当前位置:网站首页>Embedding malware into neural networks
Embedding malware into neural networks
2022-07-02 07:52:00 【MezereonXP】
Embed malware into Neural Networks
This introduction is entitled “EvilModel: Hiding Malware Inside of Neural Network Models ” The article .
This article mainly describes an implicit method of spreading malware , By modifying the weight of the neural network to achieve the spread of malware .

Essentially , Is to select some of the models “ redundancy ” The layer , Replace the weights of the neurons , For each weight , Replace its last 3 Bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit bit 3 A bit , And then realize the implicit transmission of malware .
Mentioned here redundancy , Actually, it passed the test , Check the impact on accuracy , Choose those layers that have little impact on the accuracy .

As shown in the figure above , The horizontal axis is the number of replacement neurons , The vertical axis is the accuracy of the modified model .
Here are some observations :
- As the number of modified neurons increases , The more accuracy is affected .
- Neurons closer to the input layer , It is more suitable for embedding malware , Less impact
Because the modification of neural network weight will reduce its original accuracy , So the author also explored the effect of heavy training , As shown in the figure below :
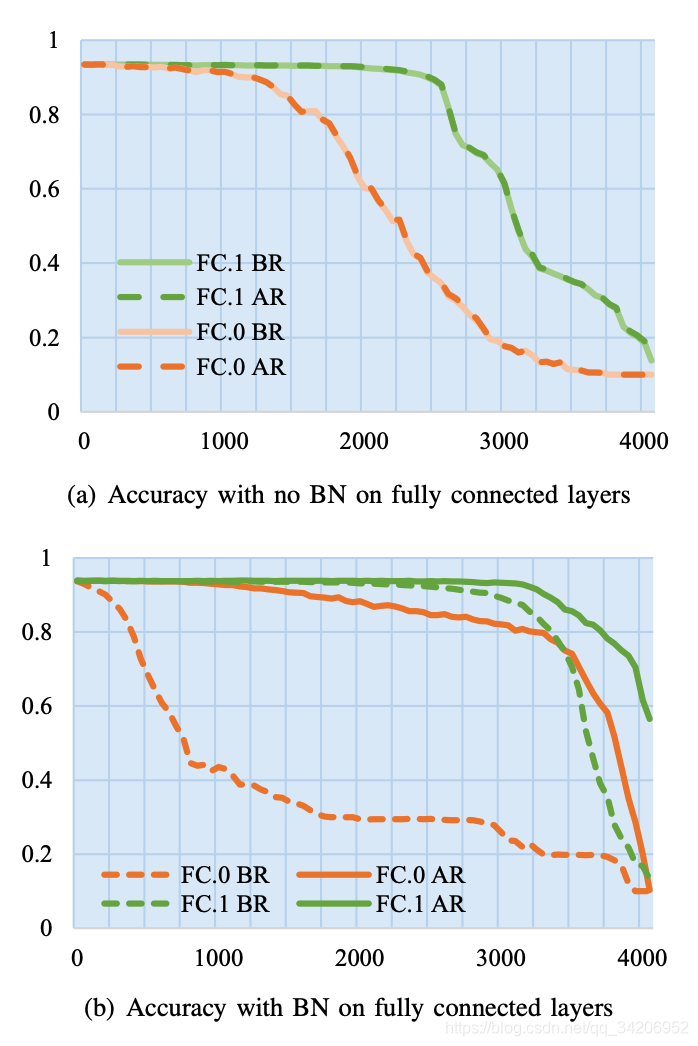
among ,BR Means before retraining (Before),AR It means after heavy training (After)
You can see , Didn't bring BN (BatchNorm) Layer network , Accuracy cannot be restored through retraining , With BN The accuracy of layer can be restored by retraining .
边栏推荐
- Deep learning classification Optimization Practice
- 生成模型与判别模型的区别与理解
- open3d环境错误汇总
- 【DIoU】《Distance-IoU Loss:Faster and Better Learning for Bounding Box Regression》
- 【Paper Reading】
- 将恶意软件嵌入到神经网络中
- 【雙目視覺】雙目矯正
- 基于pytorch的YOLOv5单张图片检测实现
- How to turn on night mode on laptop
- A slide with two tables will help you quickly understand the target detection
猜你喜欢
【Cascade FPD】《Deep Convolutional Network Cascade for Facial Point Detection》

iOD及Detectron2搭建过程问题记录
程序的执行
【Mixup】《Mixup:Beyond Empirical Risk Minimization》
【MnasNet】《MnasNet:Platform-Aware Neural Architecture Search for Mobile》

【TCDCN】《Facial landmark detection by deep multi-task learning》

【AutoAugment】《AutoAugment:Learning Augmentation Policies from Data》
图片数据爬取工具Image-Downloader的安装和使用
【Batch】learning notes

【双目视觉】双目矫正
随机推荐
生成模型与判别模型的区别与理解
用MLP代替掉Self-Attention
[CVPR‘22 Oral2] TAN: Temporal Alignment Networks for Long-term Video
【AutoAugment】《AutoAugment:Learning Augmentation Policies from Data》
程序的内存模型
PHP returns the corresponding key value according to the value in the two-dimensional array
Drawing mechanism of view (3)
图片数据爬取工具Image-Downloader的安装和使用
Common CNN network innovations
【多模态】CLIP模型
iOD及Detectron2搭建过程问题记录
MoCO ——Momentum Contrast for Unsupervised Visual Representation Learning
Record of problems in the construction process of IOD and detectron2
MoCO ——Momentum Contrast for Unsupervised Visual Representation Learning
Faster-ILOD、maskrcnn_ Benchmark installation process and problems encountered
传统目标检测笔记1__ Viola Jones
PPT的技巧
【Paper Reading】
【Mixed Pooling】《Mixed Pooling for Convolutional Neural Networks》
[multimodal] clip model