当前位置:网站首页>Telnet,SSH1,SSH2,Telnet/SSL,Rlogin,Serial,TAPI,RAW
Telnet,SSH1,SSH2,Telnet/SSL,Rlogin,Serial,TAPI,RAW
2022-07-07 01:38:00 【Full stack programmer webmaster】
Hello everyone , I meet you again , I'm the king of the whole stack
One 、Telnet
use Telnet To access a remote computer TCP/IP Protocol to control your network devices , It's like yelling at you when you leave a building username And password . Soon someone will be listening , And they will take advantage of your lack of safety awareness . Traditional network services such as :ftp、pop and telnet It's not safe in nature , Because they transmit passwords and data in clear text on the network , other Practical people are very easy You can intercept these passwords and data . also , The security verification methods of these service programs also have their weaknesses . It's just very easy suffer “ A middleman ”(man-in-the- middle) Attack in this way . So-called “ A middleman ” How to attack , Namely “ A middleman ” Pretending to be real server Receive your message to server The data of , Then pretend to pass the data to the real service device .server The data transmission with you is “ A middleman ” Once you've done something . There will be very serious problems .
Telnet Agreement is TCP/IP A member of the protocol family , yes Internet The standard protocol and main way of remote login service . It provides users with the ability to complete the work of the remote host on the local computer . Use on the end user's computer telnet Program . Use it to connect to server. End users are able to telnet Enter the command in the program , These orders will be in server On the implementation . It's like directly in server The input on the console is the same .
It can be controlled locally server.
To start a telnet conversation . Must input username and password To log in server.Telnet It is often used for remote control Webserver Methods .
Telnet The remote login service is divided into the following 4 A process :
1) Local connection with remote host .
The process is actually creating a TCP Connect , The user must know the remote host's Ip Address or domain name ;
2) Input on the local terminal username And password and any command or character entered later with NVT(Net Virtual Terminal) Format transfer to remote host .
This process actually sends a message from the local host to the remote host IP Data packets .
3) Output from the remote host NVT The data in the format is converted to a locally accepted format and sent back to the local terminal . Including the echo of input commands and the results of command operation ;
4) Last , The local terminal cancels the connection to the remote host . The process is to undo a TCP Connect .
Two 、SSH
SSH by Secure Shell Abbreviation , from IETF Network working group of (Network Working Group) Established by ;SSH For security protocols based on application layer and transport layer .SSH It's more reliable right now , A protocol designed to provide security for remote login sessions and other network services .
utilize SSH The protocol can effectively prevent information leakage in the process of remote management .SSH Is an alternative Telnet And other remote console management applications .
SSH The command is encrypted and kept secret in several ways .SSH It has many functions , It can replace telnet, And be able to serve ftp、pop、 even to the extent that ppp Provide a safe “ passageway ”.SSH(Secure SHell) There are two incompatible version numbers so far ——SSH1 and SSH2.
SSH1 It is divided into 1.3 and 1.5 Two version numbers .SSH1 Adopt DES、3DES、Blowfish and RC4 Equal symmetric encryption algorithm to protect data security transmission , The key of symmetric encryption algorithm It is through asymmetric encryption algorithm (RSA) Come and finish the exchange .
SSH1 Using cyclic redundancy check codes (CRC) To ensure data integrity , But later, it was found that this method had defects .
SSH2 Avoided RSA The issue of patents , And mended CRC The defects of .SSH2 With digital signature algorithms (DSA) and Diffie-Hellman(DH) Algorithm substitution RSA To complete the exchange of symmetric keys , Confirm the code with a message (HMAC) To replace CRC. At the same time SSH2 Added AES and Twofish Equal symmetric encryption algorithm .
3、 ... and 、Telnet/SSL
Secure Socket Layer, by Netscape Developed by , To secure in Internet Security of uploading and inputting data , Using data encryption (Encryption) technology , It can ensure that the data will not be intercepted and eavesdropped during the transmission on the network . At present, the general specification is 40 bit Safety standards , The United States has launched 128 bit It's a higher safety standard , But restrictions on exit . Just 3.0 Version number above I.E. or Netscape Browsers can support SSL.
The current version number is 3.0. It has been widely used in Web Browser and server Between authentication and encrypted transmission of data .
SSL The agreement is located at TCP/IP Protocol and various application layer protocols , Provide security support for data communication .
SSL The agreement can be divided into two layers : SSL Record agreements (SSL Record Protocol): It's built on reliable transport protocols ( Such as TCP) above . Provide data encapsulation for high-level protocols 、 Compress 、 Encryption and other basic functions .
