当前位置:网站首页>[tpm2.0 principle and Application guide] Chapter 1-3
[tpm2.0 principle and Application guide] Chapter 1-3
2022-07-07 17:38:00 【Godams】
It's not easy to code words , Please give me a compliment 
Chapter one TPM The history of
Trusted platform module (TPM) Is an encryption coprocessor .
Trusted computing organization (TCG)
Direct anonymous authentication (DAA)
Authenticate the portable key (Certified Migratable Key,CMK)
Privacy certificate Certification Center (CA)
Platform configuration register (PCR) yes TPM Dynamic memory area in , It is used to maintain the integrity of the measurement results of the system's boot sequence .PCR It can be used together with the identity key to prove whether the system boot sequence is normal .
Chapter two Basic safety concept
2.1 Password attacks
- Strike out at
- Attack on the algorithm itself
Cryptographic algorithms should avoid the following defects :
- Algorithm weakness : Choose a recognized algorithm
- Strike out at : Expand the key length , Let the user choose the required key length
2.2 Safety related definitions
news : A sequence of bytes transmitted between two parties
Confidentiality : Prevent unauthorized parties from viewing messages neir
Share secrets : A value known to both sides
integrity : Messages are not modified during storage and transmission
authentication : Associate the message with the creator , So that the receiver can determine that only the creator can send this message
to grant authorization : Prove that the user is allowed to perform this operation
Anti replay : Prevent attackers from reusing valid messages
Non repudiation : Prevent the sender from denying that it sent the message
2.3 Password family
- Secure hash ( Abstract )
Password hashes are more complex than ordinary hashes , It can receive a message of any length and compress it into a hash sequence of fixed length . Secure hashes are used for hash extension operations 、HMAC、 Notes 、 Asymmetric key digital signature and key derivation function . To ensure confidentiality , Secure hashes have the following important characteristics :- For a given message , It is not feasible to construct another message with the same hash as it
- It is not feasible to construct two messages with the same hash value
- It is not feasible to solve the original message from the hash value
- Hash extension
Once the message is extended , You cannot cancel the operation or delete the history by inverse operation .- The extension mechanism is used to update the platform configuration register (PCR) Value , Extended in PCR The value of can represent the platform status
- It can also be used for audit logs , The audit log records TPM Request and reply information
- HMAC: Message authentication code
It hashes the message together with a shared key to get- Can be used to TPM Prove that the user has mastered TPM Entity authorization data
- For the integrity of the structure stored externally , That is to prove that it has not been tampered with by the attacker
- It can also be used to generate keys , At this time, we need the key derivation function
- KDF: Key derivation function
TPM It needs to support the generation of multiple keys from a single secret , This secret is called the seed key , The algorithm of generating multiple secrets from seed keys is called key derivation function (FDF).TPM Use a special algorithm to make HMAC Can be used as KDF use , Usually it uses the seed key as HMAC Key to change some data HMAC To generate the key .( This embodies a basic cryptographic principle : You cannot use the same key for two different applications ) - Certified or authorized notes
Bill is a kind of HMAC Data structure of , The bill allows TPM Delay verifying the actions it performs . Because the bill capacity is limited, it is impossible to load a complete set of data , Sometimes the original data is replaced by the summary of the message . Used to generate HMAC Of HMAC Keys are not shared secrets , It's just TPM know . - Symmetric key
It will be used in the following three cases :TPM Data is confidential to the outside 、TPM Communication encryption 、 Use TPM To handle passwords together- Symmetric key algorithm mode :
- Electronic codebook (ECB): Just simple encryption , The same data group produces the same ciphertext
- Password group link (CBC)
- Password feedback (CFB)
- Output feedback (OFB)
- Counter (CTR)
- Symmetric key algorithm mode :
Encryption ensures confidentiality , But it cannot provide integrity and authentication mechanism .
Encrypted information cannot prove whether the message is recently generated , This function consists of nonce Realization
- nonce
It is a number that can only be used once in password operation , It is often used to prevent replay attacks . To ensure that the message is not replayed , The receiver will generate a nonce And send it to the sender . Sender handle nonce Put it in the message . Usually TPM nonce Will participate with a request message HMAC The calculation of , After the message is used ,TPM Will change nonce, If the requestor still uses the old nonce, The verification fails .nonce The license is large enough , No loops . - Asymmetric key
- RSA, Use the prime decomposition of large numbers as a one-way function . Generally, digital signature is not a direct signature of data , Instead, data generates summaries , Sign the abstract .
