当前位置:网站首页>Zephyr 学习笔记2,Scheduling
Zephyr 学习笔记2,Scheduling
2022-07-04 07:16:00 【mayiQX】
第二章:调度器(Scheduling)。
内核基于优先级的调度器允许应用程序的线程共享CPU。
线程从运行状态转换为挂起或等待状态,例如通过k_sem_take()或者k_sleep()。
线程转换到就绪状态,例如使用k_sem_give()或者k_thread_start()。
处理中断后返回线程上下文,当运行的线程调用k_yield()时。
当线程主动启动一个将自身转换为挂起或等待状态的操作时,它将休眠。
协作式
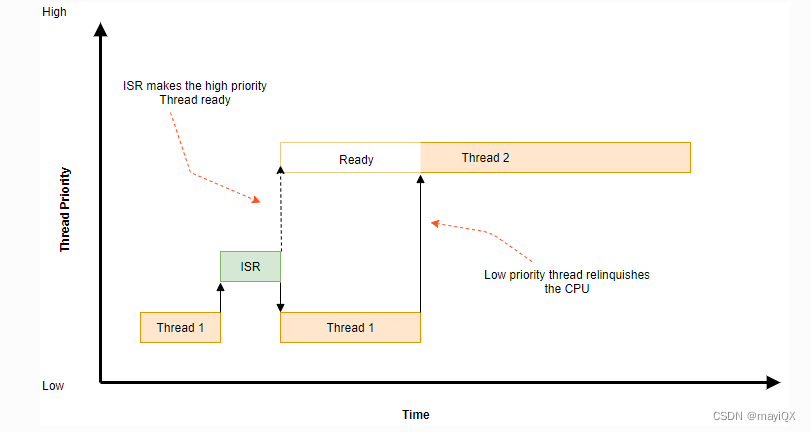
抢占式
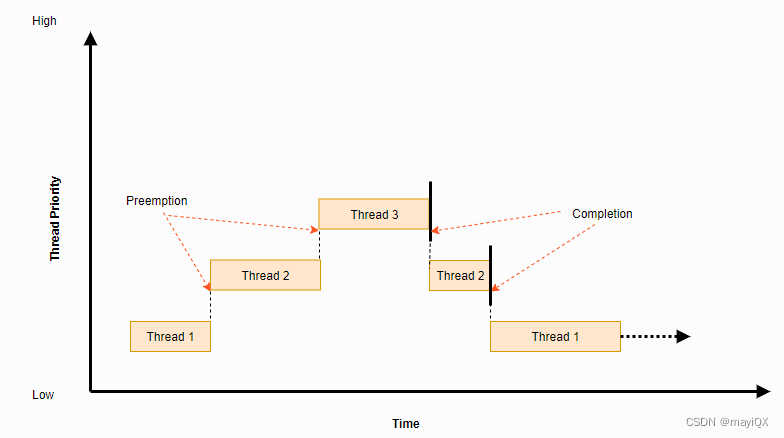
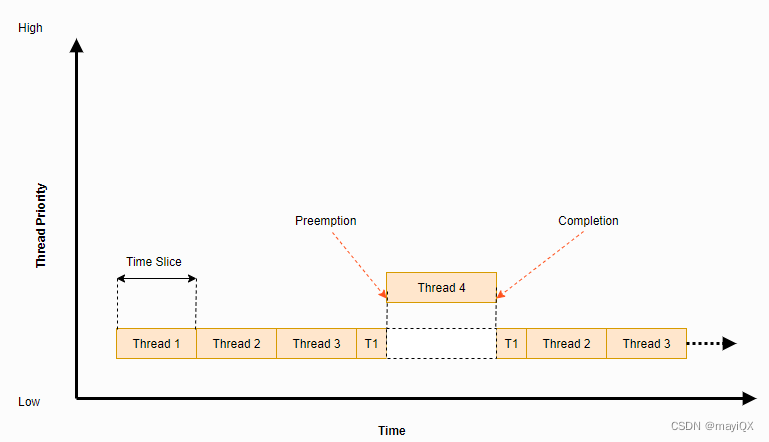
Scheduler Locking
在执行关键操作时不希望被抢占的可抢占线程可以通过调用k_sched_lock().一旦关键操作完成,可抢占线程必须调用k_sched_unlock()以恢复其正常的可抢占状态。
Thread Sleeping
k_sleep()
k_wakeup()
线程可以调用k_busy_wait()来执行繁忙等待,该等待将其处理延迟指定的时间段,而不会将CPU放弃给另一个就绪线程。
CPU Idling
static k_sem my_sem;
void my_isr(void *unused)
{
k_sem_give(&my_sem);
}
void main(void)
{
k_sem_init(&my_sem, 0, 1);
/* wait for semaphore from ISR, then do related work */
for (;;) {
/* wait for ISR to trigger work to perform */
if (k_sem_take(&my_sem, K_NO_WAIT) == 0) {
/* ... do processing */
}
/* put CPU to sleep to save power */
k_cpu_idle();
}
}边栏推荐
- tornado项目之路由装饰器
- 【森城市】GIS数据漫谈(一)
- [Valentine's day] - you can change your love and write down your lover's name
- If there are two sources in the same job, it will be reported that one of the databases cannot be found. Is there a boss to answer
- Selection (023) - what are the three stages of event propagation?
