当前位置:网站首页>SQL statement
SQL statement
2022-07-06 01:58:00 【Crazy Stuka】
List of articles
SQL sentence
SQL Statement is used to maintain the management database , Including data query , Data update , Access control , Object management and other functions
SQL Language classification :
DDL: Data definition language , Used to create database objects , Ruku 、 surface 、 Index, etc.
DML: Data manipulation language , It is used to manage the data in the table
DQL: Data query language , Used to find eligible data records from the data table
DCL: Data control language , Used to set or change database user or role permissions
Application SQL Statement instance
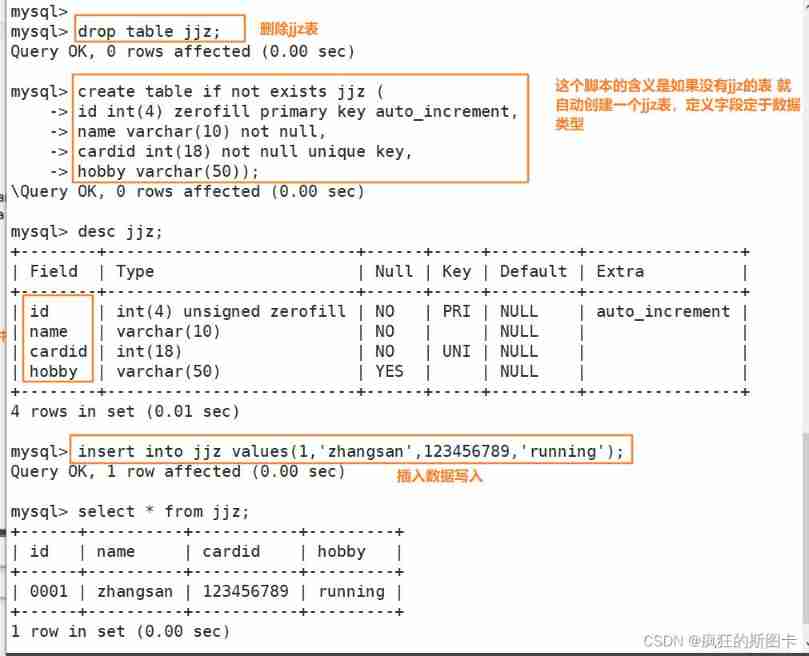
mysql> create table if not exists jjz (
-> id int(4) zerofill primary key auto_increment,
-> name varchar(10) not null,
-> cardid int(18) not null unique key,
-> hobby varchar(50));
#if not exists: Indicates whether the table to be created exists , If it doesn't exist, continue to create
#int(4) zerofill: Indicates if the value is less than 4 digit , Then use “0” fill
#auto_increment: Indicates that the secondary field is a self increasing field , That is, each record is automatically incremented 1, The default from the 1 Began to increase , Self growing field data cannot be duplicated , Self growing fields must be primary keys , If the added record data does not specify a secondary field and the addition fails, it will also be automatically incremented once
#unique key: Represents the secondary field unique key constraint , The data in this field cannot be repeated , There can only be one primary key in a table , But there can be multiple unique keys in a table
#not null: Indicates that this field is not allowed to be NULL
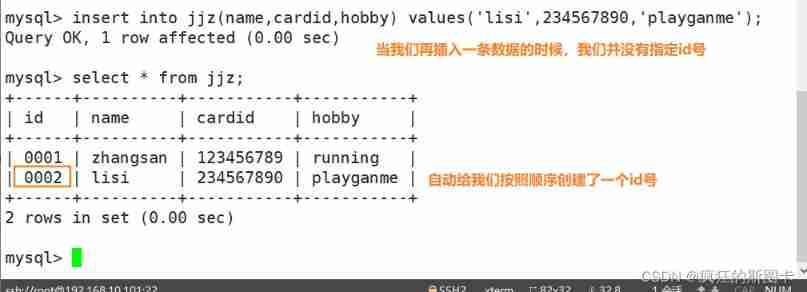
Data table advanced operations
1. Clone table , Generate the data records of the data table into a new table
The first method
mysql> create table New table like Old table ;
notes : Just clone the structure of the table
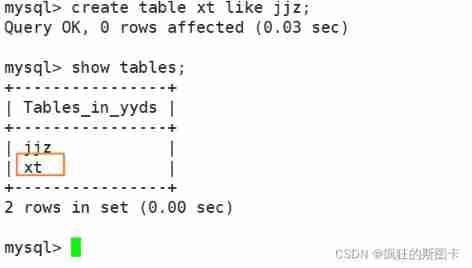
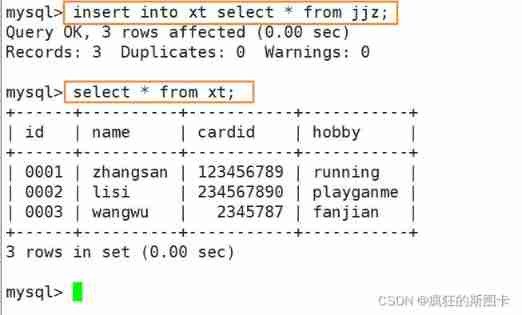
Clone old table data to new table
mysql> insert into New table select * from Old table ;
The second method
Directly clone table structure and table data
mysql> create table New table (select * from Old table );
Clear the table , Delete all data in the table
Method 1
mysql> delete from Table name ;
#delete After emptying the table , There are deleted entries in the returned results ;delete Delete the recorded data line by line when working ; If there is a self growing field in the table , Use delete from After deleting all records , The newly added record will change from the original maximum record ID Continue to write the record automatically later .
