当前位置:网站首页>HCIA review
HCIA review
2022-07-06 05:54:00 【I'm Puxin man】
Catalog
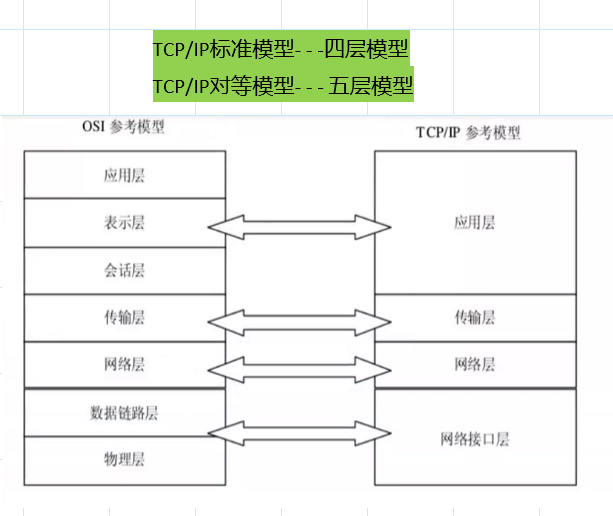
OSI/RM

application layer >> Provide various application services , Convert abstract language to coding , Provide human-computer interaction interface
The presentation layer >> Convert the encoding to binary Unified format
The session layer >> Maintain the session between the network application and the network server
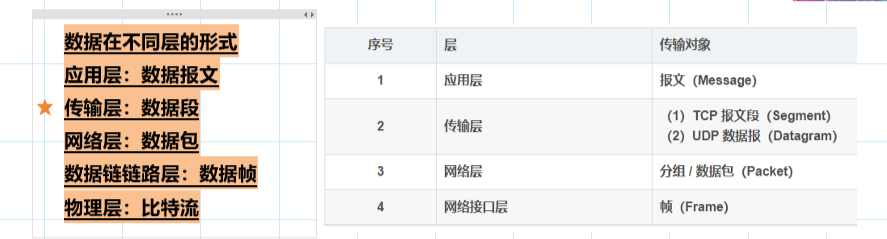
Transport layer >> End to end communication ( Apply to application ) sport dport
The network layer >> Use IP Address realizes logical addressing between hosts --- SIP DIP
Data link layer >> Control physical hardware Convert binary into electrical signal
The physical layer >> Handle the transmission of electrical signals
The length of the port number is 16 Binary bits
0-65535
among 0 It is not used as a port of the transport layer
The port number range is 1-65535
1-1023 For well-known port number
- DNS Domain name resolution service (53)
- DHCP(UDP67,68)
obtain DIP Address method
1. Know the server's IP Address
2. Access the server through the domain name
3. Access the server through the application
4. radio broadcast
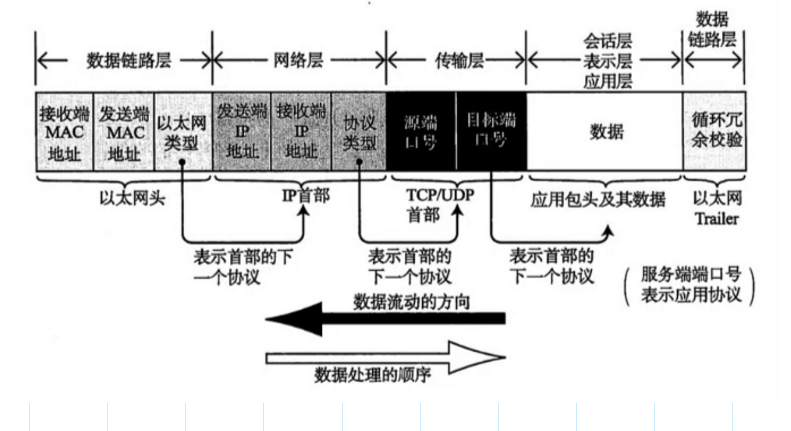
