当前位置:网站首页>Mysql database operation
Mysql database operation
2022-07-06 03:05:00 【_ half past seven】
Mysql Basic operation
1、 Connect to database
Get into mysql Of bin Enter in the address bar under the directory cmd
Enter the command :
mysql -u root -p
After that “ Enter password: ” A hint of , Enter the password to log in

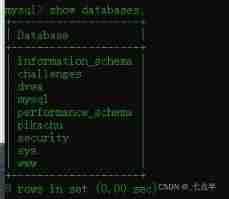
2、 Displays all databases in the system
Enter the command
show databases;
Most of the sql The commands have semicolons (;) As an end sign
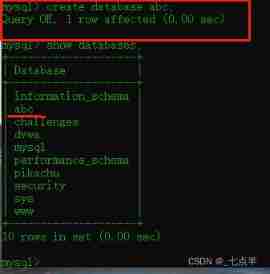
3、 New database abc
command :
create database abc;
After the creation is successful, use the following command to view the results
show databases;
4、 Using a database abc
command :
use abc;
![]()
5、 In the database abc Create a table aaa
command :
create table aaa(id int(10),name varchar(20),username varchar(20),password varchar(20),age int(3));
![]()
6、 Add data to the table
increase 8 Data :
command :
insert into aaa(id,name,username,password,age) values(1,"zhao","111","zhao111",25);
insert into aaa(id,name,username,password,age) values(2,"qian","222","qian222",27);
insert into aaa(id,name,username,password,age) values(3,"sun","333","sun333",24);
insert into aaa(id,name,username,password,age) values(4,"li","444","li444",28);
insert into aaa(id,name,username,password,age) values(5,"zhou","555","zhou555",22);
insert into aaa(id,name,username,password,age) values(6,"wu","666","wu666",29);
insert into aaa(id,name,username,password,age) values(7,"zheng","777","zheng777",20);
insert into aaa(id,name,username,password,age) values(8,"wang","888","wang888",21);
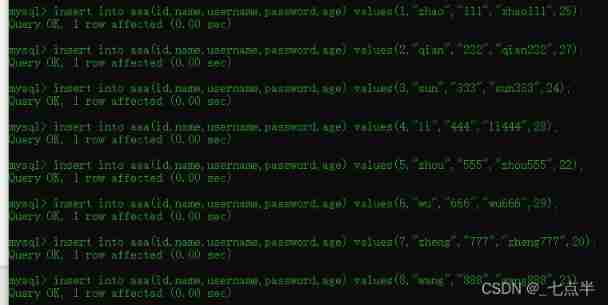
After successful insertion, you can use the following command to view aaa Everything in the table :
select * from aaa;
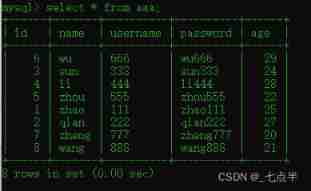
7、 In the table aaa Delete data from
Delete id=5 The data of , command :
delete from aaa where id=5;
After deleting successfully , View results :
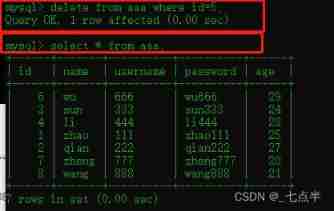
8、 Modify table aaa The data of
modify id=3 The data of , Put it password Set to 123456789, command :
update aaa set password=123456789 where id=3;
After deleting successfully , View results :
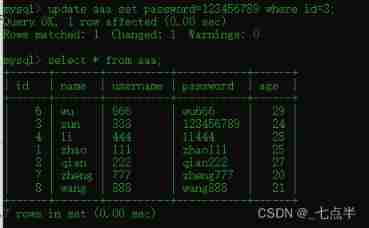
9、 Query table aaa Data in
Query all the data
select * from aaa;
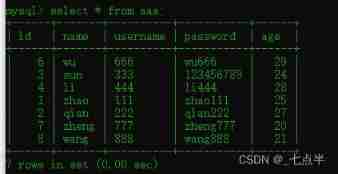
Look up id and name Field
select id,name from aaa;
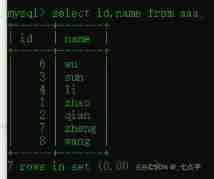
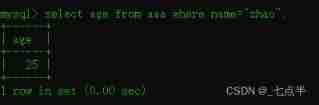
Inquire about name by zhao Of age
select age from aaa where name="zhao";
MySQL Advanced operation
1、order by Usage of
(1) take aaa The data in the table is sorted by age from high to low :
select * from aaa order by age desc;
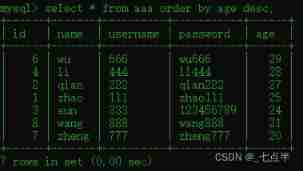
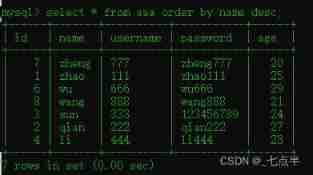
(2) take aaa The data in the table are based on name From high to low (z-a) Sort :
select * from aaa order by name desc;
2、limit Usage of
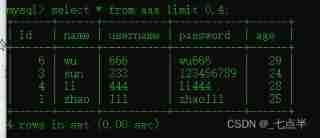
The first... In the query table 4 Data
select * from aaa limit 0,4;
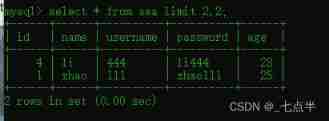
From the query table 2 Bar start ,2 Data
select * from aaa limit 2,2;
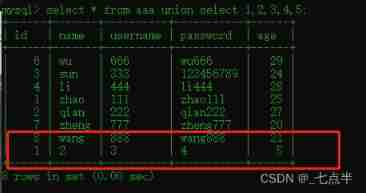
3、union select Usage of
select * from aaa union select 1,2,3,4,5;
The result of this command is ,select * from aaa Query results and select 1,2,3,4,5 The result of stitching
4、union select combination information_schema database
MySQL5.0 There is a version called information_schema The database of , It stores all the information in the database , It's about MySQL Information about all other databases maintained by the server . Such as database name , Table of database , Data type and access right of table column . and 5.0 There is no .
show databases;
select schema_name from information_schema.schemata;
The result of the two commands is the same , Enter the names of all databases

