当前位置:网站首页>PHP面试题 foreach($arr as &$value)与foreach($arr as $value)的用法
PHP面试题 foreach($arr as &$value)与foreach($arr as $value)的用法
2022-07-07 16:14:00 【南宋x】
边栏推荐
- Face recognition attendance system based on Baidu flying plasma platform (easydl)
- Summary of debian10 system problems
- socket編程之常用api介紹與socket、select、poll、epoll高並發服務器模型代碼實現
- Chapter 3 business function development (user login)
- 深度学习-制作自己的数据集
- 通过 Play Integrity API 的 nonce 字段提高应用安全性
- nest.js入门之 database
- Interviewer: why is the page too laggy and how to solve it? [test interview question sharing]
- Easy to understand [linear regression of machine learning]
- Taffydb open source JS database
猜你喜欢

三仙归洞js小游戏源码
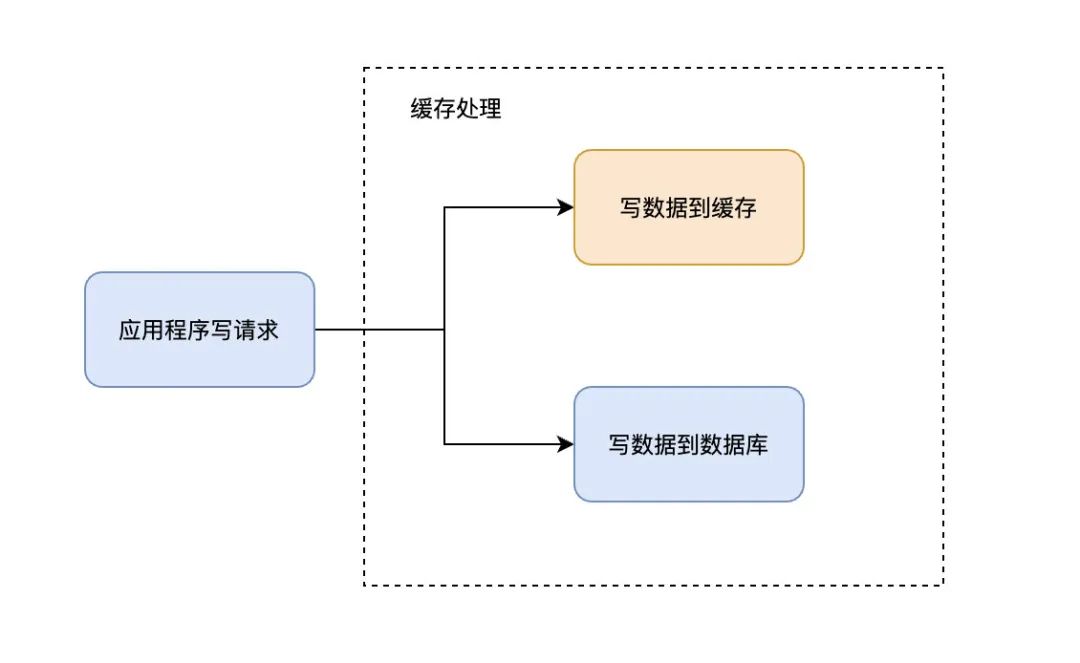
4种常见的缓存模式,你都知道吗?

Mrs offline data analysis: process OBS data through Flink job
swiper左右切换滑块插件
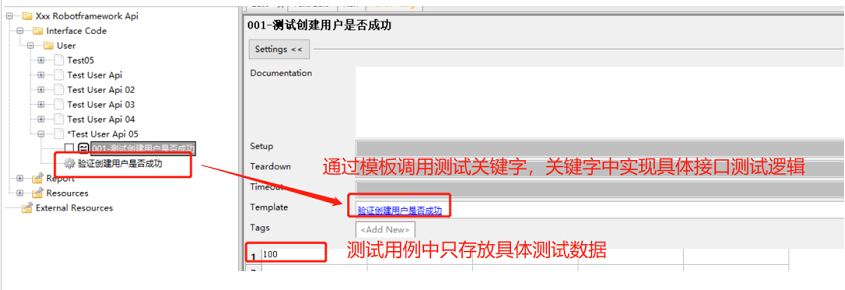
Automated testing: a practical skill that everyone wants to know about robot framework

Target detection 1 -- actual operation of Yolo data annotation and script for converting XML to TXT file
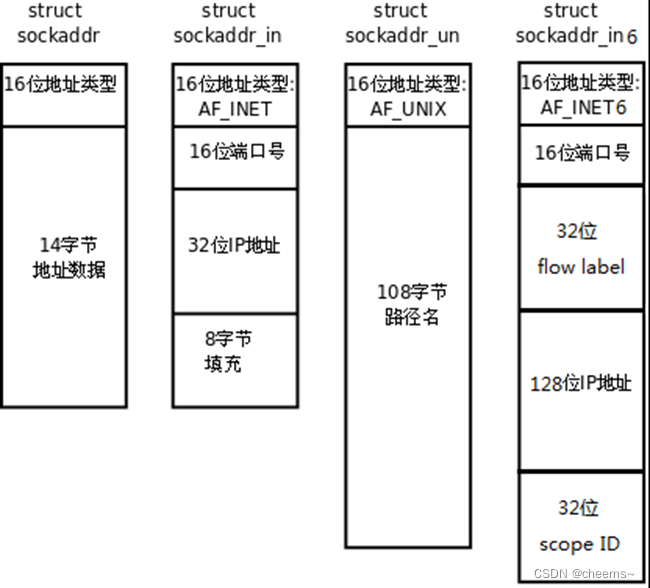
Introduction of common API for socket programming and code implementation of socket, select, poll, epoll high concurrency server model
Ansible learning summary (9) -- ansible loop, condition judgment, trigger, processing failure and other task control use summary
Yearning-SQL审核平台
USB通信协议深入理解
随机推荐
手机app外卖订餐个人中心页面
自动化测试:Robot FrameWork框架大家都想知道的实用技巧
In depth understanding of USB communication protocol
Target detection 1 -- actual operation of Yolo data annotation and script for converting XML to TXT file
Mobile app takeout ordering personal center page
Hutool - 轻量级 DB 操作解决方案
三仙归洞js小游戏源码
Download, installation and development environment construction of "harmonyos" deveco
线上比赛相关规则补充说明
AI defeated mankind and designed a better economic mechanism
手撕Nacos源码(先撕客户端源码)
Discuss | what preparations should be made before ar application is launched?
Dragging the custom style of Baidu map to the right makes the global map longitude 0 unable to be displayed normally
Simple loading animation
通过 Play Integrity API 的 nonce 字段提高应用安全性
Self made dataset in pytoch for dataset rewriting
[principle and technology of network attack and Defense] Chapter 7: password attack technology Chapter 8: network monitoring technology
[trusted computing] Lesson 11: TPM password resource management (III) NV index and PCR
Use seven methods to enhance all the images in a folder
物联网OTA技术介绍