当前位置:网站首页>[depth first search] Ji suanke: find numbers
[depth first search] Ji suanke: find numbers
2022-07-06 18:46:00 【muse_ age】
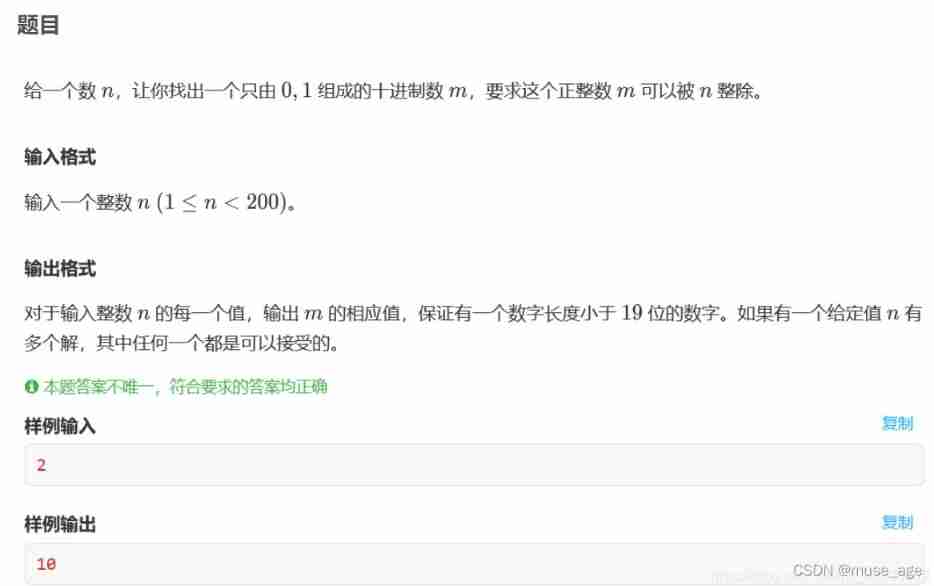
dfs(num) The current number is num
The first is 1, Then everyone can choose 0 perhaps 1.
DFS(num *10);// choice 0 after num
DFS(num*10+1);// choice 1 after num
Because the question in the question is whether it exists , Then we can stop searching after finding a solution .
Pruning operation :
Define a bool Global variables flag, When a solution is found ,flag Set up true,
prune :
if(flag){return;}
Code :
Use it carefully long long
#include<iostream>
using namespace std;
int n;
bool flag;
void dfs(long long num){
if(flag==true){
return;
}
if(num%n==0){
cout<<num<<endl;
flag=true;
return;
}
dfs(num*10);
dfs(num*10+1);
}
int main(){
flag=false;
cin>>n;
dfs(1);
}边栏推荐
- DOM简要
