当前位置:网站首页>Oscp raven2 target penetration process
Oscp raven2 target penetration process
2022-07-06 06:23:00 【shatianyzg】
Information reconnaissance stage
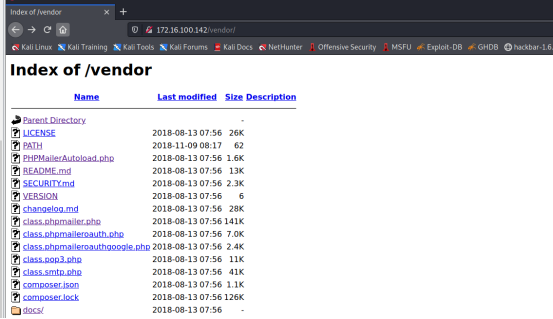
use dirb The scan found the following information
---- Entering directory: http://172.16.100.142/vendor/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode ‘-w’ if you want to scan it anyway)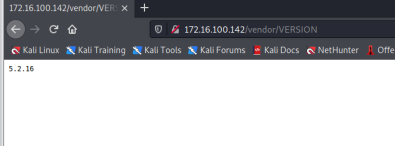
Find the first flag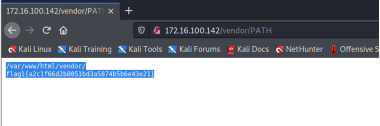
seek PHPMailer 5.2.16 Of exp
searchsploit phpmailer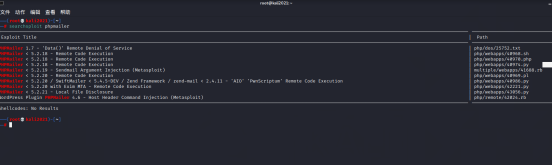
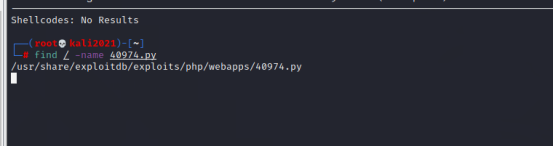
Copy exp To current directory

utilize 40974.py get shell, Get the second flag
边栏推荐
猜你喜欢
随机推荐
org.activiti.bpmn.exceptions.XMLException: cvc-complex-type.2.4.a: 发现了以元素 ‘outgoing‘ 开头的无效内容
【MQTT从入门到提高系列 | 01】从0到1快速搭建MQTT测试环境
