当前位置:网站首页>The remainder operation is a hash function
The remainder operation is a hash function
2022-07-05 04:28:00 【Blue dye k9z】
Hash
Hashes are sometimes translated as hashes .
It is to input any length , Through the hash algorithm , Compressed to a fixed length of output .
- If you want to read and write quickly 100 Ten thousand data records , To achieve high-speed access , But due to the limitation of conditions , We are not able to accommodate 100 Continuous address space of 10000 records , What should I do .
- See if the system can provide several smaller continuous spaces , And each space can store a certain number of records .
- For example, we found 100 A smaller continuous space . in other words , These spaces are separated from each other , But the interior is continuous , And enough to hold 1 Ten thousand records are stored continuously , Then we can use the remainder and congruence theorem to design a hash function , And implement the structure of hash table .
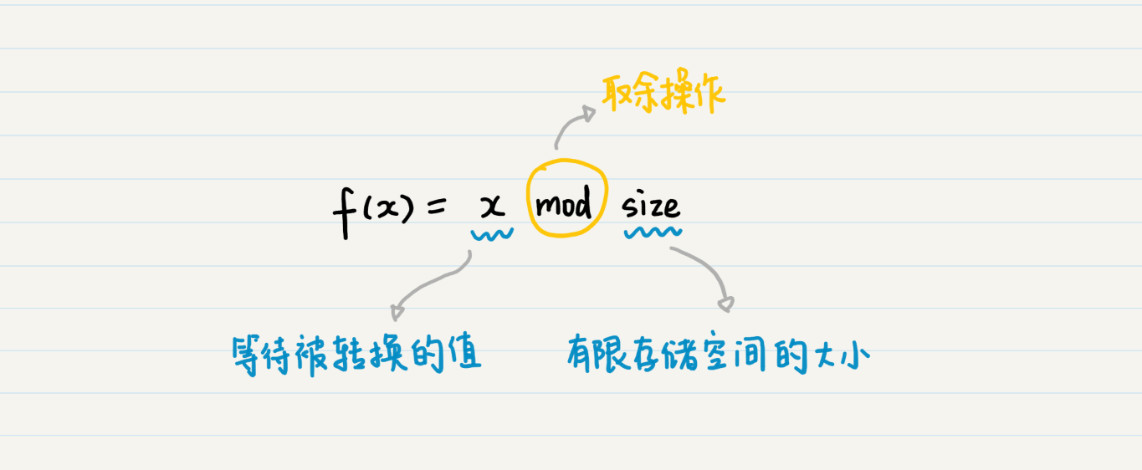
- Suppose there are two records , Their record labels are 1 and 101.
- We put these models 100 Then the remainder is 1 Of , Store in No 1 In a free space .
- And so on , Set the remainder to 2 Of 2、102、202 etc. , Store in No 2 Two free spaces .
- such , We can change according to the fast number of the remainder , Group data , And store them in different address spaces .
- The remainder operation itself is very simple , Therefore, there is little increase in addressing time .

In order to increase the randomness of data hash , You can add a large random number to the formula MAX
Under the action of the new calculation formula , Will be allocated to different available space
Used MAX After this random number , Records allocated to the same space are more “ Random ”, It is more suitable for application scenarios that need to reshuffle the data , Such as encryption algorithm 、MapReduce Data distribution in 、 High speed query and location of records, etc .
encryption
Suppose you want to encrypt a set of three digits , Then set such an encryption rule :
- Start with each three digit number 、 Tens and hundreds , Add a large random number .
- Then divide the number on each by 7, Replace the original... With the remainder 、 Ten 、 Hundreds of digits .
- Finally, the first and third bits are exchanged .
This is a basic encryption transformation process .
If say , We need to encrypt 625, Random number selection 590127.
Na Bai 、 Ten 、 Add this random number to each bit , It becomes 590133 590129 590132, Divide the three by 7 Find the remainder and get 5 1 4.
The final figure is 415.
If the encryption person knows the encryption rules , Then we can calculate that the original data is 625.
( Tips :590127%7=6)
边栏推荐
- 10 programming habits that web developers should develop
- 解密函数计算异步任务能力之「任务的状态及生命周期管理」
- 2022-2028 global and Chinese virtual data storage Market Research Report
- A應用喚醒B應該快速方法
- Common features of ES6
- Scheduling system of kubernetes cluster
- Neural network and deep learning Chapter 1: introduction reading questions
- 【thingsboard】替换首页logo的方法
- mxnet导入报各种libcudart*.so、 libcuda*.so找不到
- 官宣!第三届云原生编程挑战赛正式启动!
猜你喜欢

American 5g open ran suffered another major setback, and its attempt to counter China's 5g technology has failed
电源管理总线 (PMBus)

Live broadcast preview | container service ack elasticity prediction best practice

What are the building energy-saving software
蛇形矩阵
Realize the attention function of the article in the applet

Fuel consumption calculator

Threejs factory model 3DMAX model obj+mtl format, source file download
【科普】热设计基础知识:5G光器件之散热分析
Rome chain analysis
随机推荐
Common features of ES6
windows下Redis-cluster集群搭建
Study notes 7
Live broadcast preview | container service ack elasticity prediction best practice
如何进行「小步重构」?
Neural networks and deep learning Chapter 2: machine learning overview reading questions
Possible stack order of stack order with length n
A solution to the problem that variables cannot change dynamically when debugging in keil5
Introduction to RT thread kernel (5) -- memory management
Is "golden nine and silver ten" the best time to find a job? Not necessarily
程序员应该怎么学数学
Longyuan war "epidemic" 2021 network security competition web easyjaba
2022-2028 global and Chinese virtual data storage Market Research Report
托管式服务网络:云原生时代的应用体系架构进化
Uncover the seven quirky brain circuits necessary for technology leaders
Advanced length of redis -- deletion strategy, master-slave replication, sentinel mode
MacBook installation postgresql+postgis
[untitled]
【UNIAPP】系统热更新实现思路
这是一个不确定的时代