当前位置:网站首页>Performance analysis of user login TPS low and CPU full
Performance analysis of user login TPS low and CPU full
2022-07-06 03:07:00 【zuozewei】
User login is just a common function , But its logic is not simple at all . Because the login process needs to compare and verify personal information , During the verification process, the corresponding encryption algorithm must be called , Encryption algorithm is a function that requires high performance . The complex encryption algorithm has high security , But the performance is poor ; Uncomplicated encryption algorithm has good performance , But it's safe , This is a question of trade-offs .
Follow the design steps of the benchmark scenario of the test scheme , First, test the benchmark scenario of this interface .
● Problem phenomenon
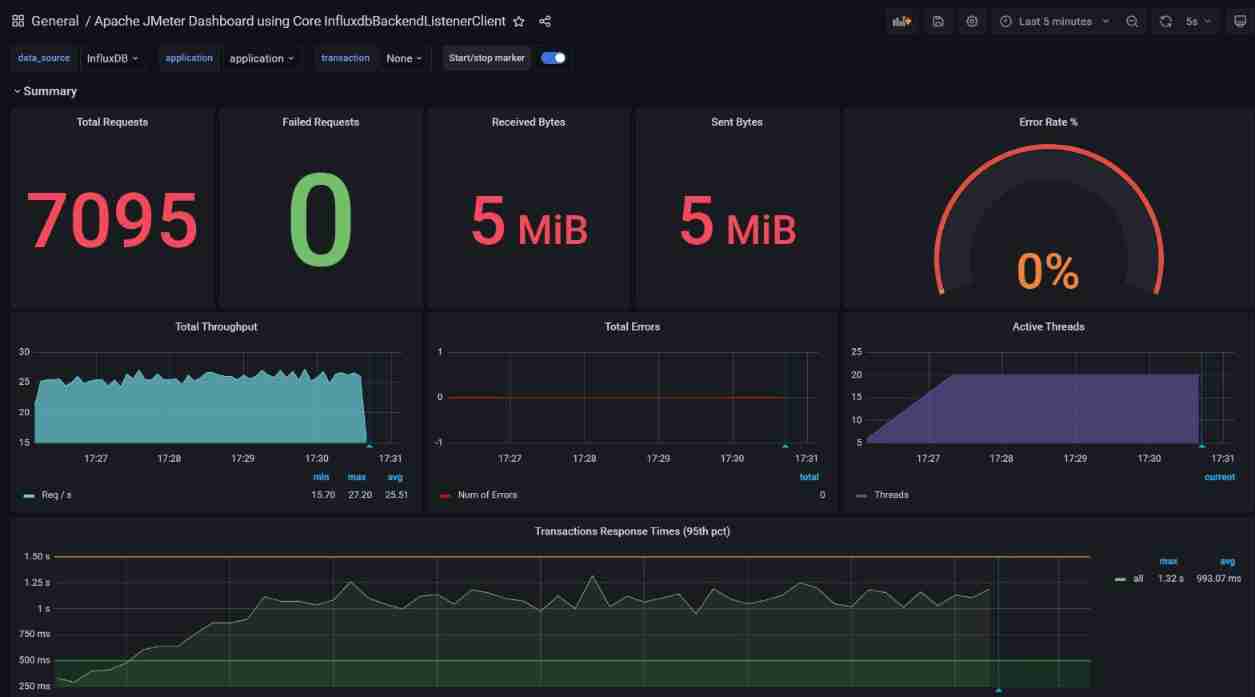
As shown in the figure above , This phenomenon is becoming more and more obvious .
In the pressure measurement results TPS The average is 25 The average response time reached 993 ms.
● The analysis process
In terms of performance analysis logic , For the problem of long response time , The first thing to do is to split the time . Since this system has been deployed SkyWalking, Use it to see where time is mainly spent .
