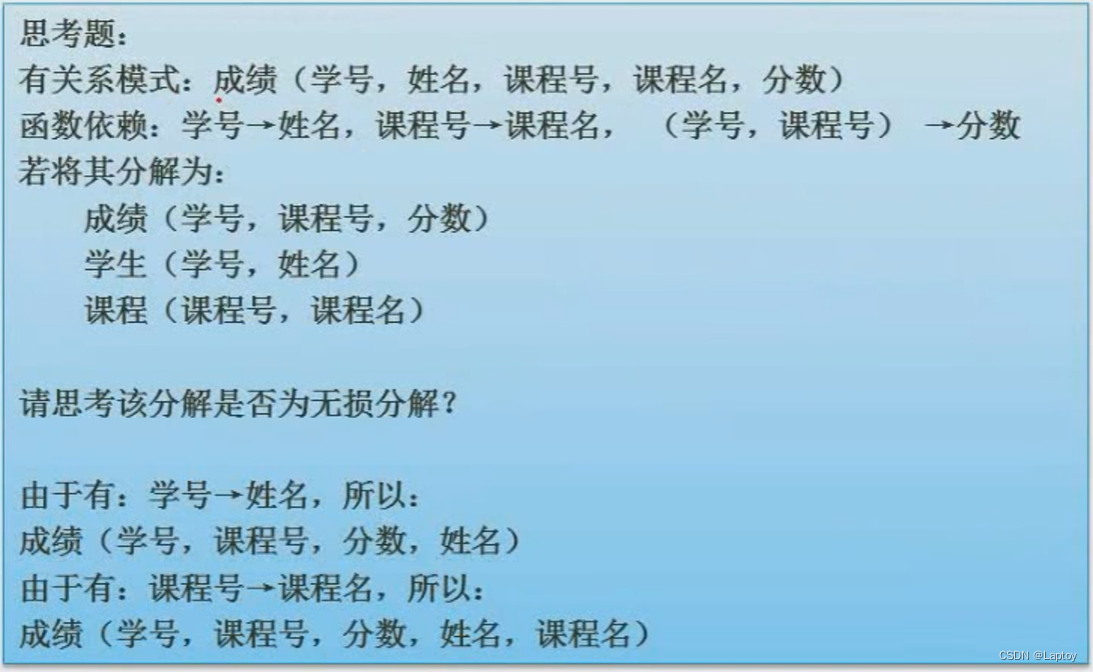
Example 2
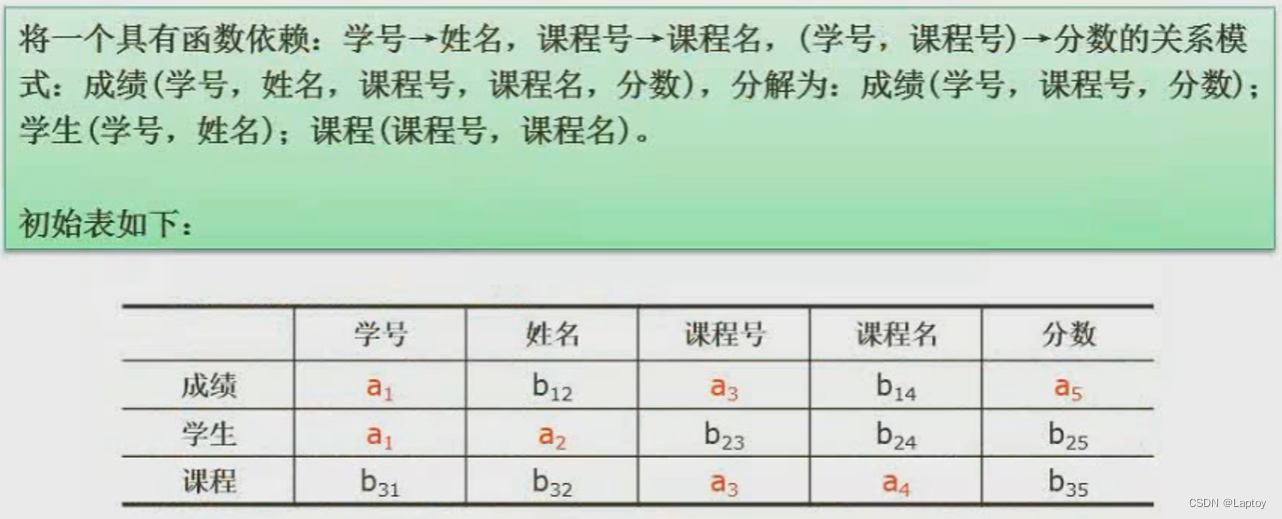
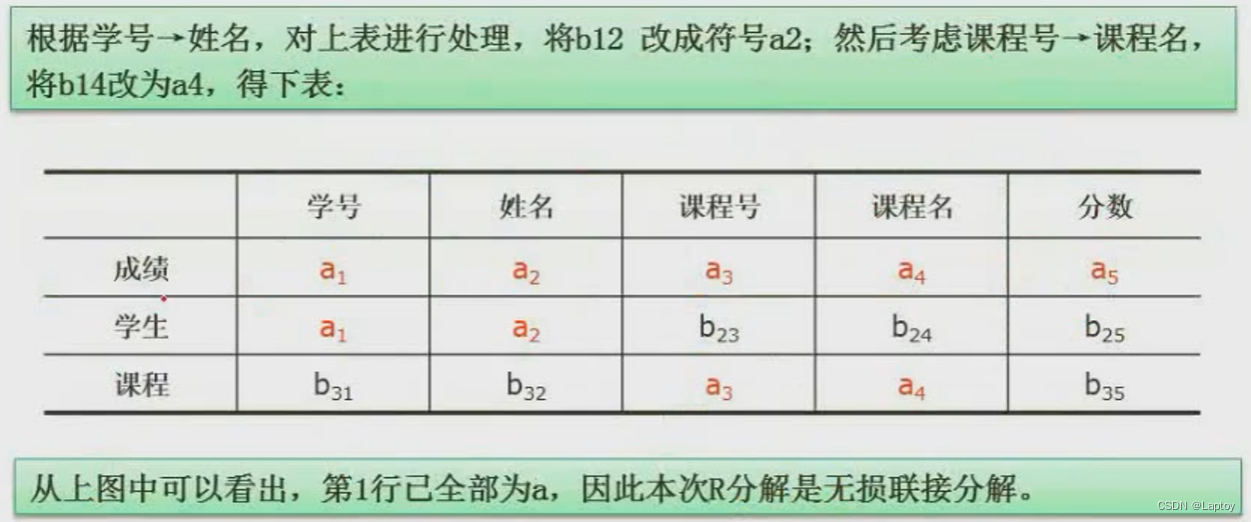
Example 3
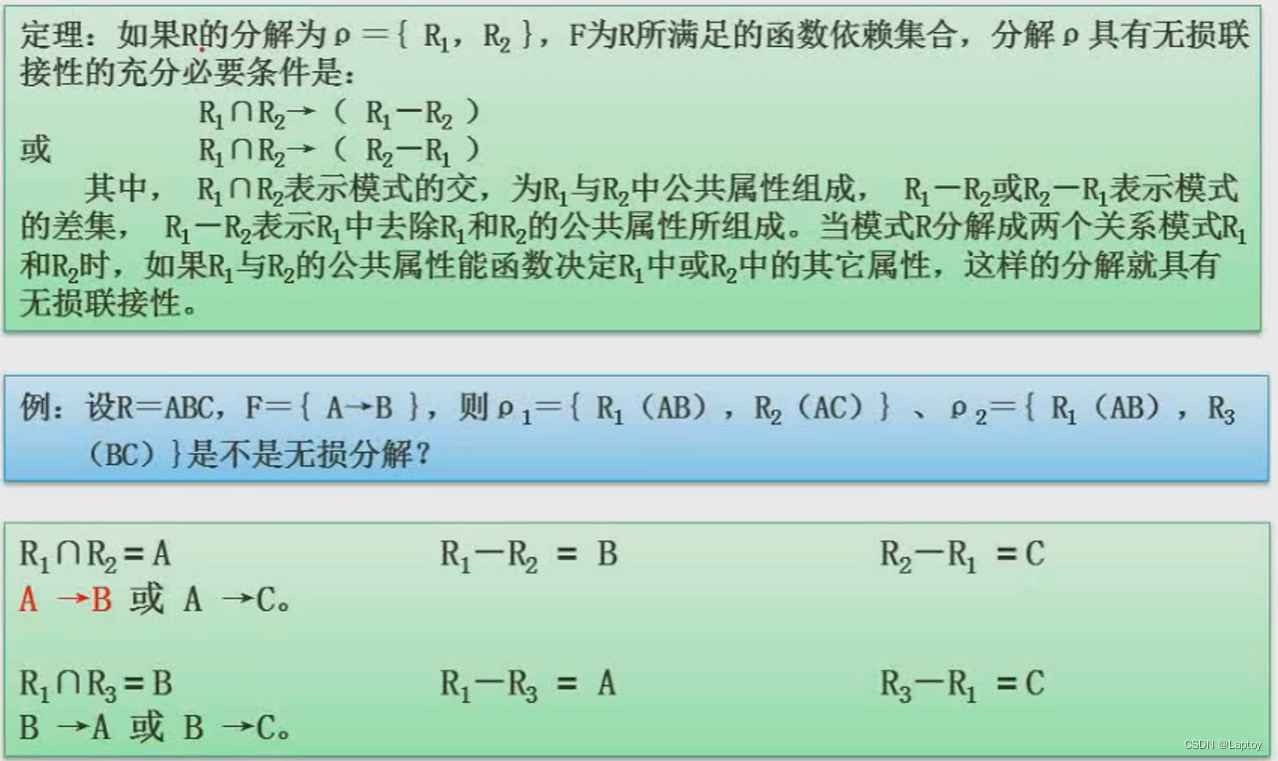
6、 ... and 、 concurrency control
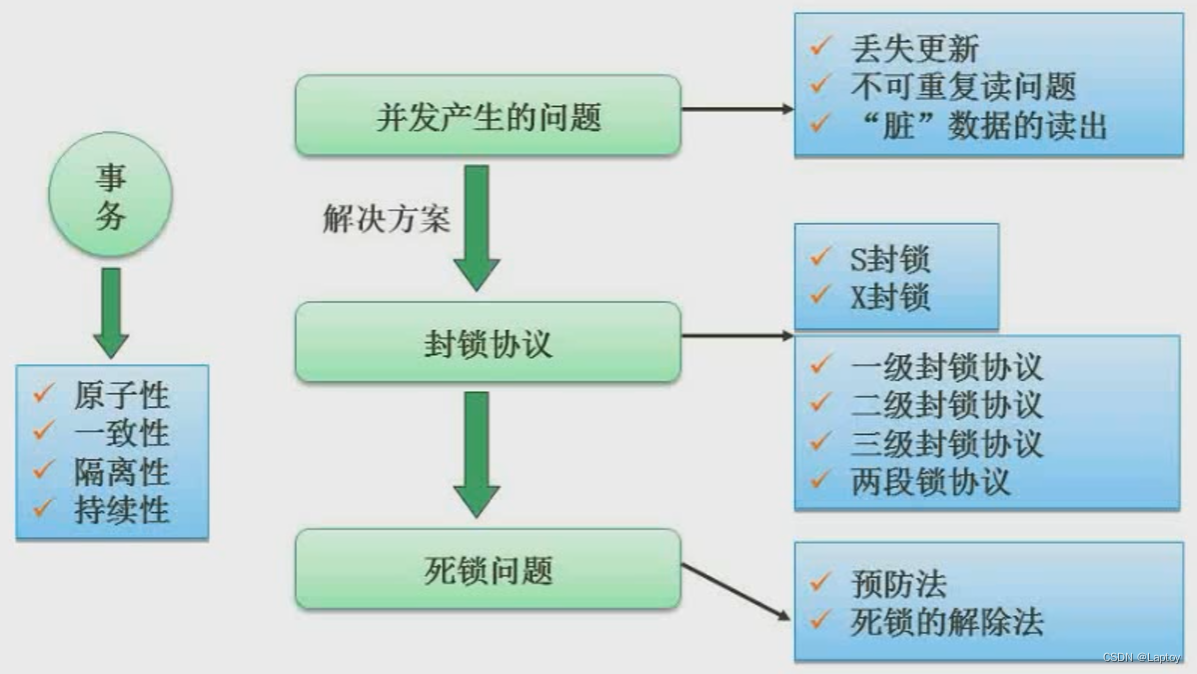
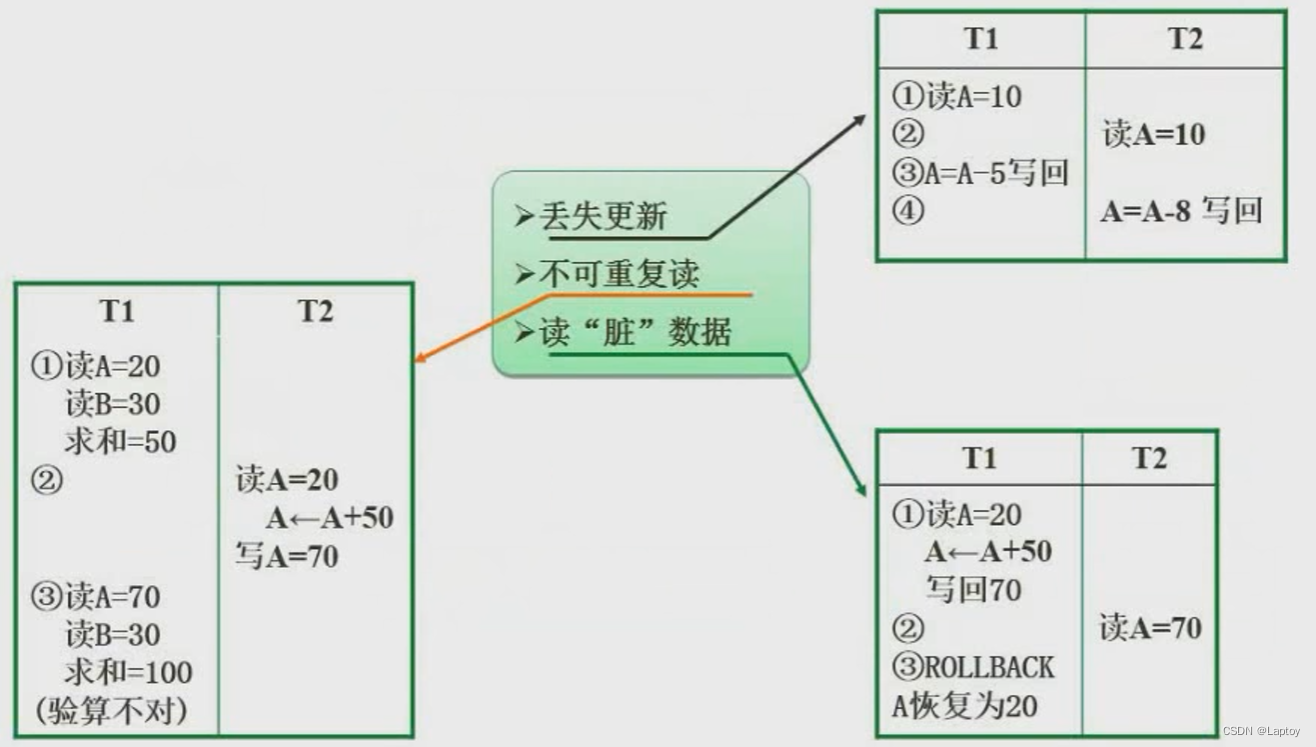
6.1、 Problems caused by concurrency control
6.2、 Blocking agreement

Exclusive lock : Also known as X Lock or write lock . If business T For data objects A add X lock , Only T Read and modify A, Nothing else can be done to A Add any type of lock , until T Release A The lock on the .