- ECC, Elliptic curve based on finite field . Under the same strength ECC Key ratio RSA The key is much shorter .
- ECDH(Diffie-Hellman) Realize key transfer :ECC and RSA The difference is that the ,ECC Two steps are needed. , and RSA Just one step . stay TPM You need to use ECDH when , First ( In software ) Generate another ECDH secret key , The second step , With newly generated ECDH The private key and TPM ECDH The public key of the key type generates a temporary random number , Enter random numbers into KDF Generate a symmetric key in . Simply speaking ,RSA Symmetric keys can be provided directly , and ECDH You need to generate it yourself .
- ECDSA( Elliptic curve digital signature algorithm ): Same as RSA The difference is that , because ECC The key is small , Therefore, we must ensure that the hash value of the message being signed is not too large .
2.4 Public key authentication
How to ensure that the public key is trusted , You can create digital certificates , The certificate includes the public key part of the user and the attributes of the key , Certificate by CA Key signature .
The first 3 Chapter TPM 2.0 Quick tutorial
TPM1.2 The specification mainly aims to solve the following problems :
- Device identification
- Key security generation
- Key safe storage
- NVRAM Storage
- Equipment health certificate : Prove the health of the system , If the system is damaged , It may not be credible
TPM 2.0 It also expands the following functions :
- Algorithm flexibility
- Enhanced authorization : Multi factor and multi-user authentication authorization strategy
- Key fast loading : Load the key through the symmetric key algorithm
- Non vulnerability PCR: In the past, when the key was locked with the device state, it would cause management problems , Because usually , When the equipment status must be changed by the authorization status , The key must also be changed , Not now .
- Flexible management : Different kinds of authorization can be separated
- Identify resources by name
3.1 TPM 1.2 Usage scenarios of
- Identity recognition
- encryption
- Key storage
- Random number generator (RNG)
- NVRAM Storage : With restricted access properties , It can store keys , once PC close , The key is not available , This ensures that some data can be provided to users , Don't worry about being erased by accident or malicious intent ,NVRAM Provide the following functions :
- Store the root key for the certificate chain : They can't be modified
- Store endorsement key (EK):EK Stored by the manufacturer , It is used to decrypt the certificate and pass the password to TPM, Designed to protect sensitive privacy .
- Store... Used to represent the state of the machine : For example, in the unified extensible firmware interface UEFI Safe startup enables the use of .
- Storage of the decryption key used before the disk is available : Such as the key used for self encryption drive
- Platform configuration register (PCR): Can be TPM in PCR It is regarded as the storage place of the results measured in the guidance process .
- Privacy enabled :EK It cannot be directly used to identify specific TPM, contrary TPM A protocol is provided to generate identification keys (AIK), This key can be used as TPM Pseudo identity key of the platform . Provide privacy CA The agreement means EK Can be used to prove AIK From the TPM, Without proving AIK From which TPM.
3.2 TPM 2.0 Additional usage scenarios
- Algorithm flexibility
- Enhanced authorization
new EA Allow for many new situations : Multi factor multi-user authentication 、 Resources only use n Time 、 Resources are used only for certain periods of time 、 Revoke the use of resources 、 How resources are used by different people .- password ( Plaintext )
- HMAC secret key ( Also in the TPM 1.2 in )
- Signature ( for example , Through smart card )
- Use additional data signatures
- At least at startup ,PCR Value as a proxy for system state
- Location as a proxy for a specific command source location
- Time
- Internal counter value
- NV Index value
- NV Indexes : Can be based on NV Whether the index has been written to authorize
- Physical existence
- Key fast loading (TPM 2.0 new function )
TPM 1.2 in , When a key is initialized and loaded , It must use the private key of the parent key of the key for time-consuming private key decryption . It's a bit of a twist , My understanding is that , stay 1.2 The key calculated each time in will exist during the power on and power off cycle , Delete after power failure , however TPM 2.0 The key can be stored in external memory , In this way, you can read it every time you power on or power off , Without recalculating . - Non vulnerability PCR(TPM 2.0 new function )
PCR Values usually indicate the state of the machine , Smaller number PCR Indicates the boot process of the system , Higher PCR Indicates the event after kernel startup .** Both keys and data can be locked to a specific with a specific value PCR, This behavior is called sealing .** But if the key or data is locked to represent BIOS Of PCR, Then upgrade BIOS It's hard , This is vulnerability PCR. stay TPM 2.0 in , The matter can be sealed as approved by a specific signer PCR value , Not specific PCR value , Only when PCR In the process of being approved by a specific authority ( By digital signature ) When , To make TPM Release a secret . - Flexible management
TPM 1.0 Specification , At the same time ,TPM There are only two authorizations : The owner authorizes and stores the root key (SRK) to grant authorization , Owner authorization is used for many purposes- Reset the dictionary attack counter
- take TPM Reset to factory settings
- prevent SRK Modified by people who know well-known secrets
- Prevent creation AIK, Except for TPM The owner's end user provides privacy
- By preventing creation and deletion NVRAM Indexes , avoid NVRAM Threatened by people other than those who know the owner's authorization
TPM2.0 in , The roles represented by the various uses authorized by the owner are separated in the specification , This is done by giving roles different authorizations and strategies , And make them in TPM Have different hierarchy To achieve .
