当前位置:网站首页>Test de vulnérabilité de téléchargement de fichiers basé sur dvwa
Test de vulnérabilité de téléchargement de fichiers basé sur dvwa
2022-07-06 01:07:00 【Wishlifejump】
Table des matières
DVWA
Low
DVWA SecurityDe“low”Les niveaux peuvent être téléchargés directement“Un mot.”Trojan.
1.1 Écrivez le test Trojan
<?php
phpinfo();
?>1.2 Téléchargement direct sans filtre de suffixe
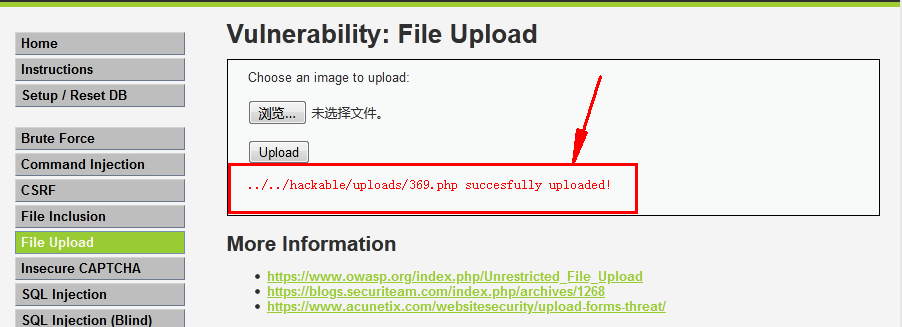
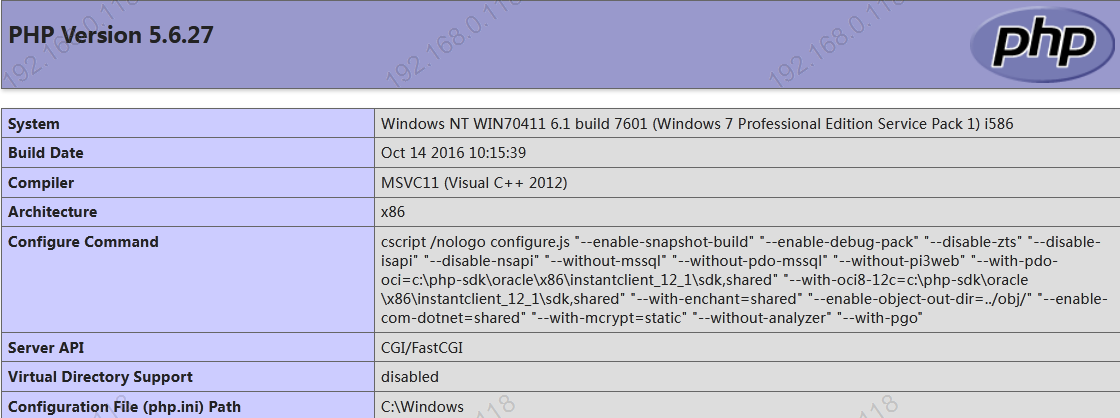
1.3Echo upload path,Accès direct
http://localhost/dvwa/hackable/uploads/info.php
Medium
MediumNiveau différent deLowNiveau,MediumLes limites de téléchargement sont imposées à l'avant,En contournant le mécanisme de détection,Capture de paquets modifier le nom du suffixe pour obtenir l'effet de téléchargement.
2.1 Télécharger des fichiers légaux,Ouvrez l'agent maintenant
2.2 Après avoir attrapé le paquet,send to repeater
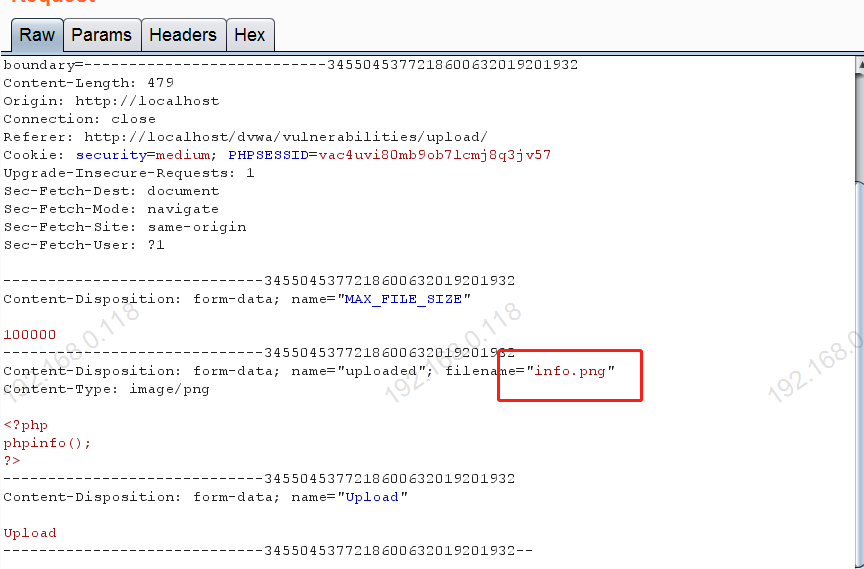
info.png Lire comme suit:info.php
Le Code de réponse est200 Manuel téléchargé avec succès .
