当前位置:网站首页>[tpm2.0 principle and Application guide] Chapter 5, 7 and 8
[tpm2.0 principle and Application guide] Chapter 5, 7 and 8
2022-07-07 18:02:00 【Godams】
The first 5 Chapter Specification guidelines
5.2 Some definitions
The following definitions apply to commands and responses :
- to grant authorization : Grant access to TPM Rights of certain entities in
- Password Authorization : This is a one-time express authorization
- HMAC to grant authorization :HMAC Keys are derived from shared keys , This is the basis of authorization
- Policy or enhanced authorization : Authorize with policy assertions that must be met . A policy assertion is a command sent to... Before it is authorized TPM The order of
- conversation : The session is used to authorize , And each command operates ( encryption , Decrypt , Audit, etc ) All in one conversation . Based on HMAC In the conversation with strategy , The session is created and used by several other commands . Password authorization is a special session that does not carry any state .
- Handle : One is used to identify occupancy TPM In memory TPM Resource identifier
- Byte stream : Actually send... In the order TPM Bytes of , In response, it means actually from TPM Bytes received
- Standardize data
- Anti serialization data :C Language structure format data
- Serialized data : Normalized data ( That is, send or from TPM Received format )
The following fields , Describe in the order in which the command byte stream appears :
- Command header : Common part of all commands
- Handle area : The package contains what the command in part III refers to 0~3 A handle
- Authorized area : Contains command session data . Multiple sessions can be associated with a single command , So this area can contain 0-3 Parameters of painting . It contains authorization information 、 Each command session information and some need to be in the application and TPM Session state information for communication between .
- Parameter area : Contains the parameters of the specific command described in part 3
The main field definitions of the response byte stream :
- Response head : The common part of all responses
- Handle area
- Parameter area
- Authorized area : Contains response session data . Multiple sessions can be associated with a single command , Therefore, this area can contain 0-3 Parameters of sessions .
5.3 The third part command
Commands without authorization (TPM2_Startup) It's made up of three parts :
- General description : Describe the order with text situation , Specify the constraints entered
- Command and response : Input data of command and output data of response
- Detailed operation : Condition table containing code and code return error
The rest of chapter five is about specific command details , I won't go into details here
The first 7 Chapter TPM Software stack (TSS)
7.1 TSS summary
From top to bottom ,TSS It includes the following layers : features API(Featurn API,FAPI)、 Enhanced systems API(Enhanced System API,ESAPI)、 System API(System API,SAPI)、TPM Command transmission interface (TPM Command Transmission Interface,TCTI)、TPM Access to the agent (TPM Access Broker,TAB), Explorer (Resource Manager,RM) And device drivers (Device Driver)
Technicians should be based on FAPI Programming , Equate to JAVA,C# etc. . Next ESAPI, Need a lot of TPM knowledge , It provides some session management and password support .SAPI Layer allows you to access TPM All functions of , But it needs advanced professional knowledge .TCTI Layer is used to transport TPM Command and receive response .TAB Layer control multi process synchronous access TPM.RM Be similar to PC Virtual memory management on , be responsible for TPM Objects and sessions are TPM Swap in and out of internal storage space .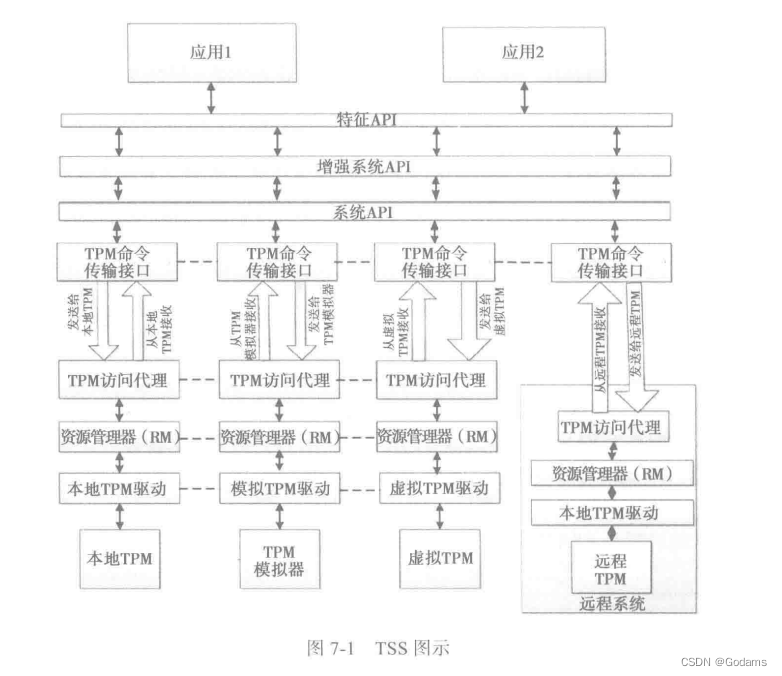
7.2 FAPI
establish TSS features API(FAPI) The clear purpose of is , Easy for programmers to use TPM 2.0 function . One way to implement this layer is to use configuration files , Create default configuration options , When creating and using keys , There is no need to choose an algorithm explicitly 、 Key length 、 Encryption mode and signature mechanism .
