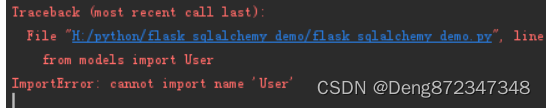
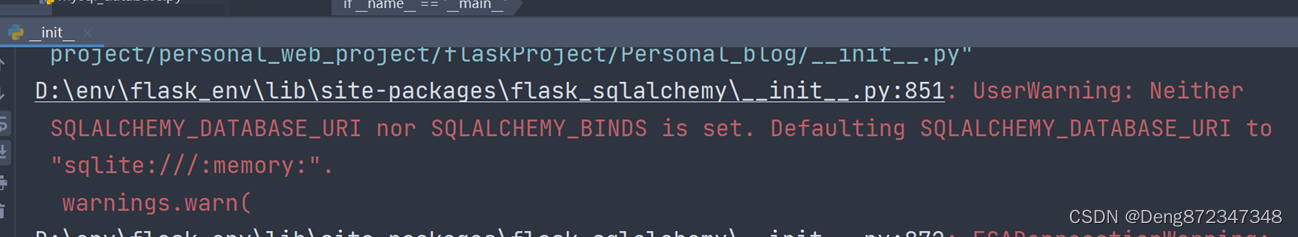
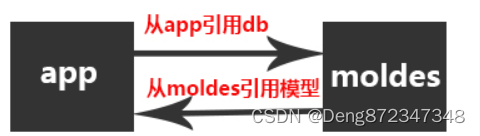
当前位置:网站首页>flask-sqlalchemy 循环引用
flask-sqlalchemy 循环引用
2022-07-04 07:07:00 【Deng872347348】
边栏推荐
- MySQL storage engine
- Novel website program source code that can be automatically collected
- MySQL 45 lecture learning notes (12) MySQL will "shake" for a while
- Knowledge payment applet dream vending machine V2
- 电脑通过Putty远程连接树莓派
- Tar source code analysis 8
- Tar source code analysis Part 3
- 《剑指Offer》第2版——力扣刷题
- Deep profile data leakage prevention scheme
- 关于IDEA如何设置快捷键集
猜你喜欢
电脑通过Putty远程连接树莓派
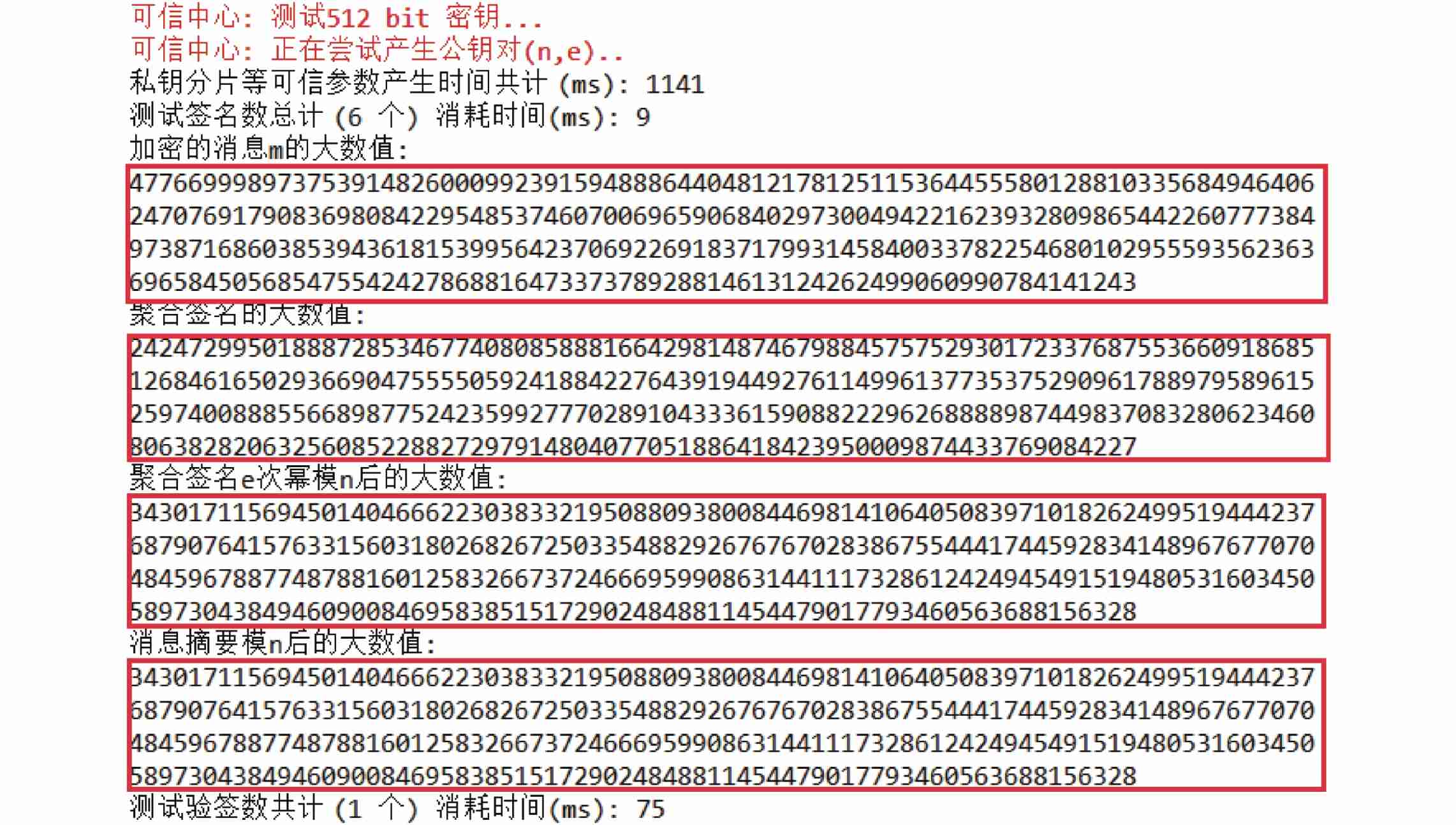
Research on an endogenous data security interaction protocol oriented to dual platform and dual chain architecture