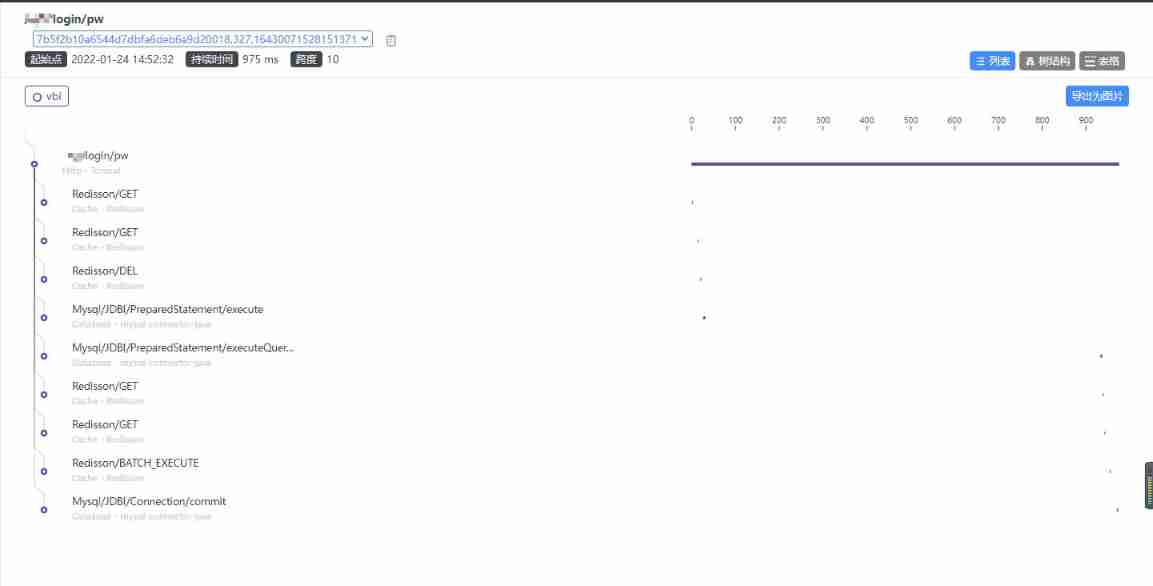
Look at the picture ,Tomcat Of SelfDuration The most. , In other words, time is almost consumed in the service itself .
● Global monitoring
First, check the resource level of the application server :
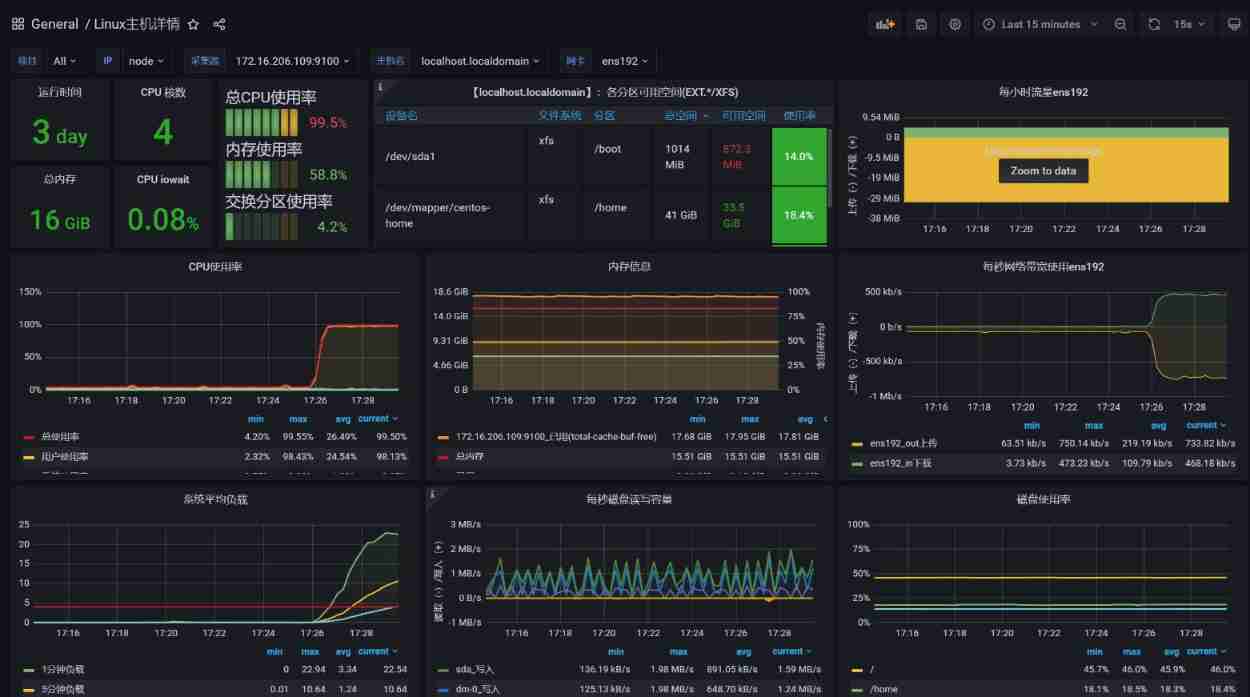
You can see 4C Of CPU Resources have been exhausted .
