当前位置:网站首页>The shooting range that web penetration must play - DVWA shooting range 1 (centos8.2+phpstudy installation environment)
The shooting range that web penetration must play - DVWA shooting range 1 (centos8.2+phpstudy installation environment)
2022-08-02 04:02:00 【Learn Safe Tom Cat】
文章目录
前言
学习web渗透dvwaThe shooting range is a must,Although there are not many topics,But it is relatively friendly to beginners,I will take you through this chapter,From the construction of the environment and the analysis of the gameplay of each level.It may not be written clearly,也希望大家谅解.
I use it in my shooting range environmentcentos8.2,Maybe some other shooting ranges will be added later,做一台webPenetration Environment Machine.For convenience, I use it herephpstudy搭建网站.
一 .环境搭建的准备
**phpstudy和dvwa靶场环境**
下载地址:
phpstudy:yum install -y wget && wget -O install.sh https://notdocker.xp.cn/install.sh && sh install.sh
dvwa靶场环境:https://github.com/digininja/DVWA
第一步:安装phpstudy
Since my virtual machine doesn'twget,And the built-in source can't be used,So I also configured a local source installation herewget
mount /dev/cdrom /mnt #挂载光盘
vi /etc/yum.repo.d/centos.repo
以下为内容
[baseOS]
name=baseOS
baseurl=file:///mnt/BaseOS
enabled=1
gpgcheck=0
[AppSteram]
name=AppSteram
baseurl=file:///mnt/AppStream
enabled=1
gpgcheck=0
yum install wget -y #安装wget
The virtual machine can be connected to the external network and execute the following command
yum install -y wget && wget -O install.sh https://notdocker.xp.cn/install.sh && sh install.sh
After the installation is complete we will get a login address、账号和密码
我们使用浏览器进行访问,输入账号、密码,The verification code can log in to the background.
登录成功后,Let's change the password first.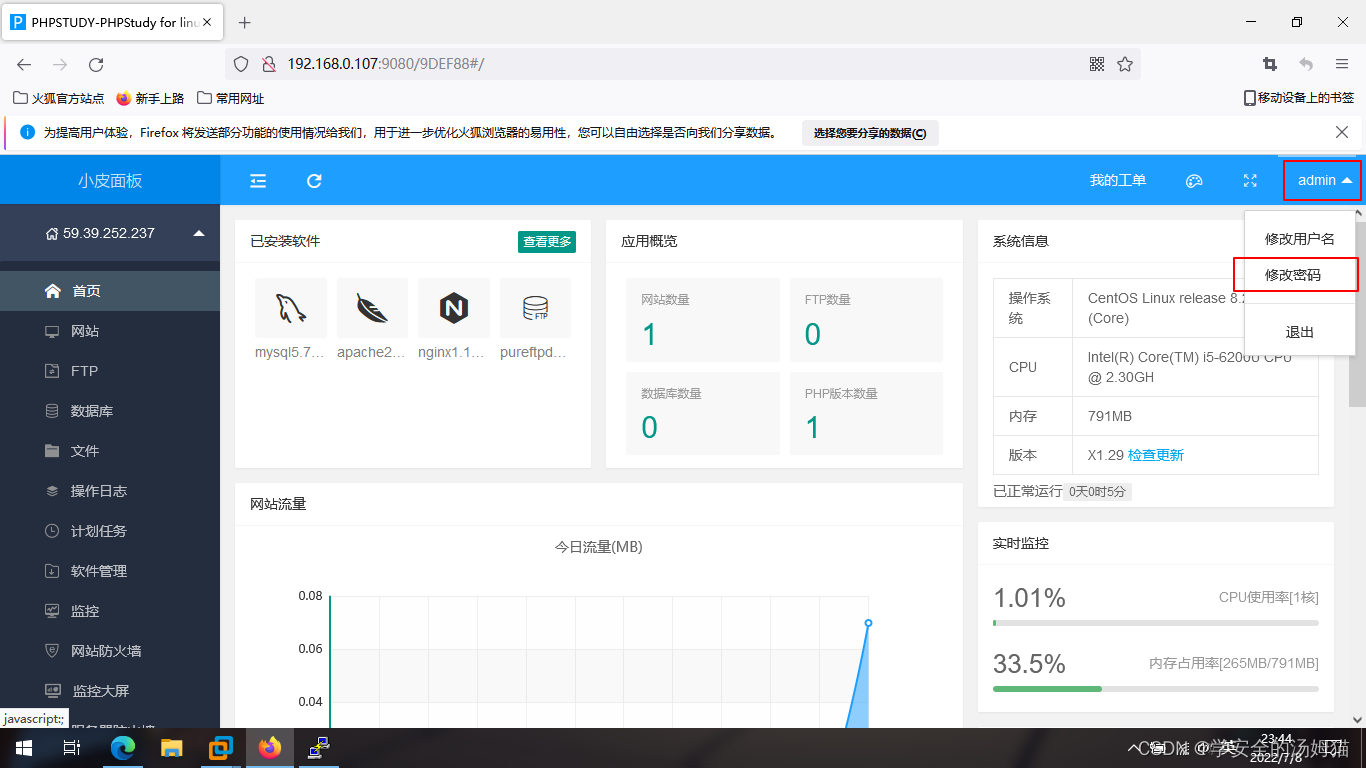