Method 2
mysql> truncate table Table name ;
#truncate After emptying the table , There are deleted record entries in the returned result ;truncate When working, the table structure is rebuilt as it is , So in terms of speed ,truncate than delete Empty the watch, quick ; After using the data in the table ,ID From 1 Start re recording
Create a temporary table
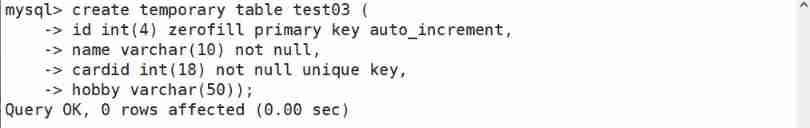
Look at the data in the table
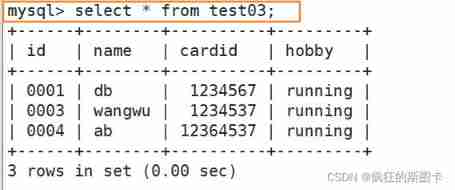
But when looking at the tables in the database when Temporary tables are invisible , And only the current connection is valid , After logging out of the connection, it will be automatically destroyed
Create foreign key constraints , Ensure the integrity and unity of data
Definition of foreign key : If the same attribute field x In Table 1 is the primary key , In Table 2, it is not the primary key , Then the fields x The foreign key called table 2 .