The container deployed here , Let's take a look at the resource usage of each container :
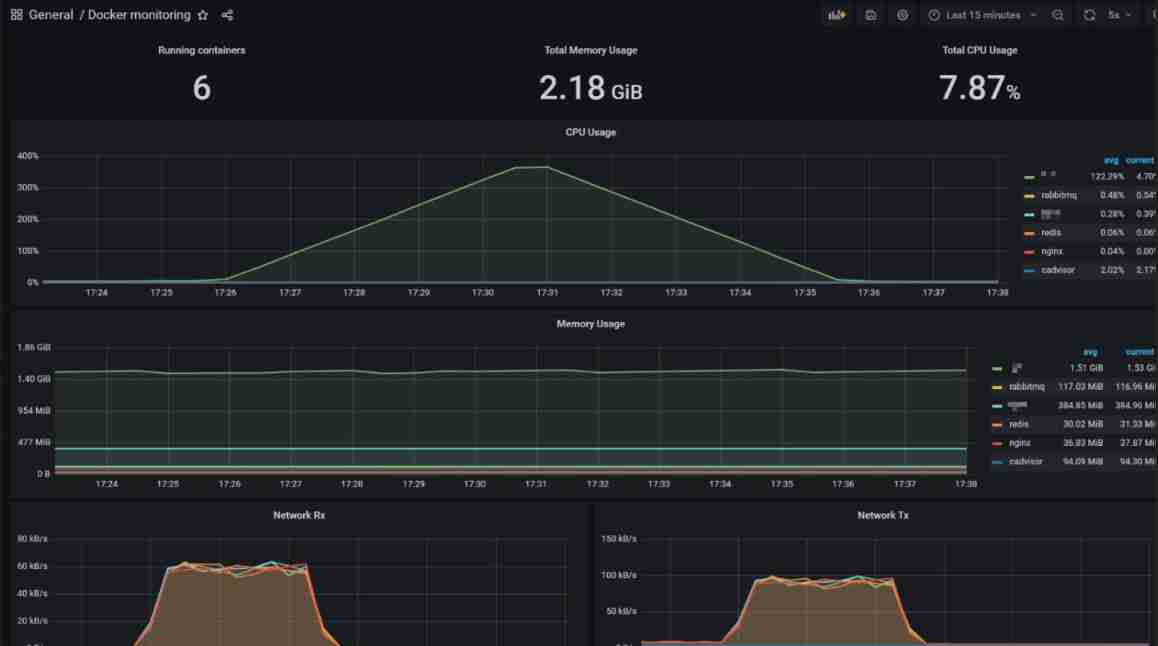
You can see that resources are mainly consumed by the service container .
● Service orientation analysis
First, enter the service container to view the resource consumption :
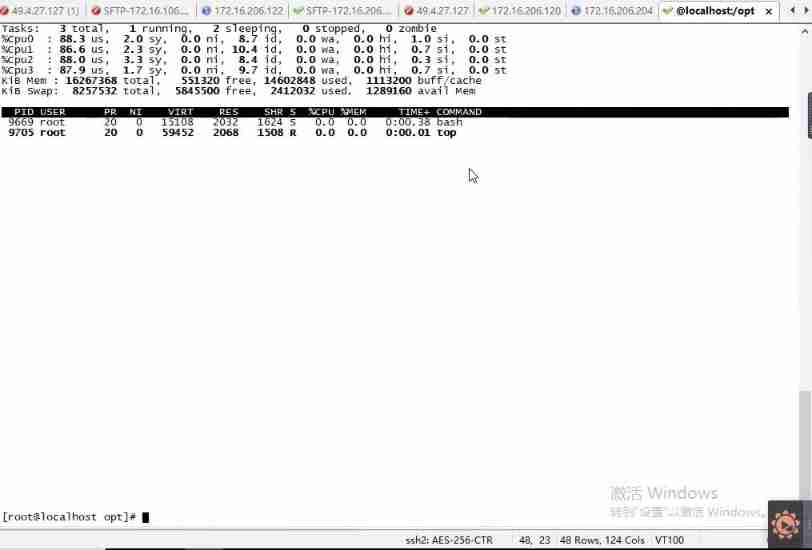
stay SkyWaking You can't see the complete call stack in , Consider connecting directly to the service Java The time consumption of the method in the process . Here we use Arthas Follow up .