MAC Address by 48 Bit binary structure
Global uniqueness , use the same pattern --SMAC DMAC
Data link layer adopt MAC Address for physical addressing
obtain DMAC Methods - -ARP agreement -- - - Address resolution protocol
1. positive ARP- - - adopt IP The address for MAC Address
The host by Broadcast transmission ARP, Based on the known IP Address , request MAC Address . All devices in the broadcast domain can receive request packets , All devices that receive packets will record the source in the packet IP Address and source MAC The correspondence of the address is local ARP The cache table . after , Look at the request IP Address , If it's local IP Address , Will be performed ARP The reply , Local MAC Address inform . If it's not local IP Address , The packet will be discarded directly . after , When sending data again , Give priority to local ARP Cache table , If there are records in the table , Then the information will be sent directly according to the record . If there is no record , Then send ARP Request package acquisition MAC Address
2. reverse ARP- - - adopt MAC The address for IP Address
3. free ARP
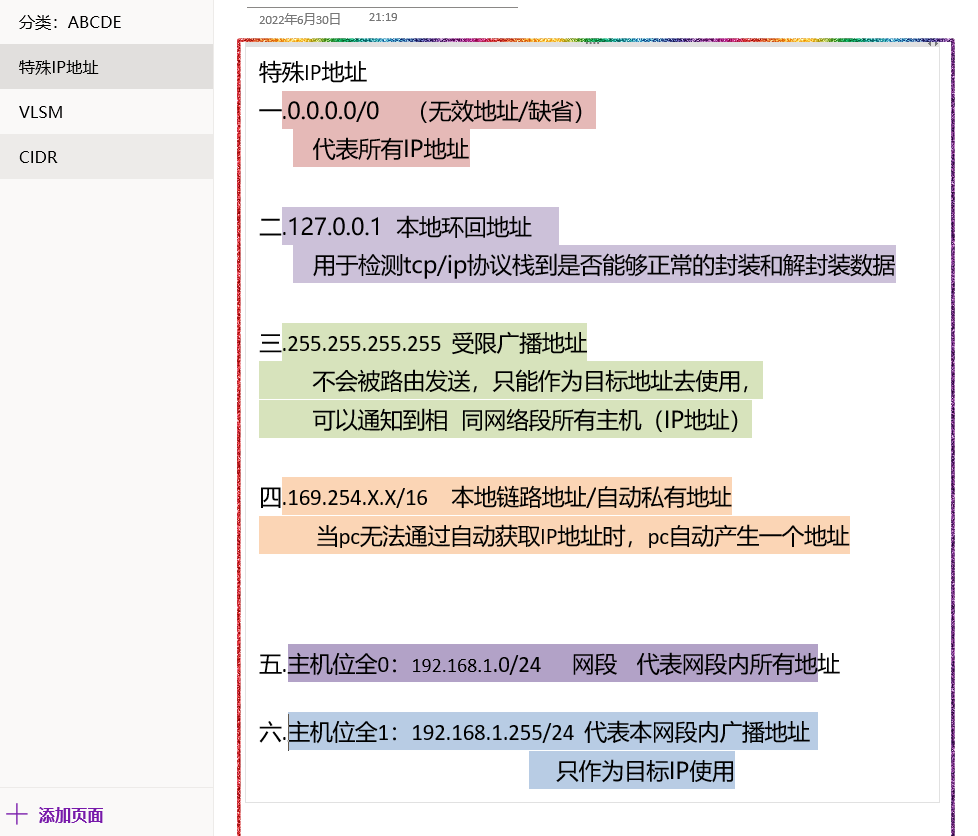
IP Address
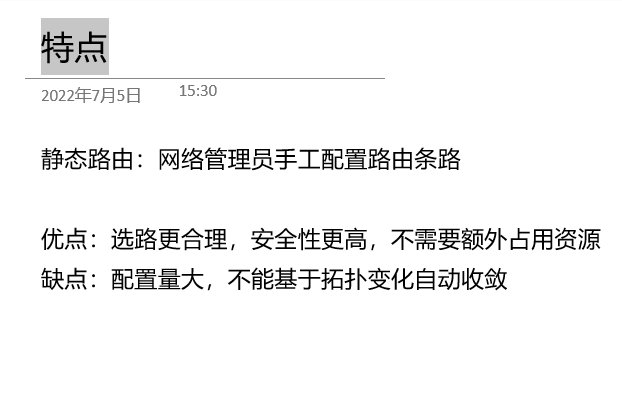
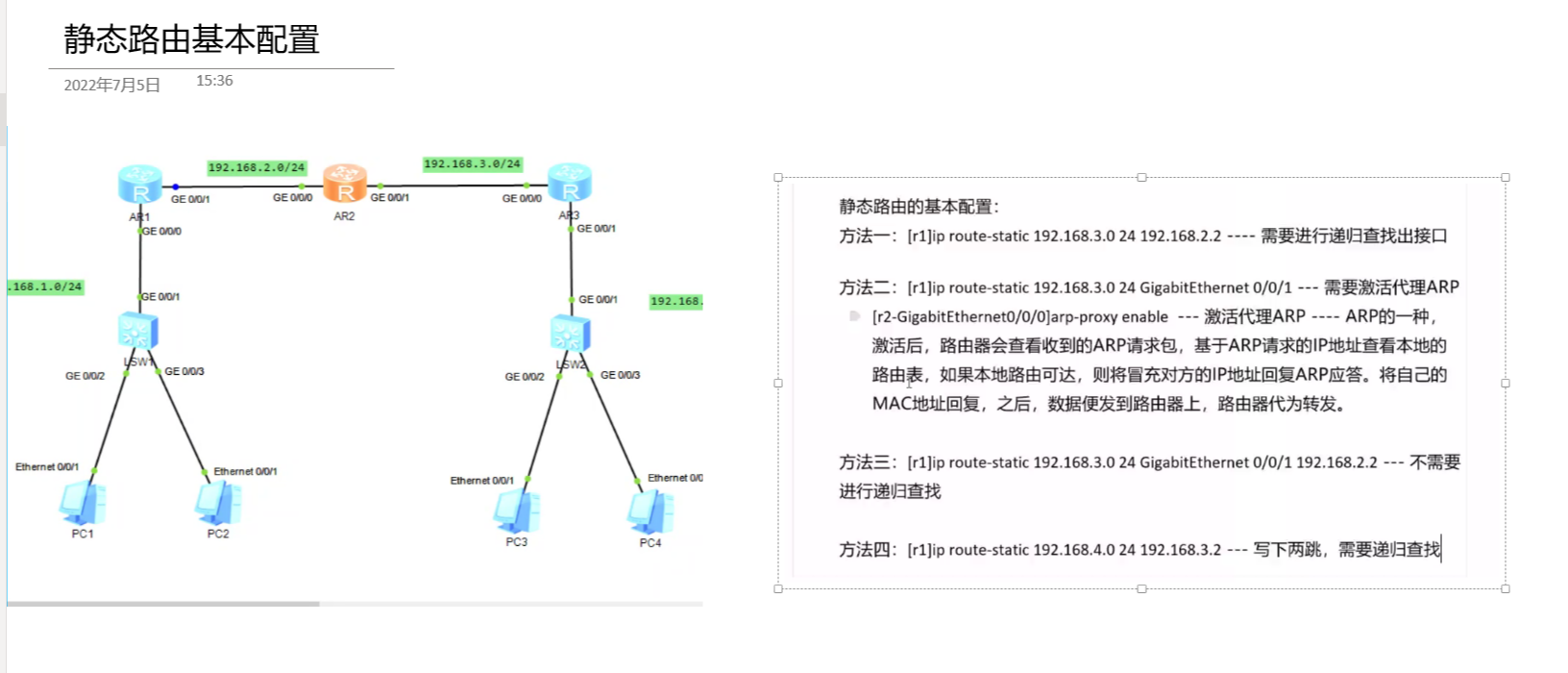
Static routing

