当前位置:网站首页>Solution for processing overtime orders (Overtime unpaid)
Solution for processing overtime orders (Overtime unpaid)
2022-07-03 02:04:00 【Small brother's advanced】
1. Overtime unpaid order processing
1.1 Demand analysis
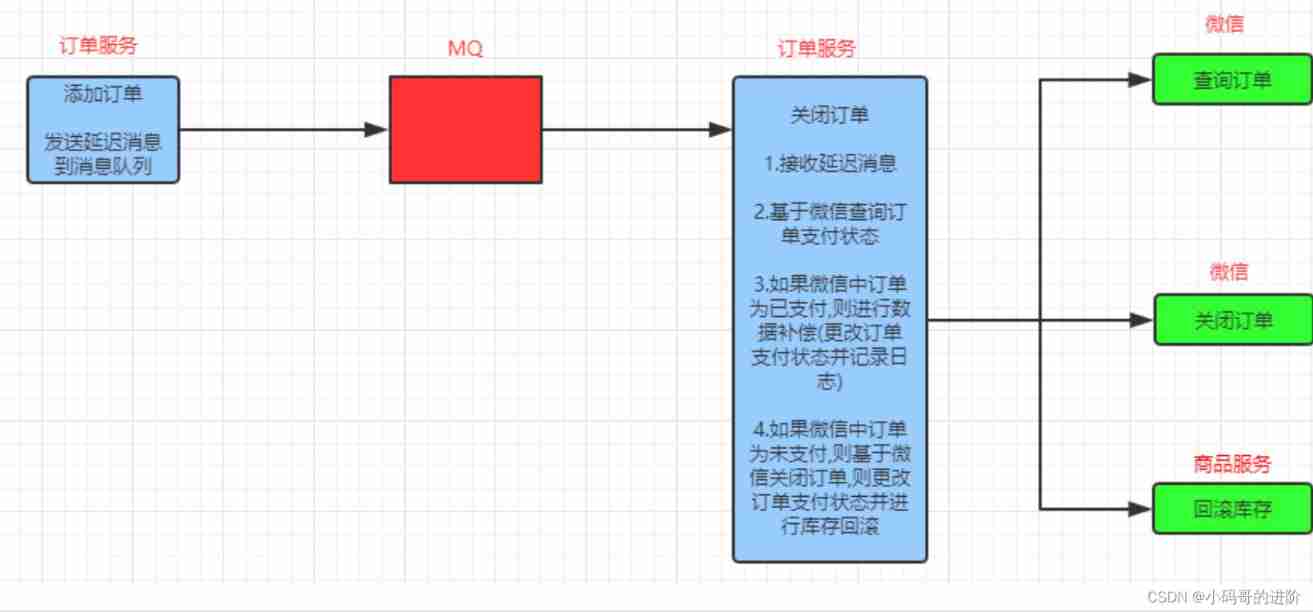
Orders that have not been paid beyond the time limit , We need to deal with overtime orders : First call wechat payment api, Query the payment status of this order . Call to close the order if not paid api, And modify the order status to closed , And roll back the inventory . If the order has been paid , Then do the compensation operation ( Modify order status and records ).
1.2 Realize the idea
Implementation steps :
1. When generating an order ( The creation time of the order is recorded in the table )
2. According to the creation time of the order 30 Minutes , If the order is not paid
3. Put the order generation message into the dead letter queue
4. Consume the messages in the dead letter queue : Delete the unpaid orders in the database , Need to modify the inventory of goods
How to get orders that exceed the time limit ? We can use delayed message queues ( Dead letter queue ) To achieve .
The so-called delayed message queue , That is, messages sent by message producers will not be consumed immediately , Instead, it can be consumed after the set time .
We can send a delay message when the order is created , Message is order number , The system will retrieve this message after a limited time , Then query the payment status of the order , Make corresponding treatment according to the results .
1.3 rabbitmq Delay message
Use RabbitMQ To implement deferred messages, you must first understand RabbitMQ Two concepts of : News TTL And dead letter Exchange, Through the combination of the two to achieve the above requirements .
1.3.1 News TTL(Time To Live)
News TTL It's the survival time of the message .RabbitMQ You can set the queue and message separately TTL. Setting the queue is the retention time when the queue has no consumers , You can also make separate settings for each individual message . Beyond this time , We think the news is dead , Call it a dead letter .
Let's create a queue queue.temp, stay Arguments Add x-message-ttl by 5000 ( In milliseconds ), Then every message that enters this queue is 5 Seconds later .
1.3.2 A dead letter exchanger Dead Letter Exchanges
A message satisfies the following conditions , It will enter the dead letter switch , Remember, this is the switch, not the queue , A switch can correspond to many queues .
(1) A message was Consumer Rejected , also reject Method parameters requeue yes false. That is to say, it will not be put in the queue again , Used by other consumers .
(2) From the above news TTL here we are , The news is out of date .
(3) The length limit of the queue is full . Messages in the front row will be discarded or thrown on the dead letter switch .
Dead Letter Exchange In fact, it is a kind of ordinary exchange, And create other exchange There is no difference . Just in a certain setting Dead Letter Exchange There are messages out of date in the queue of , Will automatically trigger message forwarding , Send to Dead Letter Exchange In the middle .
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-IL59uC3x-1644889547028)(images/10-6-1634236948865.png )]](/img/b7/b0439d620f8047d95b7e58a8334b95.jpg)
We can now test the delay queue .
(1) Create a dead letter exchange exchange.ordertimeout (fanout)
(2) Create a queue queue.ordertimeout
(3) Establish a dead letter exchange exchange.ordertimeout And queues queue.ordertimeout Binding between
(4) Create a queue queue.ordercreate,Arguments add to
x-message-ttl=10000
x-dead-letter-exchange: exchange.ordertimeout
(5) test : towards queue.ordercreate Queue add message , wait for 10 Message from in seconds queue.ordercreate The queue disappears ,
1.3.3 Delayed message processing
From message queue queue.ordertimeout Extract messages from , Execute order deletion
边栏推荐
- A 30-year-old software tester, who has been unemployed for 4 months, is confused and doesn't know what to do?
- How is the mask effect achieved in the LPL ban/pick selection stage?
- 疫情當頭,作為Leader如何進行團隊的管理?| 社區征文
- CFdiv2-Fixed Point Guessing-(区间答案二分)
- es6 filter() 数组过滤方法总结
- Storage basic operation
- Performance test | script template sorting, tool sorting and result analysis
- 浏览器是如何对页面进行渲染的呢?
- Reprint some Qt development experience written by great Xia 6.5
- Take you ten days to easily complete the go micro service series (II)
猜你喜欢

