当前位置:网站首页>渲大师携手向日葵,远控赋能云渲染及GPU算力服务
渲大师携手向日葵,远控赋能云渲染及GPU算力服务
2022-07-06 11:02:00 【InfoQ】


边栏推荐
- 首先看K一个难看的数字
- Noninvasive and cuff free blood pressure measurement for telemedicine [translation]
- Mathematics in machine learning -- common probability distribution (XIII): Logistic Distribution
- Execution process of MySQL query request - underlying principle
- Understanding disentangling in β- VAE paper reading notes
- This article discusses the memory layout of objects in the JVM, as well as the principle and application of memory alignment and compression pointer
- Penetration test information collection - CDN bypass
- [depth first search] Ji suanke: find numbers
- 华为0基金会——图片整理
- DOM简要
猜你喜欢
徐翔妻子应莹回应“股评”:自己写的!
![[depth first search] Ji suanke: find numbers](/img/e4/708a1e8252bcd2d0d621c66bf6bfed.jpg)
[depth first search] Ji suanke: find numbers
![[Matlab] Simulink 同一模块的输入输出的变量不能同名](/img/99/adfe50075010916439cd053b8f04c7.png)
[Matlab] Simulink 同一模块的输入输出的变量不能同名
None of the strongest kings in the monitoring industry!
Handwritten online chat system (principle part 1)
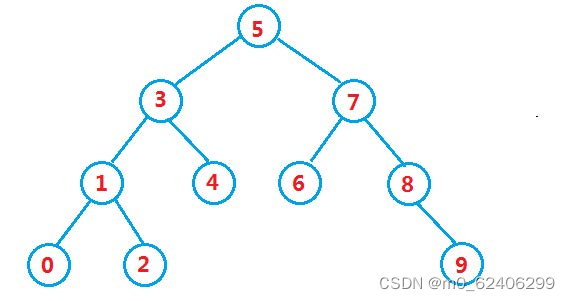
Binary search tree

Describe the process of key exchange

Blue Bridge Cup real question: one question with clear code, master three codes
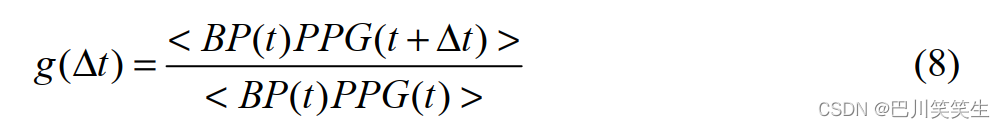
基于ppg和fft神经网络的光学血压估计【翻译】
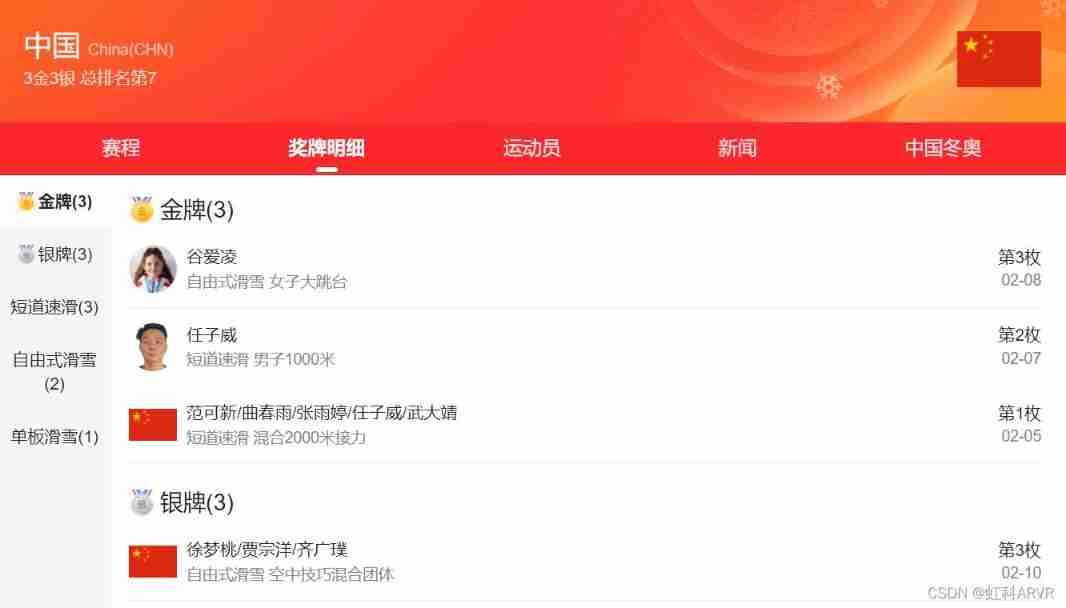
Hongke shares | plate by plate ar application in Beijing Winter Olympics
随机推荐
Epoll () whether it involves wait queue analysis
[sword finger offer] 60 Points of N dice
手写一个的在线聊天系统(原理篇1)
Tree-LSTM的一些理解以及DGL代码实现
用友OA漏洞学习——NCFindWeb 目录遍历漏洞
Docker installation redis
Penetration test information collection - site architecture and construction
44 colleges and universities were selected! Publicity of distributed intelligent computing project list
How are you in the first half of the year occupied by the epidemic| Mid 2022 summary
AUTOCAD——中心线绘制、CAD默认线宽是多少?可以修改吗?
echart简单组件封装
Jushan database was among the first batch of financial information innovation solutions!
Reproduce ThinkPHP 2 X Arbitrary Code Execution Vulnerability
Penetration test information collection - CDN bypass
CSRF vulnerability analysis
Penetration test information collection - App information
Describe the process of key exchange
AFNetworking框架_上传文件或图像server
Numerical analysis: least squares and ridge regression (pytoch Implementation)
UFIDA OA vulnerability learning - ncfindweb directory traversal vulnerability