Set the print page style by modifying style
Web界面元素的测试
G - Supermarket
Testing of web interface elements
CoordinatorLayout+NestedScrollView+RecyclerView 上拉底部显示不全
数据库-当前读与快照读
模拟卷Leetcode【普通】1109. 航班预订统计
[postman] dynamic variable (also known as mock function)
测试周期被压缩?教你9个方法去应对
LeetCode 739. 每日温度
Avtiviti创建表时报错:Error getting a new connection. Cause: org.apache.commons.dbcp.SQLNestedException
模拟卷Leetcode【普通】1447. 最简分数
一文揭开,测试外包公司的真 相
10m25dcf484c8g (FPGA) amy-6m-0002 BGA GPS module
Black cat takes you to learn UFS protocol Chapter 4: detailed explanation of UFS protocol stack
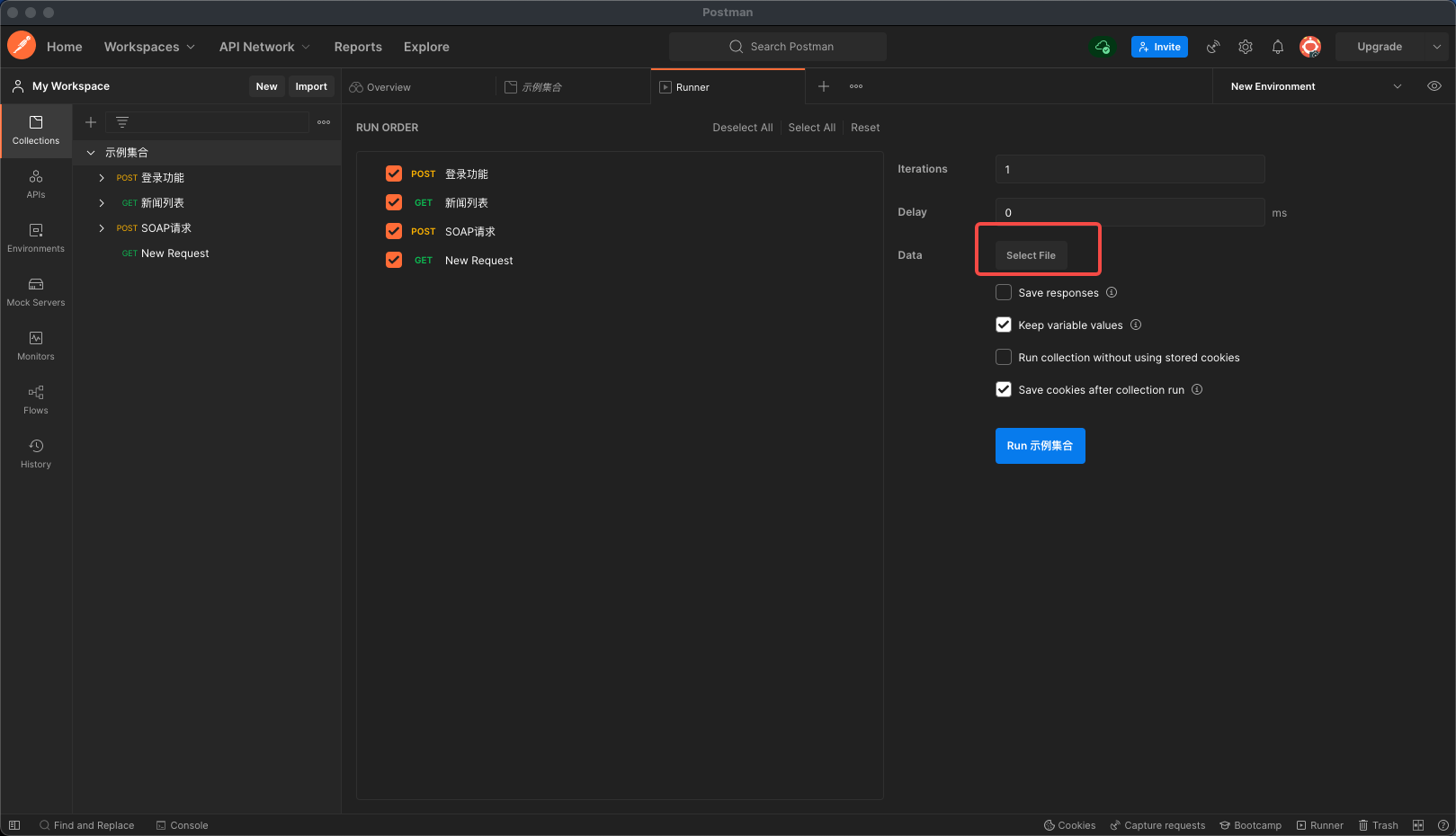
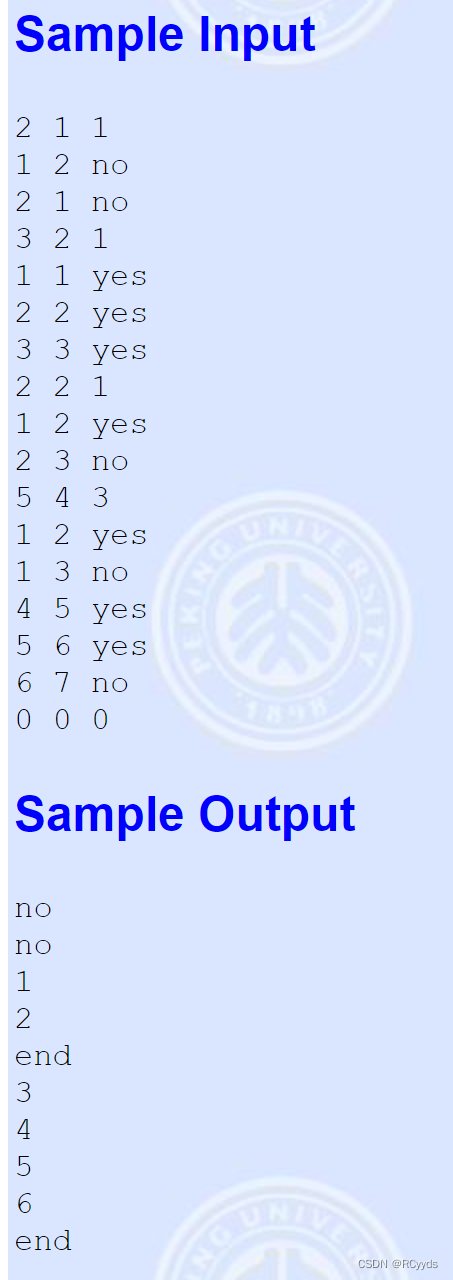
【Postman】Collections-运行配置之导入数据文件
Basic knowledge of error
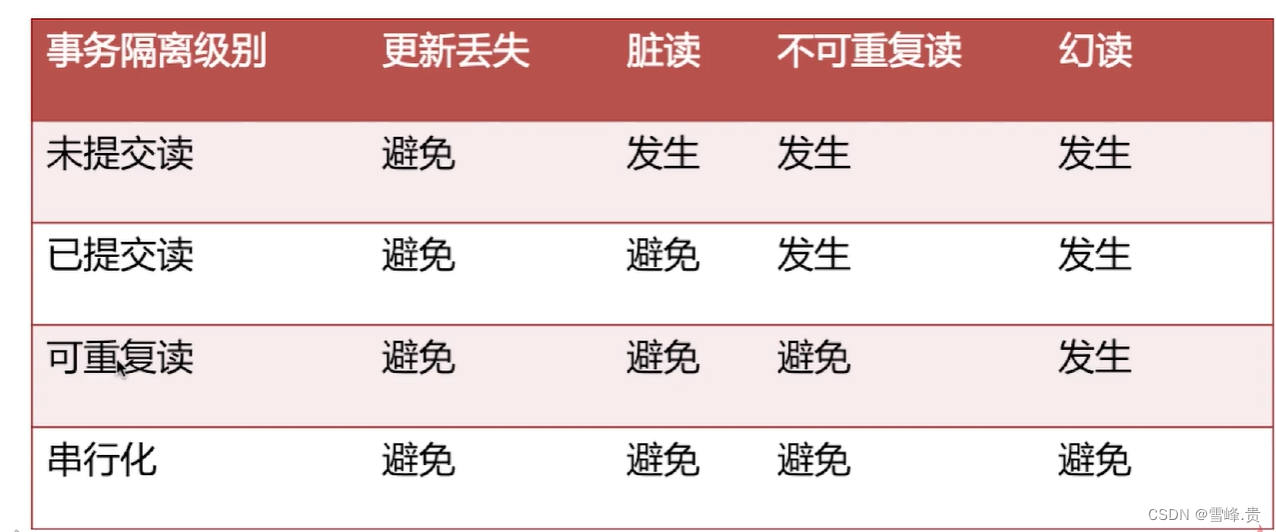
数据库隔离级别
![[postman] collections configuration running process](/img/09/bcd9fd6379fa724671ffd09278442e.png)