点击右上角的admin(用户名),Then click Change Password
第二步:配置需要的环境
Select Software Management on the left,我这里使用的是mysql7.27和apache2.4.39,还有一个php程序
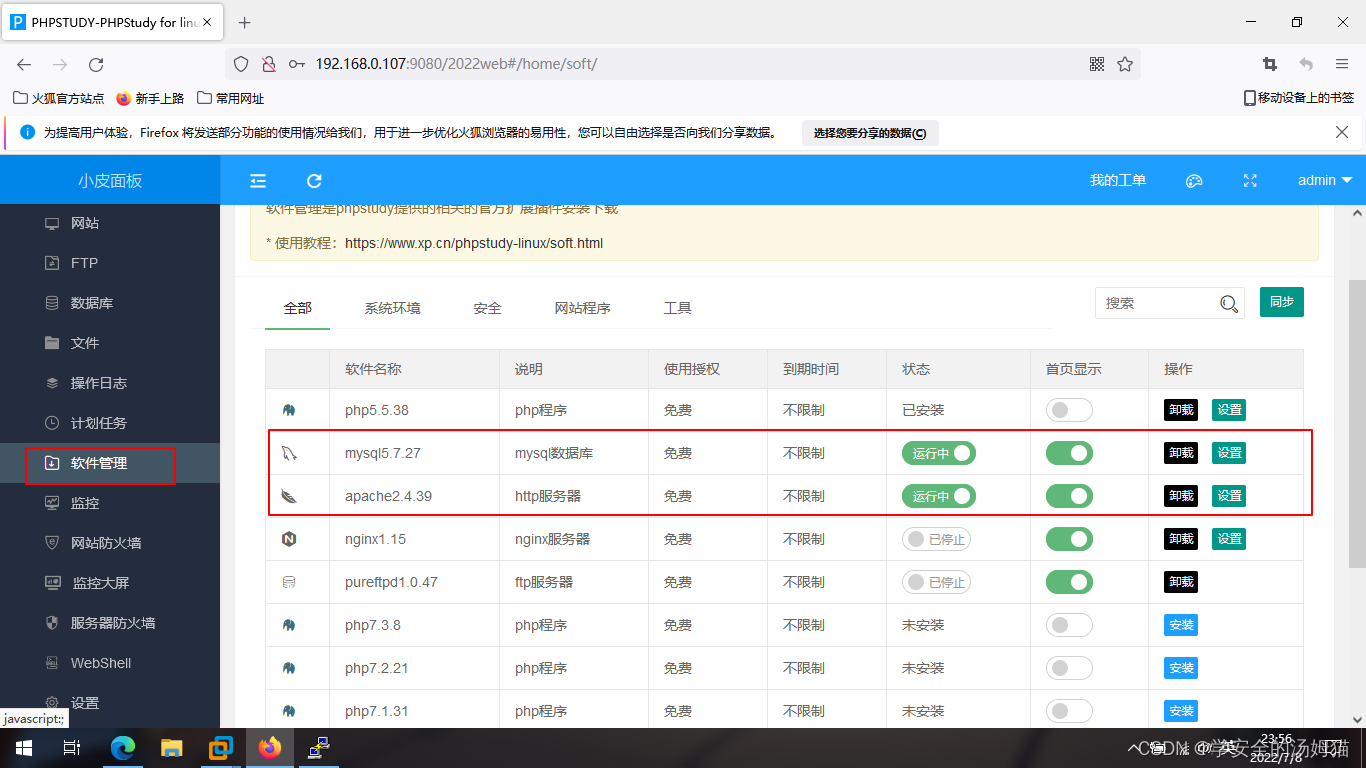
第三步:安装dvwa靶场
这里我已经下载好了,使用winscp上传到虚拟机,使用unzip解压
unzip DVWA-master.zip #解压
mv DVWA-master/ dvwa/ #Change the name of the directory
mv dvwa/ /www/admin/localhost_80/wwwroot/ #Put the unzipped file in the root directory of the website
If you don't know the root directory, we can check it on the management page
Click on the website to see it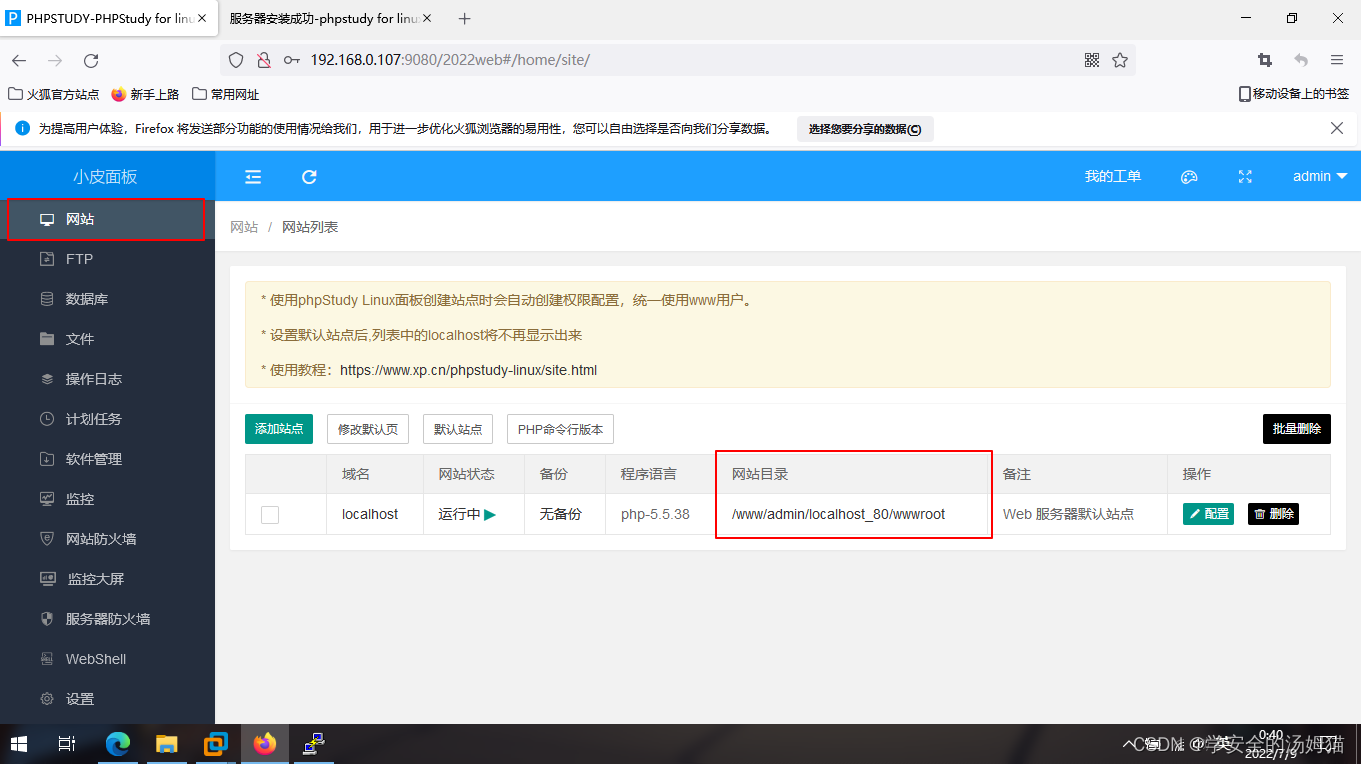
接下来我们来配置dvwa环境的config
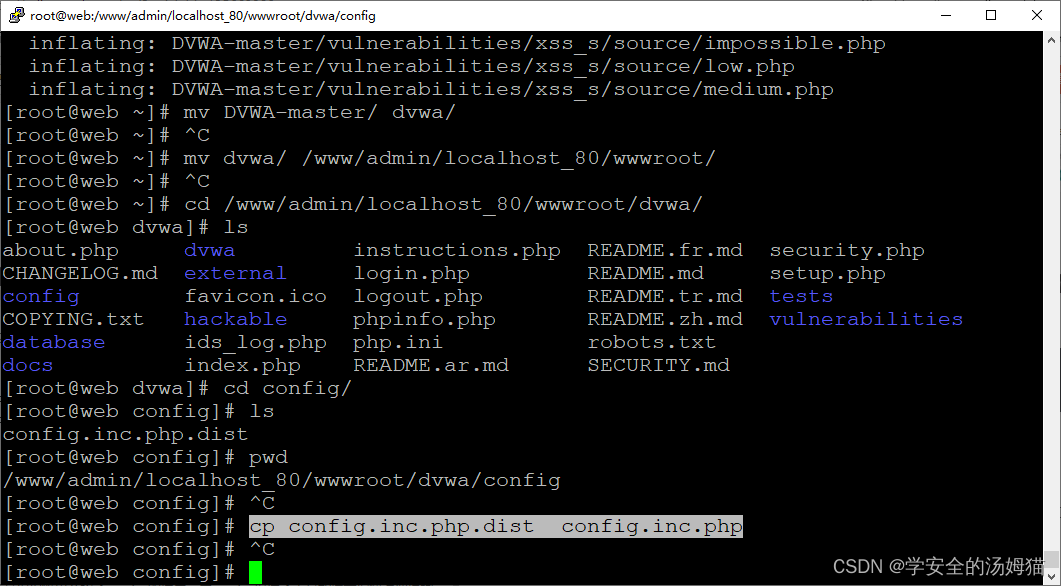
cd /www/admin/localhost_80/wwwroot/dvwa/config #进入配置文件夹
cp config.inc.php.dist config.inc.php #Copy a file and change to php文件格式
vim config.inc.php #Enter to modify the contents of the file
跳转到20line to change the usernameroot
跳转到21行修改密码为root 因为phpstudy的mysql 默认用户名和密码都是root