Check out the busiest previous N Thread and print stack :
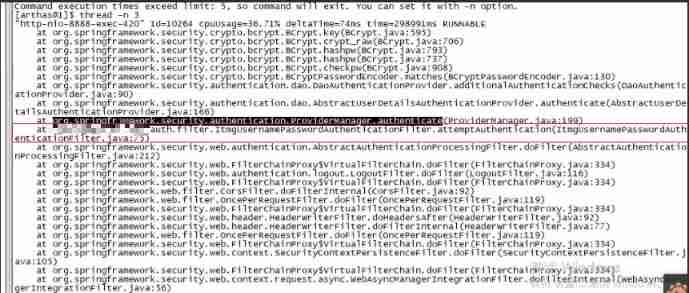
Here is the business code of the program .
therefore trace attemptAuthentication This method .
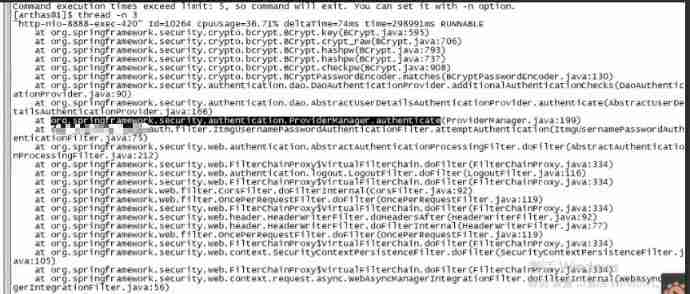
next trace authenticate This method .

Follow it layer by layer , Finally came here :
Since the crypt_raw The method takes a long time , Then decompile the source code to see what this paragraph is .
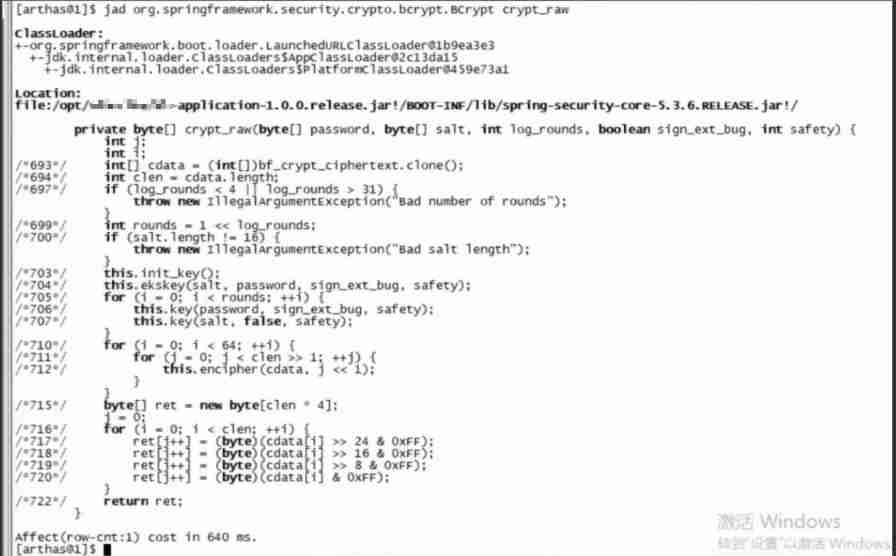
As you can see, here is an encryption algorithm BCrypt, So the conclusion is obvious BCrypt Although the encryption algorithm has high security , But the performance is poor .
● demo verification
Use here SpringBoot Realization MD5 Encryption and BCrypt Encrypted instance .