Understanding of primary key table and foreign key table :
(1) Tables with public keywords as primary keys are primary key tables ( Parent table 、 Main table )
(2) Tables with public keywords as foreign keys are foreign key tables ( From the table 、 appearance )
Be careful : The fields of the primary table associated with the foreign key must be set as the primary key . It is required that the slave table cannot be a temporary table , The fields of the master-slave table have the same data type 、 Character length and constraints .
First, create two tables
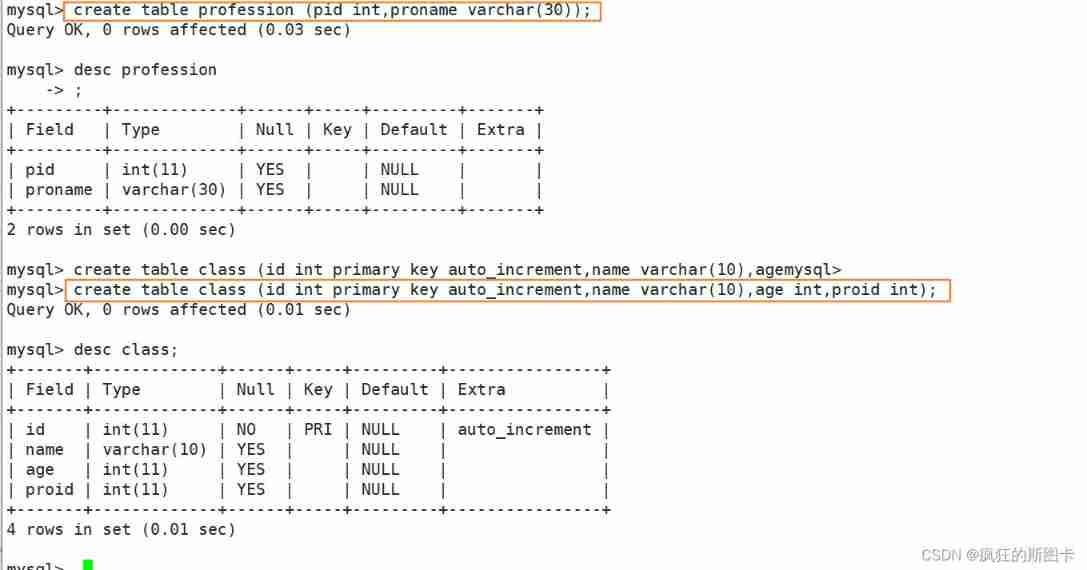
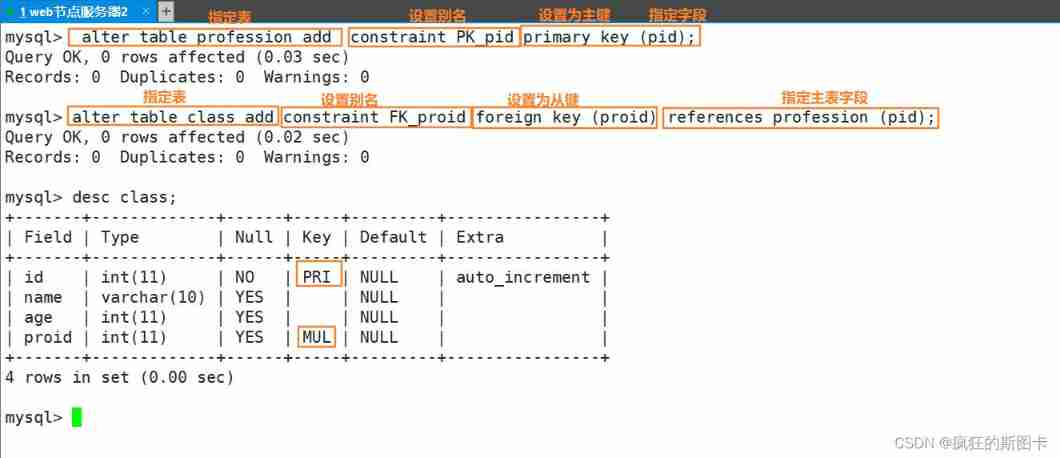
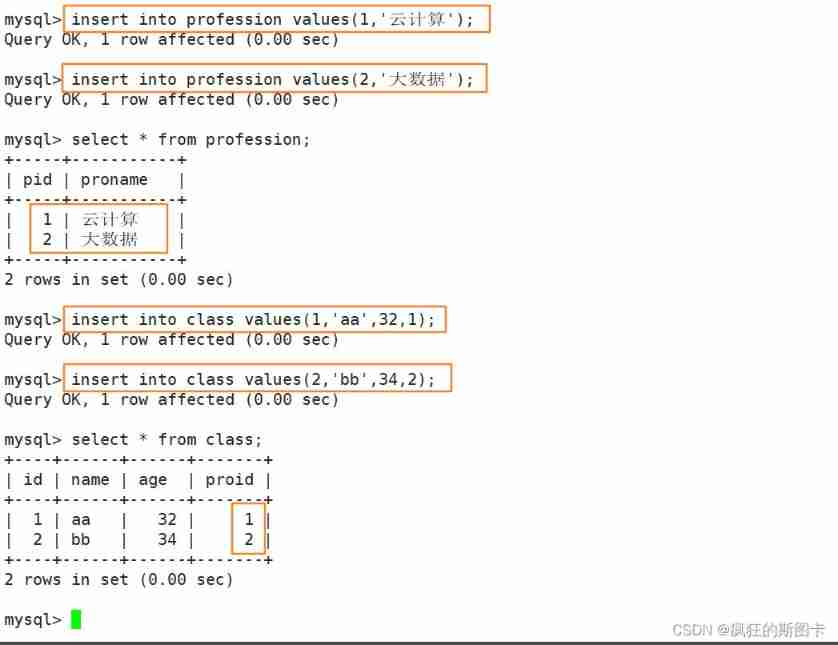
Two points need to be noted here , When inserting data , First add from the main table and then add in the foreign key table , First the main table and then the appearance