- Video based full link Intelligent Cloud? This article explains in detail what Alibaba cloud video cloud "intelligent media production" is
- POJ 2208 six lengths of tetrahedron are known, and the volume is calculated
- Penetration test information collection - site architecture and construction
- Wchars, coding, standards and portability - wchars, encodings, standards and portability
- 44 colleges and universities were selected! Publicity of distributed intelligent computing project list
- echart简单组件封装
- 一种用于夜间和无袖测量血压手臂可穿戴设备【翻译】
- SAP Fiori 应用索引大全工具和 SAP Fiori Tools 的使用介绍
- 文档编辑之markdown语法(typora)
猜你喜欢

重磅硬核 | 一文聊透对象在 JVM 中的内存布局,以及内存对齐和压缩指针的原理及应用
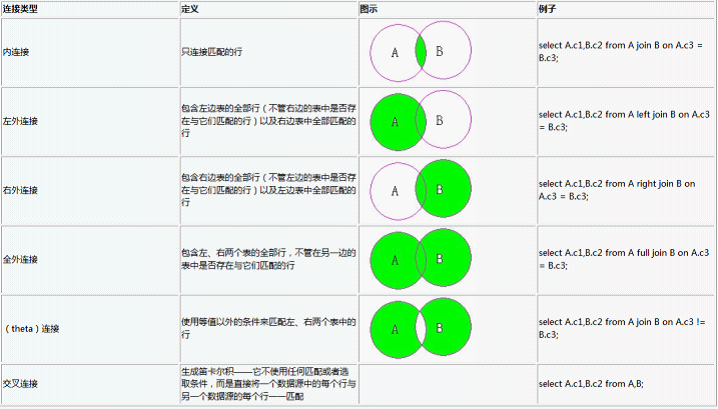
Oracle advanced (IV) table connection explanation
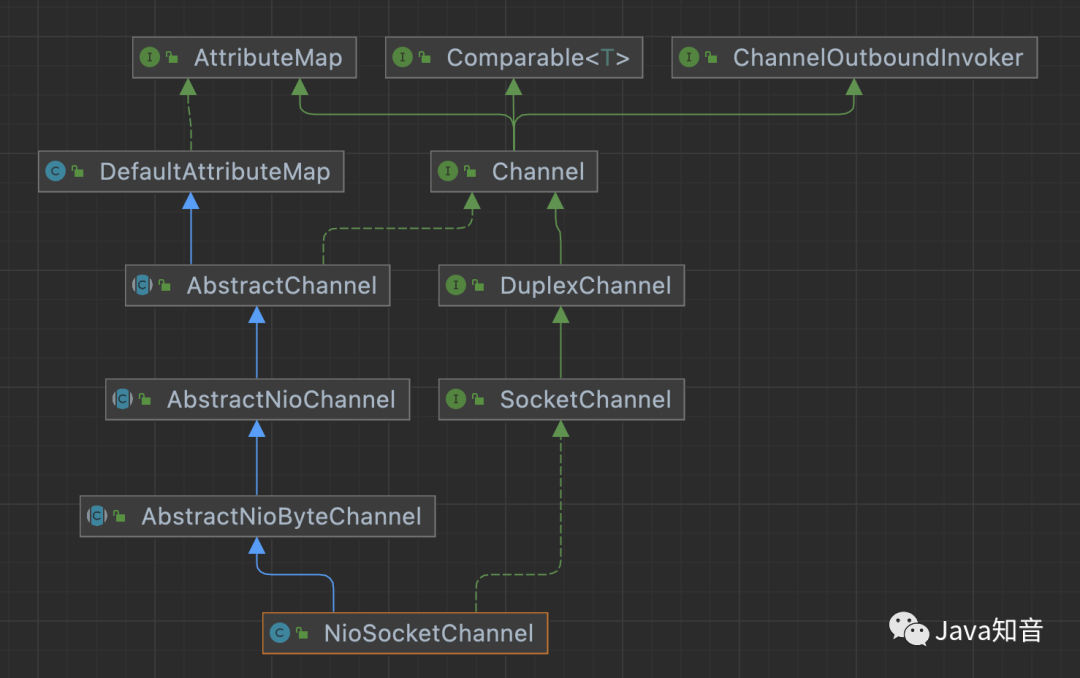
Handwritten online chat system (principle part 1)
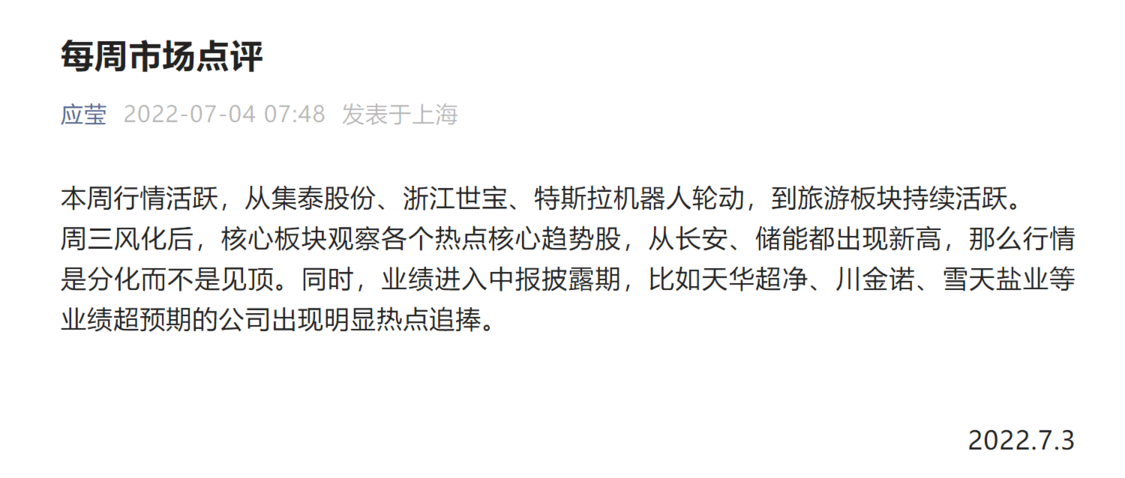
徐翔妻子应莹回应“股评”:自己写的!
