当前位置:网站首页>[principle and technology of network attack and Defense] Chapter 1: Introduction
[principle and technology of network attack and Defense] Chapter 1: Introduction
2022-07-07 18:01:00 【Godams】
1.1 Overview of Cyberspace Security
“ cyberspace ” Of 4 elements : facilities ( Internet 、 Communication network 、 Computer system 、 Automatic control system 、 Digital devices )、 user ( people )、 operation ( application 、 service ) And data .
Cyberspace Security mainly includes 4 Two levels of security :
- Equipment layer security
- System layer security
- Data layer security
- Application layer security
The basic concept of network attack and defense :
Attack :⾮ French envoy ⽤ Or get ⽹ Information in the network or ⽹ Normal circulation of collaterals ⾏ Of ⾏ by 、 technology .
prevent : Protect your computer ⽹ Various techniques of network .
⽹ Collateral attack and defense are essentially both offensive and defensive ⽅ Around right ⽹ Cognition of network vulnerability ⽽ Into the ⾏ The game of .
⽹ Network attack technology is both ⽹ The motivation for the development of collateral Defense Technology , It's also ⽹ The defense object of Network Defense Technology .
APT Advanced Sustainable attack
Advanced Persistent Threat.
For specific objects ,⻓ period 、 Planned 、 organized ⽹ Collateral attack ⾏ by : Latency 、 Continuity 、 complexity
⽹ Network space (Cyberspace)
Information Age ⼈ We depend on ⽣ Stored information environment , Is a collection of all information systems
⽹ Network space security involves ⽹ Electromagnetic equipment in network space 、 electric ⼦ The information system 、 shipment ⾏ Data and systems should ⽤ Security problems in . It is necessary to prevent ⽌、 Protect “ Information and communication technology systems ” And the data it carries are damaged. We should also deal with the political security caused by these ICT systems 、 Economic security 、⽂ Chemical safety 、 Social security and national defense security .
⽹ Main research on network space security ⽹ Security threats and protection in Cyberspace .
Including infrastructure 、 Security and credibility of information system 、 And the confidentiality of relevant information 、 integrity 、 can ⽤ sex 、 Authenticity and controllability
1.2 Network security protection
1.2.1 Network security attributes
- confidentiality
- integrity
- Usability : To guarantee legality ⽤ The legitimacy of information ⽤. Resources can only be provided by legitimate parties ⼈ send ⽤.
- Non repudiation or non repudiation
1.2.2 Cyber security threats
- Environmental and disaster factors :⾃ However, disasters such as ⽕ disaster ⽔ Disaster, lightning, etc. may damage data , You need to be prepared in advance .
- Human factors :⼈ Negligence or ⿊ Guest attack .
- The system itself : Hardware system failure 、 Software failure or security defect 、⽹ Network and communication protocol defects
1.2.3 Network security protection system
- Bucket principle : Improve the lowest point of safety of the whole system
- The principle of integrity
- Principle of balance
- The principle of hierarchy
- The principle of consistency
- Principle of operability
- The principle of combining technology and management
- Plan as a whole 、 Step by step implementation principle
- Dynamic development principle
1.2.4 The development of network security protection technology
The development of network security protection technology has mainly experienced three stages :
- First generation security technology : For the purpose of protection , Clear network boundaries , Access control 、 Physical security , Cryptography
- Second generation security technology : For the purpose of security , Take detection technology as the core , Backed by recovery , Integrated protection 、 testing 、 Response and recovery technologies fall into four categories . prevent ⽕ wall Firewall、⼊ Intrusion detection system IDS、 Virtual specialty ⽤⽹ VPN、 Public key infrastructure PKI
- Third generation security technology : For the purpose of persistence , That is, the system is under attack 、 In case of faults and accidents , Still have the ability to continue to perform all or key missions for a certain period of time . Its core technology is intrusion tolerance technology , Real time performance 、 function 、 Safety adjustment 、 Real time condition perception and response .
Network security challenges :
- The computing power of general computing devices is getting stronger
- The challenges of the increasingly complex and diverse computing environment
- The development of information technology itself brings problems
- The complexity and dynamics of network and system attacks are still difficult to grasp
To meet these challenges , The development of network security protection technology will be credible 、 Networking 、 The direction of integration and visualization .