FAPI Basic names are defined for entities of the default type
- secret key
- NV
- Standard strategy and certification
use FAPI Entities created and used by commands are authorized by policies , all FAPI Functions assume that the key is authenticated only by policy .
7.3 SAPI
SAPI The design purpose of the specification is as follows :
- Provides access to TPM Capabilities of all functions
- Cross platform availability , Embed from high 、 Storage constrained environments to multiprocessing servers .
- In providing access TPM Under the condition of all functions , Make programmers easy
- Both synchronous and asynchronous calls are supported TPM
- SAPI The implementation does not need to allocate any memory , In most implementations , The caller is responsible for allocating SAPI All the memory of .
SAPI It contains four groups of functions : Command context allocation function 、 Command preparation function 、 Command execution function 、 Command completion function :
- Command context allocation function : For distribution SAPI Command context data structure , It is an opaque structure
- Command preparation function
- Command execution function : Commands can be sent synchronously or asynchronously
- Command completion function : This set of functions is required for command post-processing , If the session is set as an encrypted session , Then this group of functions also includes the response HMAC Calculation and response parameter decryption .
7.4 TCTI
TPM Command transmission interface (TCTI) The context structure tells SAPI function , How to communicate with TPM signal communication . Each process 、 Every TPM There is one. TCTI Context structure , Created from the initial code .
stay TPM Any layer of the stack , As long as you send and receive ordered byte streams , They all use TCTI. At present, this is reflected in two places ,SAPI and TAB as well as RM And drive .
7.5 TAB
TAB Used to control and synchronize a single share TPM Multi process access .
- When a process goes to TPM Send commands and from tpm When receiving a response , Other processes are not allowed to send commands and receive responses .
- TAB The process needs to be blocked from accessing the process that does not belong to it TPM conversation 、 Objects and sequences , Which one to use TCTI Connect to load objects 、 Start a session or start a sequence , Determine the ownership relationship .
7.6 RM
RM The function of is equivalent to the virtual memory manager in the operating system . because TPM The on-chip storage space is limited , object 、 conversation 、 The sequence needs to be in TPM Exchange with external memory , In order to let TPM The command can execute .
One TPM The command can use up to three entity handles and three session handles . All these are stored in TPM In the memory , for TPM Used to execute commands .RM My job is to intercept the command byte stream , Determine what resources need to be loaded into TPM in , Exchange enough space to load the required resources , Then load the required resources .
7.7 Device drivers
The device driver receives a command byte buffer and buffer size , Perform the necessary actions , Send those bytes to TPM. When requested by a higher level in the stack , The driver will wait , until TPM Prepare response data , Then read the response data , Return it to the upper layer of the stack .
The first 8 Chapter Entity
TPM Entity is TPM An item that can be directly indexed through a handle . This chapter will introduce : Permanent entity (hierarchy、 Dictionary attack locking mechanism 、PCR); Non volatile index (NV Indexes ); object ( Keys and data ); Volatile entities ( Various conversations );
8.1 Permanent entity
The handle to the permanent entity is made of TPM Specification definition , Cannot be created or deleted . stay TPM 1.2 in ,PCR And the owner is the only permanent entity ; Store root key (SRK) There is also a fixed handle , But it is not a permanent entity . stay TPM 1.2 There are many : Three persistence hierarchy、 Temporary hierarchy、 Dictionary attack lock reset 、PCR、 Keep handle 、 Clear text password authorization session and platform hierarchy NV function .