Shared lock : Also known as S Lock or read lock . If business T For data objects A add S lock , Only T Read A, But it can't be modified A, Other affairs can only be right again A Add S lock , until T Release A Upper S lock . This ensures that other transactions can read A, But in T Release A Upper S You can't do it before you lock it A Make any changes .
7、 ... and 、 Integrity constraints
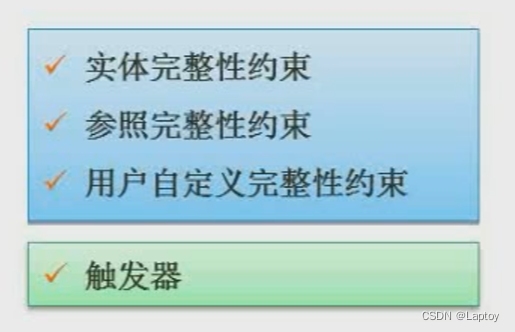
Entity integrity : If attribute ( Attribute group )A It's the basic relationship R The main attribute of , be A Can't take null value .( let me put it another way , The primary key cannot be empty )
Referential integrity : If attribute ( Attribute group )F It's the basic relationship R The foreign key , It and basic relationship S The main code of Ks Corresponding , For R Each tuple in F The value on must be : be equal to S The main code value of a tuple in , Or take a null value .( let me put it another way , The foreign key is either empty , Or equal to the primary key of another relationship )
