当前位置:网站首页>Leetcode problem solving -- 173 Binary search tree iterator
Leetcode problem solving -- 173 Binary search tree iterator
2022-07-06 03:07:00 【Snowy solitary boat】
Iterative thinking
private TreeNode node;
private Stack<TreeNode> stack;
public BSTIterator(TreeNode root) {
this.node =root;
stack = new Stack<>();
}
public int next() {
while (node !=null){
stack.push(node);
node = node.left;
}
node = stack.pop();
int next = node.val;
node = node.right;
return next;
}
public boolean hasNext() {
return node !=null||!stack.isEmpty();
}
Ideas : The iterative scheme based on the middle order traversal is improved
Every call next Get the value of a node
At the same time, the judgment conditions of the original cycle are extracted to hasNext Method to go
Be careful :
This scheme is based on the understanding of the iterative method of middle order traversal , If a little partner doesn't know , And I want to know more about the explanation idea of middle order traversal iteration , Sure Click here to jump
Other options
In fact, you can recursively traverse the tree once , Put it in an array , Creating index variables can also achieve the above functions ,leetcode The official also has corresponding solutions , But I want to , In fact, iterators are originally what I can do as much as you want , If it is realized in this way , Small amount of data is OK , If it's big data , It will undoubtedly cause bad time loss , So I didn't write it out , Interested students can Click here Jump leetcode Official explanation
边栏推荐
- Mysql database operation
- 适合程序员学习的国外网站推荐
- Pure QT version of Chinese chess: realize two-man, man-machine and network games
- 07 singleton mode
- 【Kubernetes 系列】一文學會Kubernetes Service安全的暴露應用
- 张丽俊:穿透不确定性要靠四个“不变”
- Audio-AudioRecord Binder通信机制
- Daily question brushing plan-2-13 fingertip life
- 【paddle】加载模型权重后预测报错AttributeError: ‘Model‘ object has no attribute ‘_place‘
- Modeling specifications: naming conventions
猜你喜欢
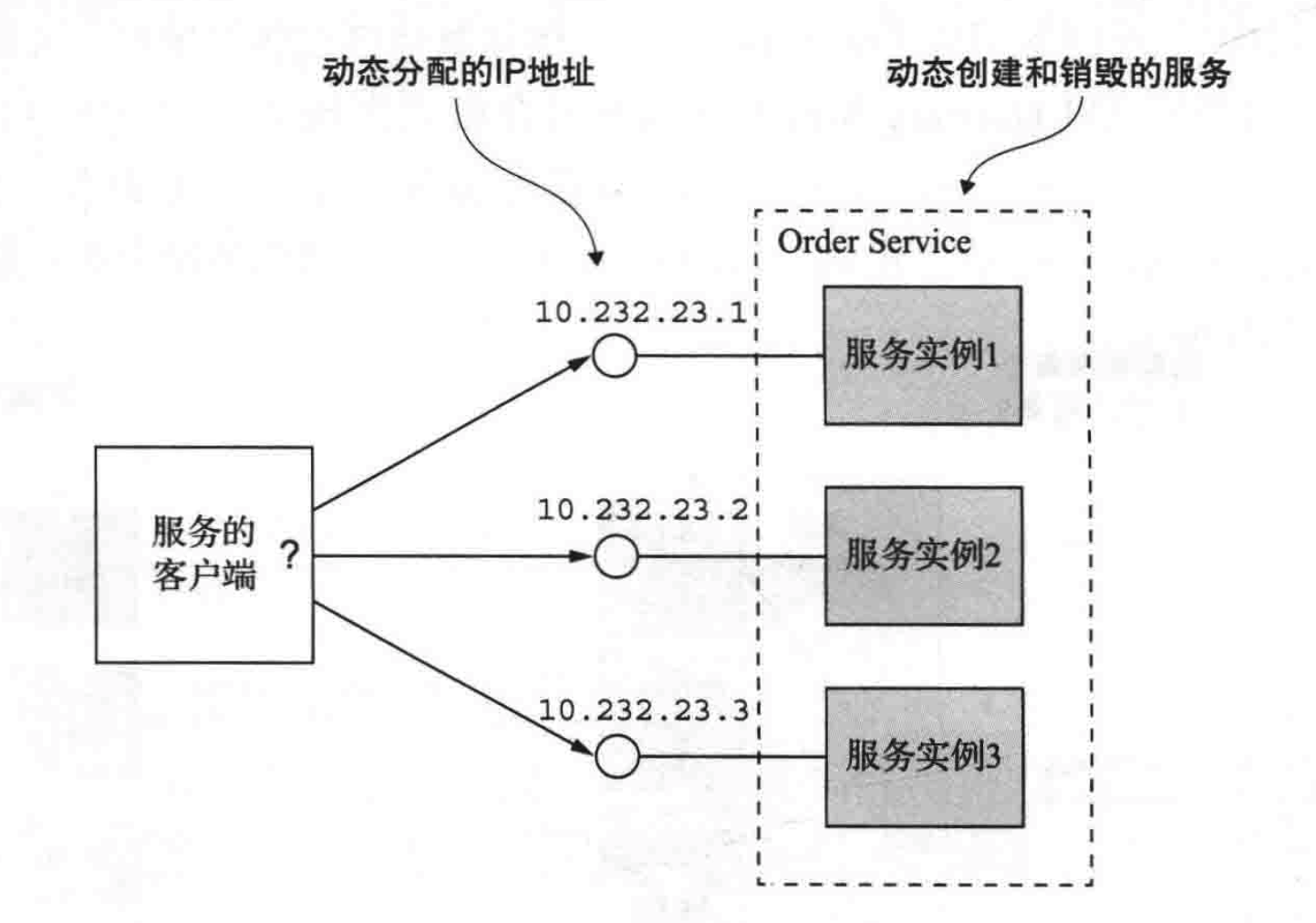
微服务注册与发现

Software design principles
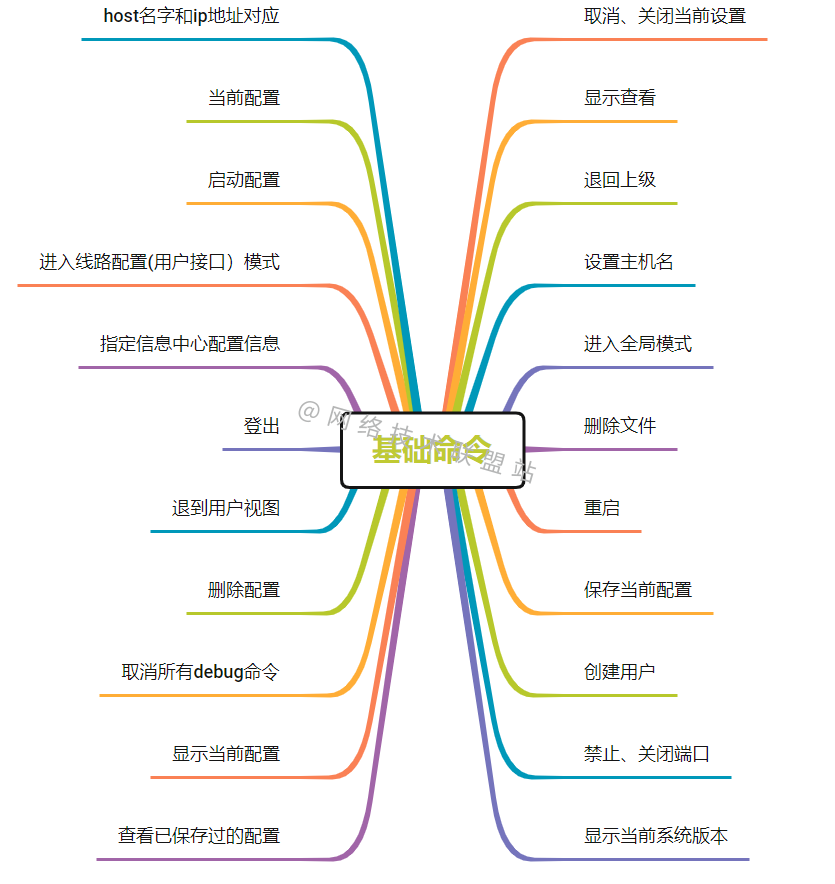
华为、H3C、思科命令对比,思维导图形式从基础、交换、路由三大方向介绍【转自微信公众号网络技术联盟站】
Solution: attributeerror: 'STR' object has no attribute 'decode‘