When deleting data , Delete the appearance record first and then the main table record
View foreign key constraints and delete foreign key constraints
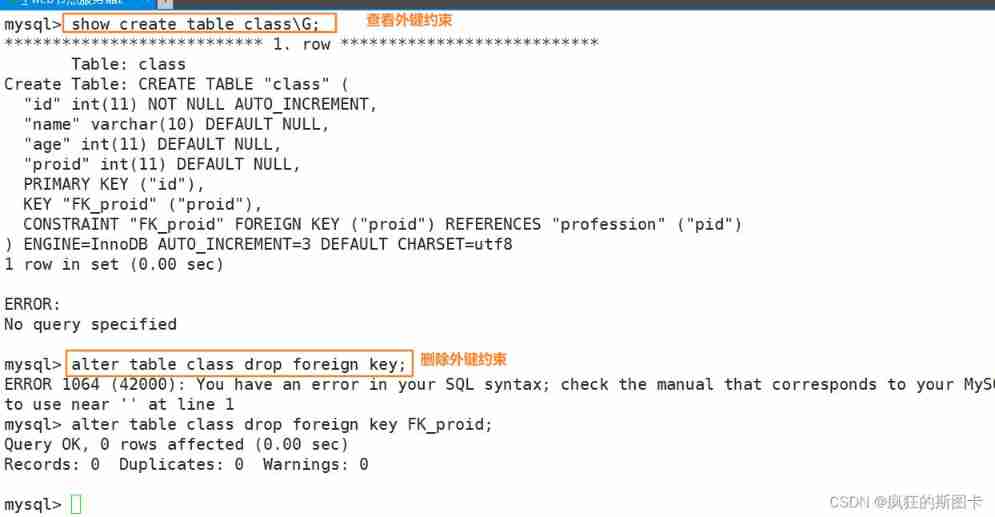
MySQL in 6 A common constraint :
Primary key constraint (primary key)
Foreign key constraints ( foreign key )
Non empty constraint (not null)
Uniqueness constraint (unique [key l index] )
Default constraint ( default)
Self increasing constraint (auto_ increment)
Mysql DCL sentence
Create user password encryption
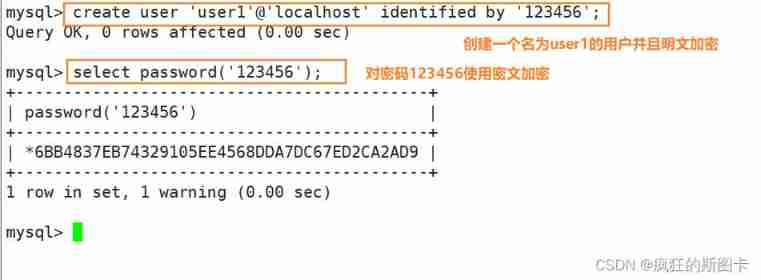
Database account user information storage location
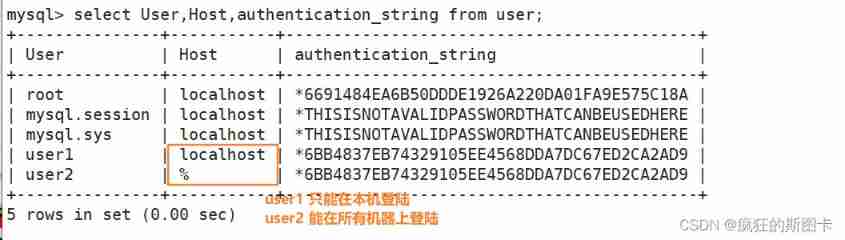
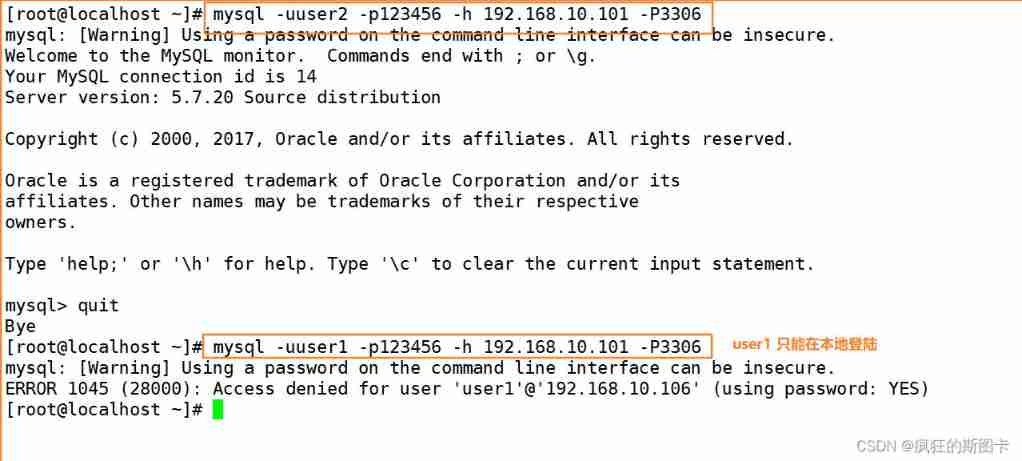
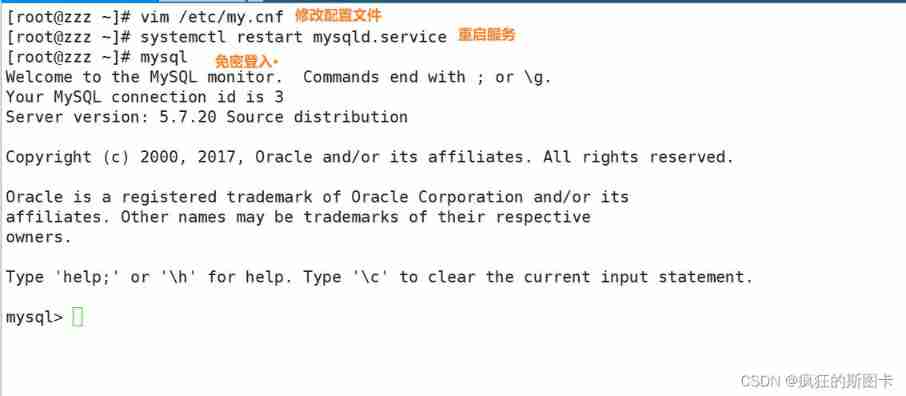
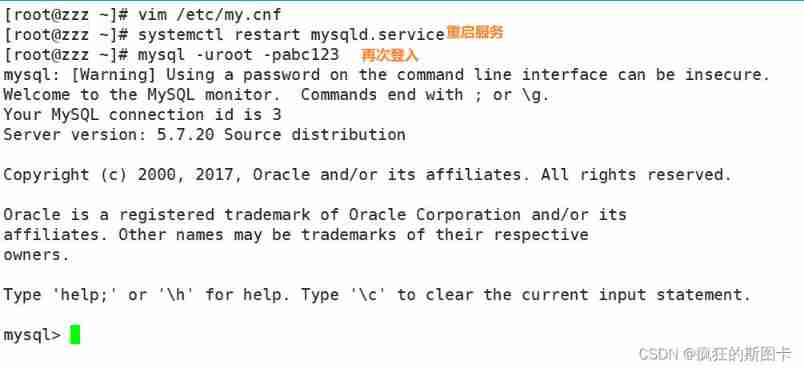
mysql Remote login
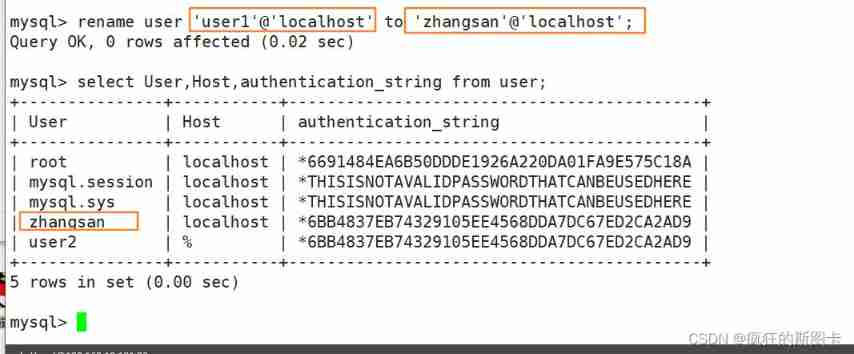
rename user
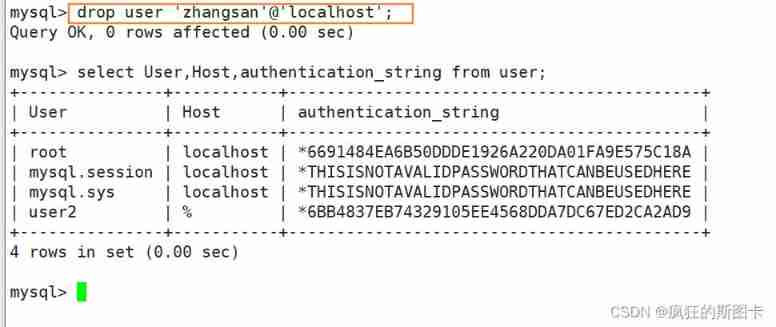