第四步:Use a browser to log in to the webpage to view it
Enter the address followed by the name of our folder to access it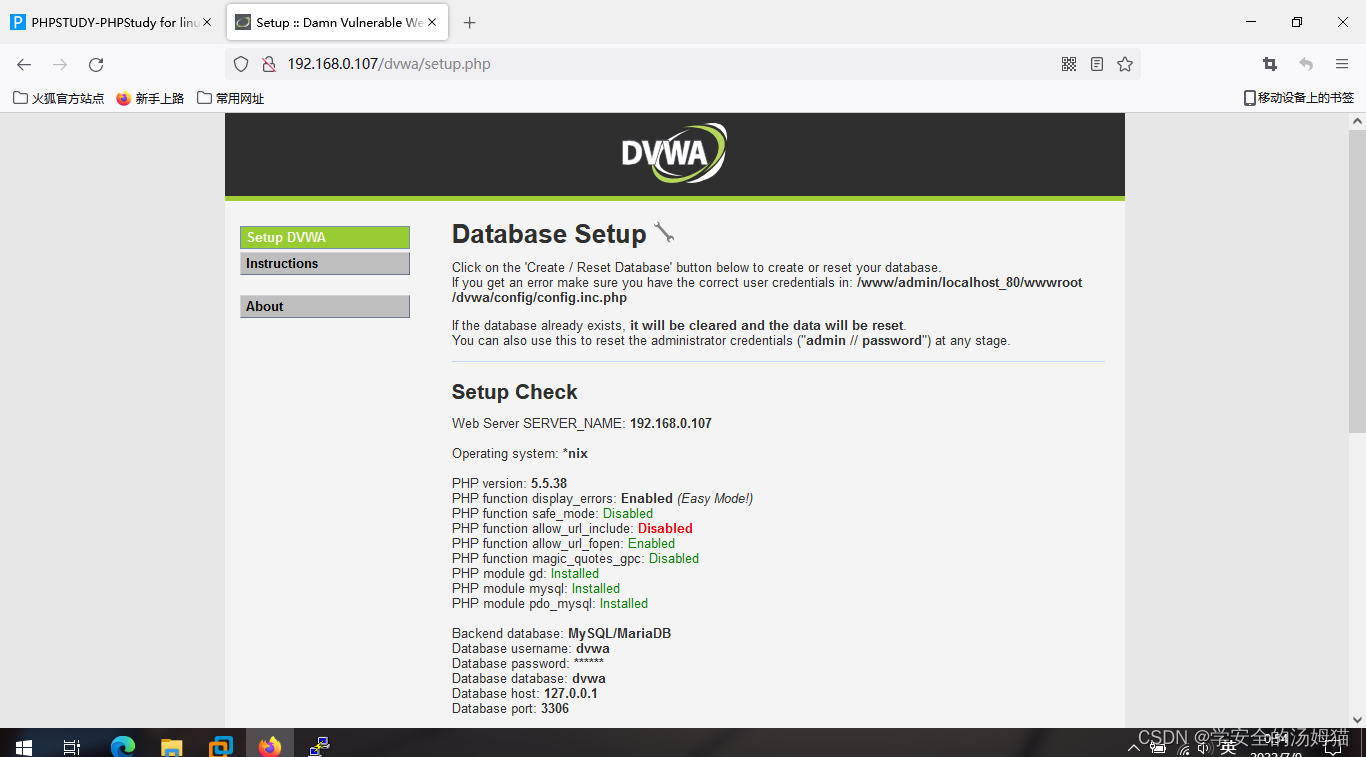
Pull to the bottom to have one“create / reset database”Click the button to create the database
Once clicked, the login page will appear,If it doesn't appear, try a few more times
dvwa的默认用户名为admin密码为password,输入后即可登录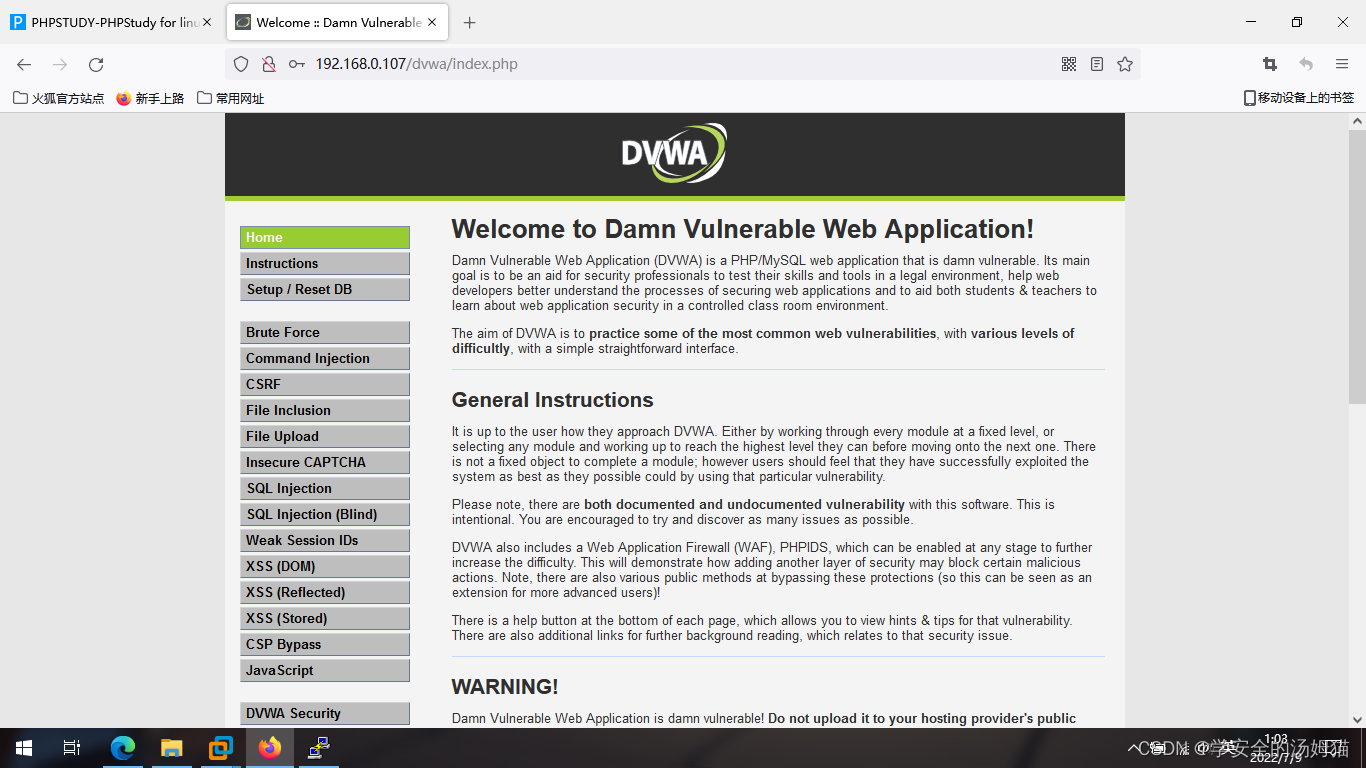
总结
使用windowsIt will save a lot of trouble if the environment is built,I thought it was time to make oneweb漏洞靶机,After that, other shooting ranges will be installed,所以就使用了linux,因为windowsThe large capacity makes my computer unbearable,The performance of the original computer was not very good,使用liunxIt can solve my current problem to a great extent.
Notes can be written in some places that are not very clear,也请大家见谅.If there is a mistake, please leave a message and point it out.
