当前位置:网站首页>The art of Engineering (3): do not rely on each other between functions of code robustness
The art of Engineering (3): do not rely on each other between functions of code robustness
2022-07-06 17:38:00 【Wzzzzzzx】
My code has three files , One is responsible for producing SVG character string , One is responsible for storing the string , One responsible for drawing
The code is roughly as follows , And three separate documents
class Producer {
void createSvgString();
...
};
class Storage {
void setSvgStying();
...
};
class Draw {
void drawSvgFigure();
...
};
Now there is a need , I need to judge this SVG Is the pattern a closed pattern .
At first, in order to avoid modifying too much logic , I'm building SVG String time , For closed containers , At the end of the string, a Z ending . Then I just need to draw classes , Judging it can solve the problem .
There is a big problem with this method , It's easy to bury a hole for subsequent developers . The method of determining whether it is a container depends heavily on generating SVG String function , If you ignore this later , When developing other functions for containers , When something goes wrong , It needs to be in another file , Solve in an irrelevant class .
So the practice here should be to create a function , Used to judge whether it is a container , Then pass the result to the drawing class .
When I work again , Pay attention to one function and concentrate on one job , Don't intersperse the work that other functions should do .
边栏推荐
- Take you hand-in-hand to do intensive learning experiments -- knock the level in detail
- Chrome prompts the solution of "your company management" (the startup page is bound to the company's official website and cannot be modified)
- TCP connection is more than communicating with TCP protocol
- 05 personal R & D products and promotion - data synchronization tool
- Solrcloud related commands
- MySQL basic addition, deletion, modification and query of SQL statements
- 04个人研发的产品及推广-数据推送工具
- Xin'an Second Edition; Chapter 11 learning notes on the principle and application of network physical isolation technology
- Integrated development management platform
- 基于Infragistics.Document.Excel导出表格的类
猜你喜欢
Huawei certified cloud computing hica
案例:检查空字段【注解+反射+自定义异常】
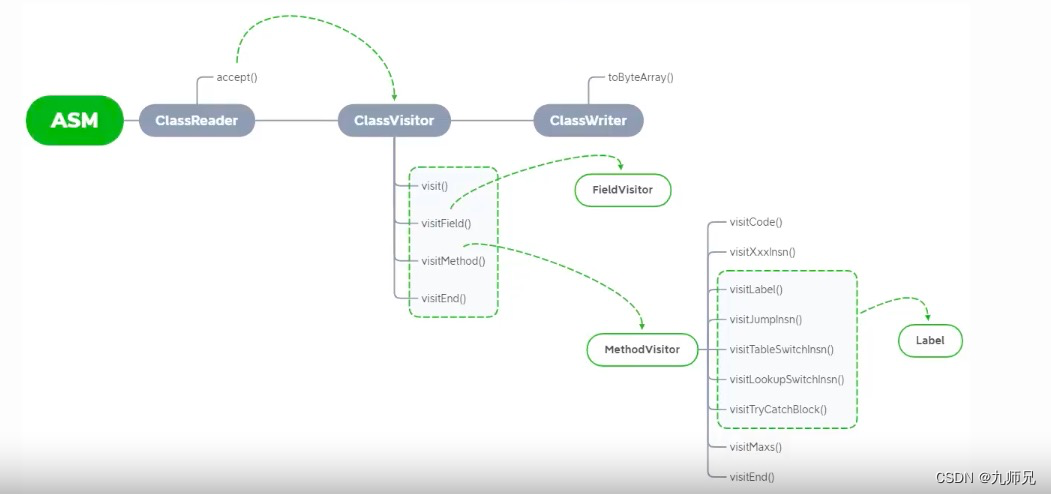
【ASM】字节码操作 ClassWriter 类介绍与使用
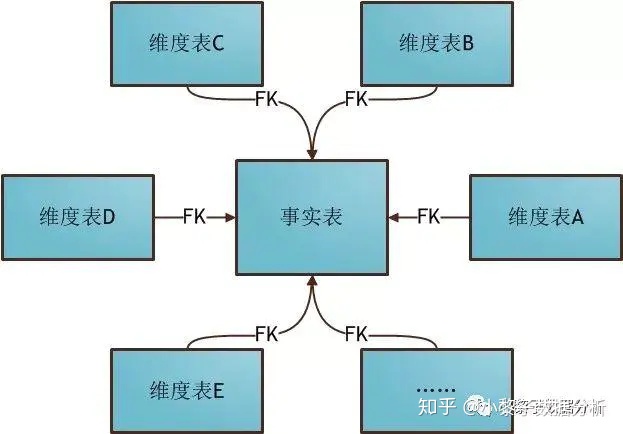
Models used in data warehouse modeling and layered introduction

【MySQL入门】第四话 · 和kiko一起探索MySQL中的运算符
Application service configurator (regular, database backup, file backup, remote backup)

The most complete tcpdump and Wireshark packet capturing practice in the whole network
C# WinForm中DataGridView单元格显示图片
![[getting started with MySQL] fourth, explore operators in MySQL with Kiko](/img/11/66b4908ed8f253d599942f35bde96a.png)
[getting started with MySQL] fourth, explore operators in MySQL with Kiko
Flink analysis (I): basic concept analysis
随机推荐
Application service configurator (regular, database backup, file backup, remote backup)
Akamai浅谈风控原理与解决方案
Pyspark operator processing spatial data full parsing (4): let's talk about spatial operations first
自动答题 之 Selenium测试直接运行在浏览器中,就像真正的用户在操作一样。
vscode
JVM garbage collector part 2
How uipath determines that an object is null
Re signal writeup
Serial serialold parnew of JVM garbage collector
Start job: operation returned an invalid status code 'badrequst' or 'forbidden‘
轻量级计划服务工具研发与实践
分布式(一致性协议)之领导人选举( DotNext.Net.Cluster 实现Raft 选举 )
Automatic operation and maintenance sharp weapon ansible Playbook
CTF逆向入门题——掷骰子
学 SQL 必须了解的 10 个高级概念
Precipitated database operation class - version C (SQL Server)
JVM 垃圾回收器之Serial SerialOld ParNew
Xin'an Second Edition: Chapter 24 industrial control safety demand analysis and safety protection engineering learning notes
Solrcloud related commands
Case: check the empty field [annotation + reflection + custom exception]