- 输入年份、月份,确定天数
- The number of patent applications in China has again surpassed that of the United States and Japan, ranking first in the world for 11 consecutive years
- Enter the year, month, and determine the number of days
- com. alibaba. nacos. api. exception. NacosException
- socket inet_ pton() inet_ Ntop() function (a new network address translation function, which converts the expression format and numerical format to each other. The old ones are inet_aton(), INET_ ntoa
猜你喜欢

The number of patent applications in China has again surpassed that of the United States and Japan, ranking first in the world for 11 consecutive years
Adaptive spatiotemporal fusion of multi-target networks for compressed video perception enhancement
Selenium ide plug-in download, installation and use tutorial
![[GF (q) + LDPC] regular LDPC coding and decoding design and MATLAB simulation based on the GF (q) field of binary graph](/img/5e/7ce21dd544aacf23b4ceef1ec547fd.png)
[GF (q) + LDPC] regular LDPC coding and decoding design and MATLAB simulation based on the GF (q) field of binary graph
How to share the source code anti disclosure scheme
Zhanrui tankbang | jointly build, cooperate and win-win zhanrui core ecology

云Redis 有什么用? 云redis怎么用?
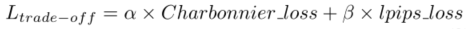
用于压缩视频感知增强的多目标网络自适应时空融合
![SQL foundation 9 [grouping data]](/img/8a/a72941d8c3413316b063033a1b5038.jpg)
SQL foundation 9 [grouping data]
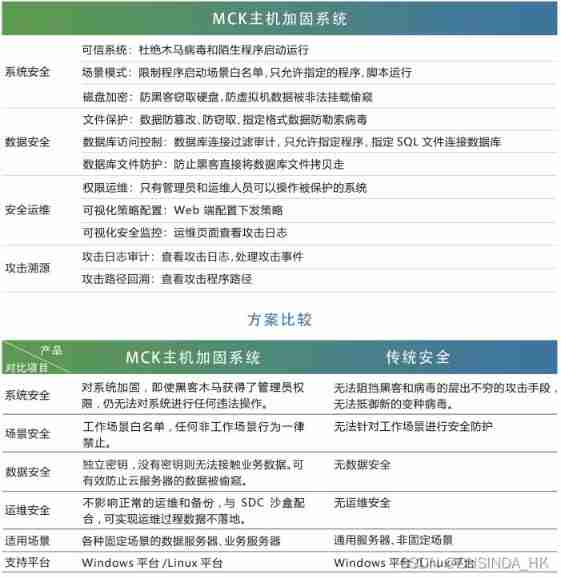
Industrial computer anti-virus
随机推荐
Latex中的单引号,双引号如何输入?
Zabbix agent主动模式的实现
Design of test cases
MySQL 45 lecture learning notes (x) force index
MySQL error resolution - error 1261 (01000): row 1 doesn't contain data for all columns
请问旧版的的常用SQL怎么迁移到新版本里来?
What is the use of cloud redis? How to use cloud redis?
Boast about Devops
输入年份、月份,确定天数
SQL foundation 9 [grouping data]
If there are two sources in the same job, it will be reported that one of the databases cannot be found. Is there a boss to answer
Master-slave replication principle of MySQL database
果果带你写链表,小学生看了都说好
tornado项目之路由装饰器
kubernetes集群之Label管理
Crawler (III) crawling house prices in Tianjin
Deep understanding of redis -- a new type of bitmap / hyperloglgo / Geo
Rhcsa the next day
the input device is not a TTY. If you are using mintty, try prefixing the command with ‘winpty‘
【森城市】GIS数据漫谈(一)