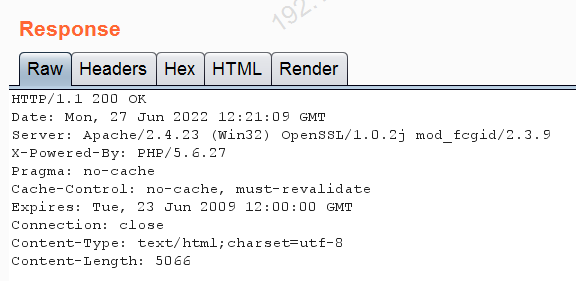
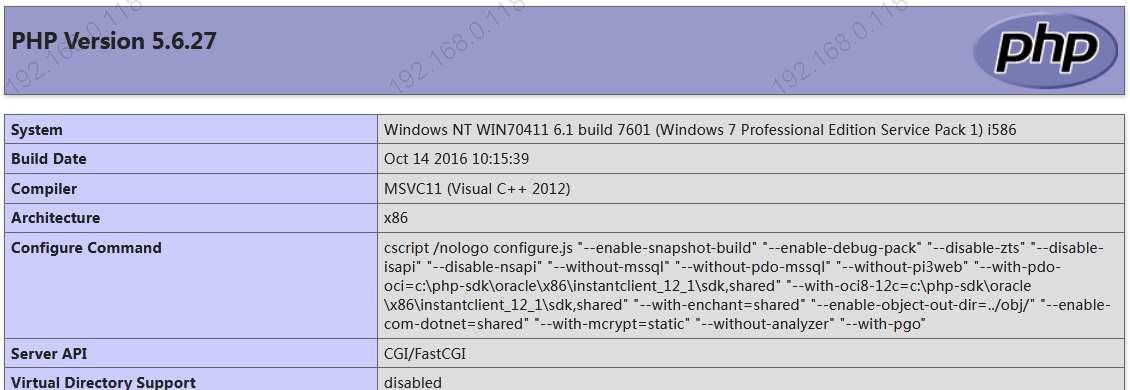
2.3 Mise en œuvrephpScript
https://localhost/dvwa/hackable/uploads/info.php
边栏推荐
- Live broadcast system code, custom soft keyboard style: three kinds of switching: letters, numbers and punctuation
- Five challenges of ads-npu chip architecture design
- Live video source code, realize local storage of search history
- Spark AQE
- [groovy] compile time meta programming (AST syntax tree conversion with annotations | define annotations and use groovyasttransformationclass to indicate ast conversion interface | ast conversion inte
- Construction plan of Zhuhai food physical and chemical testing laboratory
- Redis' cache penetration, cache breakdown, cache avalanche
- synchronized 和 ReentrantLock
- 面试必刷算法TOP101之回溯篇 TOP34
- JVM_ 15_ Concepts related to garbage collection
猜你喜欢
Building core knowledge points
Recoverable fuse characteristic test
Study diary: February 13, 2022
VSphere implements virtual machine migration
Finding the nearest common ancestor of binary search tree by recursion
Free chat robot API

Folding and sinking sand -- weekly record of ETF
Installation and use of esxi
看抖音直播Beyond演唱会有感
MYSQL GROUP_ The concat function realizes the content merging of the same ID
随机推荐
curlpost-php
KDD 2022 | EEG AI helps diagnose epilepsy
Promise
How spark gets columns in dataframe --column, $, column, apply
有谁知道 达梦数据库表的列的数据类型 精度怎么修改呀
The value of applet containers
Mobilenet series (5): use pytorch to build mobilenetv3 and learn and train based on migration
GNSS terminology
Obstacle detection
IP storage and query in MySQL
VSphere implements virtual machine migration
Comment faire votre propre robot
Idea remotely submits spark tasks to the yarn cluster
The detailed page returns to the list and retains the original position of the scroll bar
FFT 学习笔记(自认为详细)
程序员搞开源,读什么书最合适?
Kotlin core programming - algebraic data types and pattern matching (3)
curlpost-php
After Luke zettlemoyer, head of meta AI Seattle research | trillion parameters, will the large model continue to grow?
VMware Tools安装报错:无法自动安装VSock驱动程序