Delete user name
Change the current user password
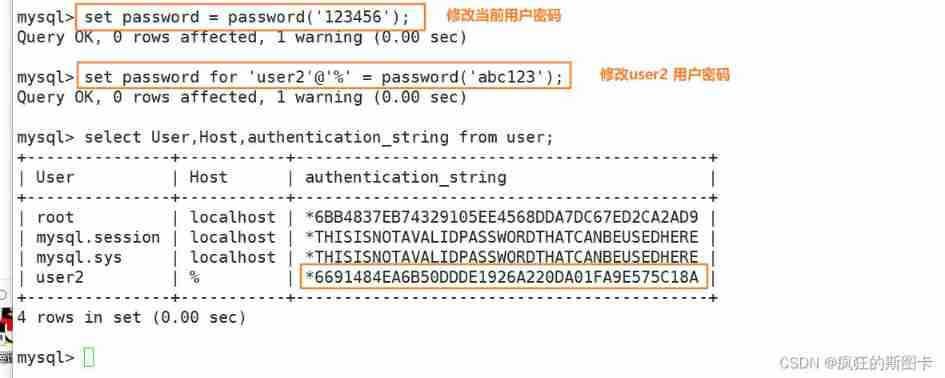
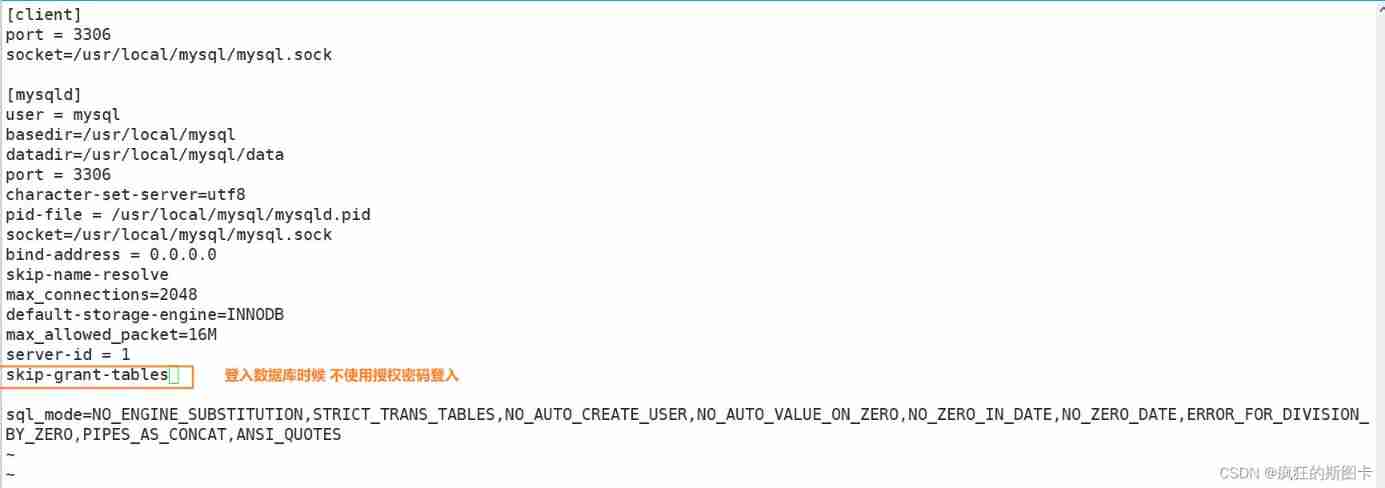
Forget the password , How to deal with it
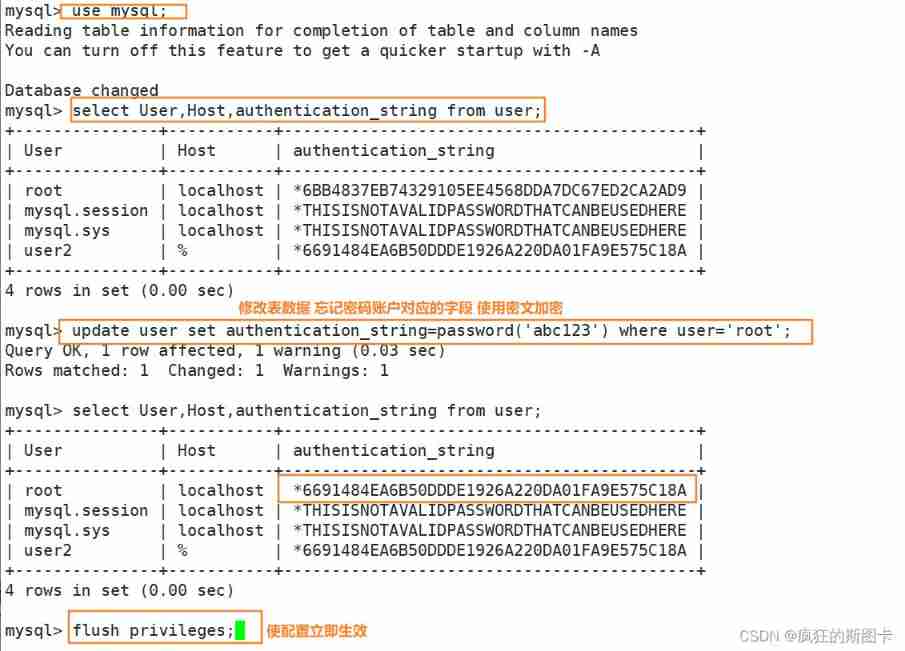
Exit database
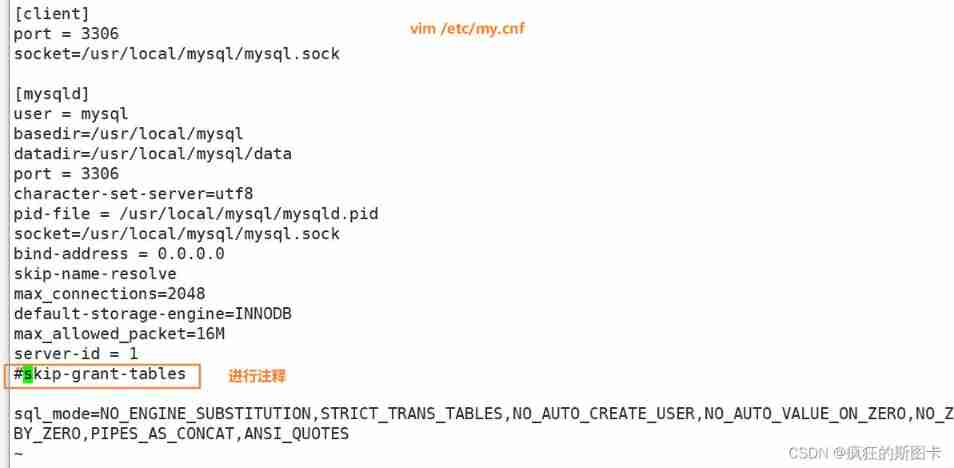
Database user authorization
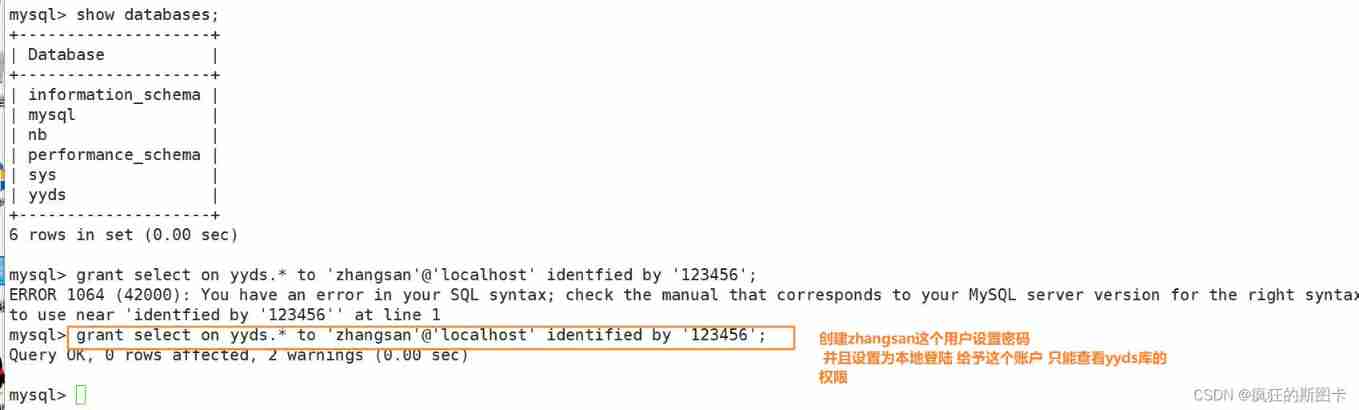
1. Grant authority
GRANT sentence : It is specially used to set the access rights of database users . When the specified user name does not exist ,GRANT Statement will create a new user , When the specified user name exists ,GRANT Statement is used to modify user information .
GRANT Permission list ON Database name . Table name TO ' user name '@' Source address ’[IDENTIFIED BY ' password '];
# Permission list : Used to list various database operations authorized for use , Separated by commas , Such as "select, insert, updatel". Use "al1" Indicates all permissions , You can authorize any operation .
# Database name . Table name : The name of the database and table used to specify the authorization operation , You can use wildcards "*". for example , Use "kac." The object representing the authorization operation is kac All the tables in the database .
' user name @ Source address ': Used to specify the user name and the client address to which access is allowed , Who can connect 、 Where can I connect . The source address can be a domain name 、IP Address , You can also use "%" wildcard , Represents all addresses in an area or network segment , Such as "%. kgc.com”、"192.168.80." etc. .
#IDENTIFIED BY: Used to set the password string used by users when connecting to the database . When creating a new user , If you omit "*IDENTFIED BY" part , Then the user's password will be empty .
