当前位置:网站首页>What does UDP attack mean? UDP attack prevention measures
What does UDP attack mean? UDP attack prevention measures
2022-07-06 06:55:00 【IDC02_ FEIYA】
UDP What does attack mean ?UDP Attack precautions
UDP What does attack mean ?
UDP Flood attack is a kind of host based denial of service attack . User datagram protocol (UDP) It's a connectionless protocol , It does not require any program to establish a connection to transmit data . When a packet passes UDP When the protocol is sent , The sending parties do not need to establish a connection through three handshakes , The receiver must receive and process the packet . Therefore, a large number of them are sent to the victim host UDP Packets can saturate the network .
together UDP Torrent attack ,UDP The message is sent to the random or designated port of the victim system . Usually ,UDP The flood attack is set as a random port pointing to the target . This makes the victim system must analyze the incoming data to determine which application service requested the data . If the victim system is being attacked , The service is not running , It will use ICMP The message responds to a “ The destination port is unreachable ” news .
Usually , In attack DDOS The tool will forge the source of the attack package IP Address . This helps hide the identity of the agent , At the same time, it can ensure that the response message from the victim host will not be returned to the agent .UDP Flood attack will also jam the network bandwidth around the victim host ( It depends on the network architecture and line speed ). therefore , Sometimes the host connected to the surrounding network of the victim system will also encounter network connection problems . If enough messages are sent to the victim's computer port UDP Data packets , The whole system will go down .