SSL handshake protocol (SSL Handshake Protocol): It is based on SSL Record the agreement above , Used before the actual transmission data starts , The two communicating parties conduct identity authentication 、 Negotiate encryption algorithms 、 Exchange encryption key, etc .
SSL The services provided by the agreement mainly include :
1) Authenticated users and server, Ensure that the data is sent to the correct client and server.
2) Encrypt data to prevent it from being stolen in the middle of the process ;
3) Maintain data integrity , Make sure that the data is not changed during transmission .
SSL(Secure Sockets Layer Secure socket layer ), And its successor transport layer security (Transport Layer Security,TLS) It is a security protocol that provides security and data integrity for network communication , Is certificate based authentication .
Telnet/SSL It's with SSL Of Telnet.
Four 、Rlogin
Rlogin Originated in Berkeley Unix, At first it can only work in Unix Between systems . Now it can be executed on other operating systems .Rlogin and Telnet Functions are used in a similar way , But it's much simpler .
Telnet,SSH1,SSH2,Telnet/SSL,Rlogin,Serial,TAPI,RAW
Now , There's always new Telnet Options are added to Telnet In the middle , This makes Telnet The number of source code implemented has been greatly increased . and Rlogin It still hasn't changed much , It's still relatively simple .
5、 ... and 、Serial
Serial means one event at a time , It is usually the opposite of parallelism, that is, multiple events occur at one time .
In transmitting data , Time division and space separation technology are often used . The transmission of single bits in the serial transmission information is separated in time , In the case of sending multiple bits in parallel, space is used ( On multiple lines or paths ) Separate .
In computer hardware and data transmission : Serial connection 、 Operation and medium usually mean slow and simple operation , And parallelism means faster operations . Such hints are not always correct , Due to the serial medium ( such as , fiber cable ) It can be much faster than the medium that transmits multiple signals in parallel . stay PC in , Printers are usually connected through parallel interfaces and cables . So you can print faster .
Keyboard and mouse only need serial interface and circuit .
Traditional computers and their programs often work serially . The computer reads programs one by one and runs their instructions , However , Some modern computers have multiple processors . Instructions can be run in parallel .
6、 ... and 、TAPI
TAPI It is a telephone application programming interface (telephONe Application Programming Interface) Abbreviation . It enables users to talk with people on the phone or video phone on the computer .
Developers use TAPI The application written can effectively use the services of telephone service providers , Both through a simulation Modem Visit it , You can also access professional PBX (PBX) Advanced functions provided .
The computer has TAPI, And you have the right applications and hardware installed , Then you can achieve :
1. Be able to see the people you are talking to
2. Click someone's photo to call
3. Can send in your e-mail Add voice files to . You can also listen to what you receive e-mail Voice files in .
4. Use a similar graphical user interface (GUI) To set up a conference call , Then attend the meeting on time .
5. Send and receive faxes
6. Be able to code and control the computer to take the initiative to answer the call of a certain number
7. Portable wireless mobile phone
7、 ... and 、RAW
RAW Protocol is the default protocol for most printing devices . In order to send RAW Format job , Print server Will open a for the printer network interface TCP flow . For many devices . This interface will be port 9100. Creating TCP/IPport after ,Windows Will be in accordance with RFC 1759(Printer MIB), Use SNMP To query the object identifier of the device (Object Identifier.OID).
Suppose the device returns a value , Then parse the system files tcpmon.ini To find a match .
Suppose the printer manufacturer provides special configuration information for a specific device . Then these configuration information have been created together with the configuration settings .
such as , Some external printing server The interface supports multiple printers ( such as . have 3 Parallel port Connected Hewlett Packard JetDirect EX). Manufacturers can use different port To indicate which printer a job should be submitted to ( such as , Do your homework 9102 Submit to port1, Do your homework 9103 Submit to port2 wait ). This function is special for the need to use port Name printing server Interfaces help , example : some IBM On the network printer PASSport.
Copyright notice : This article is the original article of the blogger . Blog , Do not reprint without permission |Copyright 2011-2015, Kallen Ding, All Rights Reserved.