Set the local login permission of the account
Open another port
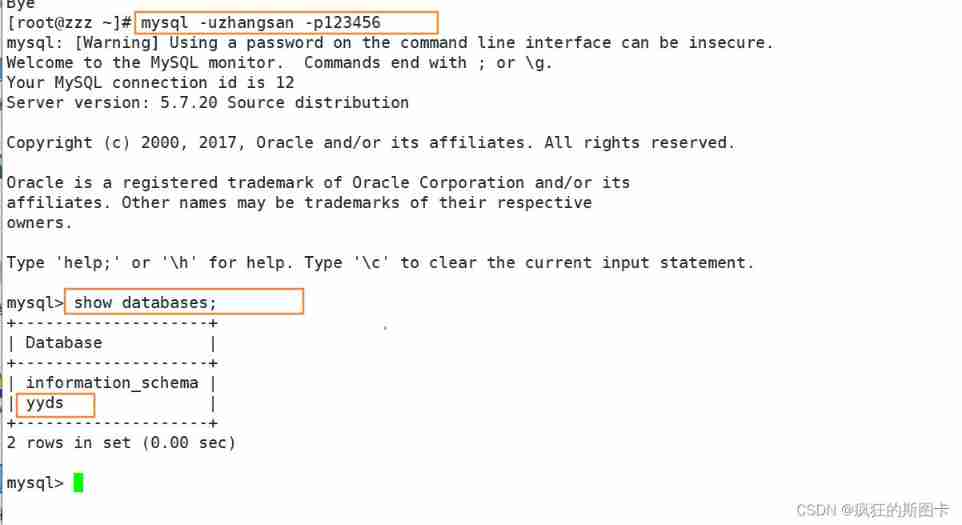
Create an account And set the permission to allow login on all hosts , Have permission to view all tables
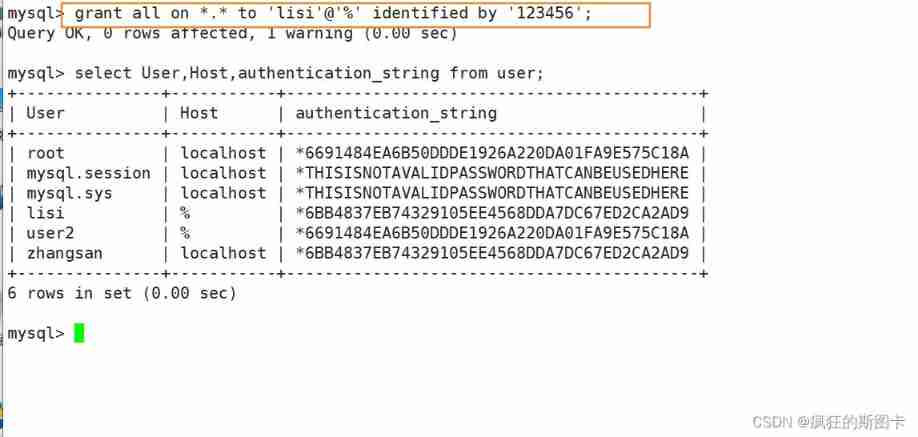
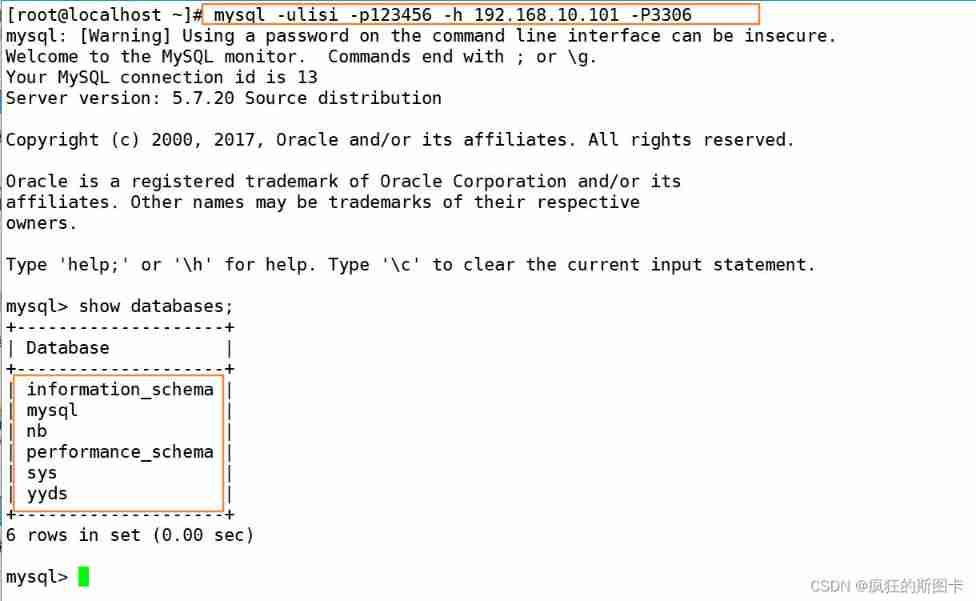
Switch to another host to verify login
View the permission of an account
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-oLN8IxLN-1644586831353)(C:\Users\zhuquanhao\Desktop\ Screenshot command set \linux\MyAQL Database management statement \29.png)]
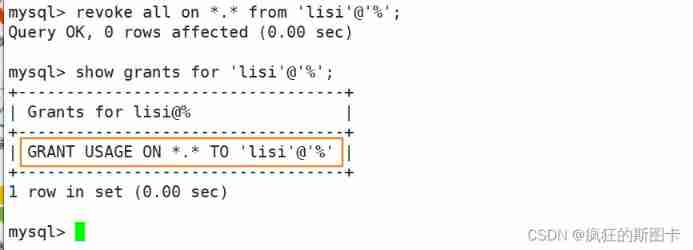
How to revoke the authority of an account
边栏推荐
- PHP error what is an error?
- Initialize MySQL database when docker container starts
- Paddle框架:PaddleNLP概述【飛槳自然語言處理開發庫】
- Basic operations of database and table ----- delete data table
- Leetcode3, implémenter strstr ()
- Social networking website for college students based on computer graduation design PHP
- [Jiudu OJ 09] two points to find student information
- Flowable source code comments (36) process instance migration status job processor, BPMN history cleanup job processor, external worker task completion job processor
- dried food! Accelerating sparse neural network through hardware and software co design
- Redis如何实现多可用区?