This is also why many game developers choose to seal when renting servers UDP The reason why the .
UDP Attack precautions
To ensure network security , Using firewall to filter harmful data from unknown sources can effectively reduce UDP Torrent attack . in addition , The following measures can also be taken :
1、 Disable or filter monitoring and response services .
2、 Disable or filter other UDP service .
3、 If the user must provide some UDP External access to services , Proxy mechanisms can be used to protect Services , So that it will not be abused .
4、 Monitor the user's network to know which systems are using these services , And monitor the signs of abuse .
Thank you for reading , Pay attention and don't get lost ~
边栏推荐
- Day 245/300 JS forEach 多层嵌套后数据无法更新到对象中
- UniPro甘特图“初体验”:关注细节背后的多场景探索
- 成功解决TypeError: data type ‘category‘ not understood
- LeetCode - 152 乘积最大子数组
- 【服务器数据恢复】IBM服务器raid5两块硬盘离线数据恢复案例
- 19. Actual memory management of segment page combination
- 云上有AI,让地球科学研究更省力
- [advanced software testing step 1] basic knowledge of automated testing
- Delete external table source data
- Fedora/rehl installation semanage
猜你喜欢

Due to high network costs, arbitrum Odyssey activities are suspended, and nitro release is imminent

My seven years with NLP
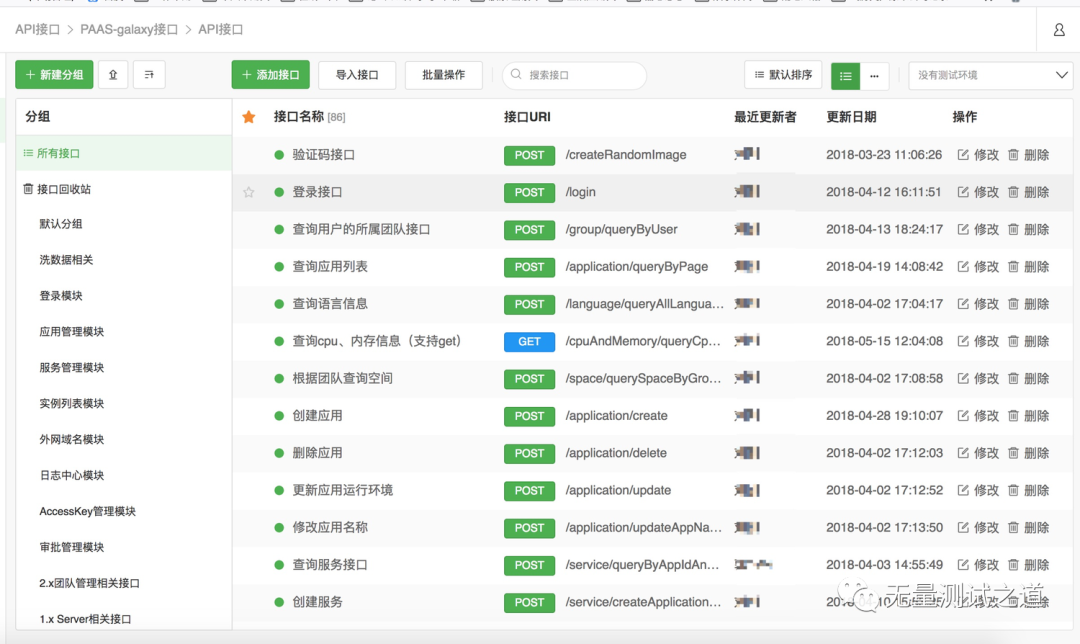
Practical guidance for interface automation testing (Part I): what preparations should be made for interface automation
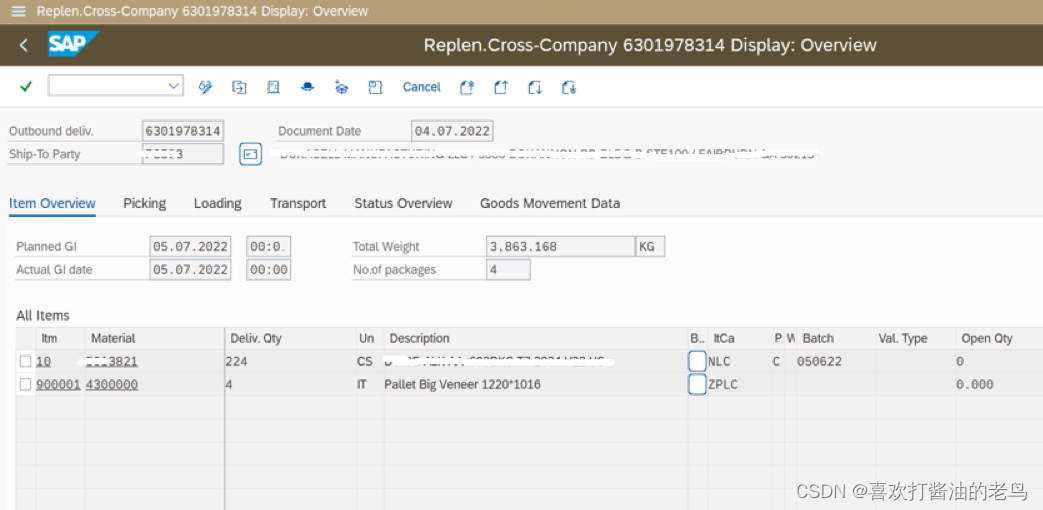
SAP SD发货流程中托盘的管理
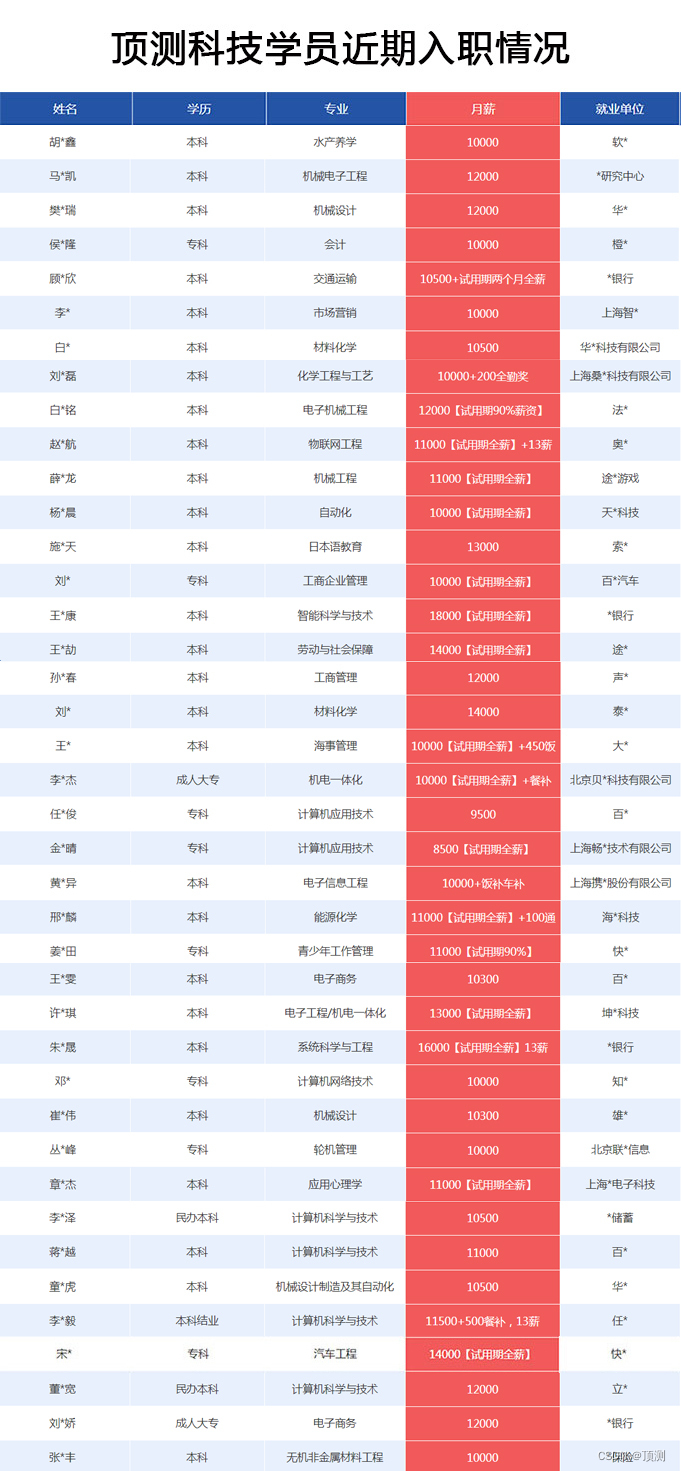
顶测分享:想转行,这些问题一定要考虑清楚!