Publisher : Full stack programmer stack length , Reprint please indicate the source :https://javaforall.cn/116906.html Link to the original text :https://javaforall.cn
边栏推荐
- AcWing 346. Solution to the problem of water splashing festival in the corridor (deduction formula, minimum spanning tree)
- Add the applet "lazycodeloading": "requiredcomponents" in taro,
- Dark horse notes - exception handling
- 云呐|工单管理软件,工单管理软件APP
- Neon Optimization: About Cross access and reverse cross access
- AcWing 1141. LAN problem solving (kruskalkruskal finding the minimum spanning tree)
- 黑马笔记---创建不可变集合与Stream流
- 安利一波C2工具
- Yunna | work order management measures, how to carry out work order management
- THREE. AxesHelper is not a constructor
猜你喜欢
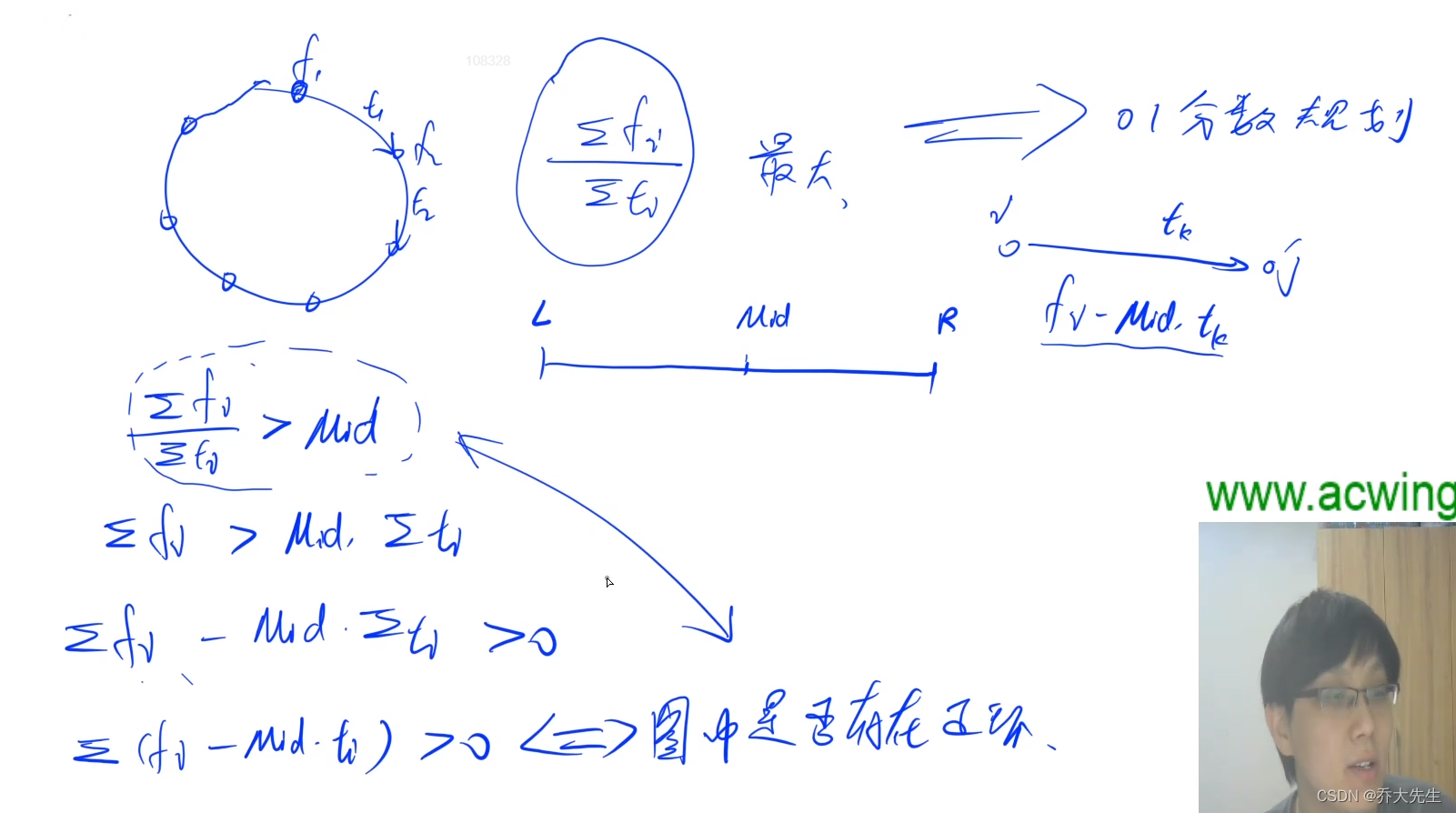
AcWing 361. Sightseeing cow problem solution (SPFA seeking positive ring)
制作带照明的DIY焊接排烟器
永久的摇篮
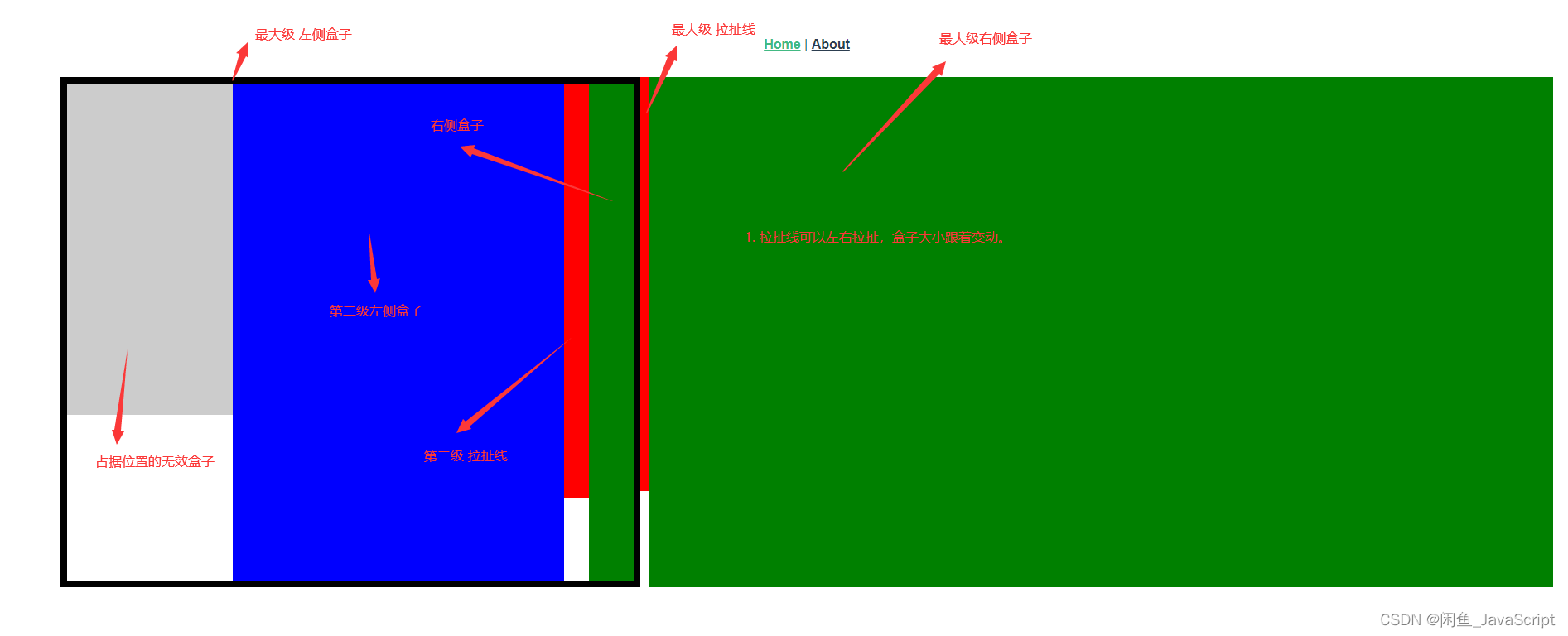
盒子拉伸拉扯(左右模式)

云呐|工单管理办法,如何开展工单管理

Yunna - work order management system and process, work order management specification

Right mouse button customization
2022 Google CTF SEGFAULT LABYRINTH wp
Body mass index program, entry to write dead applet project
AcWing 1148. Secret milk transportation problem solution (minimum spanning tree)
随机推荐
AcWing 1142. 繁忙的都市 题解(最小生成树)
405 method not allowed appears when the third party jumps to the website
WCF Foundation
2022 Google CTF SEGFAULT LABYRINTH wp
C语言实例_2
Comparison of picture beds of free white whoring
c语言—数组
WCF基金会
修改px4飞控的系统时间
How to manage distributed teams?
C language instance_ five
tansig和logsig的差异,为什么BP喜欢用tansig
swiper组件中使用video导致全屏错位
Spark TPCDS Data Gen
Sword finger offer II 035 Minimum time difference - quick sort plus data conversion
LeetCode:1175. 质数排列
shell脚本快速统计项目代码行数
2022 Google CTF SEGFAULT LABYRINTH wp
golang 基础 —— 数据类型
Set up [redis in centos7.x]