- Identify resources by name (TPM2.0 new function )
TPM1.0 in , Resources are identified by handles rather than encrypted names , therefore , If two resources have the same authorization , Low level software may be tricked into changing the handle of identifying resources , So users may be cheated , Grant different authorizations to different behaviors .TPM2.0 in , Resources are identified by name , Password is bound to name , Thus eliminating this attack . The name contains the key policy , So the name can be used to prove what it means to authorize the use of the key .
边栏推荐
猜你喜欢
简单的loading动画
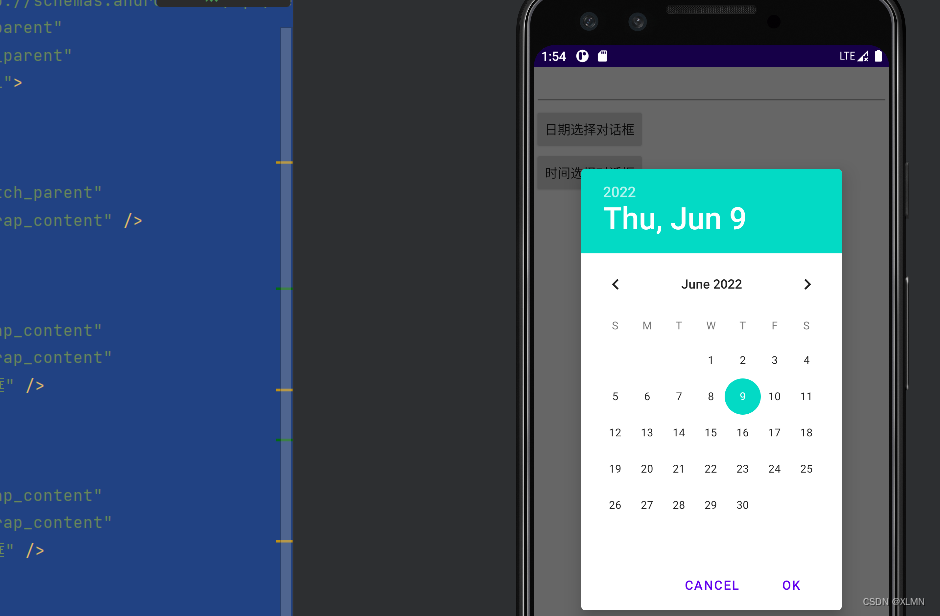
DatePickerDialog and trimepickerdialog
【解惑】App处于前台,Activity就不会被回收了?