猜你喜欢
Leetcode3. Implement strstr()
Blue Bridge Cup embedded_ STM32 learning_ Key_ Explain in detail
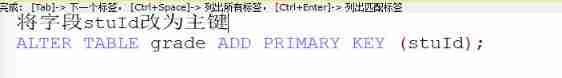
Basic operations of databases and tables ----- primary key constraints
500 lines of code to understand the principle of mecached cache client driver
Executing two identical SQL statements in the same sqlsession will result in different total numbers

Poj2315 football games
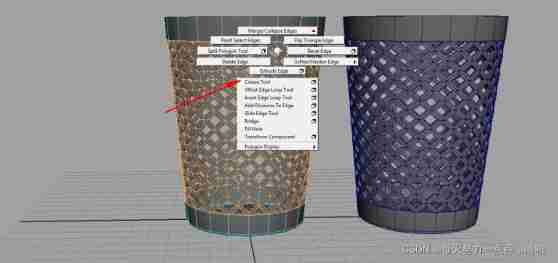
Maya hollowed out modeling
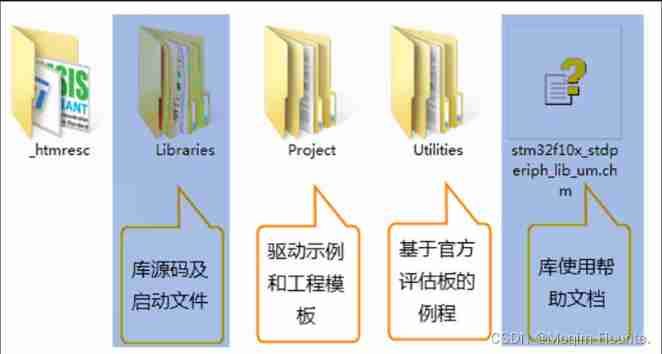
Blue Bridge Cup embedded_ STM32_ New project file_ Explain in detail
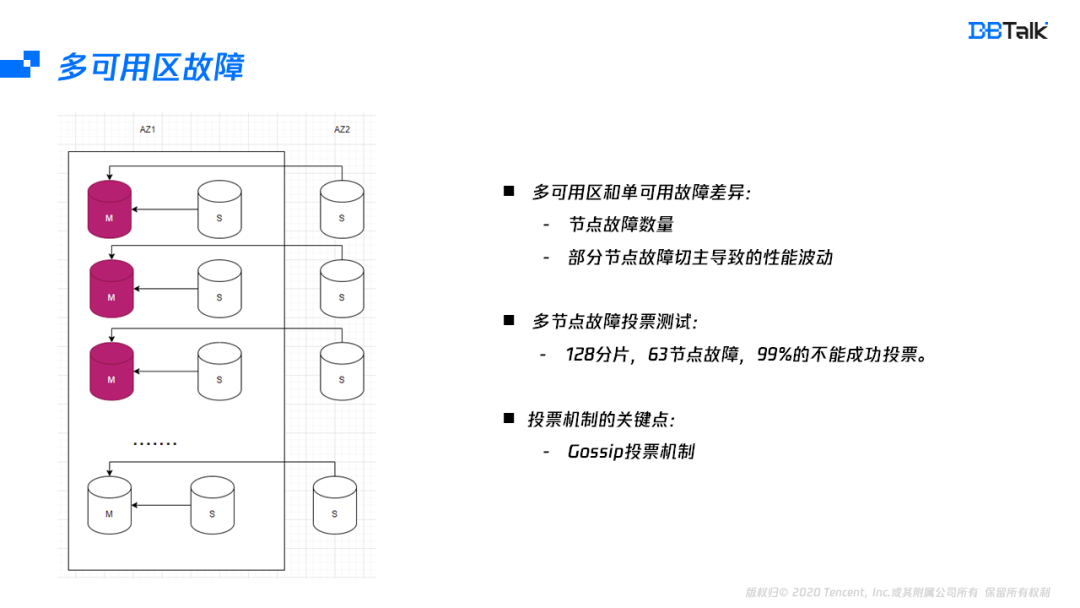
How does redis implement multiple zones?
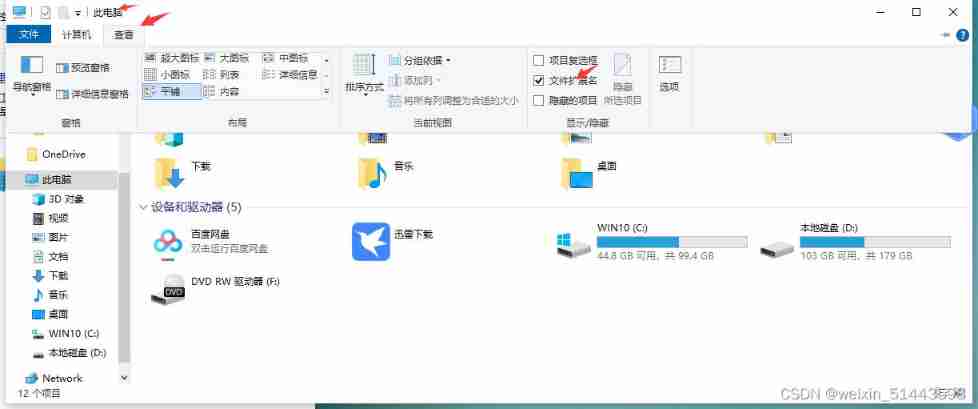
Win10 add file extension
随机推荐
Basic operations of database and table ----- delete data table
[detailed] several ways to quickly realize object mapping
插卡4G工业路由器充电桩智能柜专网视频监控4G转以太网转WiFi有线网速测试 软硬件定制
GBase 8c数据库升级报错
leetcode3、实现 strStr()
Paddle框架:PaddleNLP概述【飛槳自然語言處理開發庫】
FTP server, ssh server (super brief)
Alibaba canal usage details (pit draining version)_ MySQL and ES data synchronization
Virtual machine network, networking settings, interconnection with host computer, network configuration
Basic operations of databases and tables ----- default constraints
[flask] official tutorial -part3: blog blueprint, project installability
01.Go语言介绍
500 lines of code to understand the principle of mecached cache client driver
A basic lintcode MySQL database problem
You are using pip version 21.1.1; however, version 22.0.3 is available. You should consider upgradin
【Flask】响应、session与Message Flashing
【Flask】官方教程(Tutorial)-part1:项目布局、应用程序设置、定义和访问数据库
Computer graduation design PHP enterprise staff training management system
selenium 等待方式
Pangolin Library: subgraph