- persistence hierarchy
platform 、 Storage and endorsement . these hierarchy All need to be authorized to use , So each one has an authorization value and policy , Both can be hierarchy Administrator modification - Temporary hierarchy
empty hierarchy, It is also indexed by a permanent handle , It's every time TPM It will be automatically cleared after power on and restart - Reset dictionary attack lock
It has no key or object hierarchy. If it is triggered , This mechanism is used to reset the dictionary attack locking mechanism or clear . It usually represents TPM Stored hierarchy Of IT Administrators . - PCR
PC The client platform has at least 24 individual PCR.TPM It is mandatory to have at least one bank( Using the same hash algorithm PCR aggregate ), Programmable to support at startup SHA-1 perhaps SHA-256. - Keep handle
If the specific platform specification determines to use reserved handles ,TPM There will be some reserved handles for specific manufacturers in . - Password authorization session
The caller uses this handle to complete the plaintext password ( And HMAC Values correspond to ) to grant authorization - platform NV Enable
8.2 NV Indexes
TPM There is a certain amount of nonvolatile space , Users can configure them as storage space , When in the configuration , You need to give a user selected index and some attribute sets .
NV The index has an associated authorization value and authorization policy , The authorization value can be changed according to the wishes of the index owner , But strategies are being created NVRAM After the time is set , Can't be changed anymore .
NV When the index is created , Just with one hierarchy Related to , When hierarchy When cleared , Associated with it NV The index will also be deleted
8.3 object
TPM Objects are either data , Or the key , It has a public part , There may also be a four part . just as NV The index is the same , All objects belong to four hierarchy One of the : platform 、 Storage 、 Recite 、 Or empty .
8.4 Non persistent entities
It will not continue to exist after the system is powered off and restarted , Although non persistent entities can be saved , But after each power on ,TPM The encryption mechanism will prevent loading the saved context , To force the loss , This entity type has many categories :
- Authorization session : Include HMAC And policy sessions
- Hash and HMAC Event queue entities hold intermediate results
In contrast to non persistent entities , Persistent entities persist after each restart .
8.5 Persistent entities
A persistent entity is an object , One hierarchy The owner has asked to remain on restart TPM in . It differs from permanent entities in , It can be deleted ,TPM Only limited persistent memory .
Usually , Master storage key (SRK)、 Master restricted signature key (AIK), There may also be endorsement keys (EK), yes TPM The only persistent entities in .