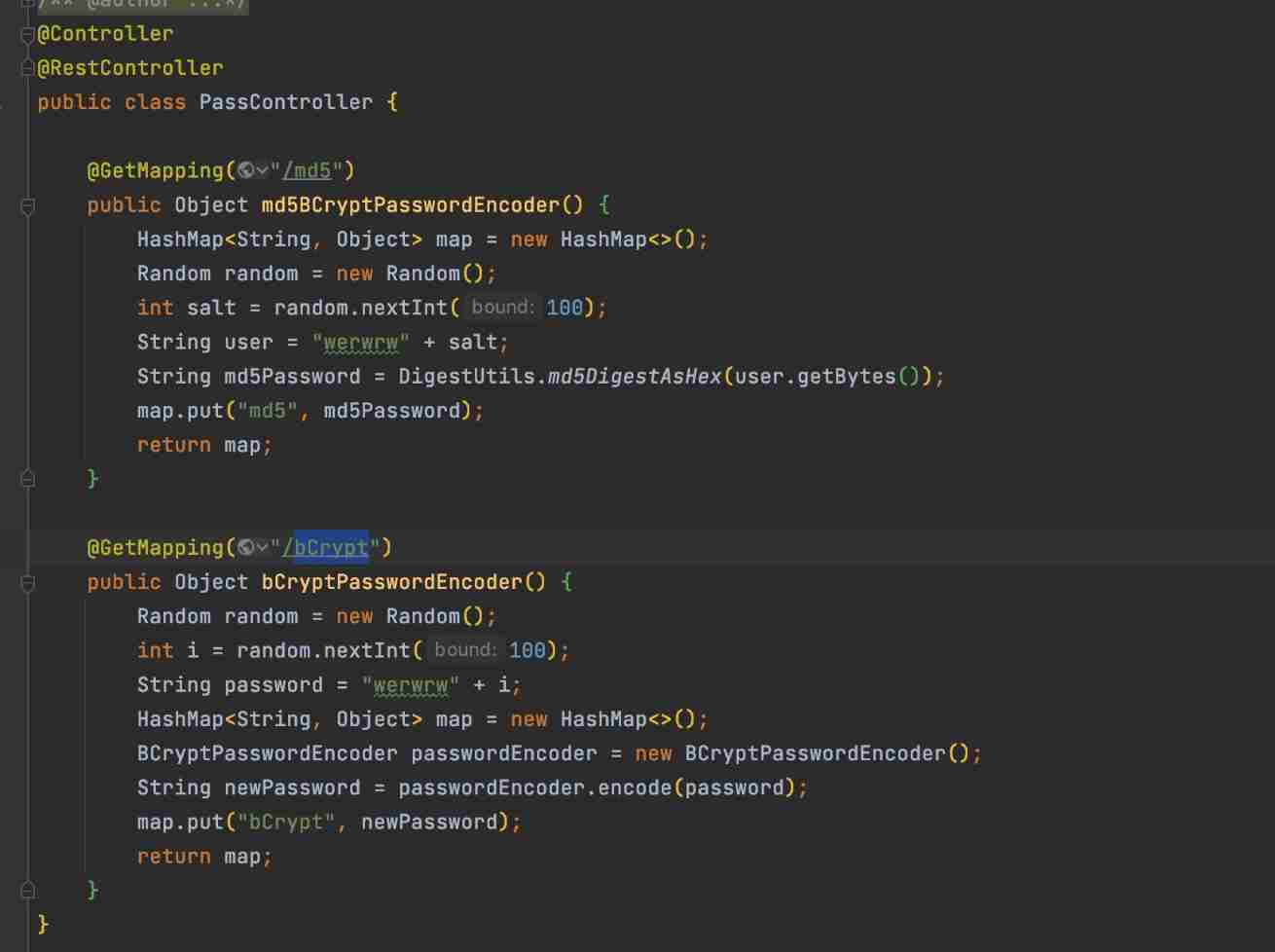
JMeter Concurrent 20 MD5 Encryption result :
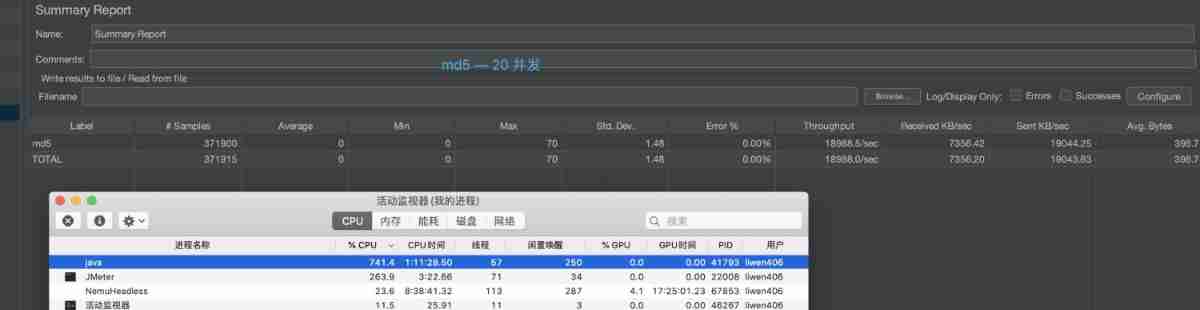
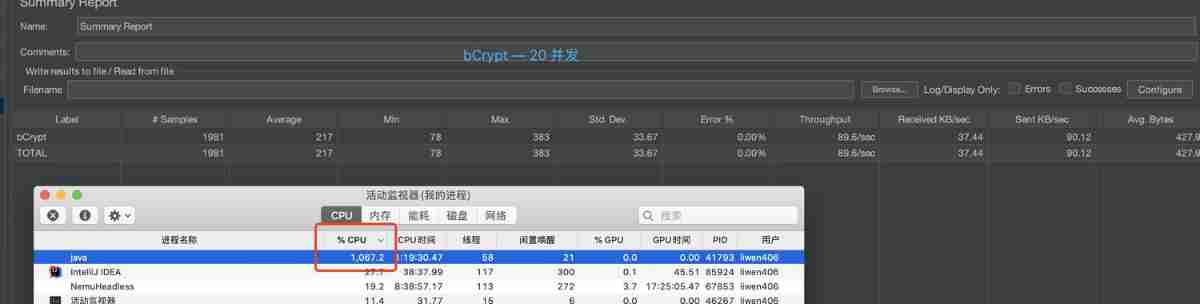
JMeter Concurrent 20 BCrypt Encryption result :
● Suggested optimization direction
Here's an explanation ,Bcrypt When encrypting , every time HASH The values are different , So it's very slow !
What exactly is Bcrypt Algorithm , You can refer to this article :https://www.jianshu.com/p/2b131bfc2f10
So that's the analysis , The optimization scheme is actually clear , That is to use faster encryption , Or remove the encryption algorithm .
边栏推荐
- Redis skip table
- CobaltStrike-4.4-K8修改版安装使用教程
- Derivation of anti Park transform and anti Clarke transform formulas for motor control
- Web security SQL injection vulnerability (1)
- The difference between sizeof and strlen in C language
- Microsoft speech synthesis assistant v1.3 text to speech tool, real speech AI generator
- codeforces每日5題(均1700)-第六天
- CSP numeric sort
- Huawei, H3C, Cisco command comparison, mind map form from the basic, switching, routing three directions [transferred from wechat official account network technology alliance station]
- Game theory matlab
猜你喜欢
Linear programming matlab
解决:AttributeError: ‘str‘ object has no attribute ‘decode‘
![[Chongqing Guangdong education] higher mathematics I reference materials of Southwest Petroleum University](/img/0f/520242492524522c887b6576463566.jpg)