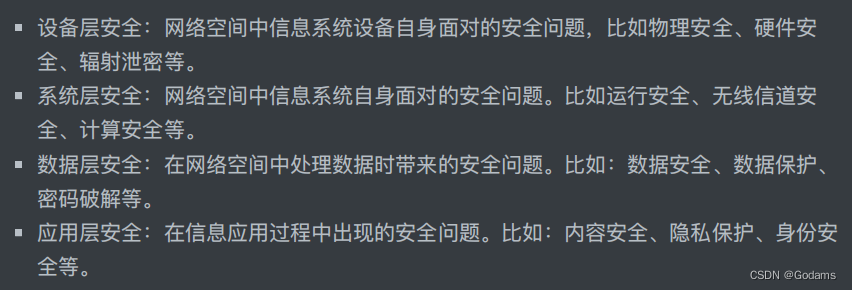
1.2.5 Four levels of security
- Equipment layer security :⽹ Information system equipment in network space ⾃ body ⾯ Right, the safety problem ,⽐ Such as physical security 、 Hardware security 、 Radiation leak, etc .
- System layer security :⽹ Information system in network space ⾃ body ⾯ Right, the safety problem .⽐ Ruyun ⾏ Security 、⽆ Line channel safety 、 Computing security, etc .
- Data layer security : stay ⽹ Security problems when processing data in network space .⽐ Such as : Data security 、 Data protection 、 Password cracking, etc .
- Should be ⽤ Layer security : Information should ⽤ Safety problems in the process .⽐ Such as : Content security 、 Privacy protection 、 Identity security, etc .
1.3 Network attack technology
1.3.1 Several features of Internet that are exploited by attackers
- Packet switching
- all ⽤ Users share resources , To give ⼀ individual ⽤ Customers' services will be affected by other ⽤ Household impact
- Attack packets will be forwarded to the victim before they are judged to be malicious .
- Certification and traceability
- Int ⽹ No authentication mechanism , It can lead to IP cheating . An attacker can forge the contents of any area in the packet , Then send the packet to Internet ⽹ in .
- The router does not have data tracking function . It's hard to verify ⼀ Does the packet originate from its claimed address . Attackers can get through IP Cheat and hide the source .
- Best effort service strategy
- best-effort As long as the service strategy is the data handed over to the network ,⽆ It is normal ⽤ The normal traffic sent by the user or the malicious traffic sent by the attacker , The network will deliver as much as possible ⽬ Land .
- hold ⽹ The distribution and fairness of network resources are entrusted to the terminal ⽤ Household ⾃ Legal .
- Anonymity and privacy
- Ordinary ⽤ Household ⽆ I know it's right ⽅ The true identity of , also ⽆ FA refuses information from unknown sources ( Mail, etc. )
- Global ⽹ Dependence on network infrastructure
- The global ⽹ Network infrastructure does not provide reliability 、 Security assurance . This allows attackers to release ⼤ Its attack effect ⼒.
- ⾸ First ,⼀ Some improper protocol design leads to ⼀ Some packets ⽐ Other packets consume more resources. Second , Int ⽹ yes ⼀ individual ⼤ collective . Many unsafe systems will seriously threaten the whole ⽹ Network safety .
1.3.2 IP Protocol and its security flaws
IP The agreement is stateless 、 No authentication protocol , Its own features are easy to be exploited by attackers .
- IP The protocol has no authentication mechanism , Almost all fields can be forged
- Packet fragmentation , Cause attackers to take advantage of , Such as : Bypass firewall check
- Addressing and protocol options , The addressing information and protocol options of packets expose the network topology information
- IP There is no access control and bandwidth control , Without access control, the attacker can view the content of the upper layer protocol , No bandwidth control may lead to packet storm .
1.3.3 The general process of network attack
⽹ Definition of network attack : benefit ⽤ Security defects of network system , For stealing 、 modify 、 Falsify or destroy information and reduce 、 damage ⽹ Collateral function ⽽ Various measures taken and ⾏ dynamic . damage ⽹ Integrity of network information system 、 can ⽤ sex 、 Confidentiality and non repudiation .