User-defined integrity : Integrity rules set by the user according to the actual situation . for example : Age cannot be negative 、 Gender can only be men and women .
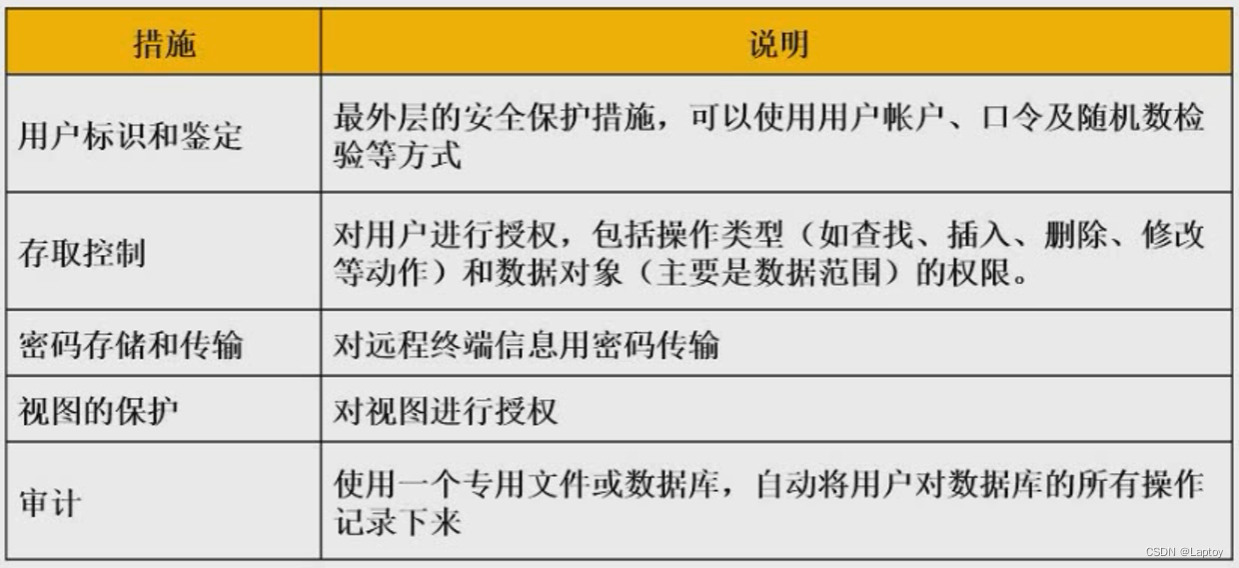
8、 ... and 、 database security
Nine 、 Database backup
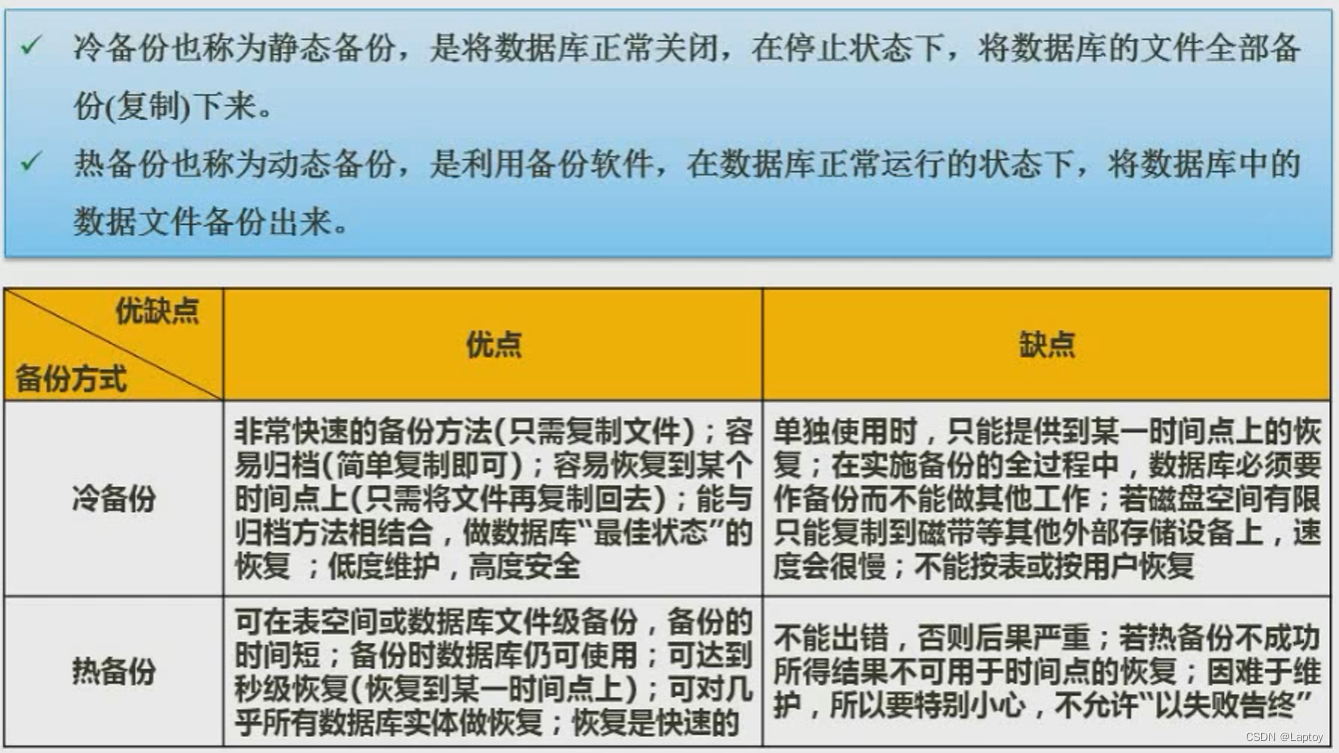
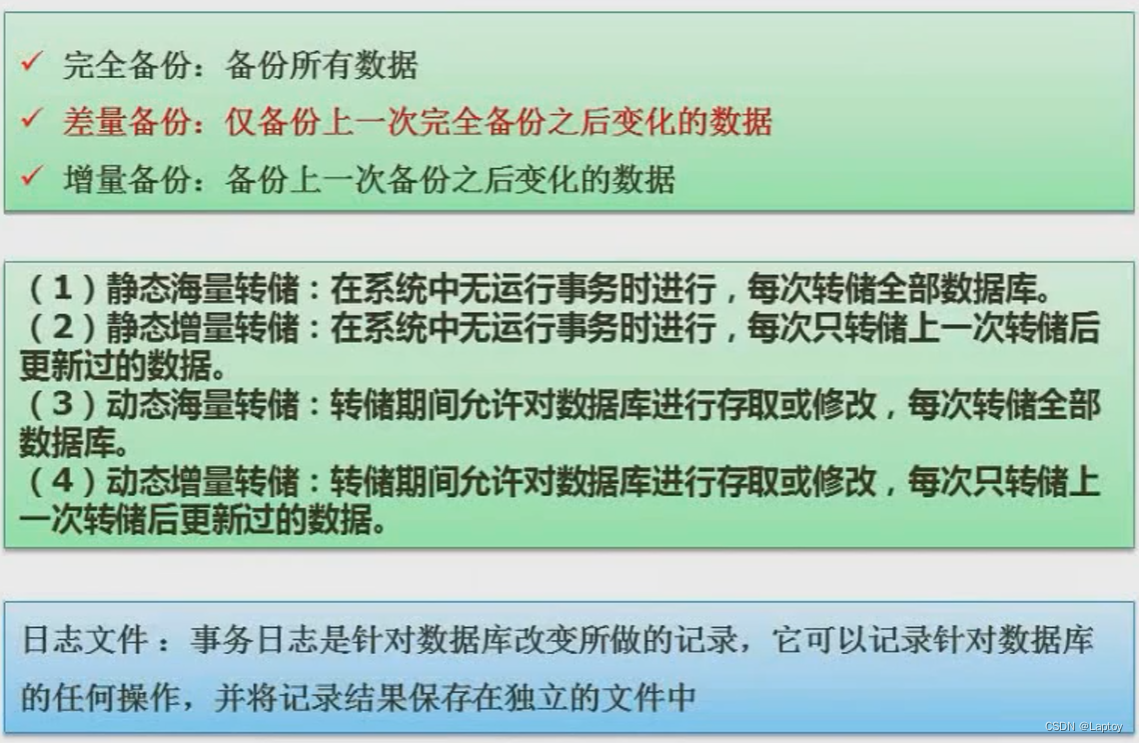
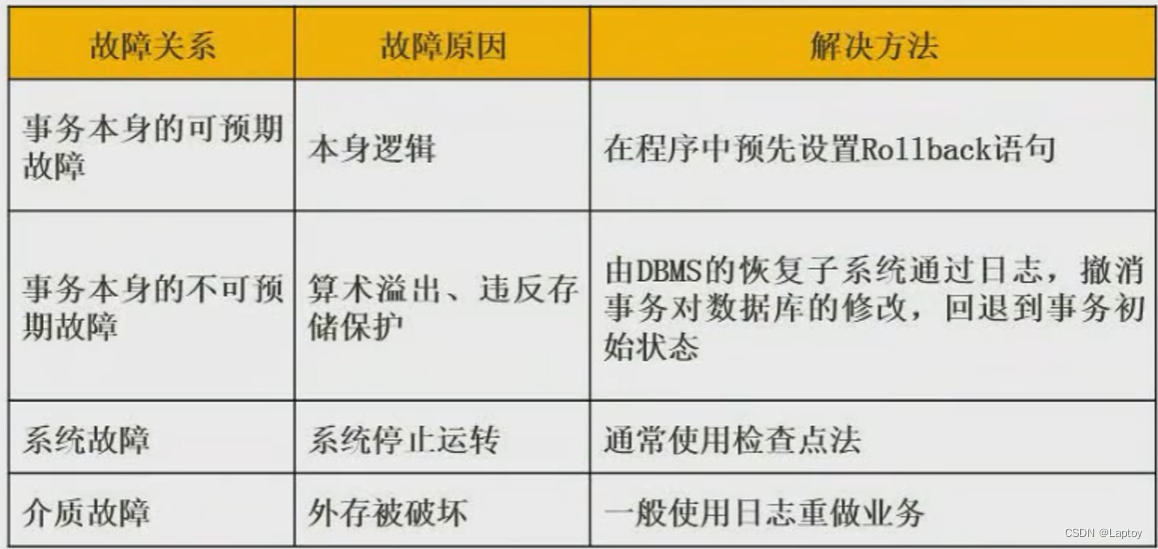
Nine 、 Data warehouse and data mining
9.1、 Data warehouse
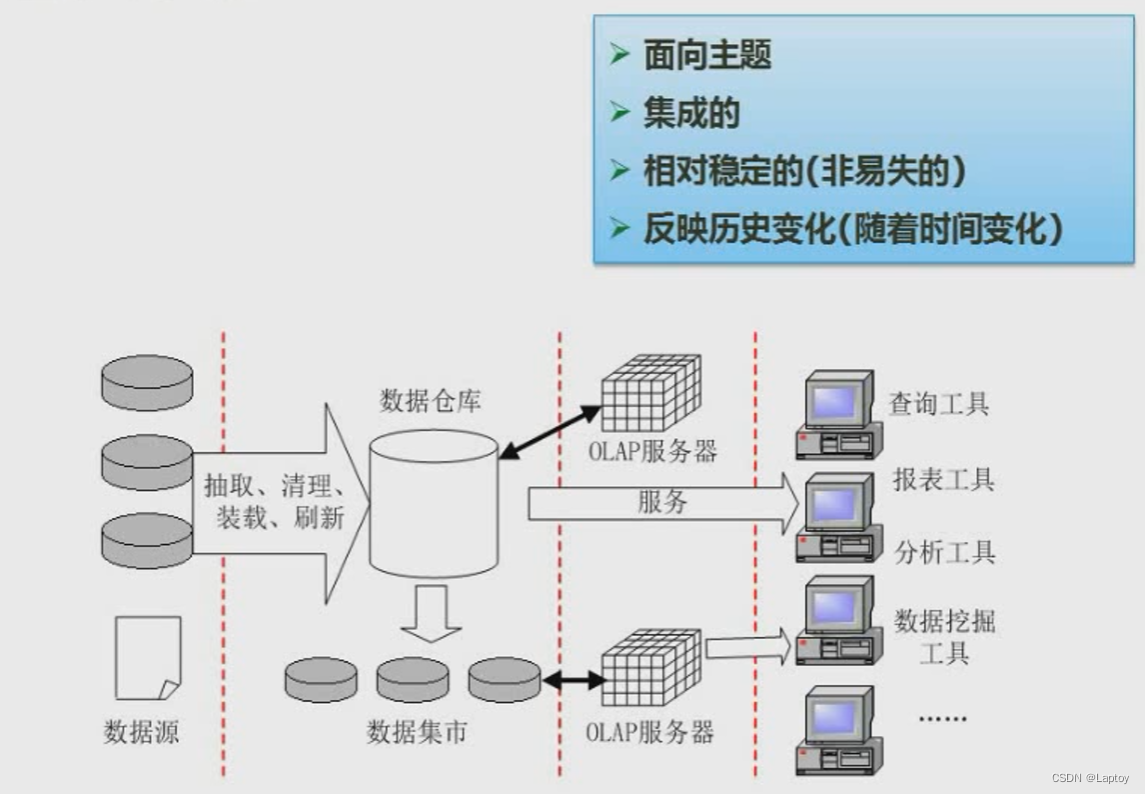
9.2、 Data mining method

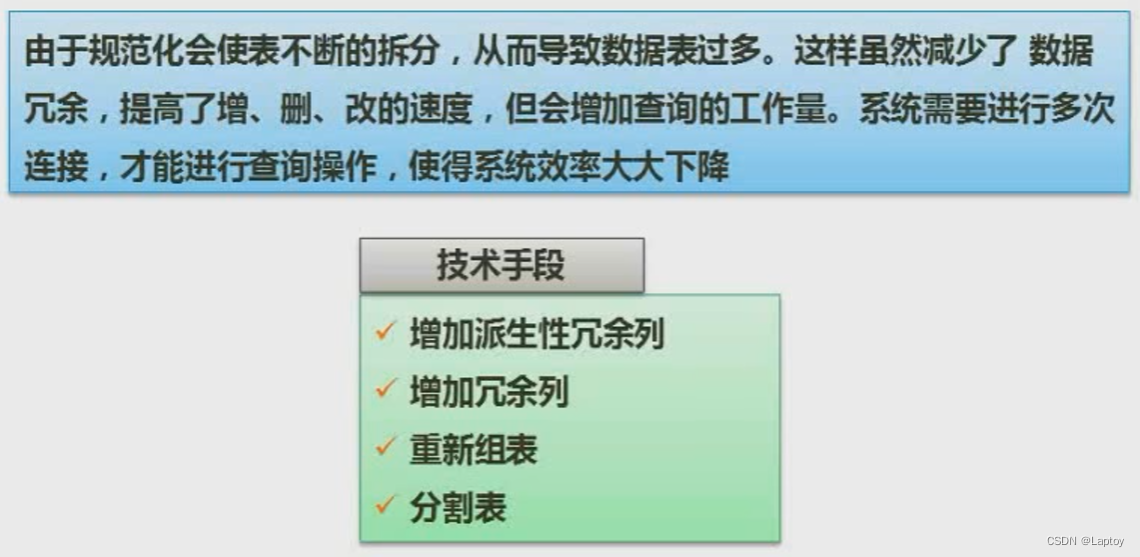
Ten 、 Anti normalization
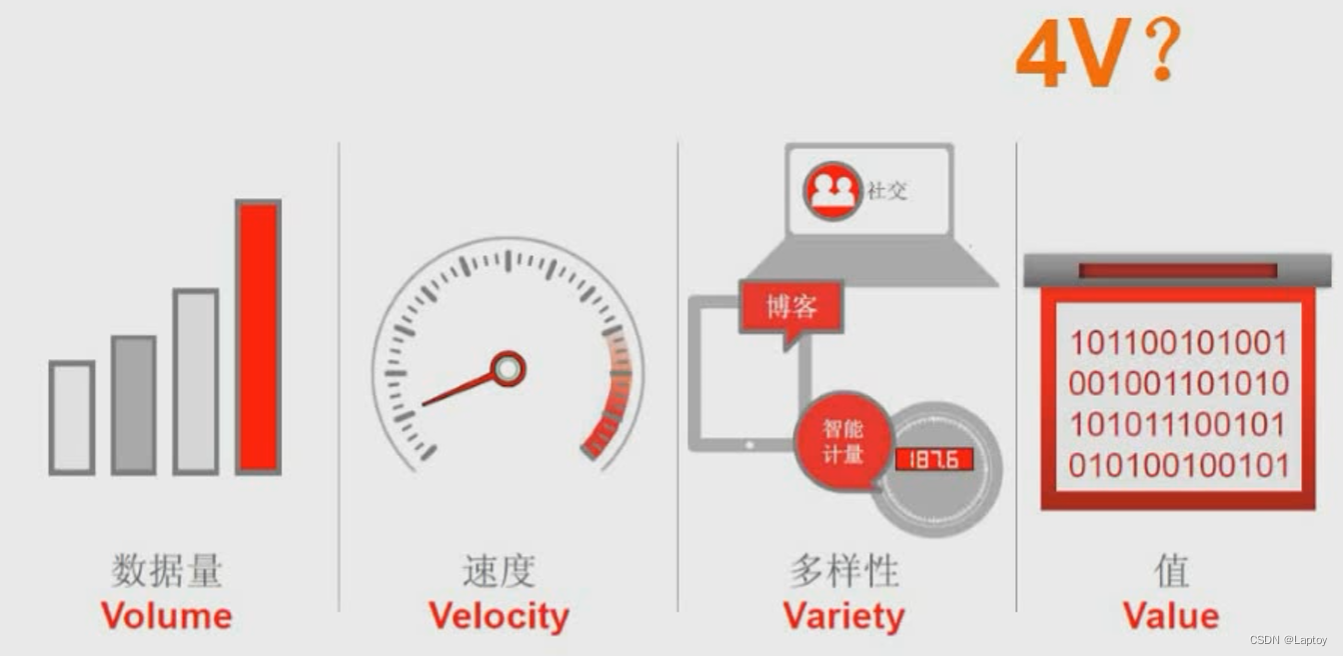