[Chongqing Guangdong education] higher mathematics I reference materials of Southwest Petroleum University
如何做好功能测试

codeforces每日5題(均1700)-第六天
Apt installation ZABBIX
![[network security interview question] - how to penetrate the test file directory through](/img/48/be645442c8ff4cc5417c115963b217.jpg)
[network security interview question] - how to penetrate the test file directory through
适合程序员学习的国外网站推荐
My C language learning record (blue bridge) -- under the pointer
![[kubernetes series] learn the exposed application of kubernetes service security](/img/61/4564230feeb988886fe595e3125ef4.png)
[kubernetes series] learn the exposed application of kubernetes service security
随机推荐
Modeling specifications: naming conventions
【若依(ruoyi)】ztree 自定义图标(iconSkin 属性)
Handwriting database client
[kubernetes series] learn the exposed application of kubernetes service security
【paddle】加载模型权重后预测报错AttributeError: ‘Model‘ object has no attribute ‘_place‘
Pat 1084 broken keyboard (20 points) string find
XSS challenges bypass the protection strategy for XSS injection
[concept] Web basic concept cognition
Elimination games
Selenium share
Microservice registration and discovery
Who is the winner of PTA
Custom attribute access__ getattribute__/ Settings__ setattr__/ Delete__ delattr__ method
Résumé des méthodes de reconnaissance des caractères ocr
1003 emergency (25 points), "DIJ deformation"
4. File modification
Software design principles
Redis skip table
深入探究指针及指针类型
如何做好功能测试
