当前位置:网站首页>Analyze 菜单分析
Analyze 菜单分析
2022-07-06 03:00:00 【thoughtCodes】
Analyze 菜单分析
- 目录
- 概述
- 设计思路
- 实现思路分析
- 1.Inspact code
- 2.code clean up
- 3.silnet cleanup
- 4.
- 5.配置当前的视察文件
- inter nuntity
- show data cover
- generate coverage report
- hide covergage
- analysize dependiences
- Analyise background dependies
- Analyise modeul dependiences
- analyise circle denpendience
- Analysis data tohere
- Analysis datea from here
- Analysiss stack trace or thead dump
- 拓展实现
- 性能参数测试:
- 参考资料和推荐阅读
Survive by day and develop by night.
talk for import biz , show your code,I am busy,make a better result.
目录
概述
需求:
设计思路
实现思路分析
1.Inspact code
用来检查java代码质量: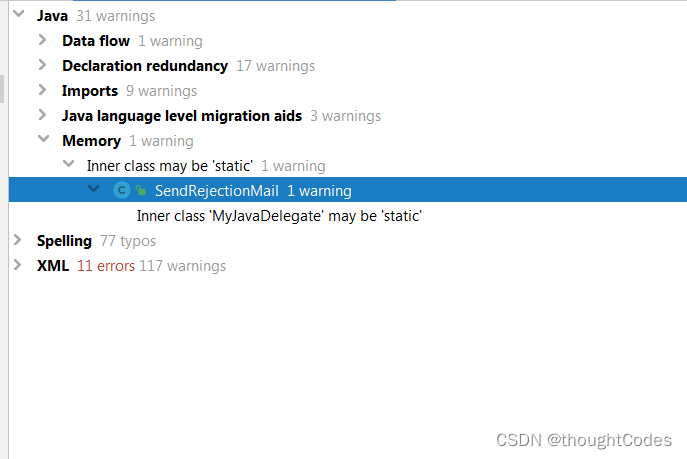
2.code clean up
代码清空文件。
3.silnet cleanup
静默模式下的代码clean up
4.
视察方法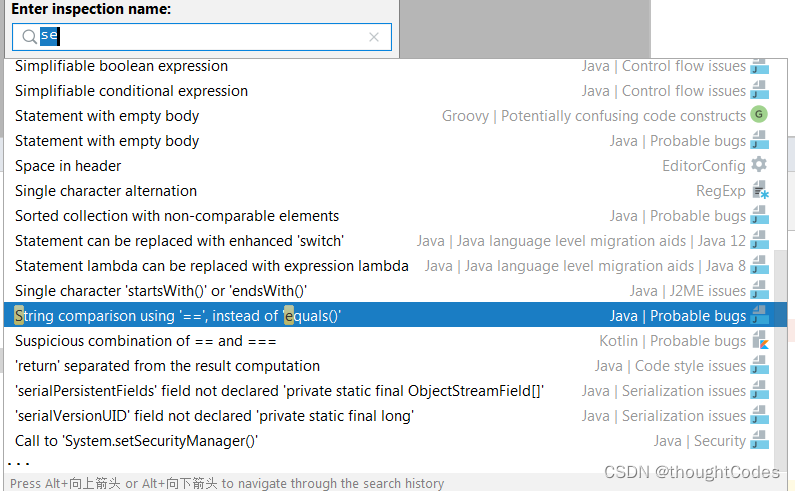
5.配置当前的视察文件
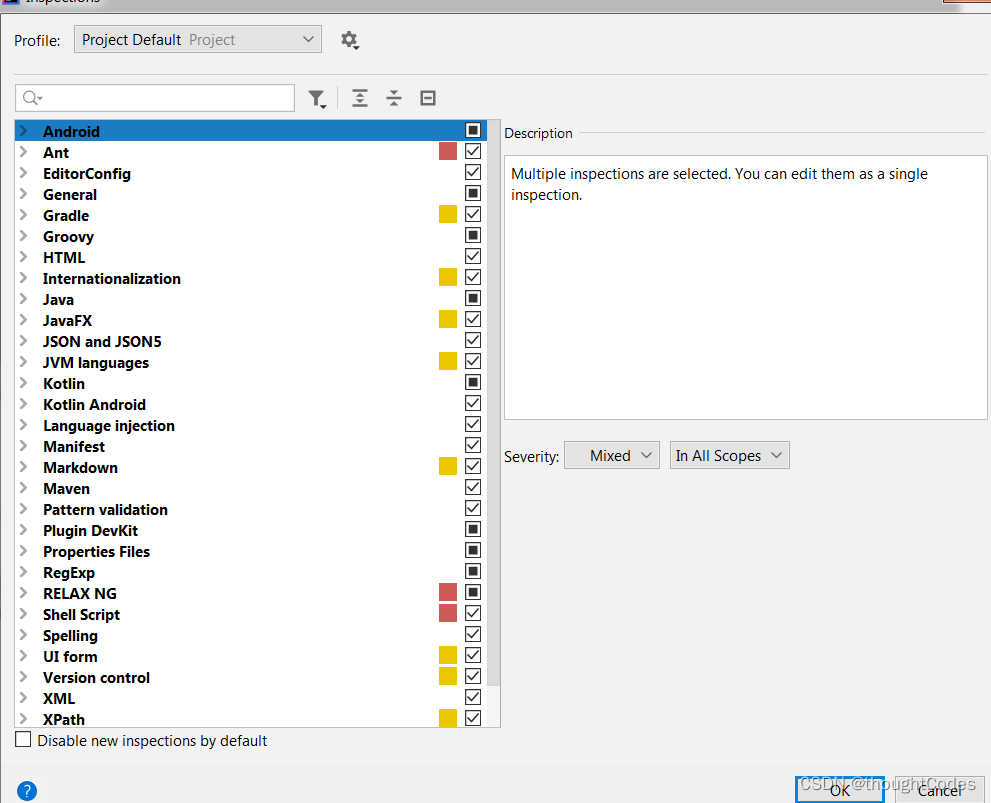
inter nuntity
代码推断
show data cover
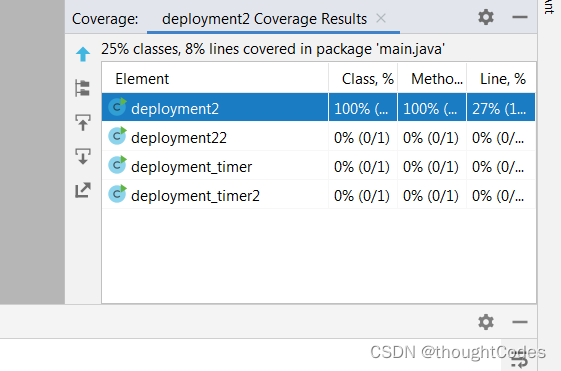
generate coverage report
生成html 的报告文件
hide covergage
隐藏覆盖
analysize dependiences
分析依赖: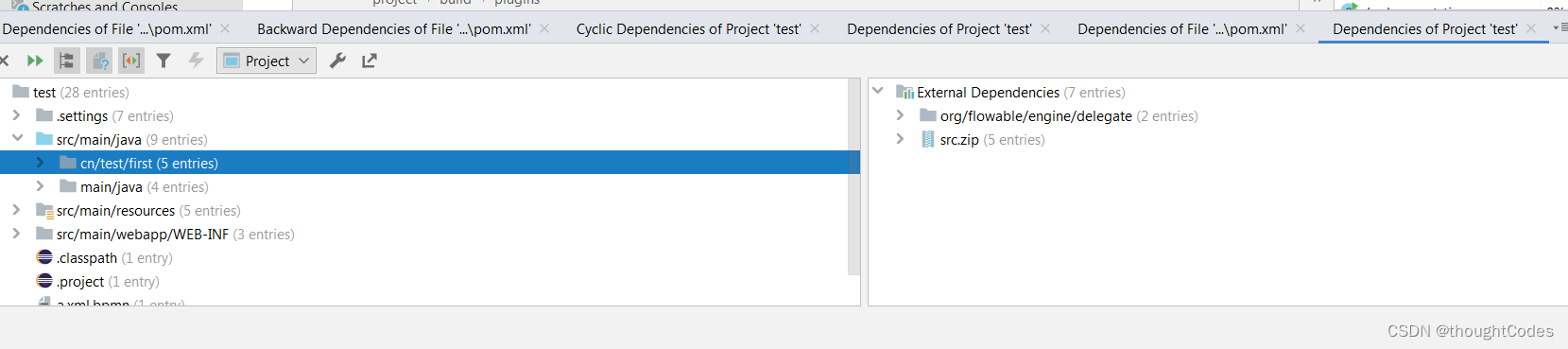
Analyise background dependies
分析反向依赖
Analyise modeul dependiences
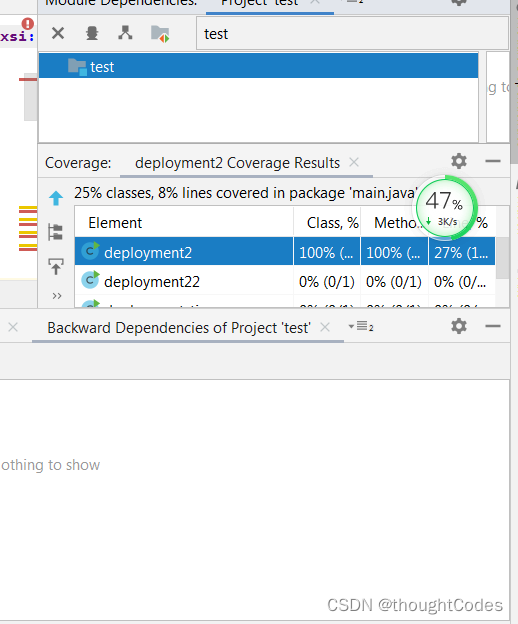
analyise circle denpendience
分析循环依赖:
分析项目是否有循环依赖:
Analysis data tohere
分析到这个数据流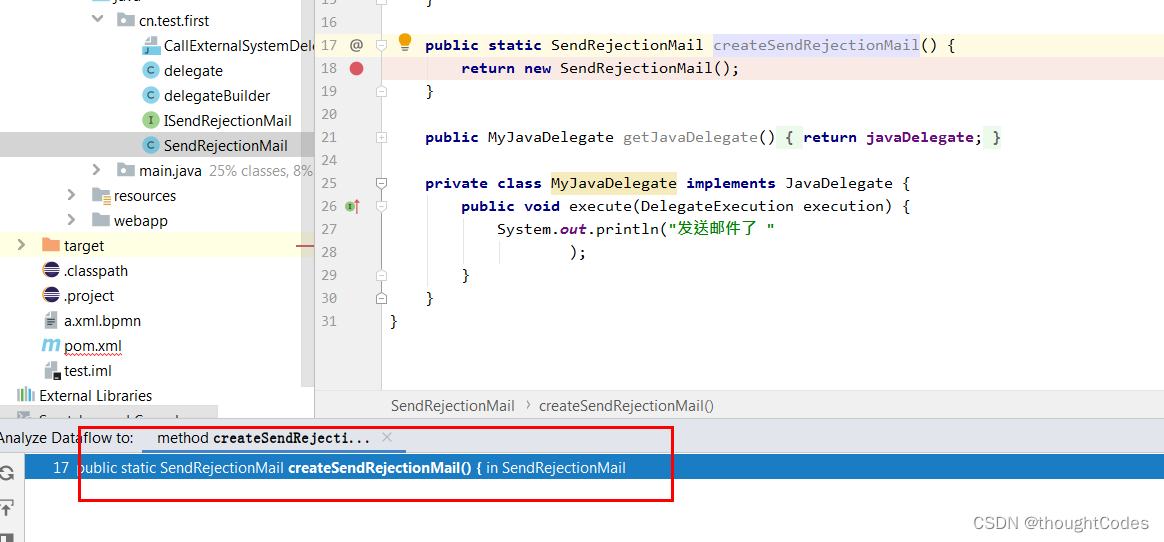
Analysis datea from here
分析到这儿的数据流
Analysiss stack trace or thead dump
分析heap,stack 轨迹,或线程dump文件。
拓展实现
这里参考:github:简单实现上述流程:
入门级实现:
: 部分源码实现.
: 源码实现
性能参数测试:
每秒大概18-20个请求,主要用于网络IO操作耗费了不少时间。
参考资料和推荐阅读
欢迎阅读,各位老铁,如果对你有帮助,点个赞加个关注呗!~
边栏推荐
- 有没有完全自主的国产化数据库技术
- Referenceerror: primordials is not defined error resolution
- Self made CA certificate and SSL certificate using OpenSSL
- Pat 1084 broken keyboard (20 points) string find
- ERA5再分析资料下载攻略
- Data and Introspection__ dict__ Attributes and__ slots__ attribute
- "Hands on learning in depth" Chapter 2 - preparatory knowledge_ 2.3 linear algebra_ Learning thinking and exercise answers
- [ruoyi] set theme style
- 原型图设计
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 13
猜你喜欢
ERA5再分析资料下载攻略
一个复制也能玩出花来
![[Chongqing Guangdong education] higher mathematics I reference materials of Southwest Petroleum University](/img/0f/520242492524522c887b6576463566.jpg)
[Chongqing Guangdong education] higher mathematics I reference materials of Southwest Petroleum University
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 23](/img/72/a80ee7ee7b967b0afa6018070d03c9.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 23
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 20](/img/d5/4bce239b522696b5312b1346336b5f.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 20
![[Yu Yue education] basic reference materials of digital electronic technology of Xi'an University of Technology](/img/47/e895a75eb3af2aaeafc6ae76caafe4.jpg)
[Yu Yue education] basic reference materials of digital electronic technology of Xi'an University of Technology
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 22](/img/e0/21367eeaeca10c0a2f2aab3a4fa1fb.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 22

Codeforces 5 questions par jour (1700 chacune) - jour 6
RobotFramework入门(一)简要介绍及使用
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 24](/img/2e/b1f348ee6abaef24b439944acf36d8.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 24
随机推荐
Briefly describe the implementation principle of redis cluster
4. File modification
Deeply analyze the chain 2+1 mode, and subvert the traditional thinking of selling goods?
Microservice registration and discovery
Fault analysis | analysis of an example of MySQL running out of host memory
Solve 9 with C language × 9 Sudoku (personal test available) (thinking analysis)
How to improve the enthusiasm of consumers when the member points marketing system is operated?
[ruoyi] ztree custom icon (iconskin attribute)
jsscript
Linear regression and logistic regression
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 11
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 14
Jenkins basic knowledge ----- detailed explanation of 03pipeline code
有没有完全自主的国产化数据库技术
Solution: attributeerror: 'STR' object has no attribute 'decode‘
Day 50 - install vsftpd on ceontos6.8
OCR文字识别方法综述
纯Qt版中国象棋:实现双人对战、人机对战及网络对战
Web security SQL injection vulnerability (1)
2.13 simulation summary