11、 ... and 、 Basic concept of big data

边栏推荐
- P3D gauge size problem
- NSIS finds out whether the file exists and sets the installation path
- Build your own random wallpaper API for free
- Idea to view the source code of jar package and some shortcut keys (necessary for reading the source code)
- Altium Designer 19.1.18 - 清除测量距离产生的信息
- "Source code interpretation" famous programmer TJ's only library
- Apple terminal skills
- Professional knowledge of public security -- teacher bilitong
- Global and Chinese markets of nano biosensors 2022-2028: Research Report on technology, participants, trends, market size and share
- STM32 knowledge points
猜你喜欢
Explanation of parallel search set theory and code implementation
CADD course learning (5) -- Construction of chemosynthesis structure with known target (ChemDraw)

About the problem that MySQL connector net cannot be cleared in MySQL
Scm-05 basis of independent keyboard

CADD课程学习(5)-- 构建靶点已知的化合结构(ChemDraw)
Basic series of SHEL script (III) for while loop
Opendrive arc drawing script
With the help of Navicat for MySQL software, the data of a database table in different or the same database link is copied to another database table
mysql 盲注常见函数
Deepin get file (folder) list
随机推荐
Graduation thesis project local deployment practice
Rename directory in C [closed] - renaming a directory in C [closed]
Apple script
GPIO circuit principle of stm32
CADD course learning (5) -- Construction of chemosynthesis structure with known target (ChemDraw)
.NET服务治理之限流中间件-FireflySoft.RateLimit
Global and Chinese market of plastic recycling machines 2022-2028: Research Report on technology, participants, trends, market size and share
"Source code interpretation" famous programmer TJ's only library
MySQL - storage engine
Unforgettable summary of 2021
editplus
Query the table name used by kettle in Oracle
Detour of Tkinter picture scaling
Embedded AI intelligent technology liquid particle counter
repo. conda. An example of COM path error
Good websites need to be read carefully
The sublime version that XP can run is 3114
SQL JOINS
PIL's image tool image reduction and splicing.
The number of occurrences of numbers in the offer 56 array (XOR)