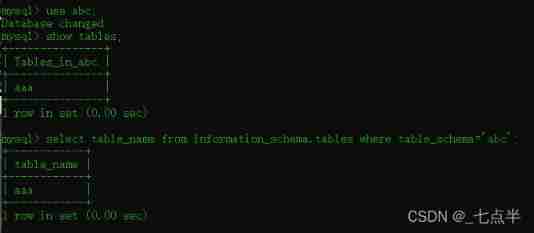
use abc;
show tables;
select table_name from information_schema.tables where table_schema='abc';
The result of the two commands is the same , It's all output abc Table of database
边栏推荐
- 有没有完全自主的国产化数据库技术
- Patch NTP server at the beginning of DDoS counterattack
- Selenium share
- Trends in DDoS Attacks
- DDoS "fire drill" service urges companies to be prepared
- 【Kubernetes 系列】一文學會Kubernetes Service安全的暴露應用
- What are the principles of software design (OCP)
- PMP practice once a day | don't get lost in the exam -7.5
- [kubernetes series] learn the exposed application of kubernetes service security
- RobotFramework入门(一)简要介绍及使用
猜你喜欢

PMP practice once a day | don't get lost in the exam -7.5
Reverse repackaging of wechat applet
QT release exe software and modify exe application icon
纯Qt版中国象棋:实现双人对战、人机对战及网络对战
How to accurately identify master data?
如何做好功能测试
A copy can also produce flowers
Fault analysis | analysis of an example of MySQL running out of host memory

My C language learning record (blue bridge) -- on the pointer
Taobao focus map layout practice
随机推荐
2.11 simulation summary
手写数据库客户端
Qt发布exe软件及修改exe应用程序图标
张丽俊:穿透不确定性要靠四个“不变”
全国大学生信息安全赛创新实践赛初赛---misc(永恒的夜)
Zhang Lijun: penetrating uncertainty depends on four "invariants"
MySQL learning notes-10-tablespace recycling
[kubernetes series] learn the exposed application of kubernetes service security
Follow the mouse's angle and keyboard events
Technology sharing | what if Undo is too big
不赚钱的科大讯飞,投资价值该怎么看?
Function knowledge points
codeforces每日5題(均1700)-第六天
如何做好功能测试
Analyze menu analysis
[ruoyi] enable Mini navigation bar
Apt installation ZABBIX
NR modulation 1
Single instance mode of encapsulating PDO with PHP in spare time
07 单件(Singleton)模式