⽹ Collateral attack ⼀ It is divided into three stages
- Preparation stage : Determine attack ⽬ Of 、 Prepare to attack ⼯ Tools and collection ⽬ Bid information
Collection and ⽬ Bid related information .⽐ Such as ⽹ Network information ( domain name ,⽹ Network topology 、IP)、 system information ( Operating system version 、 Open ⽹ Contact services )、⽤ User information (⽤ User ID 、 Email account number 、 contact ⽅ Formula, etc ) - implementation phase : hide ⾃⼰ The location of 、 benefit ⽤ Get the account and password to log in to the host with the collected information , benefit ⽤ Loopholes or other ⽅ Can't get control of the host and steal ⽹ Network resources and privileges . Access
- The aftermath stage : Eliminate traces of attack 、 plant ⼊ after ⻔, After exiting the installation ⻔(⽊⻢ etc. ) System ⽇ Clear your mind 、 Should be ⽤ Program ⽇ Clear your mind
边栏推荐
- Chapter 2 build CRM project development environment (database design)
- Mui side navigation anchor positioning JS special effect
- JS pull down the curtain JS special effect display layer
- mui侧边导航锚点定位js特效
- 【深度学习】3分钟入门
- Threshold segmentation based on RGB image and threshold adjustment by sliding
- 【重新理解通信模型】Reactor 模式在 Redis 和 Kafka 中的应用
- Create dialog style windows with popupwindow
- Introduction to OTA technology of Internet of things
- Chapter 3 business function development (safe exit)
猜你喜欢
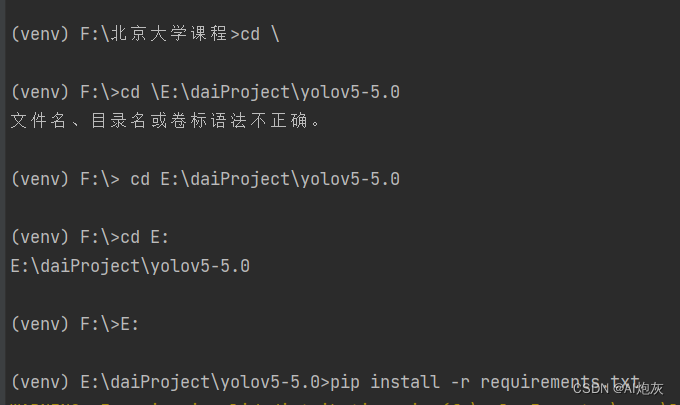
yolo训练过程中批量导入requirments.txt中所需要的包

深度学习-制作自己的数据集

Mobile pixel bird game JS play code
DatePickerDialog and trimepickerdialog
Function and usage of numberpick
Run Yolo v5-5.0 and report an error. If the sppf error cannot be found, solve it

【蓝桥杯集训100题】scratch从小到大排序 蓝桥杯scratch比赛专项预测编程题 集训模拟练习题第17题

Import requirements in batches during Yolo training Txt
Functions and usage of imageswitch
自动化测试:Robot FrameWork框架大家都想知道的实用技巧
随机推荐
js拉下帷幕js特效显示层
仿今日头条APP顶部点击可居中导航
TabHOST 选项卡的功能和用法
【OKR目标管理】案例分析
目标检测1——YOLO数据标注以及xml转为txt文件脚本实战
Chapter 2 building CRM project development environment (building development environment)
serachview的功能和用法
Cartoon | who is the first ide in the universe?
Robot engineering lifelong learning and work plan-2022-
Use seven methods to enhance all the images in a folder
Hutool - 轻量级 DB 操作解决方案
In depth understanding of USB communication protocol
Click on the top of today's headline app to navigate in the middle
calendarview日历视图组件的功能和用法
元宇宙带来的创意性改变
JS pull down the curtain JS special effect display layer
【OKR目标管理】价值分析
手机版像素小鸟游js戏代码
Test for 3 months, successful entry "byte", my interview experience summary
toast会在程序界面上显示一个简单的提示信息