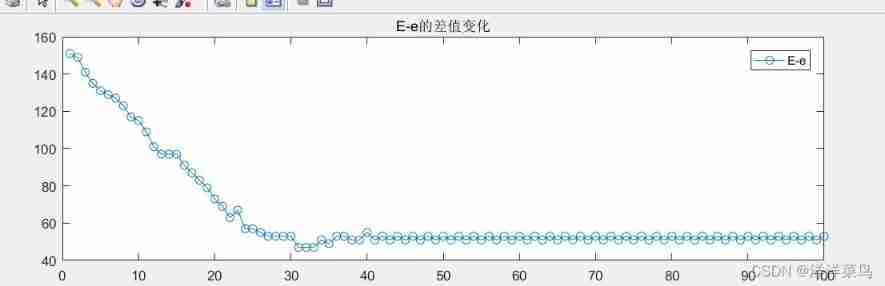
Game theory matlab
适合程序员学习的国外网站推荐
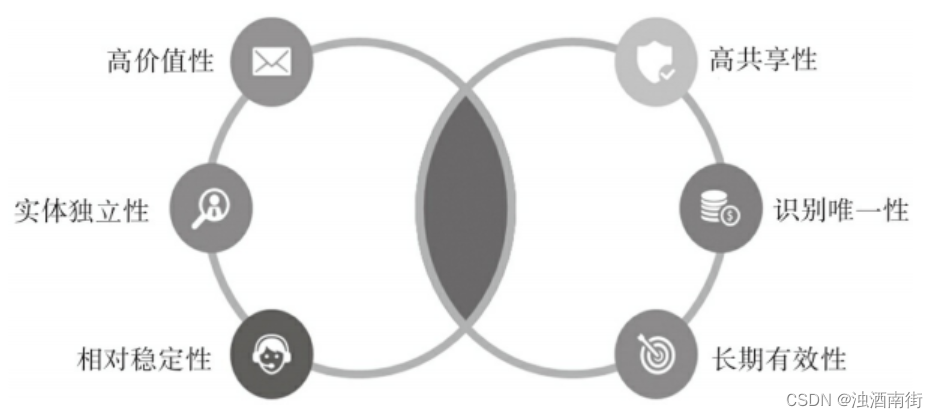
如何精准识别主数据?
【Unity3D】GUI控件
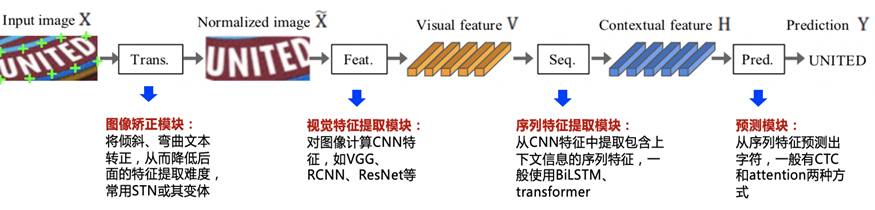
Résumé des méthodes de reconnaissance des caractères ocr
Pure QT version of Chinese chess: realize two-man, man-machine and network games
随机推荐
C # create self host webservice
Introduction to robotframework (I) brief introduction and use
BUUCTF刷题笔记——[极客大挑战 2019]EasySQL 1
jsscript
【若依(ruoyi)】设置主题样式
Taobao focus map layout practice
RobotFramework入门(三)WebUI自动化之百度搜索
Gifcam v7.0 minimalist GIF animation recording tool Chinese single file version
2022工作中遇到的问题四
全国大学生信息安全赛创新实践赛初赛---misc(永恒的夜)
Prototype design
How to improve the enthusiasm of consumers when the member points marketing system is operated?
Which ecology is better, such as Mi family, graffiti, hilink, zhiting, etc? Analysis of five mainstream smart brands
主数据管理理论与实践
2.13 simulation summary
JS regular filtering and adding image prefixes in rich text
原型图设计
Codeforces 5 questions par jour (1700 chacune) - jour 6
Redis SDS principle
OCR文字识别方法综述