边栏推荐
猜你喜欢

数字经济破浪而来 ,LTD是权益独立的Web3.0网站?
LTE CSFB process
H3C V7 switch configuration IRF
ArcGIS应用基础4 专题图的制作

授予渔,从0开始搭建一个自己想要的网页

The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
![[Jiudu OJ 08] simple search x](/img/a7/12a00c5d1db2deb064ff5f2e83dc58.jpg)
[Jiudu OJ 08] simple search x
How to download GB files from Google cloud hard disk
![[force buckle]43 String multiplication](/img/fd/de63e6185af4b6293e748aaf7cee29.jpg)
[force buckle]43 String multiplication
High quality coding tool clion
随机推荐
Huawei BFD configuration specification
Closure, decorator
The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
Query the standard text code corresponding to a work center (s) in the production order
The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
Zoom through the mouse wheel
Embedded interview questions (IV. common algorithms)
移植InfoNES到STM32
华为路由器如何配置静态路由
Analysis of grammar elements in turtle Library
C language learning notes (mind map)
类和对象(一)this指针详解
[experience] install Visio on win11
Some easy-to-use tools make your essay style more elegant
c语言——冒泡排序
PDK工艺库安装-CSMC
Download, install and use NVM of node, and related use of node and NRM
ArcGIS application foundation 4 thematic map making
[Jiudu OJ 08] simple search x
Redis message queue