stm32F407-------ADC
In 2022, 95% of the three most common misunderstandings in software testing were recruited. Are you that 5%?
y54.第三章 Kubernetes从入门到精通 -- ingress(二七)
Some functions of applet development
![[camera topic] turn a drive to light up the camera](/img/d3/7aabaa5c75813abc4a43820b4c3706.png)
[camera topic] turn a drive to light up the camera
【Camera专题】OTP数据如何保存在自定义节点中

How do it students find short-term internships? Which is better, short-term internship or long-term internship?

Depth (penetration) selector:: v-deep/deep/ and > > >
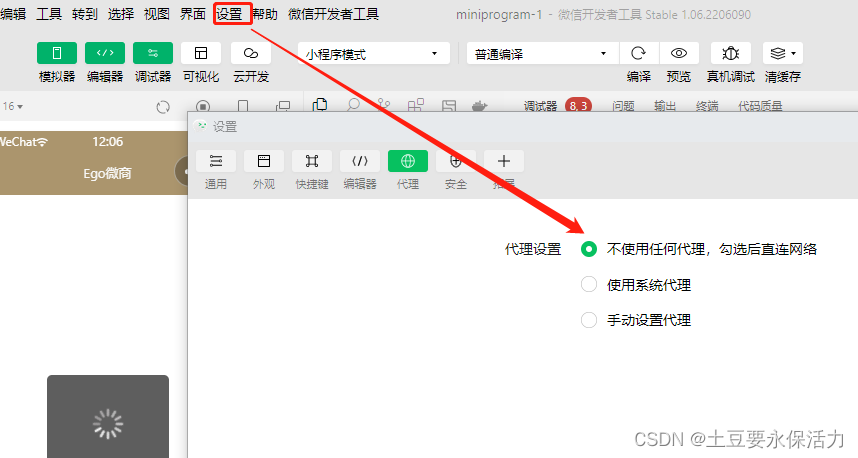
Wechat applet development tool post net:: err_ PROXY_ CONNECTION_ Failed agent problem
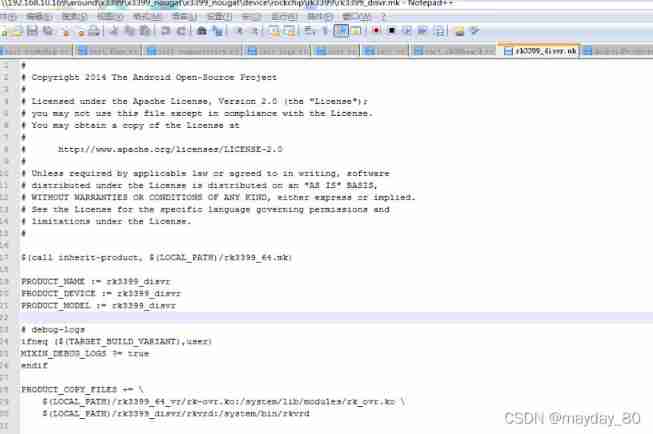
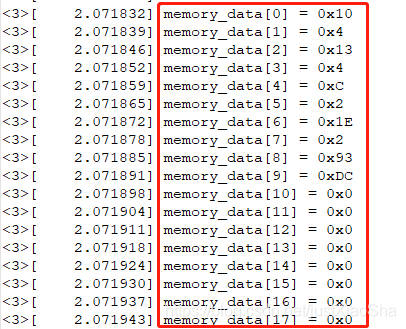
Rockchip3399 start auto load driver
随机推荐
Network security - DNS spoofing and phishing websites
How to find summer technical internship in junior year? Are you looking for a large company or a small company for technical internship?
502 (bad gateway) causes and Solutions
详细些介绍如何通过MQTT协议和华为云物联网进行通信
Analyzing several common string library functions in C language
PS去除水印详解
Comment le chef de file gère - t - il l'équipe en cas d'épidémie? Contributions communautaires
Bottleneck period must see: how can testers who have worked for 3-5 years avoid detours and break through smoothly
网络安全-NAT网络地址转换
In the face of difficult SQL requirements, HQL is not afraid
¢ growth path and experience sharing of getting an offer
Wechat applet Development Tool Post net:: Err Proxy Connexion Problèmes d'agent défectueux
Method of removing webpage scroll bar and inner and outer margins
What are MySQL locks and classifications
[shutter] top navigation bar implementation (scaffold | defaulttabcontroller | tabbar | tab | tabbarview)
[data mining] task 2: mimic-iii data processing of medical database
stm32F407-------IIC通讯协议
Niuniu's ball guessing game (dynamic planning + prefix influence)
es6 filter() 数组过滤方法总结
树形结构数据的处理