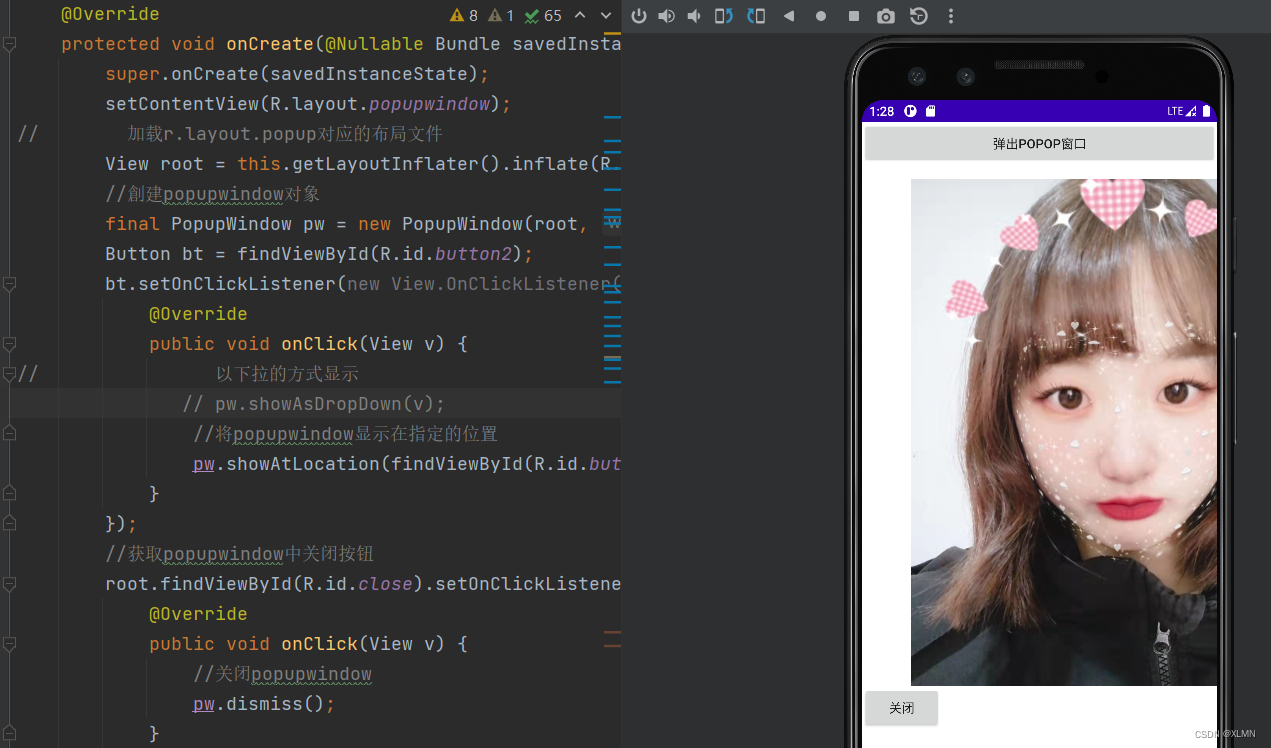
Create dialog style windows with popupwindow

使用popupwindow創建对话框风格的窗口
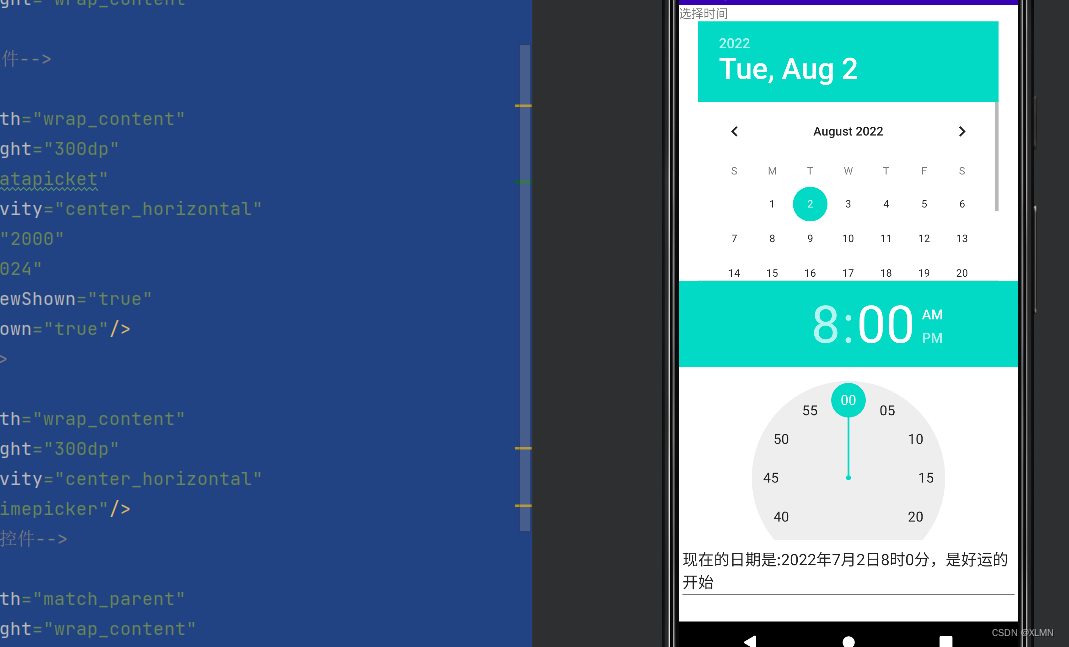
Dateticket and timeticket, functions and usage of date and time selectors
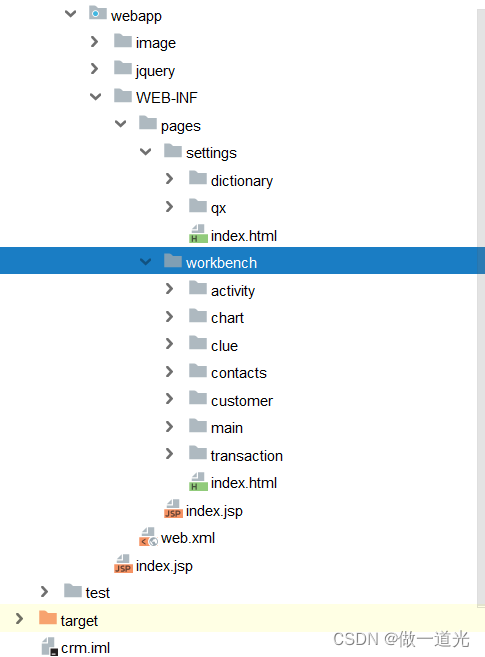
第2章搭建CRM项目开发环境(搭建开发环境)

麒麟信安携异构融合云金融信创解决方案亮相第十五届湖南地区金融科技交流会
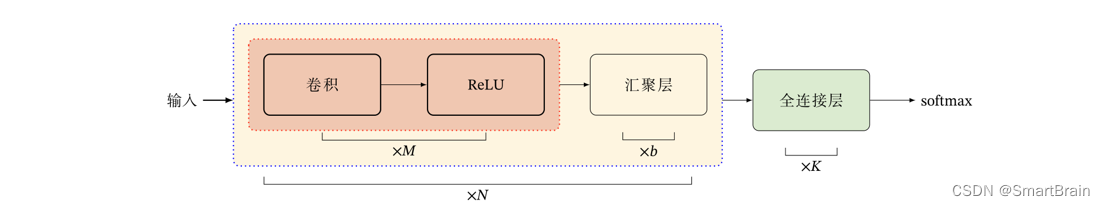
深入浅出图解CNN-卷积神经网络
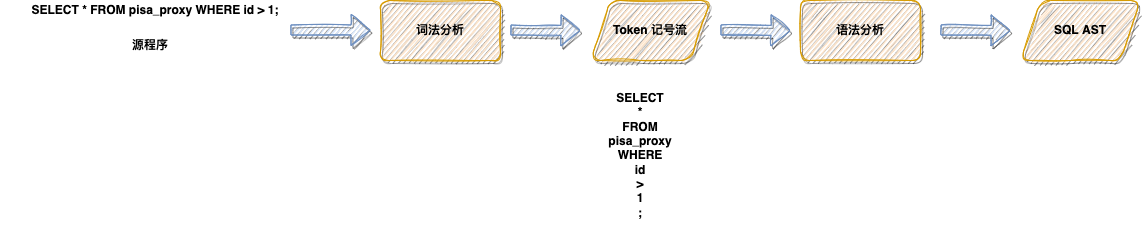
Lex & yacc of Pisa proxy SQL parsing
随机推荐
Functions and usage of serachview
Is AI more fair than people in the distribution of wealth? Research on multiplayer game from deepmind
管理VDI的几个最佳实践
99%的人都不知道|私有化部署还永久免费的即时通讯软件!
Audio device strategy audio device output and input selection is based on 7.0 code
字符串 - string(Lua)
What is cloud computing?
到底有多二(Lua)
专精特新软件开发类企业实力指数发布,麒麟信安荣誉登榜
toast会在程序界面上显示一个简单的提示信息
Functions and usage of tabhost tab
阿富汗临时政府安全部队对极端组织“伊斯兰国”一处藏匿点展开军事行动
Ratingbar的功能和用法
麒麟信安操作系统衍生产品解决方案 | 存储多路径管理系统,有效提高数据传输可靠性
A tour of grpc:03 - proto serialization / deserialization
yolo训练过程中批量导入requirments.txt中所需要的包
[fan Tan] those stories that seem to be thinking of the company but are actually very selfish (I: building wheels)
[distributed theory] (I) distributed transactions
第2章搭建CRM项目开发环境(数据库设计)
L1-019 谁先倒(Lua)