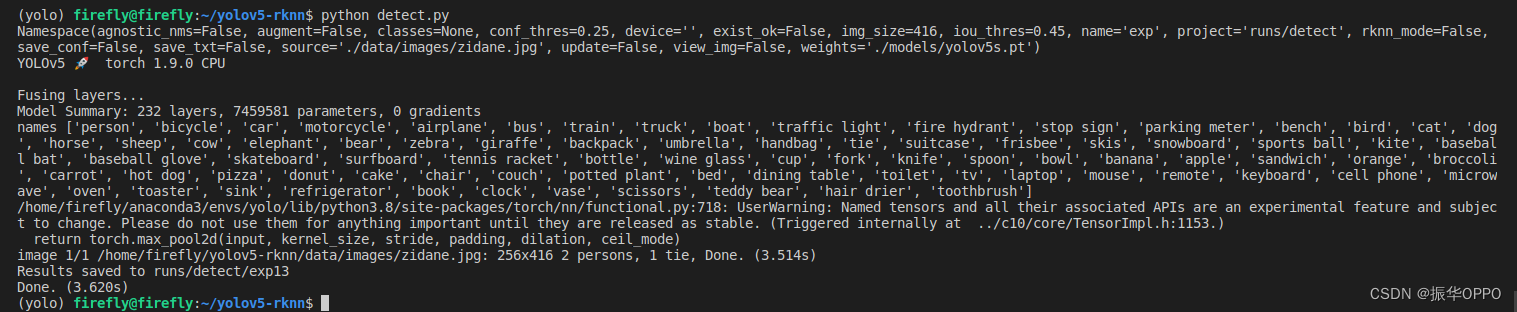
AttributeError: Can‘t get attribute ‘SPPF‘ on <module ‘models.common‘ from ‘/home/yolov5/models/comm
Misc of BUU (update from time to time)
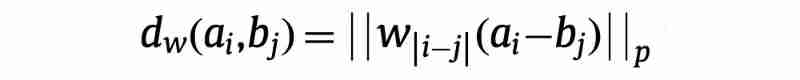
A method to measure the similarity of time series: from Euclidean distance to DTW and its variants
When my colleague went to the bathroom, I helped my product sister easily complete the BI data product and got a milk tea reward

How to reconstruct the class explosion caused by m*n strategies?
随机推荐
因高额网络费用,Arbitrum 奥德赛活动暂停,Nitro 发行迫在眉睫
Fast target recognition based on pytorch and fast RCNN
Setting and using richview trvstyle template style
ML之shap:基于adult人口普查收入二分类预测数据集(预测年收入是否超过50k)利用Shap值对XGBoost模型实现可解释性案例之详细攻略
librosa音频处理教程
基于购买行为数据对超市顾客进行市场细分(RFM模型)
Delete external table source data
kubernetes集群搭建Zabbix监控平台
Day 245/300 JS forEach 多层嵌套后数据无法更新到对象中
Apache DolphinScheduler源码分析(超详细)
成功解决AttributeError: Can only use .cat accessor with a ‘category‘ dtype
How to find a medical software testing institution? First flight software evaluation is an expert
(practice C language every day) reverse linked list II
Due to high network costs, arbitrum Odyssey activities are suspended, and nitro release is imminent
接口自动化测试框架:Pytest+Allure+Excel
AttributeError: Can‘t get attribute ‘SPPF‘ on <module ‘models.common‘ from ‘/home/yolov5/models/comm
Supporting title of the book from 0 to 1: ctfer's growth road (Zhou Geng)
Do you really know the use of idea?
Office doc add in - Online CS
At the age of 26, I changed my career from finance to software testing. After four years of precipitation, I have been a 25K Test Development Engineer