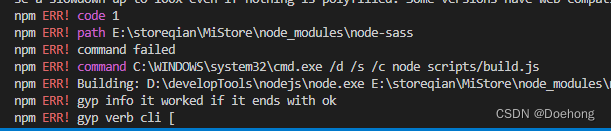
关于npm install 报错问题 error 1

Solve DoS attack production cases
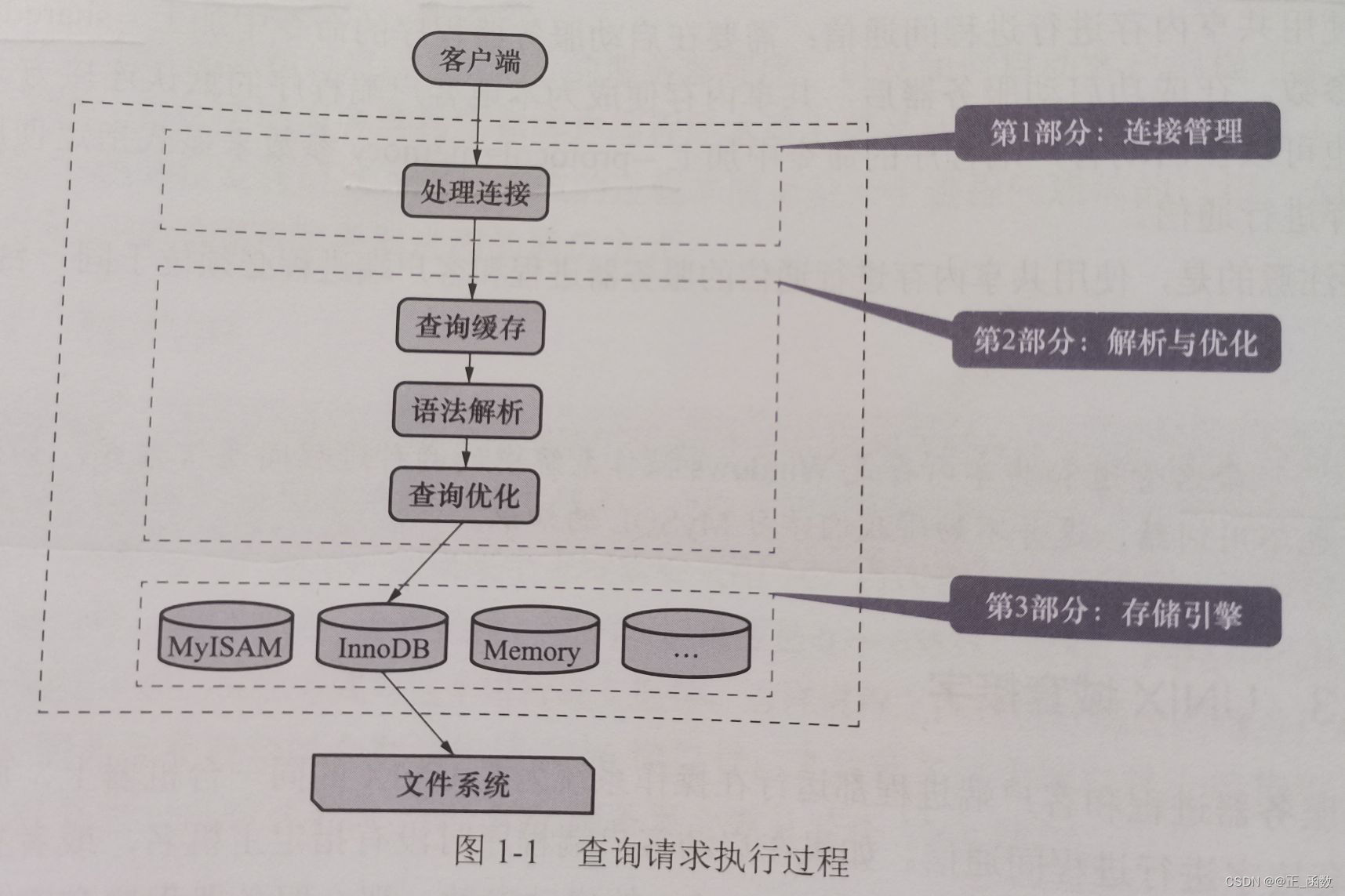
Execution process of MySQL query request - underlying principle
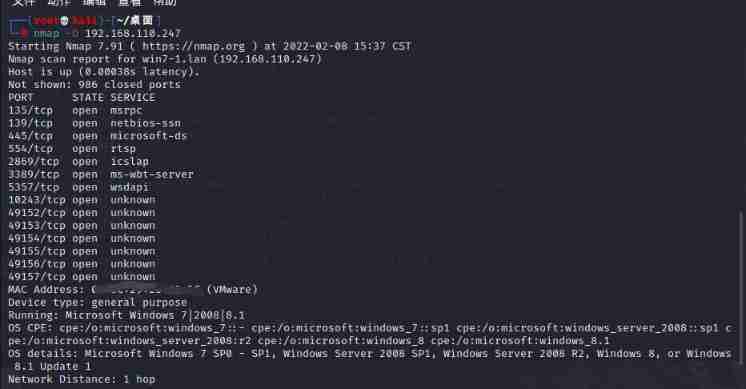
Collection of penetration test information -- use with nmap and other tools

Describe the process of key exchange
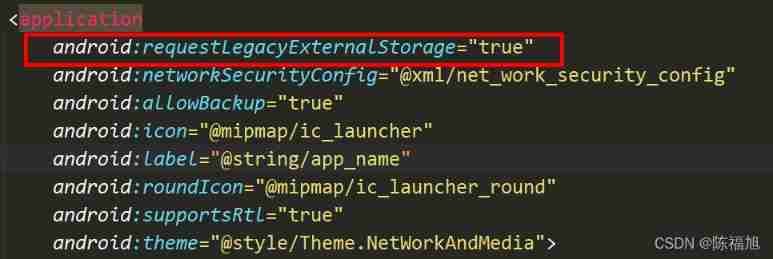
Method of accessing mobile phone storage location permission under non root condition
随机推荐
10、 Process management
测试1234
Use cpolar to build a business website (1)
atcoder它A Mountaineer
Atcoder a mountaineer
A method of sequentially loading Unity Resources
node の SQLite
AcWing 3537. Tree lookup complete binary tree
Stm32+esp8266+mqtt protocol connects onenet IOT platform
Some recruitment markets in Shanghai refuse to recruit patients with covid-19 positive
一种用于夜间和无袖测量血压手臂可穿戴设备【翻译】
Method of accessing mobile phone storage location permission under non root condition
Top command details
使用map函数、split函数一行键入多个元素
SQL injection Foundation
Test 123
使用block实现两个页面之间的传统价值观
Some understandings of tree LSTM and DGL code implementation
helm部署etcd集群
【中山大学】考研初试复试资料分享