8.6 The entity name
Hashed and HMAC Computed command parameter flow , It implies the name of each entity corresponding to the handle , Even if the command parameter may not contain a name . After it passes HMAC After the calculation is authorized , An attacker may modify the handle , But the corresponding value cannot be modified .
The name is the unique identifier of the entity . Permanent entity (hierarchy and PCR) Have a handle that will never change , So their name is their handle . Other entities (NV Indexed and loaded entities ) Have a calculated name , The name is essentially the hash value of the entity's public data . An attacker can delete this index and redefine it , however , Unless the data area is public ( Index value , Attribute values and policies ) It's the same , Otherwise the name will change , Authorization will not pass . The public data area varies with the entity type .
边栏推荐
- Cf:c. factors and powers of two [DP + sort + Select Board + select several numbers equal to the minimum number of known sums]
- datepicket和timepicket,日期、时间选择器的功能和用法
- Explain it in simple terms. CNN convolutional neural network
- Create dialog style windows with popupwindow
- Function and usage of calendar view component
- Supplementary instructions to relevant rules of online competition
- 3分钟学会制作动态折线图!
- Functions and usage of ratingbar
- SD_DATA_RECEIVE_SHIFT_REGISTER
- TabHOST 选项卡的功能和用法
猜你喜欢
Supplementary instructions to relevant rules of online competition
![[OKR target management] value analysis](/img/d9/1f0022d3aa34cc10f1151e181dd695.png)
[OKR target management] value analysis
ViewSwitcher的功能和用法
ICer知识点杂烩(后附大量题目,持续更新中)
科学家首次观察到“电子漩涡” 有助于设计出更高效的电子产品

MRS离线数据分析:通过Flink作业处理OBS数据
![[OKR target management] case analysis](/img/73/d28cdf40206408be6e2ca696b8e37f.jpg)
[OKR target management] case analysis

Functions and usage of viewflipper
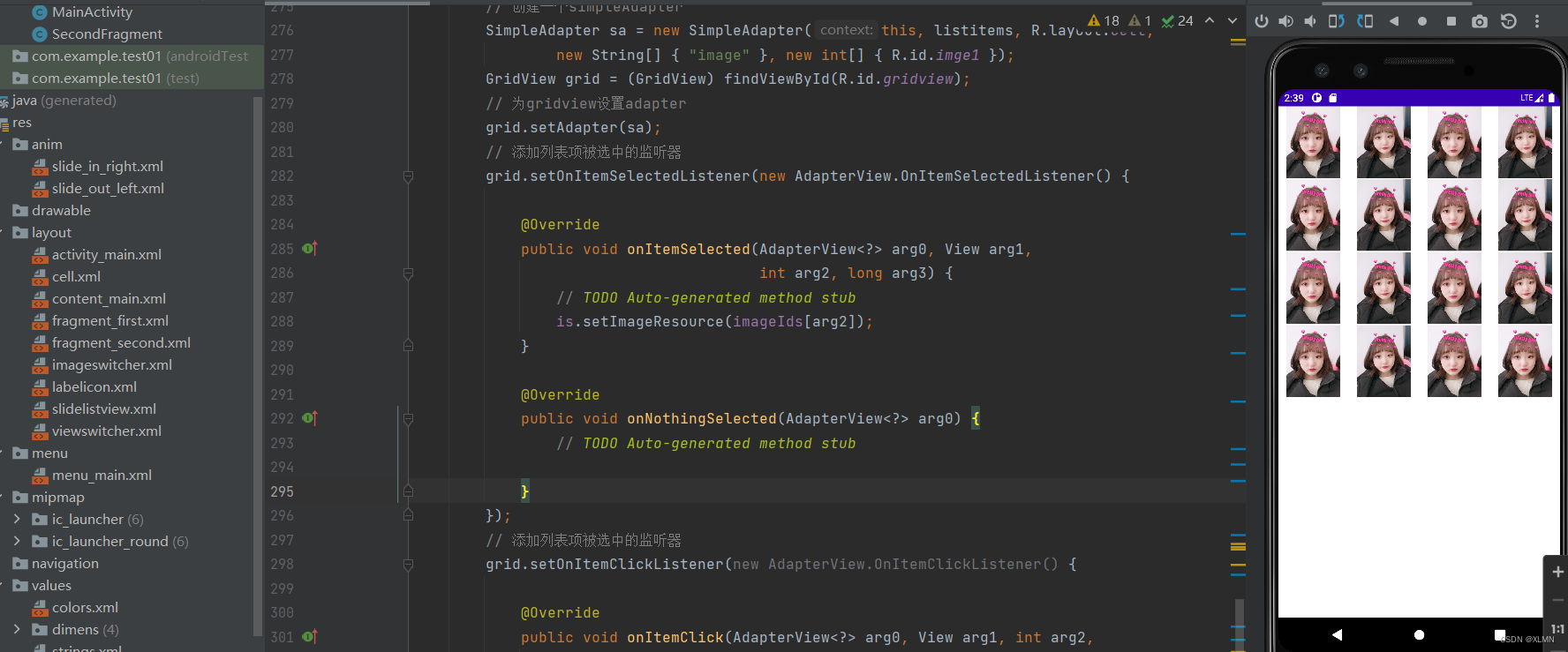
imageswitcher的功能和用法
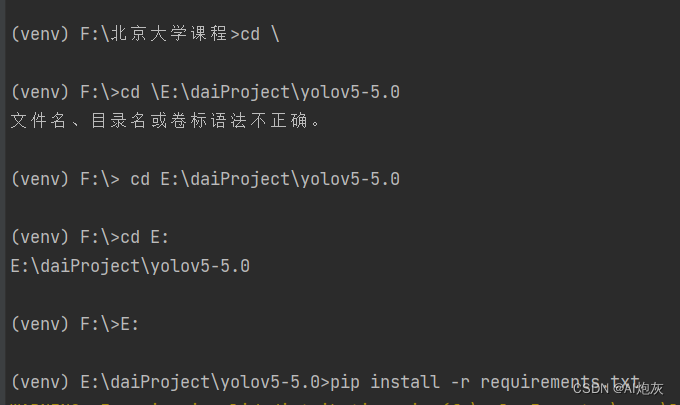
yolo训练过程中批量导入requirments.txt中所需要的包
随机推荐
Functions and usage of ratingbar
Pytorch中自制数据集进行Dataset重写
Numberpick的功能和用法
原生js验证码
【4500字归纳总结】一名软件测试工程师需要掌握的技能大全
Native JS verification code
线上比赛相关规则补充说明
[OKR target management] value analysis
深入浅出图解CNN-卷积神经网络
[re understand the communication model] the application of reactor mode in redis and Kafka
serachview的功能和用法
Mobile pixel bird game JS play code
textSwitch文本切换器的功能和用法
Supplementary instructions to relevant rules of online competition
Cartoon | who is the first ide in the universe?
Show progress bar above window
Alertdialog create dialog
Please insert the disk into "U disk (H)" & unable to access the disk structure is damaged and cannot be read
< code random recording two brushes> linked list
Functions and usage of serachview