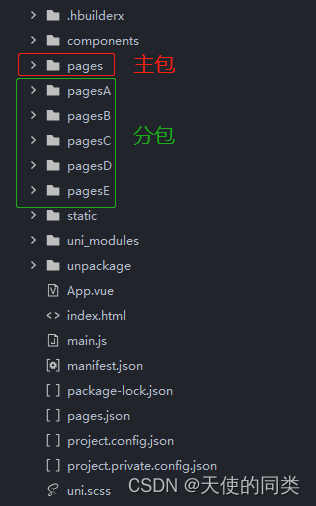
uniapp小程序分包

The cloud native programming challenge ended, and Alibaba cloud launched the first white paper on application liveliness technology in the field of cloud native
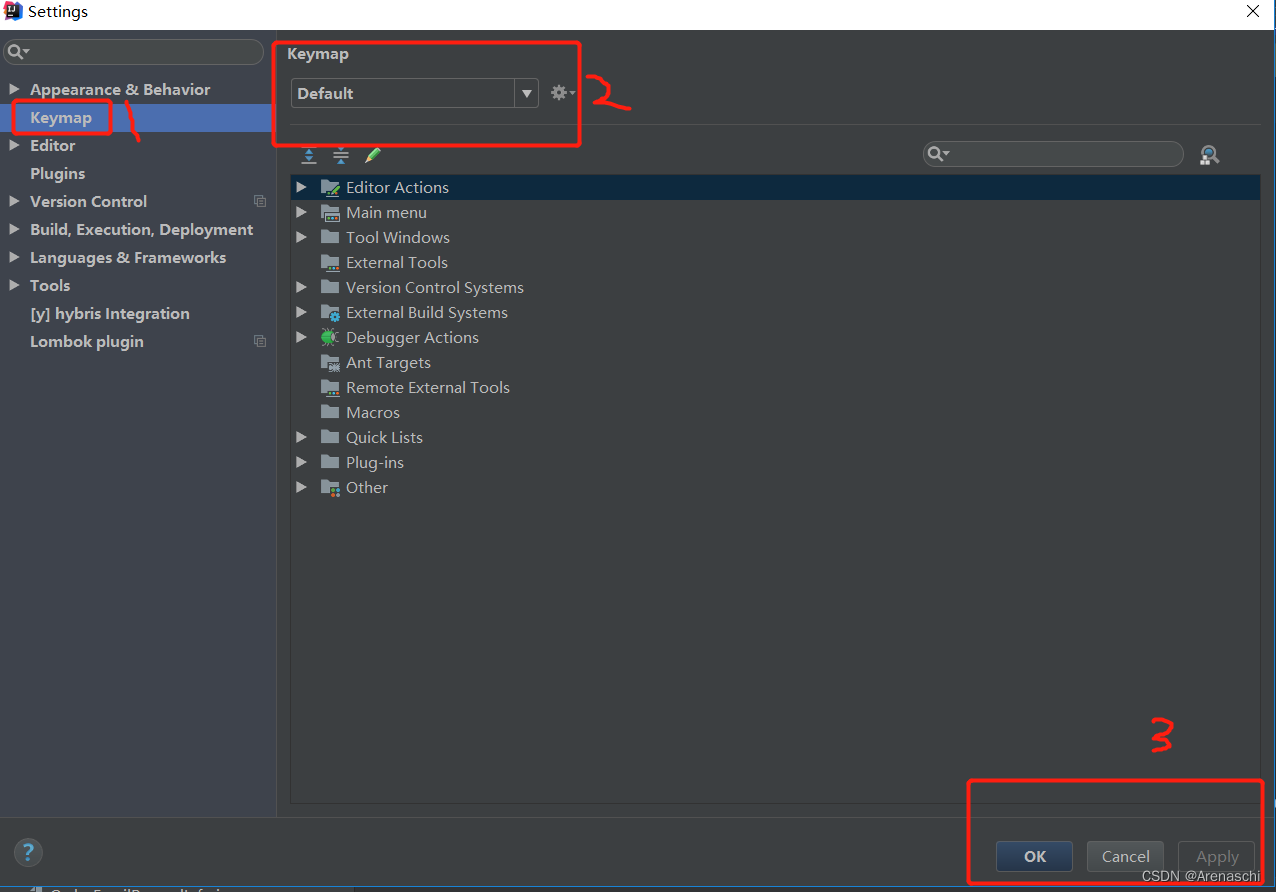
About how idea sets up shortcut key sets

Boosting the Performance of Video Compression Artifact Reduction with Reference Frame Proposals and
![[thread pool]](/img/de/d19897bdcfd65026cfe2a23c41b8c0.jpg)
[thread pool]
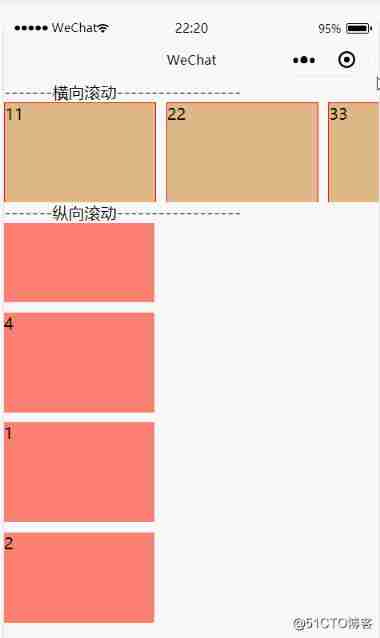
Wechat applet scroll view component scrollable view area
notepad++如何统计单词数量
Google Chrome Portable Google Chrome browser portable version official website download method
随机推荐
同一个job有两个source就报其中一个数据库找不到,有大佬回答下吗
电子协会 C语言 1级 35 、银行利息
what the fuck! If you can't grab it, write it yourself. Use code to realize a Bing Dwen Dwen. It's so beautiful ~!
The difference between synchronized and lock
Vulhub vulnerability recurrence 77_ zabbix
[MySQL transaction]
Enter the year, month, and determine the number of days
js 常用时间处理函数
How does the recv of TCP socket receive messages of specified length?
Selection (022) - what is the output of the following code?
MySQL 45 learning notes (XI) how to index string fields
【FPGA教程案例7】基于verilog的计数器设计与实现
tars源码分析之3
Deep understanding of redis -- a new type of bitmap / hyperloglgo / Geo
Responsive - media query
MySQL 45 lecture learning notes (VII) line lock
Wechat applet scroll view component scrollable view area
Tar source code analysis 6
tars源码分析之4
Review of enterprise security incidents: how can enterprises do a good job in preventing source code leakage?