边栏推荐
- ES6 array extension methods map, filter, reduce, fill and array traversal for…in for…of arr.forEach
- hackmyvm: may walkthrough
- [campo/random-user-agent] Randomly fake your User-Agent
- Scrapy crawler encounters redirection 301/302 problem solution
- Xiaoyao multi-open emulator ADB driver connection
- ES6 iterator explanation example
- (3)Thinkphp6数据库
- VIKINGS: 1 vulnhub walkthrough
- Several interesting ways to open PHP: from basic to perverted
- Using PHPMailer send mail
猜你喜欢

hackmyvm-hopper walkthrough
Shuriken: 1 vulnhub walkthrough
ES6 array extension methods map, filter, reduce, fill and array traversal for…in for…of arr.forEach
VIKINGS: 1 vulnhub walkthrough

hackmyvm: juggling walkthrough
(1) introduction to Thinkphp6, installation view, template rendering, variable assignment
TCP communications program
OPENSSL基本实验以及OPENSSL详解
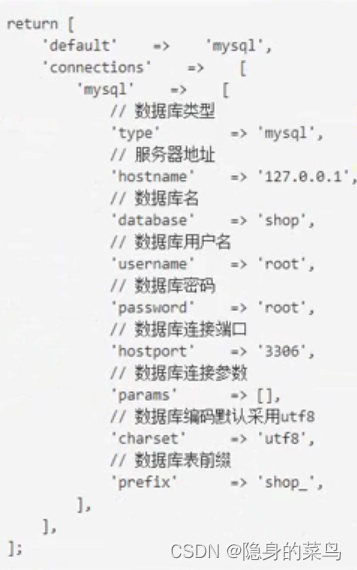
(3) Thinkphp6 database
MOMENTUM: 2 vulnhub walkthrough
随机推荐
hackmyvm-hopper walkthrough
Masashi: 1 vulnhub walkthrough
(5) Modules and packages, encoding formats, file operations, directory operations
Eric target penetration test complete tutorial
[symfony/mailer]一个优雅易用的发送邮件类库
JS objects, functions and scopes
(2)Thinkphp6模板引擎**标签
4.表单与输入
After Alibaba Cloud sets up domain name resolution redirection, I cannot use Chrome to access it
Baidu positioning js API
[campo/random-user-agent]随机伪造你的User-Agent
PHP deserialization vulnerability
The roll call system and array elements find maximum and minimum values for sorting of objects
Praying: 1 vulnhub walkthrough
Warzone: 3 (Exogen) vulnhub walkthrough
hackmyvm: juggling walkthrough
CTF入门笔记之ping
(3)Thinkphp6数据库
利用cookie获取admin权限 CTF基础题
What are the killer super powerful frameworks or libraries or applications for PHP?